A large number of publishers – big and small – are monetizing their sites by selling space for companies that provide so-called native advertising, cited as more effective and engaging than traditional banner ads.
Indeed, on a news or entertainment site, users are more inclined to click on links and articles thinking that they are one and the same, not realizing that those are actually ‘sponsored’ and tied to various third-party providers.
Rogue advertisers have realized this unique opportunity to redirect genuine traffic towards their own infrastructure where they can subject their audience to whatever content they wish.
Case in point, we caught this malvertising incident on MSN.com, the Microsoft web portal that attracts millions of unique visitors. While clicking on a story promoted by Taboola – a “leading global discovery platform” which Microsoft signed a deal with in 2016 – we were redirected to a tech support scam page. The warning claims that our computer has crashed and that we must call a number for immediate assistance.
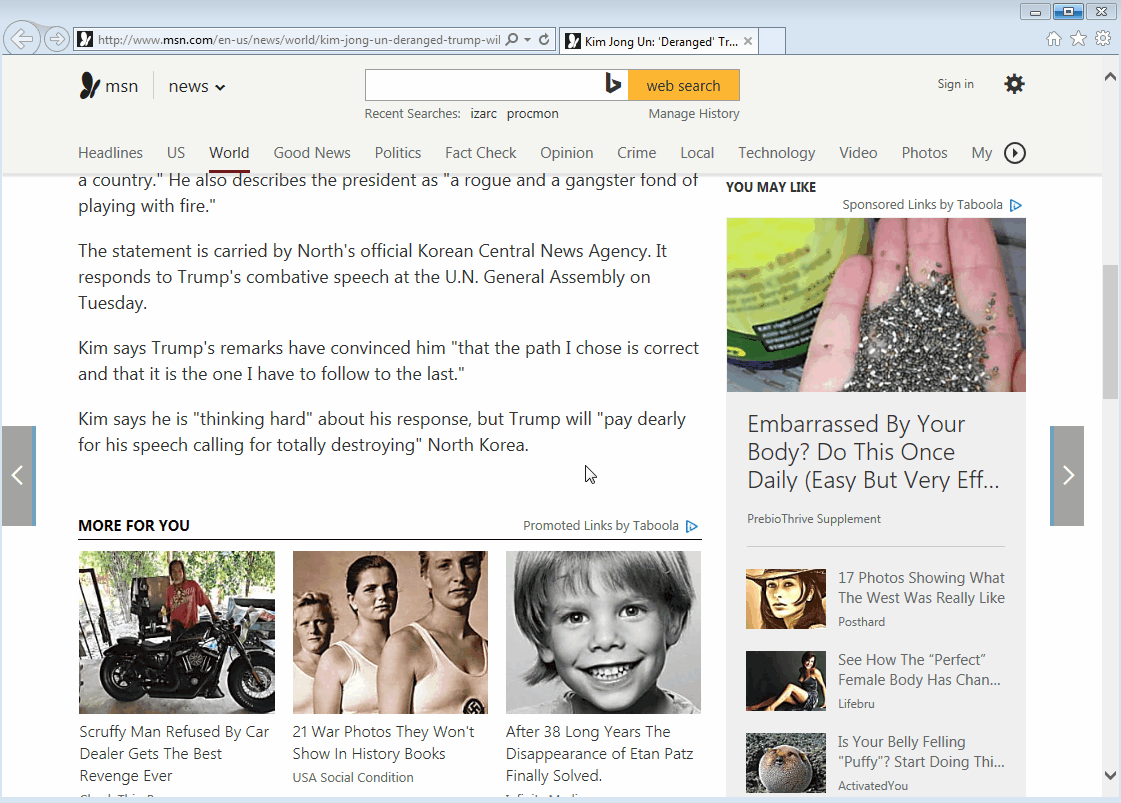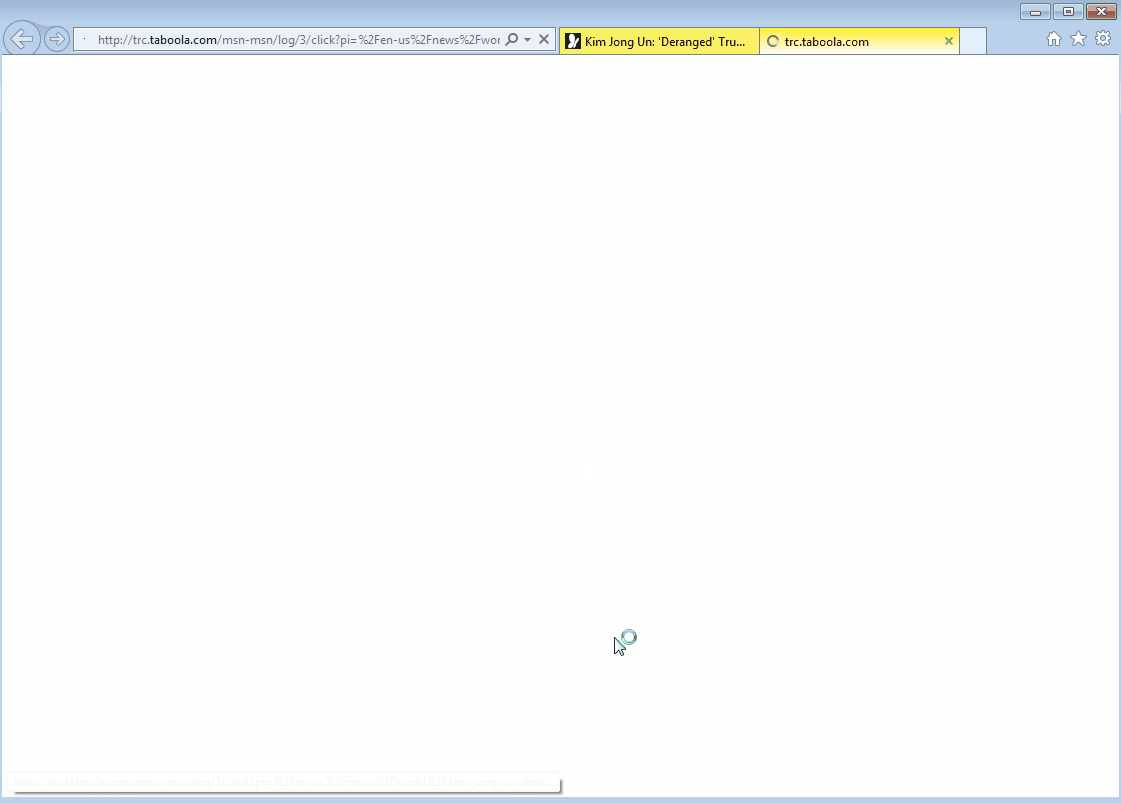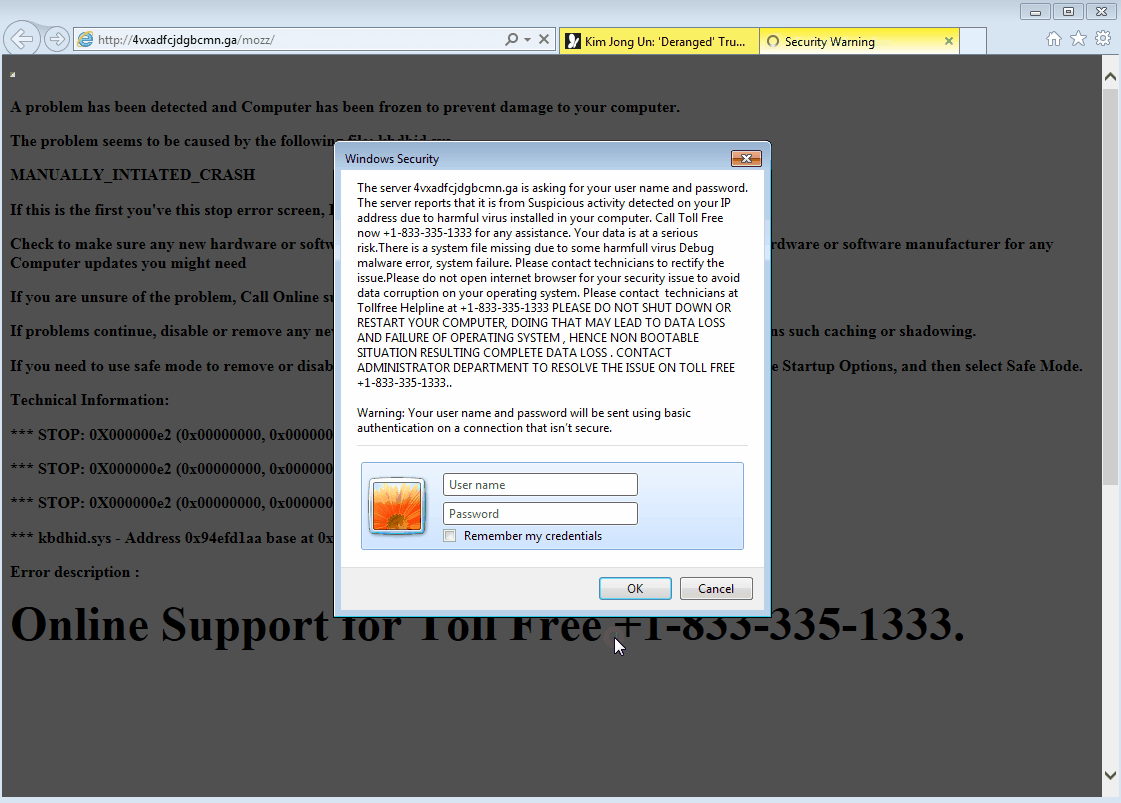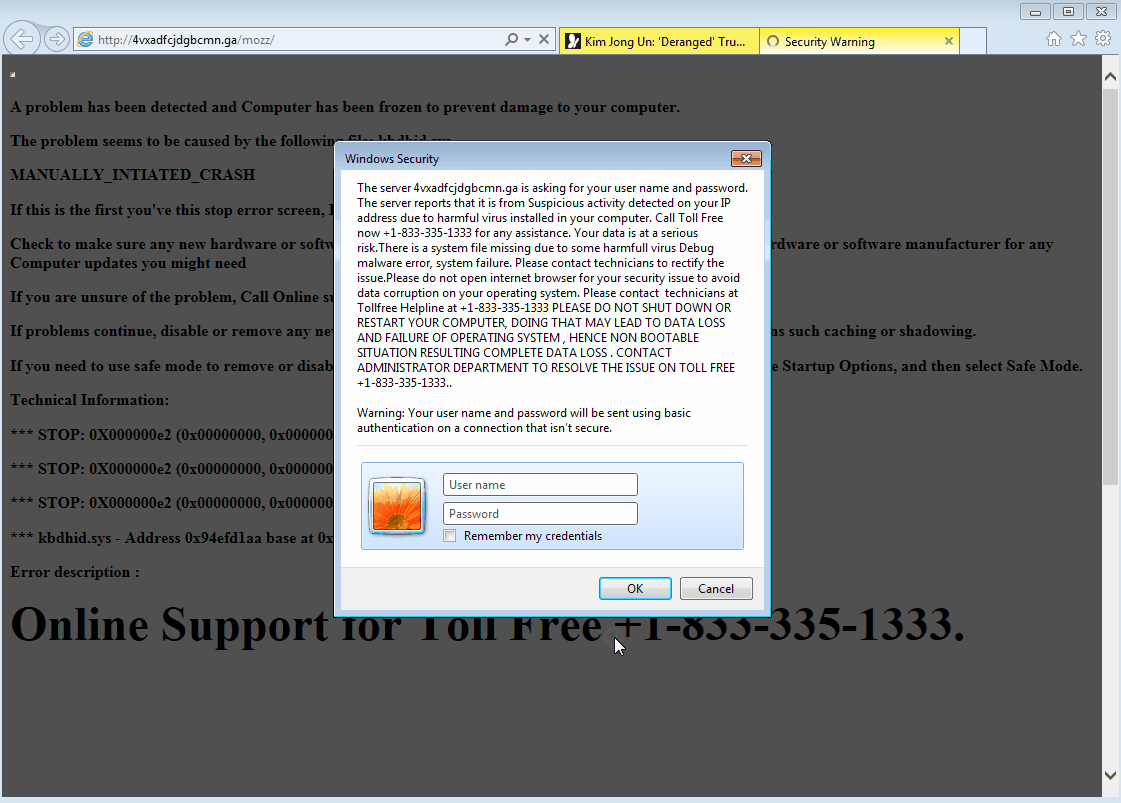
Figure 1: Automatic redirection from click on promoted story to scam page
The fraudulent page cannot be closed normally because it uses code that repeats the warning indefinitely. Unfortunately, this is enough to scare many folks and trick them into calling what they think is Microsoft support. Instead, they will be dealing with fake technicians whose goal is to extort hundreds of dollars from them.
Decoy news page hides real intentions
Rogue actors typically start creating content just like any other advertiser would and build up a profile. After all, they want to appear genuine in order to game the system with ‘hot’ content.
What’s determined as hot can be derived from real or shocking news. The point is to do a little bit of market study on what the most searched for stories or keywords are in order to attract traffic.
In this malvertising example, if we review the sequence of events, we realize that the scammer created a bogus news site (infinitymedia[.]online) which does have actual content but is performing conditional redirects, also known as ‘cloaking’.
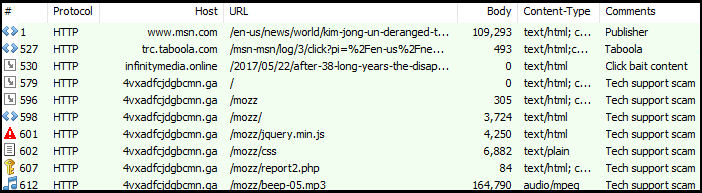
Figure 2: Traffic view showing temporary hop via decoy news site
A conditional redirect is usually a server-side mechanism that profiles the user and returns a particular response. For instance, if the server determines that a bot or crawler is making a request, it may in turn either deny it or simply serve the expected content (decoy). Similarly, if the user is running Internet Explorer, is from North America and their IP address appears to have hit the server for the first time, they may receive a scammy page instead.
The point is that it’s trivial to play a Dr. Jekyll and Mr. Hyde kind of game and serve the content you want. The fraudulent advertiser did create various pages with impactful keywords (potentially for Search Engine Optimization purposes) and can also use those stories as a decoy:
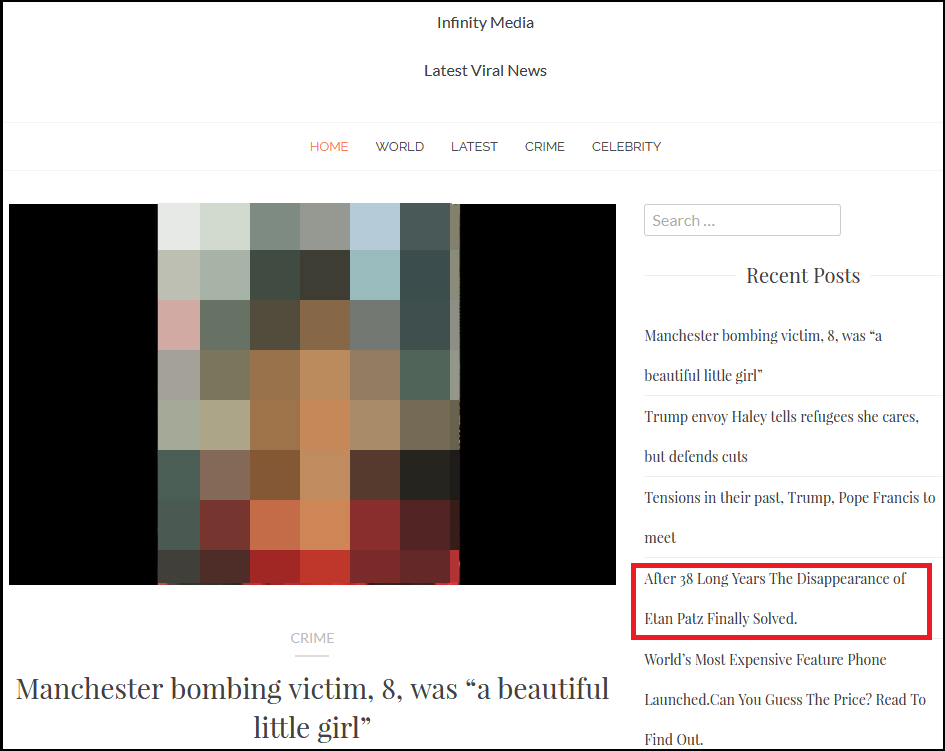
Figure 3: Stories designed for click-bait
To get back to this malvertising incident on MSN, the user was conditionally redirected to another site (the tech support scam page), and never saw the content they were looking for.
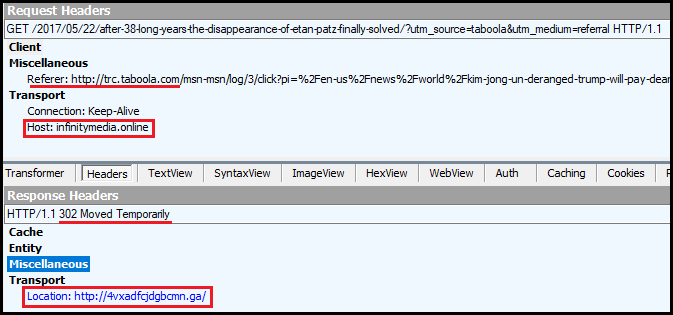
Figure 4: The 302 redirect call from the fake news site to the scam page“>
To show that this was no mere ‘coincidence’, we can look at the ownership of the ‘news’ site (infinitymedia[.]online) and see how it links to the tech support domain name (4vxadfcjdgbcmn[.]ga). A WHOIS lookup for infinitymedia[.]online returns the following information:
Domain Name: INFINITYMEDIA.ONLINE Creation Date: 2017-05-23T05:14:50.0Z Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com Registrant Name: bhanu Registrant Country: IN Registrant Email: bhanutomar90nk@gmail.com
Still, we don’t have a clear connection to 4vxadfcjdgbcmn[.]ga which does not have an identifiable registrant. Indeed, the .GA Top Level Domain (TLD) is comprised of free domain names and their registrant is… Gabon TLD B.V.
However, this particular actor made the mistake of reusing the same host server for domains he had created before. For example, if we take micro-soft-system-alert2[.]online which is registered to his email address, we notice that it resolves to 108.167.146.132, a server full of tech support scams and phishing sites, including the one used in this particular malvertising attack, namely 4vxadfcjdgbcmn[.]ga.
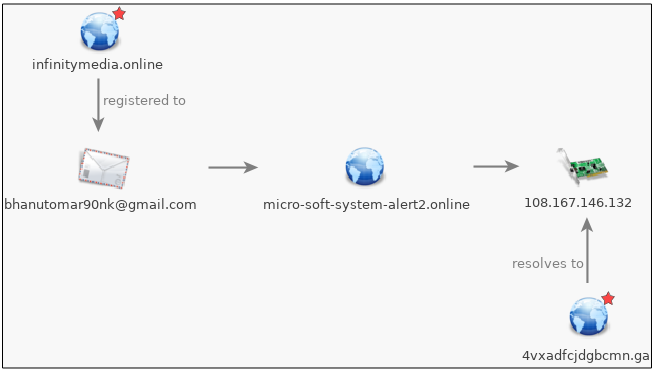
Figure 6: Connecting the fake news sites to the tech support domain
This actor is deeply involved in tech support scams:
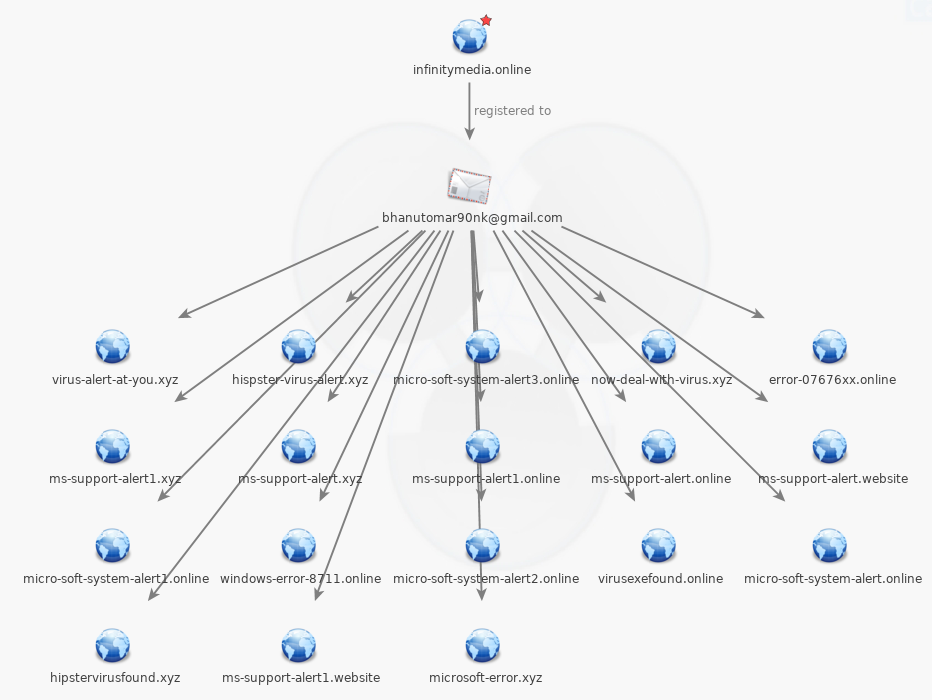
Figure 6: Tech support domains tied to that email address
Further inspection of other properties linked to bhanutomar90nk@gmail.com shows similar clickbait sites:
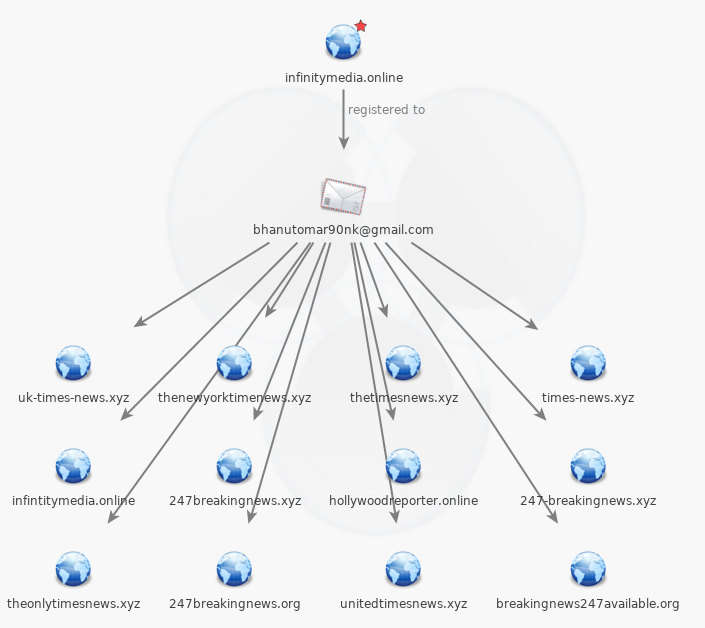
Figure 7: News or fake news?
There is no doubt that this actor has very clear intentions and has turned high-profile stories into a click-bait lead generation tool for tech support scams.
Banner ads versus native advertising
Banner ads can load third-party tags that are laced with malicious content, not to mention promoting anything that is outrageous (regardless of whether it has anything to do with the current content) and is bound to get clicks. For instance, there have been many documented instances of fake celebrity deaths used for click bait purposes on Facebook.
But promoted stories aren’t necessarily that different (or safer) when they take the user to a third-party website that is in the complete control of an advertiser, good or bad.
Users should be aware that even on a trusted platform, they should watch what they click on and be careful of sensationalist stories that may be used as click bait.
We reported the fraudulent advertiser to Taboola which told us they had opened an internal review of this particular vendor. We reached back with more questions regarding how Taboola deals with click bait and fake news, whether they scan articles for malware or scams, and finally if they had a direct point of contact to report security-related issues.
Update (10/03/2017) You can find Taboola’s answers below.
Q: Due to the prevalence of click-bait and fake news articles these days, how does Taboola validate the content provided by its advertising partners?
A: We take fake news, advertiser fraud and user security extremely seriously, and we invest significant resources in constantly monitoring the content on our ever-expanding network. Moreover, when we discover a fraudulent incident such as the one you flagged to us, we investigate and take action immediately. The item you flagged received very limited scale on our network and was disabled and removed from the network as soon as we got the notification. This particular advertiser used cloaking, which means they went through our processes adhering to our policies, but then in the backend redirected the user to something we didn’t approve. This advertiser was immediately banned from our network and will not be allowed to work with us again.
Q: Does Taboola actively scan links to third-party content stories for malware, phishing or scams in general?
A: Yes. As you mentioned in your article, cloaking is an industry-wide threat (Facebook addressed it recently in their blog post and also in this article) and we have dozens of people on our compliance team that are evaluating and categorizing the content running on Taboola. As you are very well aware, one challenge we have that there is a delicate balance that we and other technology companies face: on the one hand, we want to share our best practices of how to combat these bad actors who are using cloaking, phishing, and other methods. However, we’re also concerned about sharing too much, so as not to fuel these bad actors with additional knowledge on how to circumvent our protections. We do share a public policy that makes it clear what we allow, and do not allow, as well as we participate in many panels and are members of the NAI, who are members of the Coalition of Better Ads and there are many initiatives we work on with other companies, but we cannot share the details for the reasons mentioned previously. While we work with tens of thousands of companies, these incidents are a very rare occurrence and we do a good job protecting our publishers and advertiser partners and their audiences. When there is an incident, what is important is how fast you take care of it. For that, you need to be open to anyone that can help you find out about a bad actor, such as bloggers, users on social, reporters, our partners and of course our own internal staff.
Q: While reporting the issue, we first received a response that stated: “While we can’t fulfill every single request (after all, we are serving over 400M users every month), we promise to do our absolute best!” Is there a way for security firms and consumers to report security related issues that will get prioritized?
A: That response you quoted above sent via a contact-us form was not an appropriate answer to your email, and we apologize for that. Our Support team works 24/7 across the globe and they always prioritise security related threats and escalate them when required. It’s best to contact support@taboola.com and our team will make sure the relevant teams are addressing the issue promptly.










