Tech support scammers are a very unique type of online criminals who traditionally were never as sophisticated as malware authors. For the most part, they really didn’t need to be since even a quickly put together scary webpage with some audio background would suffice to con victims.
While this dirty business was poorly organized in the beginning, in recent years things started to shape up and a strong affiliate model blossomed via malvertising. Thousands of websites with fake warnings rely on scare tactics to drive leads (victims) into shady tech support call centres to extort their money.
One of the best and most elusive affiliates to date has been wreaking havoc on Amazon Web Services (AWS) for several months using the Google Safe Browsing template and enjoying the Amazon Elastic Compute Cloud (EC2).
The cloud infrastructure was perfect for a whack-a-mole game where thousands of domains and subdomains on quickly changing IP addresses leave security researchers frustrated while filing countless abuse reports.
This crook was clearly having fun picking various domain names fitting his mood, as well as indulging in various condescending messages on the scam pages.
- allyouneedistocallsupportnow.com
- onthehotlinetechsupport.com
- swiperighttechsupportcalls.com
- swipeleftforvirusesonyourcomputer.com
- callasaptechsupport.com
- ilove-mytechsupport-service247.com
- dontrefusetechsupport.com
- techsupportblingline.com
…
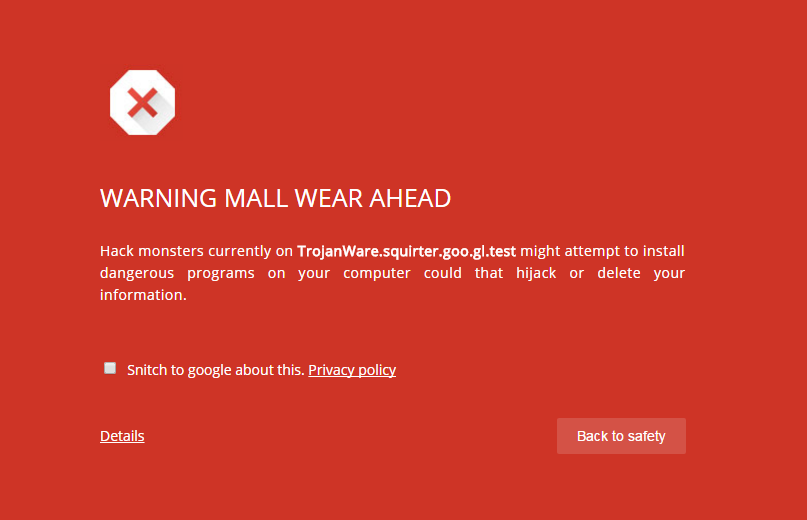
Most of these pages were pushed via malvertising and this activity peaked during the fall.
This actor was using large numbers of sub-domains for each malicious domain, a technique commonly observed in drive-by download attacks and exploit kits:
- 2h4x1u6.trapqueen-browserlock-callsupport.com
- iq8cce.trapqueen-browserlock-callsupport.com
- ghse4l.trapqueen-browserlock-callsupport.com
- ch2au7.trapqueen-browserlock-callsupport.com
- hoj6yi.trapqueen-browserlock-callsupport.com
- ci94z4.trapqueen-browserlock-callsupport.com
- omohcm.trapqueen-browserlock-callsupport.com
- 6lsryl.trapqueen-browserlock-callsupport.com
- flg42b.trapqueen-browserlock-callsupport.com
- 956eo7.trapqueen-browserlock-callsupport.com
- qjq3ud.trapqueen-browserlock-callsupport.com
He was also switching IP addresses via various Amazon EC2 instances, making the process of blocking each scam page much more difficult.
The origins
The Safe Browsing scam may have begun around May 2015 with fix-my-system.com (a domain registered on
2015-05-15) as shown below in a screenshot on May 20 (courtesy of the wayback machine).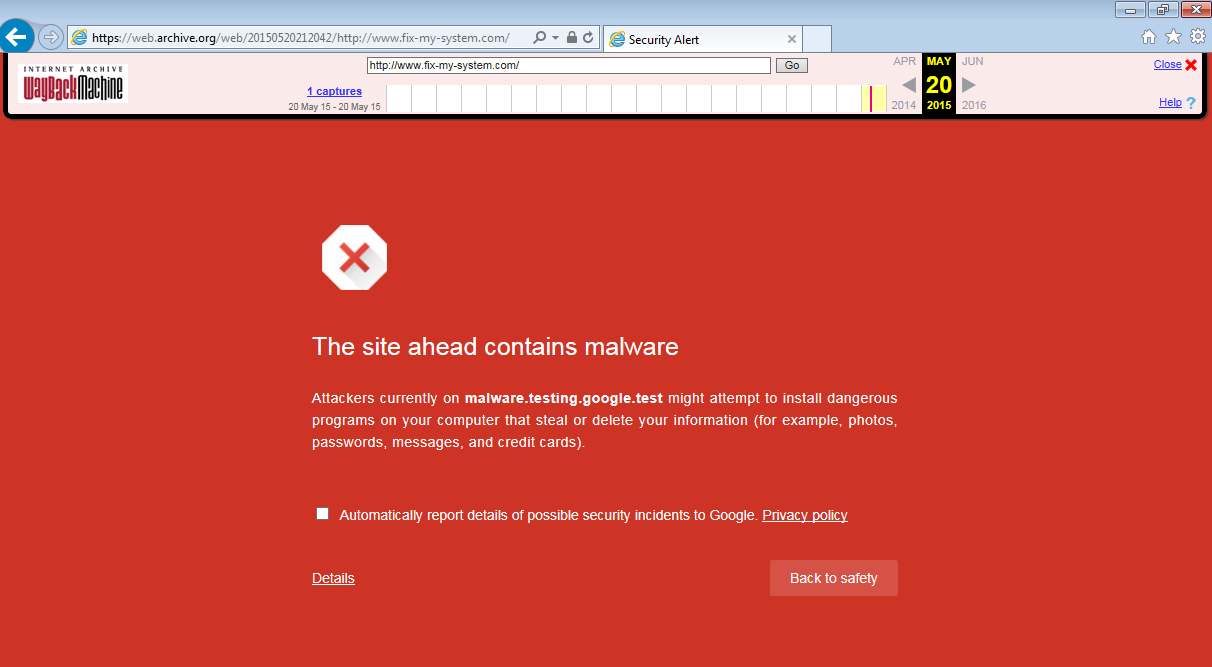
If you compare the cross logo used on Amazon and fix-my-system.com, you notice they are the same file. When extracting the JPEG’s metadata, it shows that image was created on May 14, just one day before fix-my-system.com was registered.
- s3.amazonaws.com/lp3cloudfront/cross.jpg
- fix-my-system.com/images/cross.jpg

There were perhaps other similar scam pages floating around during the month of May. The same Google Analytics ID (UA-61342480-1) the scammer used to track stats during the AWS campaign, was first used on browsererror.co (registered on May 13) and documented in this Chromium thread.
From Amazon to Rackspace
Strangely, we stopped seeing this particular campaign around late November / early December, at least via the traditional delivery mechanisms.
At the same time, we started noticing scam pages with an eerily familiar look, except they were not hosted on AWS. These ones have been taking root on another big cloud provider, Rackspace via the Akamai Content Delivery Network (CDN):
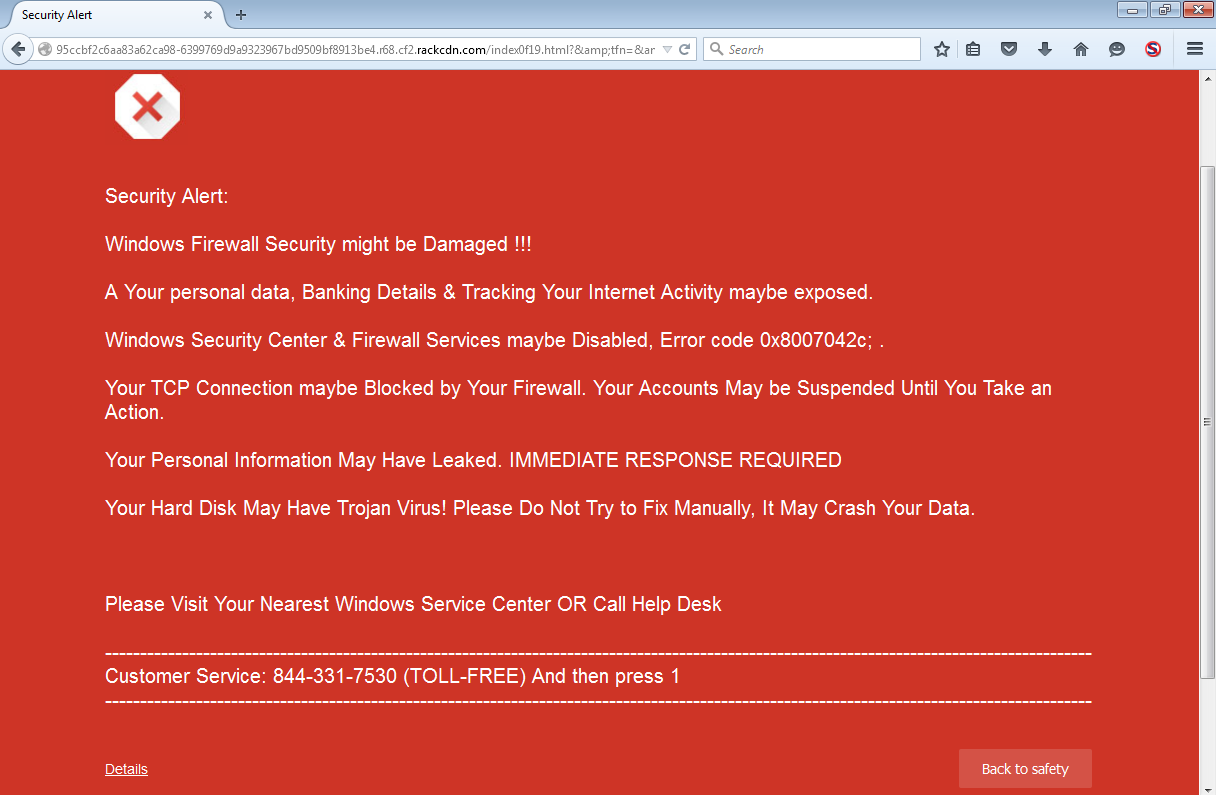
Here are some of the URLs/patterns:
- 95ccbf2c6aa83a62ca98-6399769d9a9323967bd9509bf8913be4.r68.cf2.rackcdn.com/index.html
- 2e6cce8d37e55a52fdbd-99308430c4fad7ba45f55e863183e59a.r58.cf1.rackcdn.com/index.html
- 82b379980e1e684f6a37-f44861df22a3cd4eba5cb48c72143e81.r69.cf2.rackcdn.com/index.html
- 188b8b6393dda1198fbe-0655d317fddd23f8d16491c908ad7a25.r77.cf2.rackcdn.com/index.html
- 81588c665c25cdb253f6-9602d6b2c454e8db39045981b1517c02.r78.cf1.rackcdn.com/index.html
- a5038237257bb0902ab6-1a5f1e0504c9e24f23b040bfb665316e.r34.cf1.rackcdn.com/index.html
- 879a9c84f5d91707643f-458421ed91a4e295ba8ce97333c32837.r55.cf2.rackcdn.com/index.html
IP addresses (not terribly useful as it’s a CDN):
- 63.144.17.66
- 63.144.17.17
- 63.144.17.88
- 63.144.17.58
- 63.144.17.34
- 207.228.83.56
- 207.228.83.51
The page’s source code is very similar to the original one.
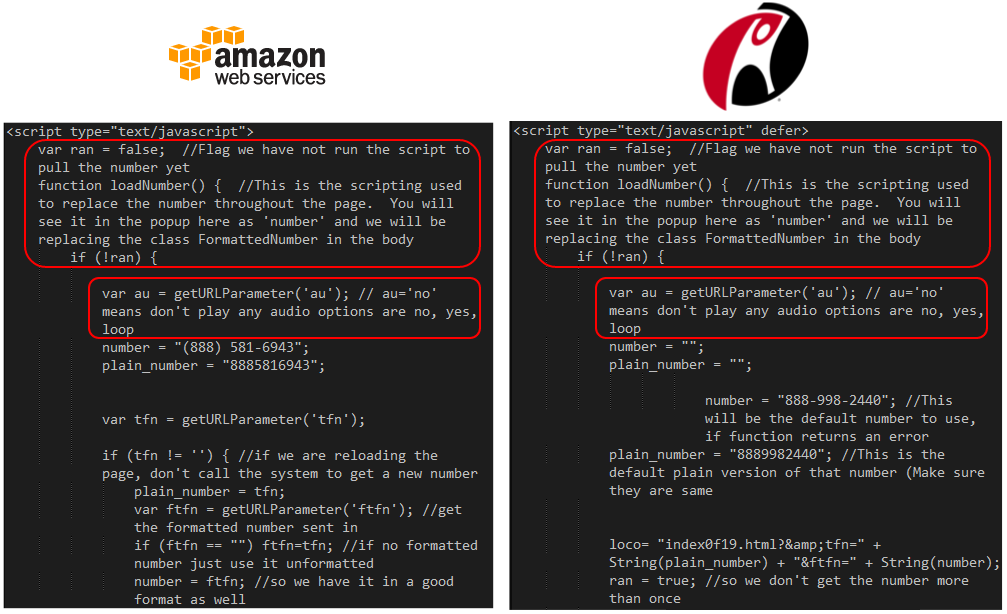
The picture that represents the X at the top of the page is exactly the same as well (same metadata also):
- da6a0dc8349026d5c07d-cc1abd3d110d027f7f34188fa53a4ad8.r8.cf2.rackcdn.com/cross.jpg
Another interesting element when looking at the neighbouring websites used by the crooks in the original AWS model was the presence of domain names advertising iPhone sweepstakes and other such scams.
This seems to be the case on Rackspace as well:
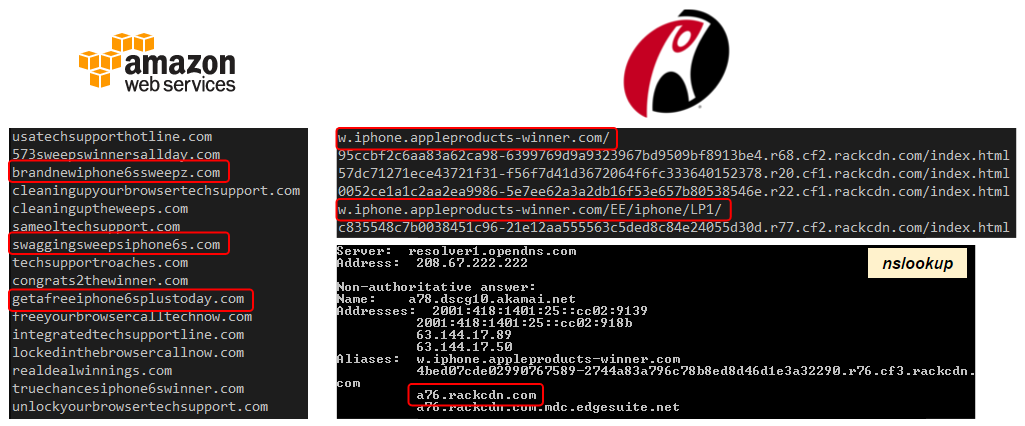
It’s possible this is a different actor simply copying previous work (tech support scammers are notorious for stealing from each other, using the popular website copier program HTTrack).
Regardless, this means that the fight against tech support scammers continues on a different battlefield. We have already reported this particular campaign to Rackspace for takedown and will keep tracking it to see where it goes next.
Malwarebytes Anti-Malware Premium users are protected against many of these fraudulent pages thanks to our malicious sites blocking technology. The best defence against tech support scams remains awareness and common sense.
For more general information on this topic, please visit our Tech Support Scams resource page.










