[Update: December 9, 2015] We already detect the second Escrow.exe malware sample as Trojan.MSIL.Stealer.
Original post:
“Steam escrow”—This is the term some video game players are familiar with, but officially, it’s known as the “Steam trade hold” system.
It involves the use of the gaming platform’s updated Steam Guard Mobile Authenticator, the security feature that is part of the Steam Mobile app. According to its official Support page, a trade hold “is a period of time where the items traded are held by Steam before they are delivered.” It is one of Valve’s attempts to combat trade scammers and scamming.
This Support page also gives gamers an overview of why this new system is necessary and how it works. We suggest that you, dear Reader, get acquainted with the new authenticator feature if you haven’t already. The trade hold system takes effect today after all.
Steam’s trade hold or “escrow” initially circulated as a rumor among several video gamers as early as the third week of November this year. This also caused quite a stir among those who regularly trade items with friends and strangers via the Steam platform to the point that some took it in their hands to begin several online petitions against the new system on Change.org and ipetitions.
To date, the ipetitions campaign has approximately 28,400 signatures; the organizer has initially aimed for 25,000.
With all the attention the Steam community has been giving to this new system, it is only natural for the online criminals to gravitate towards it, too.
We recently found a fake domain for CSGO Shuffle, a popular betting site for streamers and players of Counter-Strike: Global Offensive (CS:GO) to trade item skins. Take note that instead of taking on the current look of the Shuffle site, it has taken on the guise of Steam’s trading window.
Domain URL: csgoshuffle-trade[DOT]com (registered on the 3rd of December 2015)
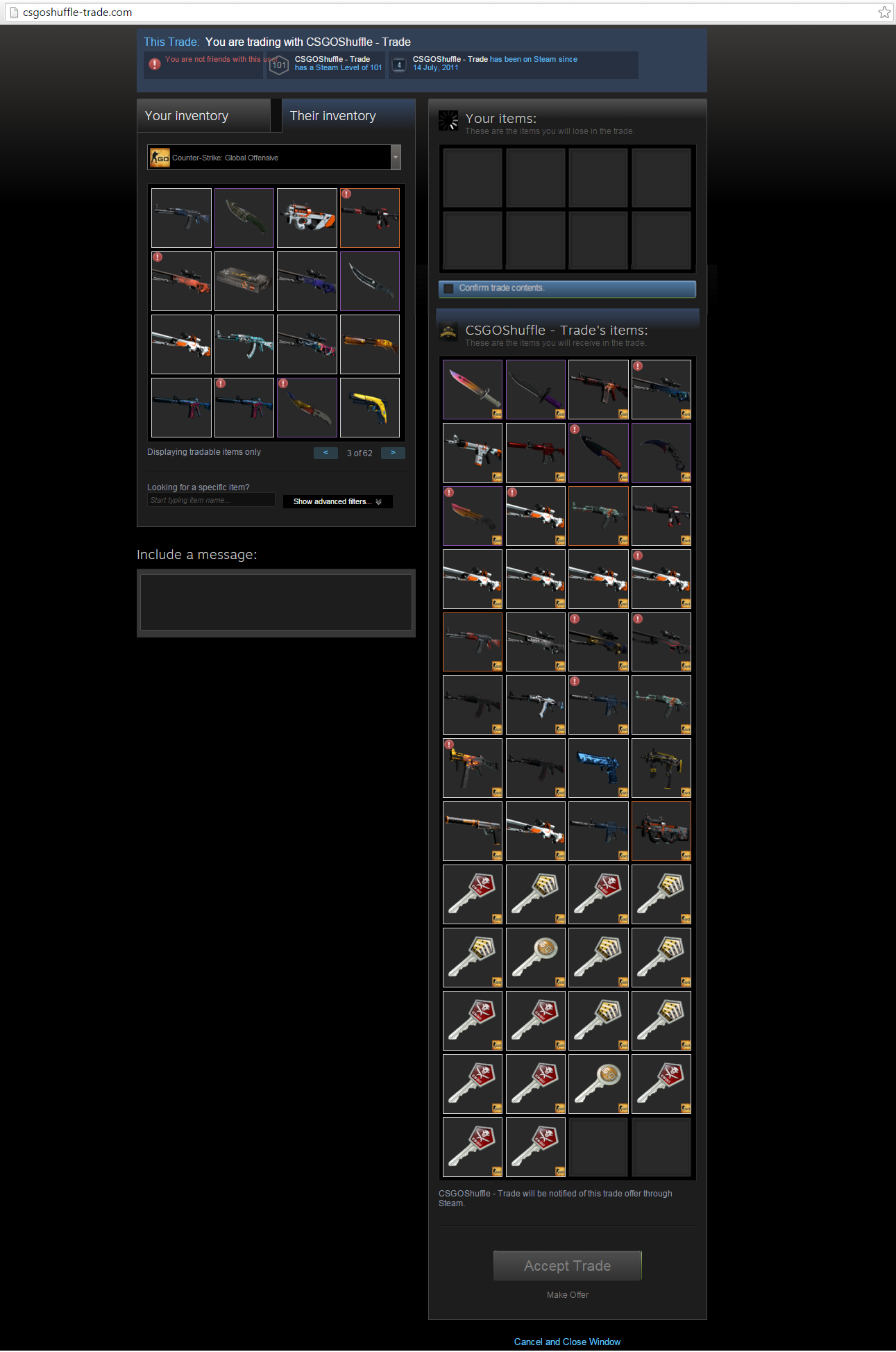
click to enlarge
Malware can be downloaded from this site, but not automatically. One triggers this event by interacting with the page the same way Steam users interact with a trading window. Below is a short illustration of this is done:
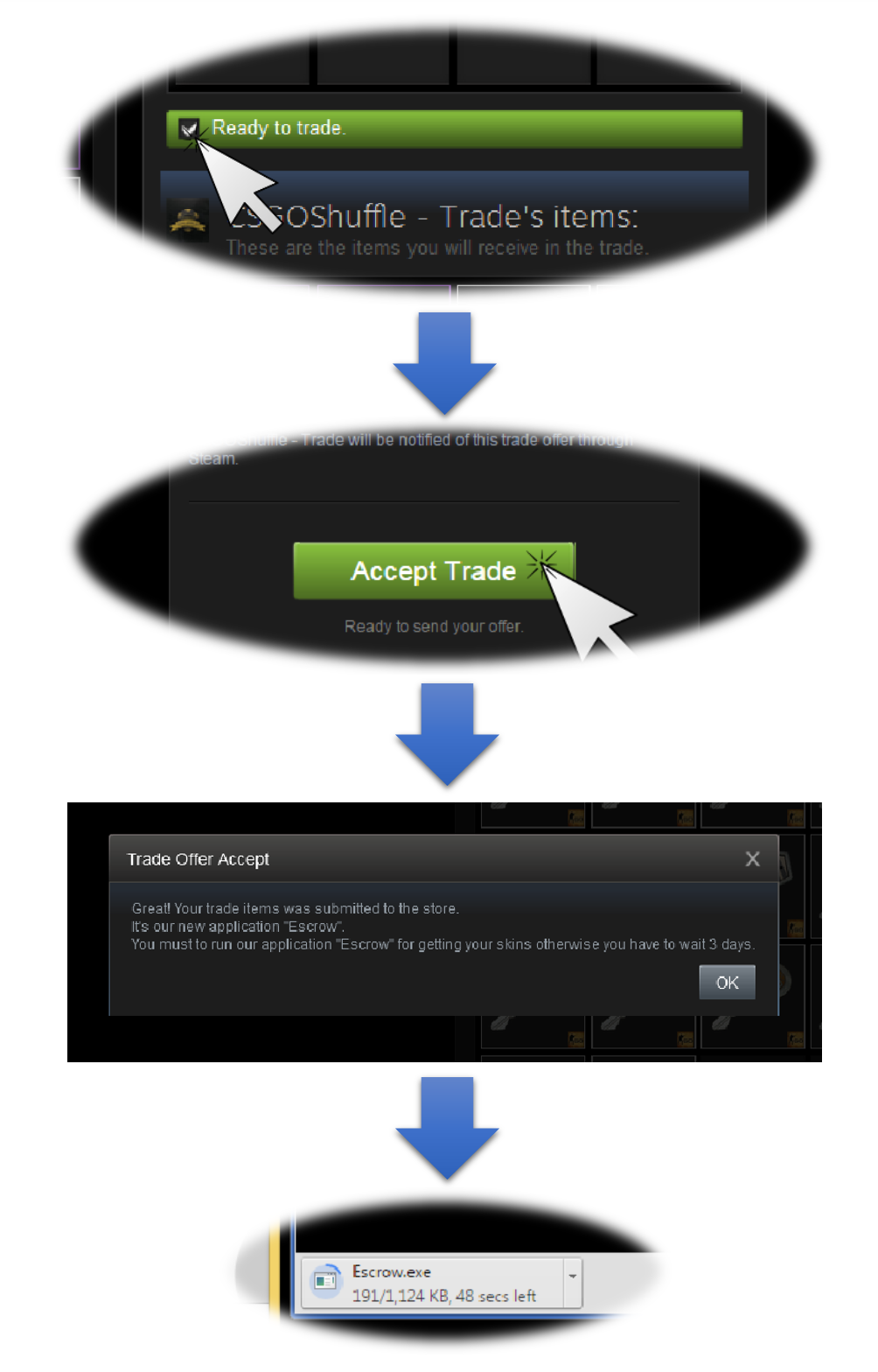
click to enlarge
First, ticking the “Confirm trade contents” blue bar confirms that the user is “ready for trade”. Doing so also enables the initially greyed out “Accept Trade” button at the bottom of the page. Once users click this button, a “Trade Offer Accept” window pops up, saying:
Great! Your trade items was submitted to the store. Its [sic] our new application “Escrow”. You must run our application “Escrow” for getting your skins otherwise you have to wait 3 days.
Clicking the “OK” button signals the page to connect to a Dropbox URL where a file named Escrow.exe is downloaded from.
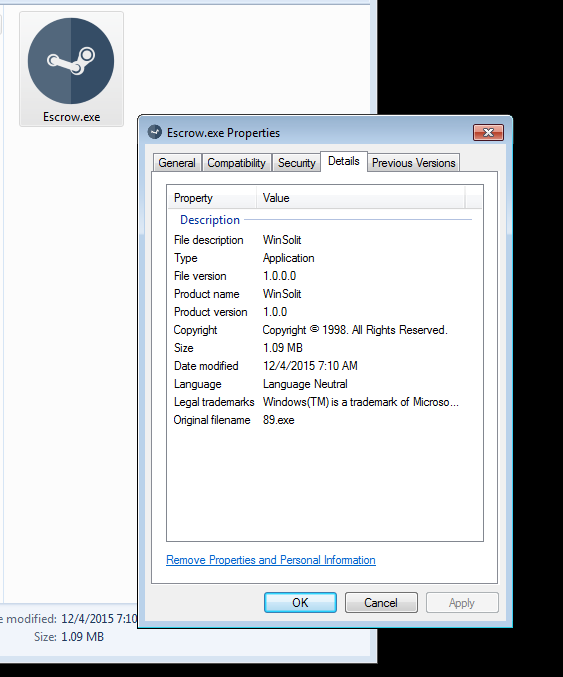
The above is the first (with MD5 hash 5014e666b01adc5f4d31bc59fd902b3d) of the two malware samples that we have retrieved from this campaign. Malwarebytes Anti-Malware (MBAM) detects it as Backdoor.NanoCore. Its source URL is currently down and replaced by a new Dropbox URL today, where we have downloaded our second sample from.
The second sample, which also went by Escrow.exe (with MD5 hash a6b685787f21a8860b153e379ab1cdd9) currently has a low detection score of 6/55 on Virus Total. We will be updating this blog with our detection accordingly.
Users of MBAM and hpHosts are protected from ever reaching csgoshuffle-trade[DOT]com as it readily blocks it.
There is only one application that Steam users have to download, and that is the Steam Mobile app. Any additional programs that users are encouraged to install onto their devices from unofficial third-party destination sites, such as the above, are highly suspect and must be avoided. The Steam Mobile app can only be downloaded from Steam’s official website, from the App Store, and Google Play.
We have already reported the URL hosting the new malware to Dropbox.
Jovi Umawing










