Update (12/2): According to Forbes, this zero-day was sold by Exodus Intel earlier this year and somehow got leaked. Additional coverage here from Motherboard.
A newly found vulnerability (CVE-2016-9079) in the Firefox web browser was found to be leveraged in the wild. It is not the first time this has happened, as some of you may recall back in 2013, the FBI used a nearly identical one to expose some users running the Tor Browser.
The Tor Browser (based on Mozilla Firefox Extended Support Release) is used worldwide by all people who want greater anonymity online which includes political activists or dissidents wanting to bypass limitations or surveillance put in place by oppressive regimes.
According to Mozilla, “the exploit took advantage of a bug in Firefox to allow the attacker to execute arbitrary code on the targeted system by having the victim load a web page containing malicious JavaScript and SVG code“.
Via this exploit, an attacker can collect the victim’s IP and MAC addresses, as well as their hostname which it sends to a remote server (5.39.27.226). This server is now down, but we were able to reproduce the exploit and observe the TCP packets where the data would be sent.
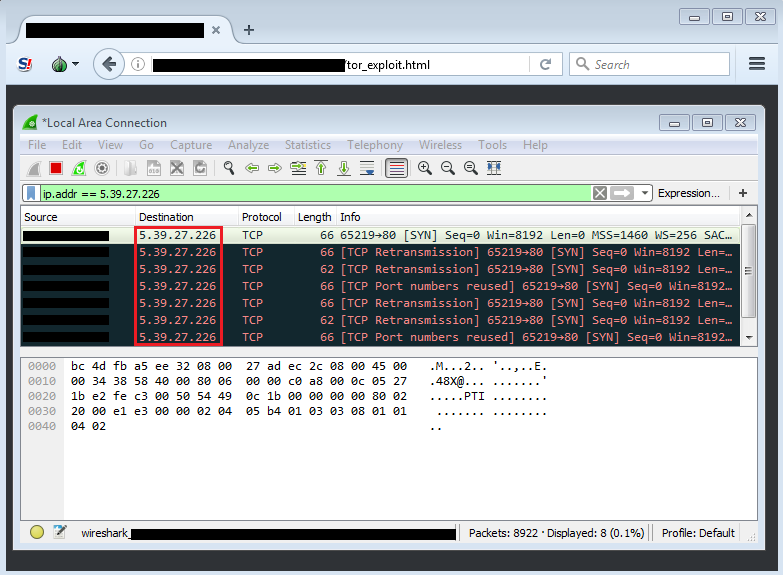
It’s worth noting that not all exploits are meant to infect the target machine. In this case, for example, the goal is to leak user data with as minimal of a footprint as possible. There’s no malicious code downloaded to disk, only shell code is ran directly from memory.
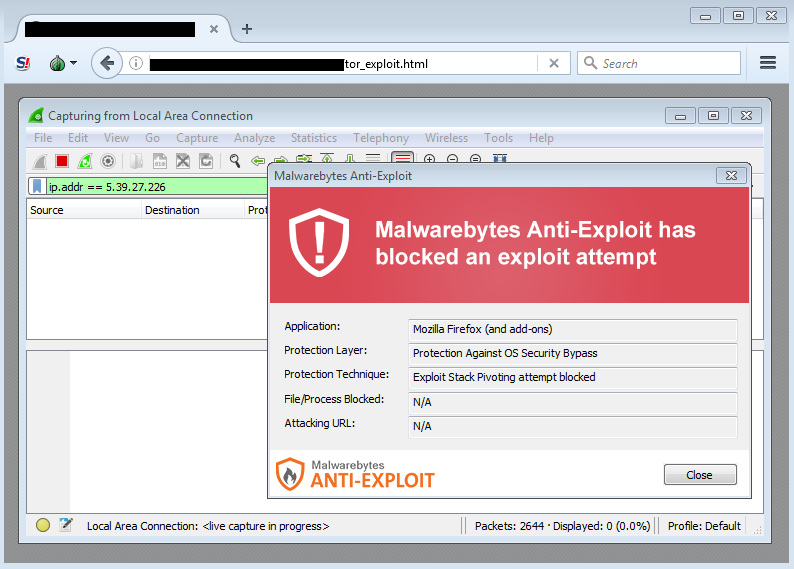
It would be very easy for attackers to change the payload and instead of trying to identify a user via their IP address they could push anything they wish. Watch this proof of concept launching calc.exe.
This zero-day can be thwarted by adjusting the security slider to ‘High’ within Tor Browser’s Privacy and Security Settings, but that is not the default option. Alternatively, people running Malwarebytes Anti-Exploit were already protected against this 0day.
This latest attack continues to increase the concern over the Tor Brower’s efficacy against exploits and how other browsers such as Google Chrome or Edge work to handle memory corruption and sandboxing. One thing is for sure, browsers and their plugins remain the best attack vector to deliver malware or leak data via drive-by attacks.
Both Mozilla and Tor have released a patch to address this zero-day.