Update (9/19/2017):
Avast posted a clarification explaining what happened and giving a timeline of the events. One point we should take note of is that the breach preceded the take-over of Piriform by Avast.
Users that are unsure whether they were affected by this and whether their data may have been sent to the C2 server can check for the presence of the following values under the registry key:
HKEY_LOCAL_MACHINESOFTWAREPiriformAgomo
The values in question are: MUID, TCID and NID
These values are not created by any clean versions of CCleaner, just by the infected ones.
Malwarebytes will detect the presence of those values and flag them as Trojan.Floxif.Trace
The trojan itself reportedly only ran on Windows 32 bit systems, but the values above were created on 64 bit systems as well.
Original post:
In a supply chain attack that may be unprecedented in the number of downloads, servers hosting CCleaner, a popular tool for cleaning up the PC, has been delivering a version of the said software with malware.
What happened?
Threat actors have managed to change the files that were being delivered by Avast servers hosting CCleaner updates. In case you are wondering why they were on those servers, Avast acquired Piriform, the original publishers of CCleaner, a few months ago.
The incident was discovered and reported by Talos. Piriform is aware of the situation and is acting to prevent further damage. They are also investigating how the files coming from their servers were modified before being released to the public.
Possible impact
It is difficult to say at this moment how many users might have been affected, but the numbers could be huge. From the statistics brought out by Piriform, CCleaner has been downloaded 2 billion times in total, 5 million times every week. The modified version, 5.33, is made available from August 15 until September 12 when version 5.34 was released. In aThe malware The malware collects the following information about the infected system:
- Computer name
- A list of installed software, including Windows updates
- A list of the currently running processes
- The MAC addresses of the first three network adapters
- Other system information that is relevant for the malware like admin privileges, whether it is a 64-bit system, etc.
The malware uses a hardcoded C2 server and a domain generating algorithm (DGA) as a backup, to send information about the affected system and fetch the final payload.”>
What to do if you think you are affected?
First of all, check the version of CCleaner on your system. If you suspect you may have downloaded CCleaner version 5.33.6162 or CCleaner Cloud version 1.07.3191, scan your system for malware.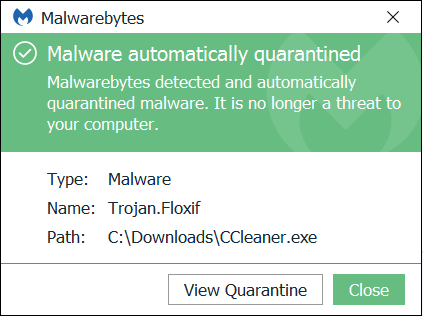
CCleaner users that are running older versions or that do not trust the one they are using now are encouraged to update their CCleaner software to version 5.34 or higher. The latest version is available for download here.
Affected versions: CCleaner version 5.33.6162 and CCleaner Cloud version 1.07.3191
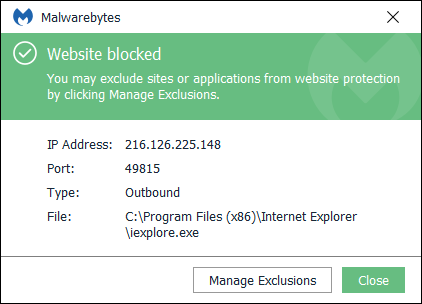
Malwarebytes blocks the IP and domains related to this malware. We also remove the malicious installer.
Stay safe!
Pieter Arntz
![[Updated] Infected CCleaner downloads from official servers](https://www.malwarebytes.com/wp-content/uploads/sites/2/2017/09/ccleanerlogo.png?w=300)










