NOTE: thanks to the Wack0lian for research contributions
It would seem that scams as a service are a growth business model. Last time, we looked at inboundpopaps[.]info, a slick scam in a box designed to get even the most technically illiterate criminals up and running and stealing from you. Today we’ve found something a little more interesting – a scam in a box company that also offers intelligence leads. That is, they’ll sell you the scam and point you at the most vulnerable targets first.
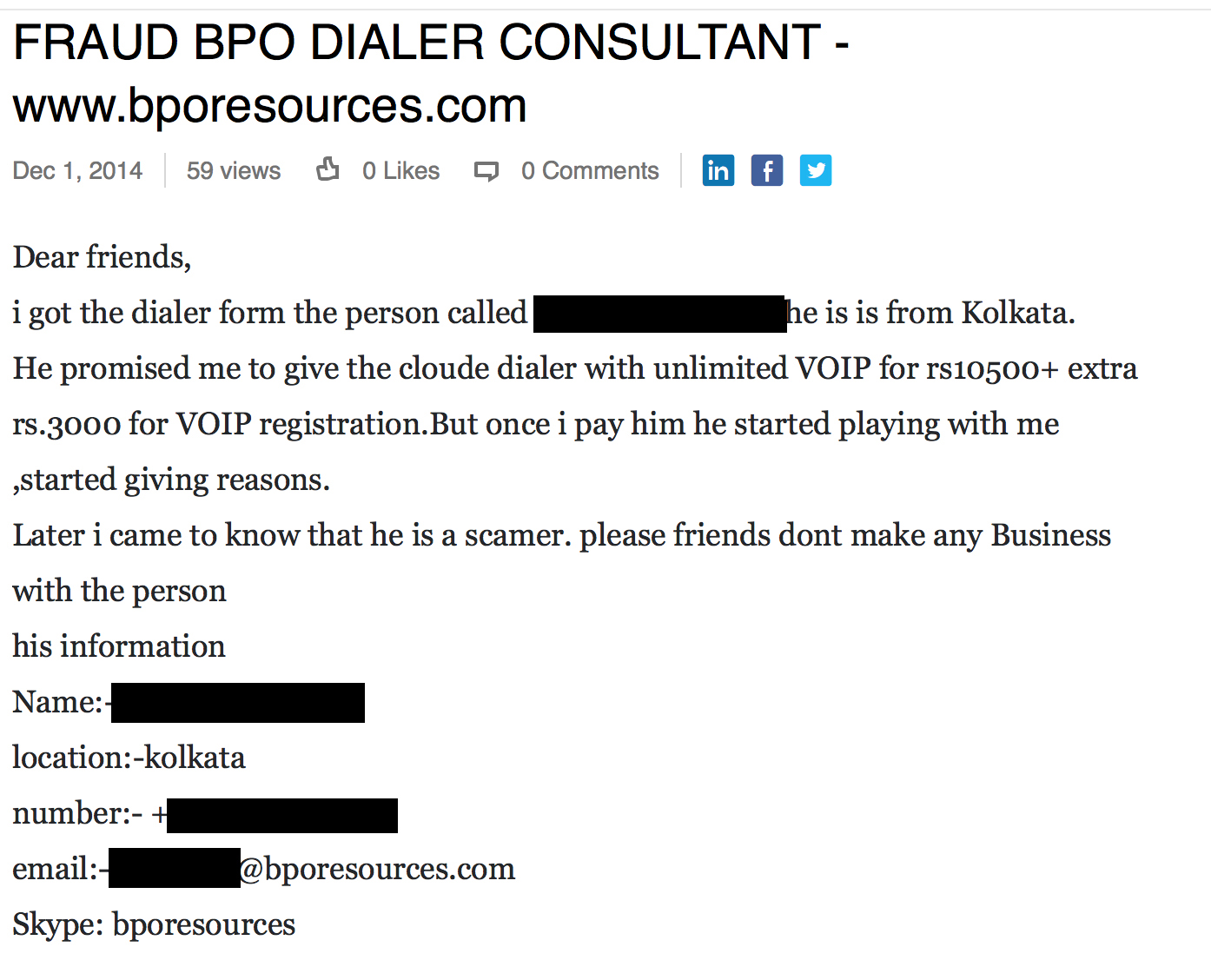
In July of 2014, someone posting under the name BPO Resources posted the following on an outsourced IT services forum.
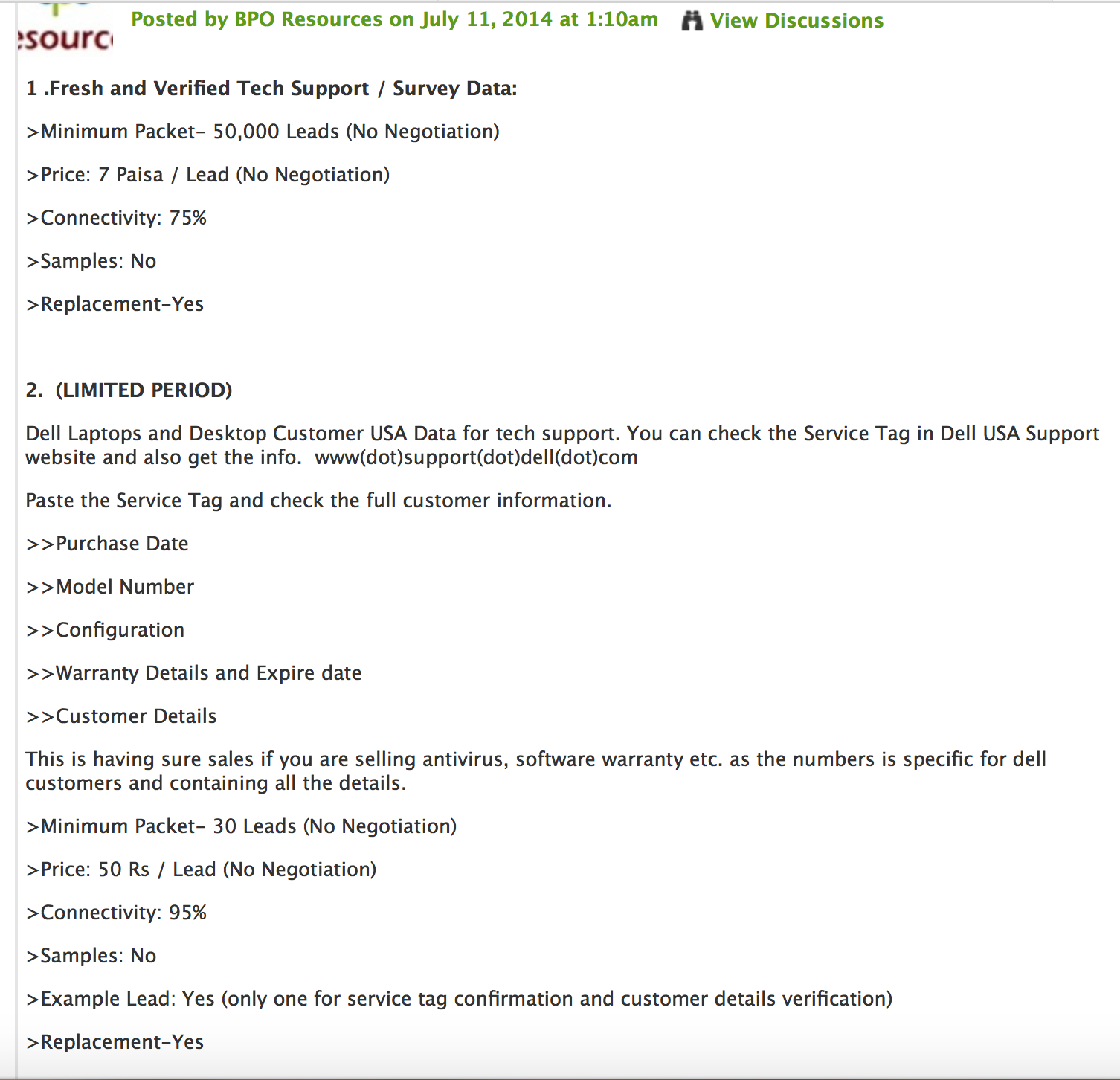
Typically tech support callers are noted for not knowing the slightest thing about the people they call, so targeted leads for specific company customers was interesting. Almost identical verbiage appears on bpoexpertsglobal.blogspot.com.
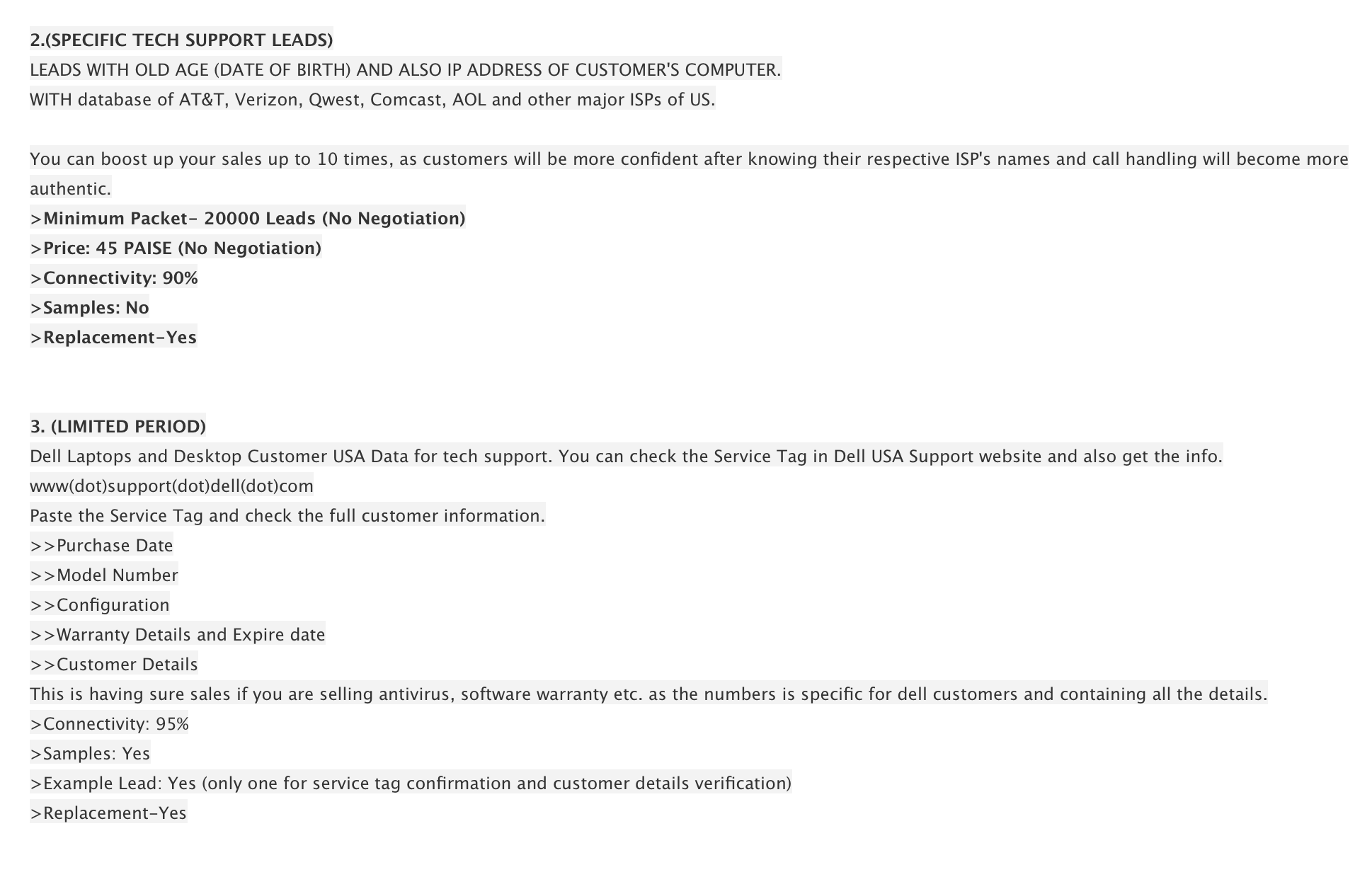
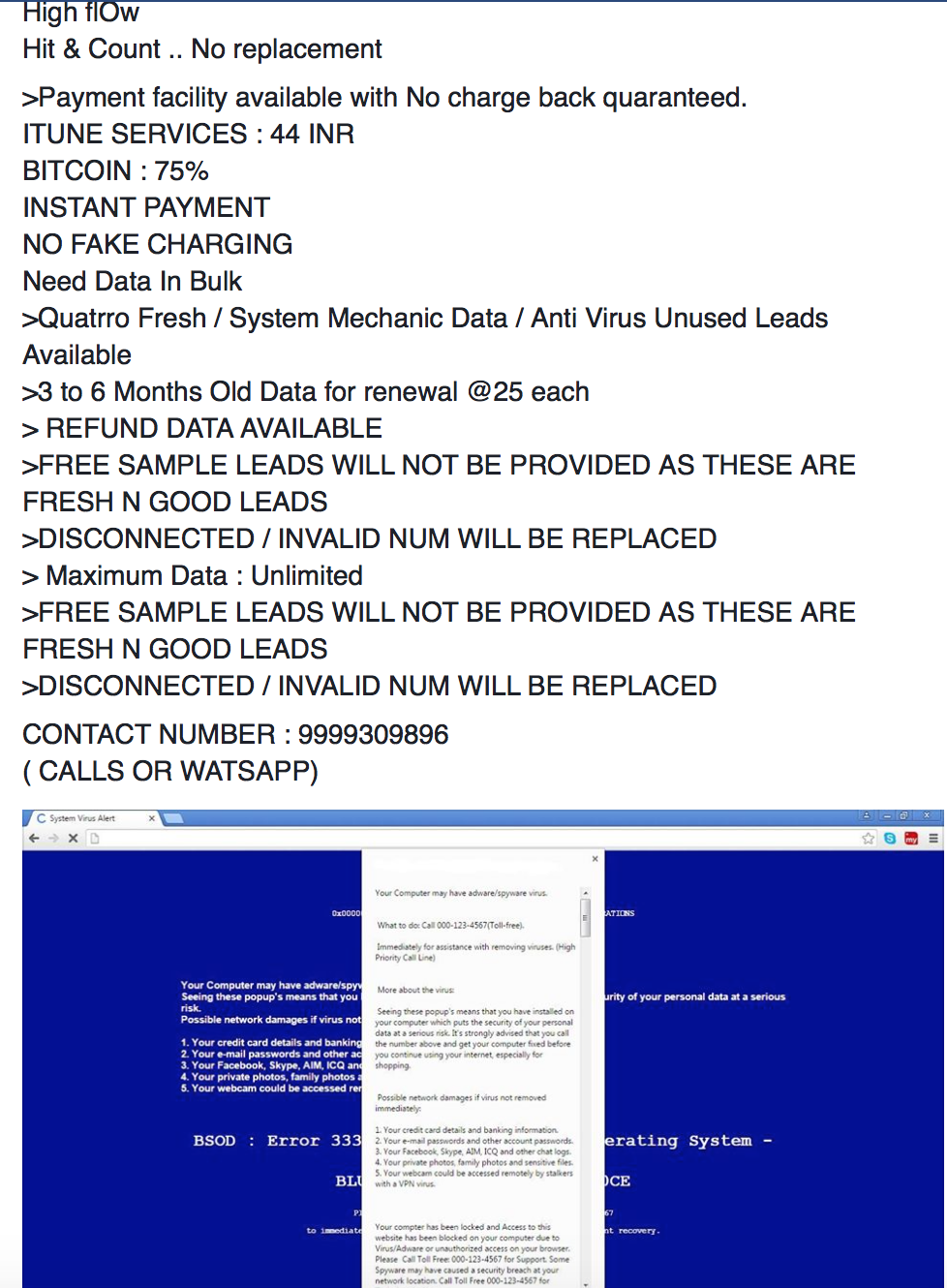
This time though, the threat actor also has on offer the personal data of elderly customers of ISPs as well. This was less surprising, as scammers of all sorts prefer to victimize the elderly. Given that this guy appears to be diversifying his crime verticals, what might he be offering more recently? Searching for BPO Experts Global provided a Youtube channel of the same name where the scammer is kind enough to demonstrate his screen locker that’s currently for sale. (We’ve written about these lockers here). If you’ve been hit by this sort of thing, be sure to check out our forums for removal guides. Let’s allow the scammer to speak for himself for a minute:
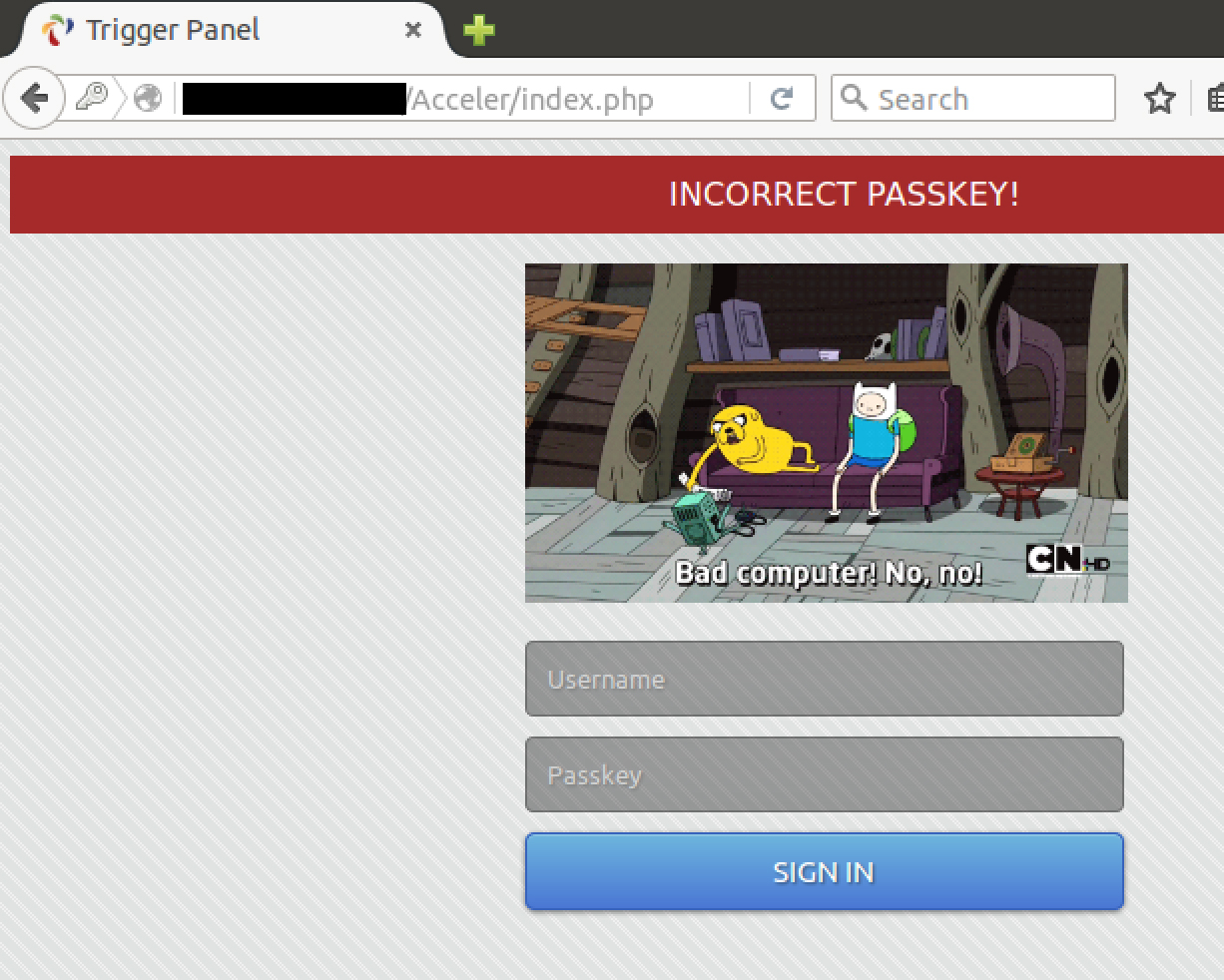
Here’s the back end login panel, with a fun graphic when you enter an incorrect password.
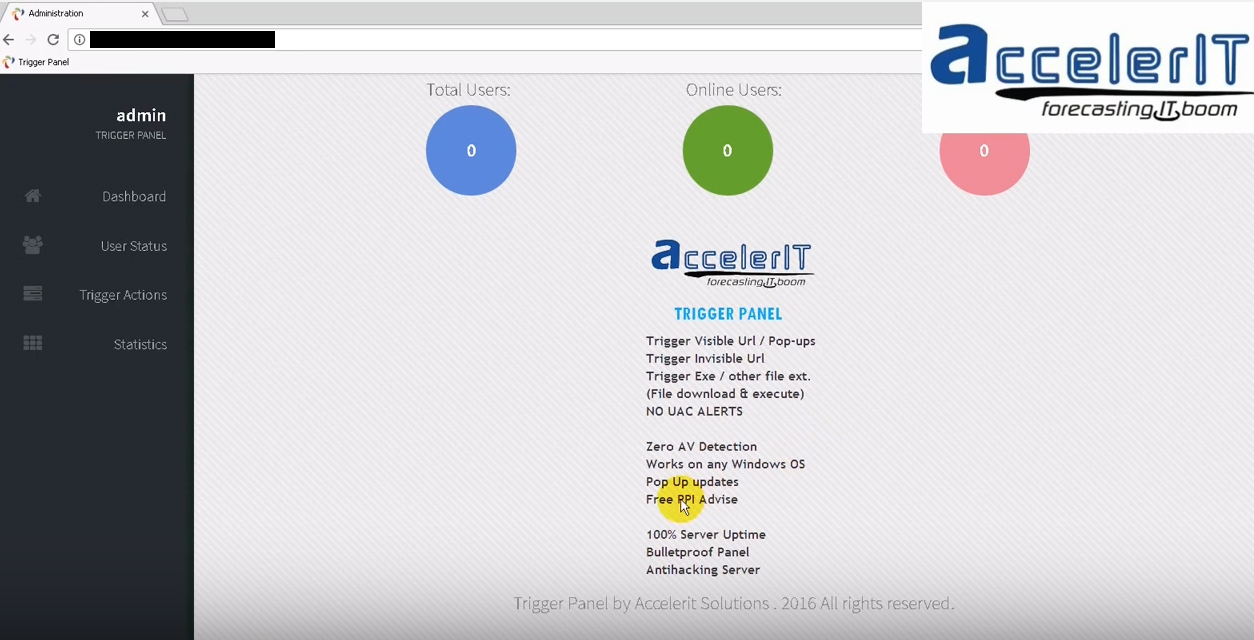
And here we have the panel itself, where the author brags about being able to trigger popups, invisible URLS, and download an execute exes on the victim’s machine, all without any UAC alerts on a Windows machine. A botnet, in other words. So we have a threat actor progressing from selling leads, to selling stolen data, to selling screen lockers in support of other scammers. But who is this guy and how does he have Dell customer data? Lets start with where he is.
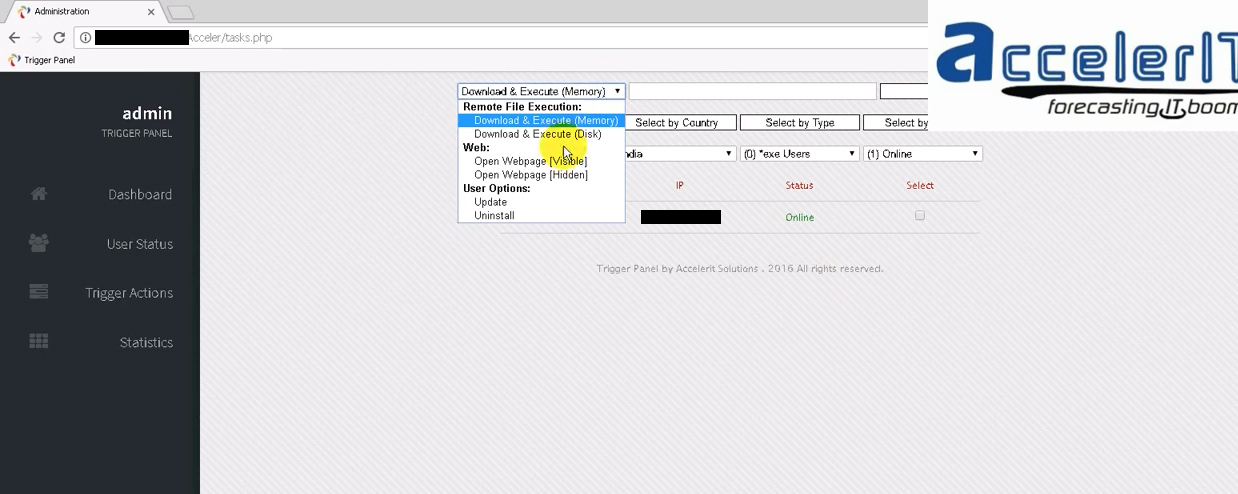
While infecting himself with his own product, he forgot to blank out his own IP, which is registered to a broadband company in Bangalore. The footnote at the bottom of the panel says “Accelerit Solutions”, which yields a homepage of systemnetworksecure.com. The site and its phone number show up in extensive comment spam and various tech support scam pitches, but does not offer up any personal details. Searching directly on the company name is more interesting.
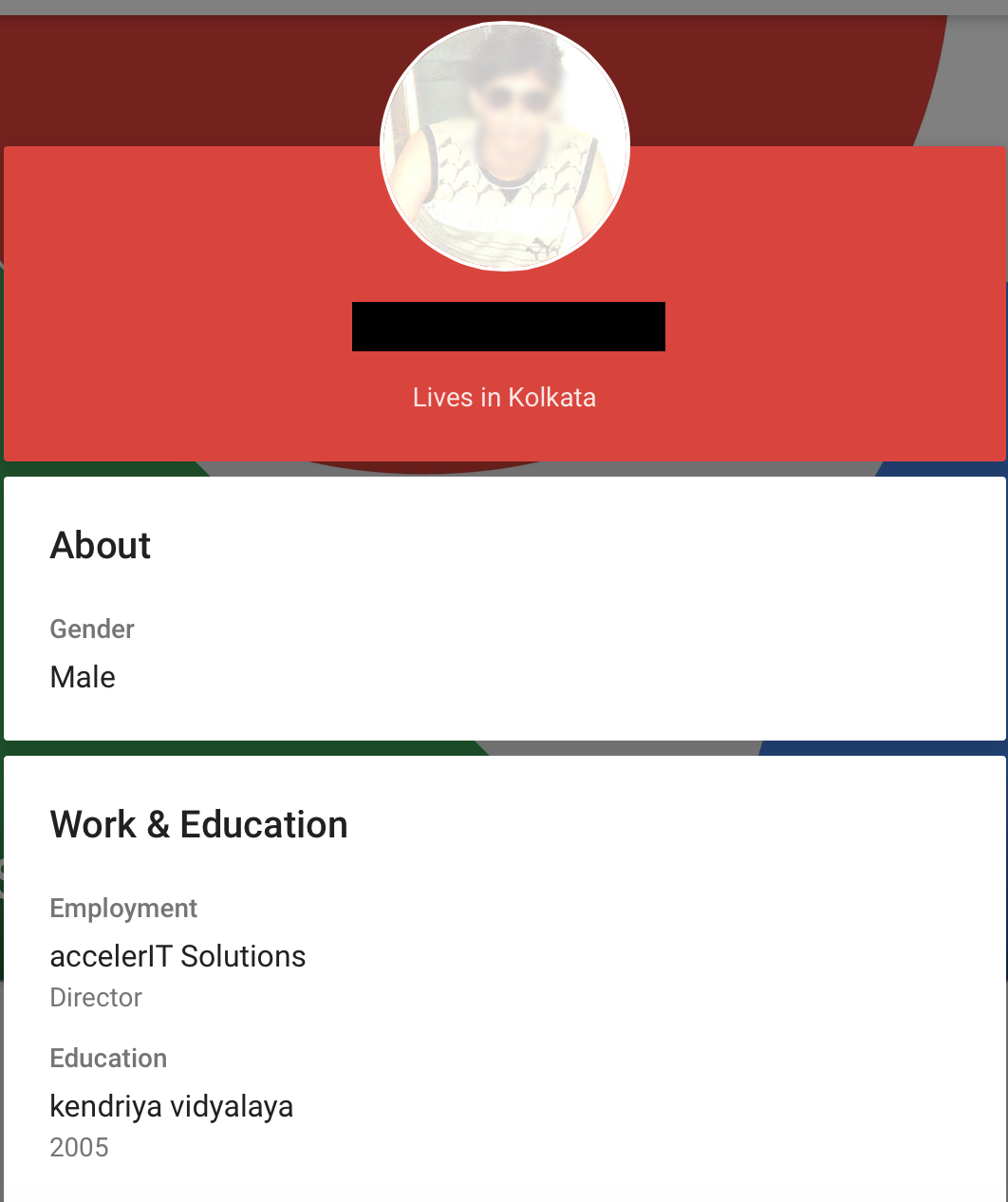
He apparently also doesn’t play nice with his customers, as we can see in reference to a previous iteration of his site. If you’ll recall, BPOresources was the name of the account that made the original forums posting in 2014.
And lastly, he’s a member of a Facebook group that openly sells pre-fab tech support scam pages.
So we have a pretty good idea of who’s behind BPO Experts Global. But how did they get the Dell customer data? Well, possibly several ways. Back in January, Ars technica wrote about a wave of tech support scam calls targeting Dell customers with apparently accurate purchase information. That article referenced a vulnerability disclosed 11/25/2015 here (followup here) involving a vulnerable preinstalled certificate that can be used to leak a Dell owner’s service tag. Brian Krebs followed up citing the same vulnerability, and referencing an ongoing Dell investigation.
Mr. X didn’t necessarily have to make use of the vulnerability himself. Tech support scammers are renowned for their quick sharing of TTPs and presumably once one scammer gained access to Dell customer data, he quickly sold and resold it to others. Given that the original forum post was dated 2014, its likely that the data cache is widely available on the underground in India. Although, as we’ve seen above, scammers largely feel free to conduct their business in the open, on US social media and in English.
Mr. X’s tech support botnet is not the first we’ve seen. He falls into a trend we’ve observed recently of the more enterprising scammers adapting to changing search engine policies banning remote tech support listings and upgrading their techniques to more sophisticated, more damaging methods that closely resemble established malware. As the less technically adept criminals get squeezed out, it’s reasonable to expect that we’ll see the remaining scammers improve, adapt, and overcome.










