Phishing continues to be a criminals’ favorite for harvesting user credentials with more or less sophisticated social engineering tricks. In this post, we take a look at a recent attack that uses existing LinkedIn user accounts to send phishing links to their contacts via private message but also to external members via email.
What makes this campaign interesting is the abuse of long standing and trusted accounts that were hacked, including Premium membership accounts that have the ability to contact other LinkedIn users (even if they aren’t a direct contact) via the InMail feature. The fraudulent message includes a reference to a shared document and a link that redirects to a phishing site for Gmail and other email providers which require potential victims to log in.
Those who proceed will have their username, password, and phone number stolen but won’t realize they were duped right away. Indeed, this phishing scam ends on a tricky note with a decoy document on wealth management from Wells Fargo.
Private message
This message was received from a trusted and existing contact, although the time stamp is showing 12:17 AM, which is perhaps one of the red flags to be noted. The message talks about a shared Google Doc and gives a link to it, via the Ow.ly URL shortener.
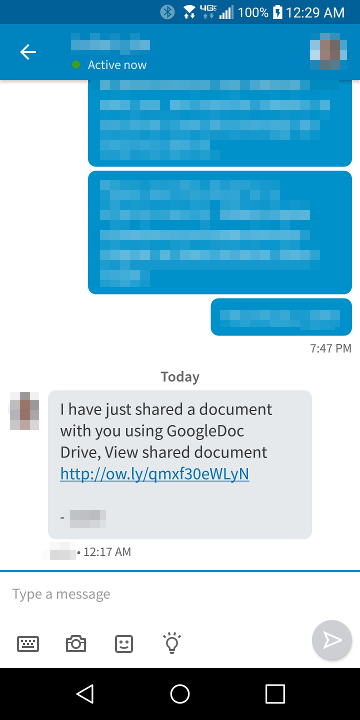
Figure 1: An instant message from a contact directing to a phishing scam
Behind the shortened URL redirection
URL shorteners are a well-known vehicle for spreading malware and phishing scams but they are also used for legitimate purposes, especially on social media where long URLs tend to be too cumbersome. In this attack, the perpetrators are abusing both ow.ly and a free hosting provider (gdk.mx) to redirect to the phishing page, itself hosted on a hacked website.
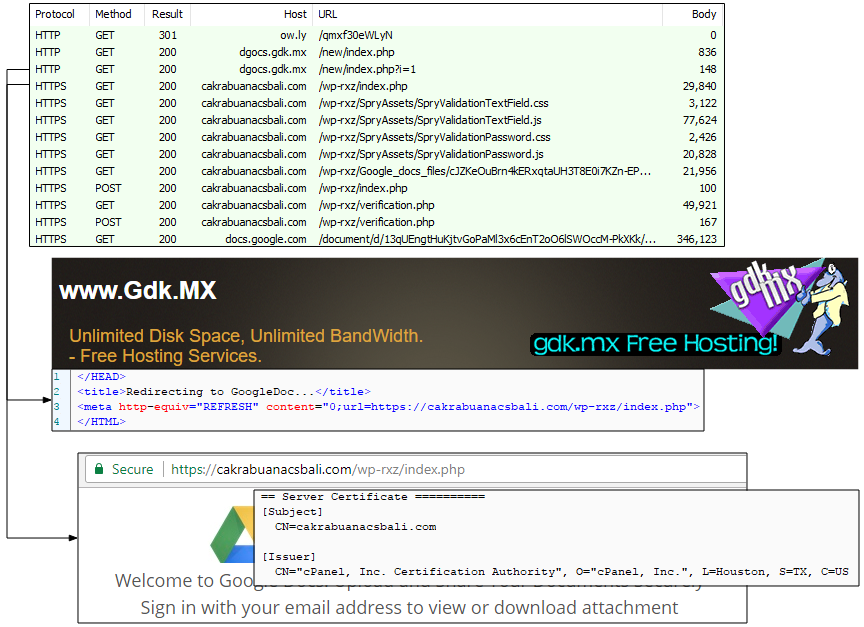
Figure 2: The redirection flow behind this phish
Phishing for email credentials
This particular page is built as a Gmail phish, but will also ask for Yahoo or AOL user names and passwords. The main page is followed by an additional request for a phone number or secondary email address and ultimately the user sees a decoy Wells Fargo document hosted on Google Docs.
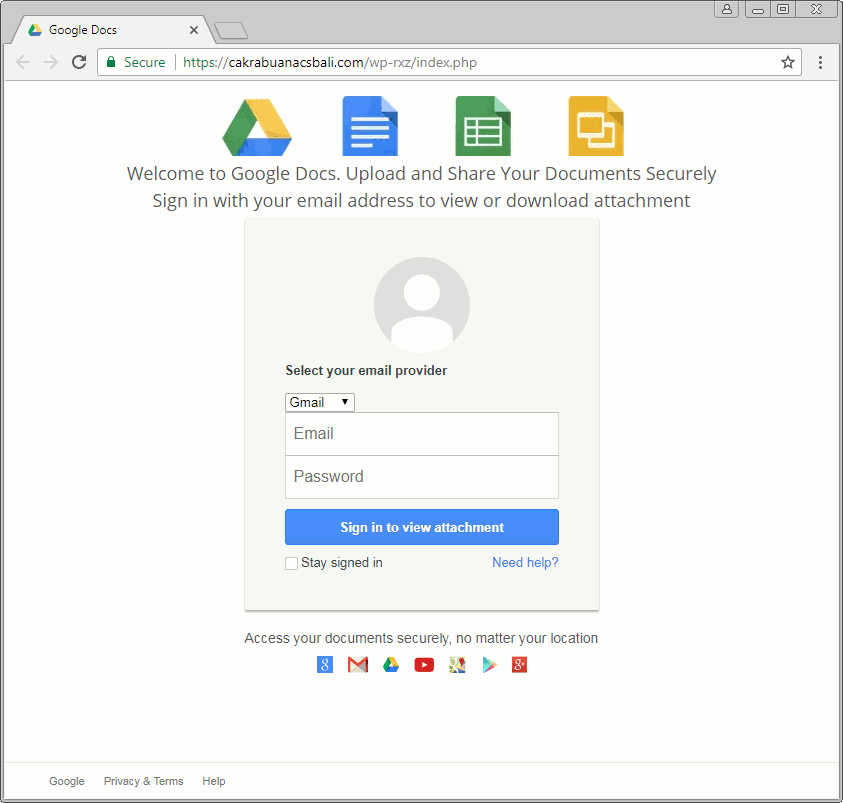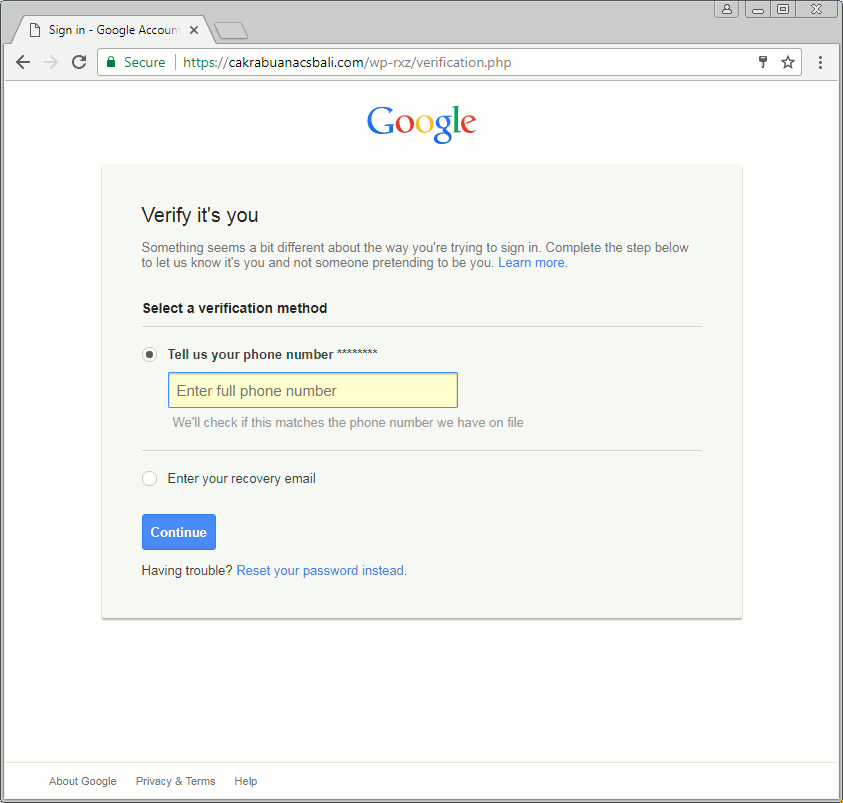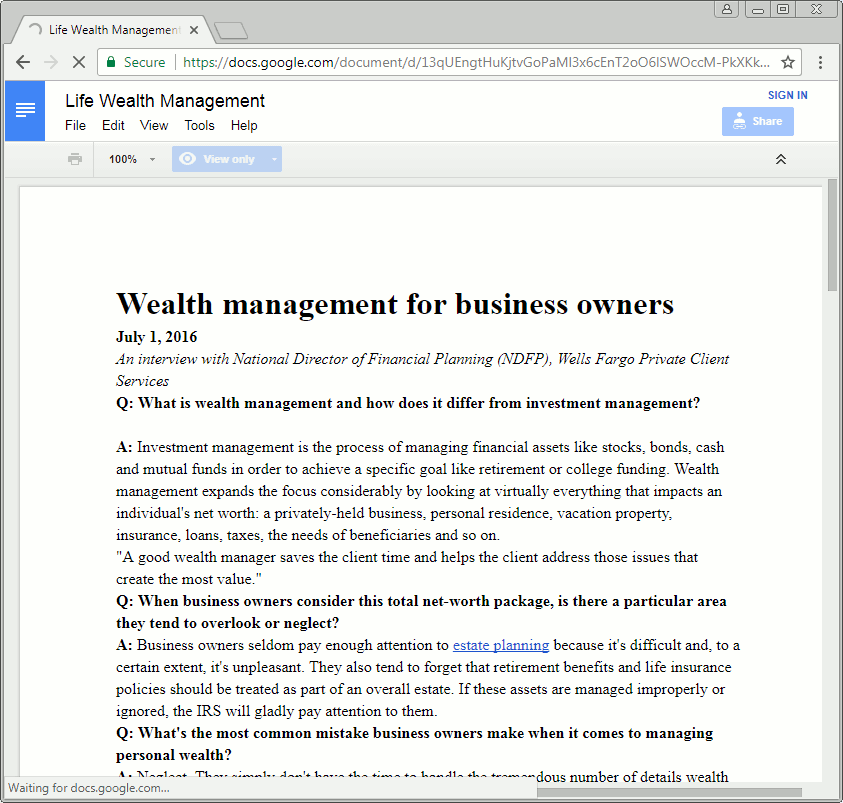
Figure 3: The phishing template, harvesting credentials and showing decoy content
InMail
Attackers are also abusing LinkedIn’s trusted InMail feature to send the same phishing link. As per LinkedIn, “InMail messages are sent directly to another LinkedIn member you’re not connected to.” This is an interesting aspect since it opens up the scope of the attack not only to the compromised account’s own contacts but also to other users.
This email was sent via LinkedIn and had a custom ‘Security Footer‘. LinkedIn will send messages “that include a security footer message with your name and professional headline to help you distinguish authentic LinkedIn emails from “phishing” email messages“, although it does point it out that it is no guarantee that the email is legitimate. In other words, the delivery method is to be trusted, but the content may not. The same can be said for phishing pages that use HTTPS – which is the case here – making content delivery secure but the content itself fraudulent.
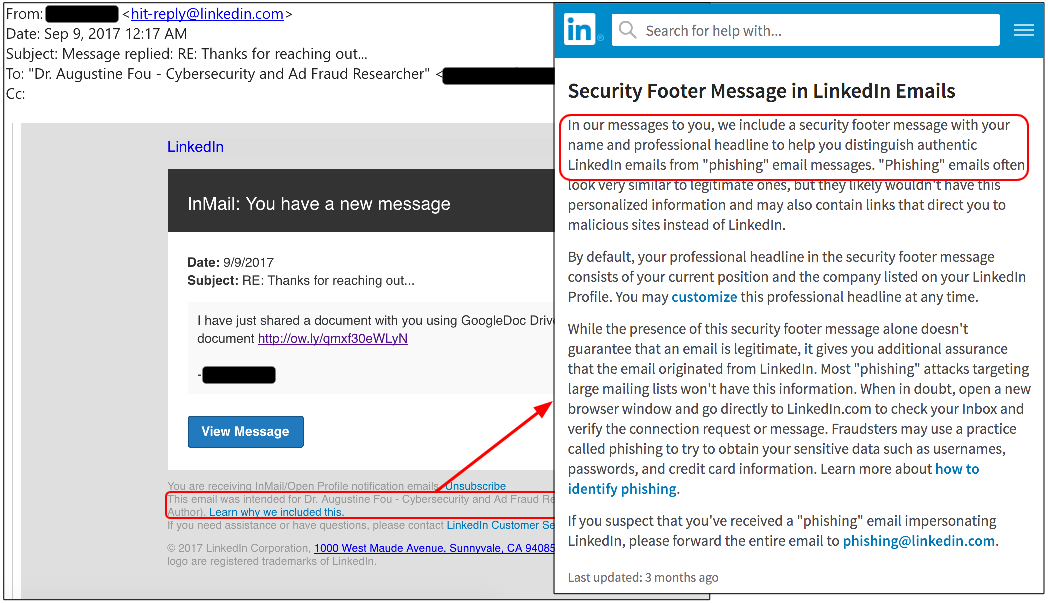
Figure 4: The phishing email received via LinkedIn that includes the ‘Security Footer’
However, there’s a caveat here. To use InMail, you need a Premium account which comes at a hefty monthly cost. There’s a good article by KnowBe4 detailing a phishing attack using LinkedIn’s own platform via InMail. The researchers showed how trivial it is to create a free account, start connecting with people, and finally upgrade to a Premium account in order to start sending scams via InMail. But the conclusion of their research is that this particular attack would not scale well due to limited InMail credits, making the operation way too expensive.
This limitation does not apply here though since the crooks are not creating (and paying for) their own accounts, but rather leveraging existing ones. Therefore, they have little to worry about burning free credits and tarnishing their victim’s reputation so long as it allows them to deliver their payload far and wide.
Personal security and its implications
We do not know how (malware, other phishing attacks, etc.) or how many LinkedIn accounts were compromised in this campaign. It’s also unclear whether the shortened URLs are unique per hacked account or not, although we think they might be. The user whose account was hacked had over 500 connections on LinkedIn and based on Hootsuite‘s stats, we know 256 people clicked on the phishing link.
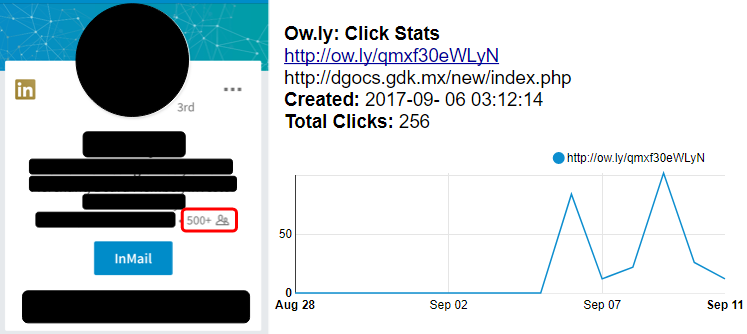
Figure 5: A Premium member account with 500+ connections caught sending phishing link
This kind of attack via social media is not new – we have seen hacked Skype or Facebook accounts send spam – but it reminds us of how much more difficult it is to block malicious activity when it comes from long standing and trusted user accounts, not to mention work acquaintances or relatives. This also makes such attacks more credible to potential victims and can lead to a snowball effect when victims become purveyors of phishing links themselves.
If your LinkedIn account gets compromised, you should immediately review its settings to change your password and enable two-step verification (instructions here). Additionally, you can post a quick update on your timeline that lets your contacts know you were hacked and that any previous message you may have sent with links should be carefully vetted.
We’d like to thank @acfou for sharing a sample of this campaign with us.
Indicators of compromise
Phishing message:
I have just shared a document with you using GoogleDoc Drive, View shared document http://ow.ly/[]
Redirection and phishing page:
ow[.]ly/qmxf30eWLyN dgocs[.]gdk.mx/new/index.php dgocs[.]gdk.mx/new/index.php?i=1 cakrabuanacsbali[.]com/wp-rxz/index.php
Decoy Google Docs Wells Fargo file:
docs.google.com/document/d/13qUEngtHuKjtvGoPaMl3x6cEnT2oO6lSWOccM-PkXKk/edit










