Ever wondered why websites that are mining in the background don’t mine for the immensely hot Bitcoin, but for Monero instead? We can explain that. As there are different types of cryptocurrencies, there are also different types of mining. After providing you with some background information about blockchain [1],[2] and cryptocurrency, we’ll explain how the mining aspect of Bitcoin works. And how others differ.
Proof-of-Work mining
Cryptocurrency miners are in a race to solve a mathematical puzzle, and the first one to solve it (and get it approved by the nodes) gets the reward. This method of mining is called the Proof-of-Work method. But what exactly is this mathematical puzzle? And what does the Proof-of-Work method involve? To explain this, we need to show you which stages are involved in the mining process:
- Verify if transactions are valid. Transactions contain the following information: source, amount, destination, and signature.
- Bundle the valid transactions in a block.
- Get the hash that was assigned to the previous block.
- Solve the Proof-of-Work problem (see below for details).
The Proof-of-Work problem is as follows: the miners look for a SHA 256 hash that has to match a certain format (target value). The hash will be based on:
- The block number they are currently mining.
- The content of the block, which in Bitcoin is the set of valid transactions that were not in any of the former blocks.
- The hash of the previous block.
- The nonce, which is the variable part of the puzzle. The miners try different nonces to find one that results in a hash under the target value.
So, based on the information gathered and provided, the miners race against each other to try and find a nonce that results in a hash that matches the prescribed format. The target value is designed so that the estimated time for someone to mine a block successfully is around 10 minutes (at the moment).
If you look at BlockExplorer.com, for example, you will notice that every BlockHash is 256 hexadecimal digits long and starts with 18 zeroes. For example the BlockHash for Block #497542 equals 00000000000000000088cece59872a04457d0b613fe1d119d9467062e57987f1. At the time of writing, this is the target—the value of the hash has to be so low that the first 18 digits are zeroes. So, basically, miners have some fixed input and start trying different nonces (which must be an integer), and then calculate whether the resulting hash is under the target value.

How is Monero different?
Browser mining and other methods of using your system’s resources for other people’s gain is usually done using other cryptocurrencies besides Bitcoin, and Monero is the most common one. In essence, Monero mining is not all that different from Bitcoin. It also uses the Proof-of-Work method. Yet, Monero is a popular cryptocurrency to those that mine behind the scenes, and we’ll explain why.Anonymity
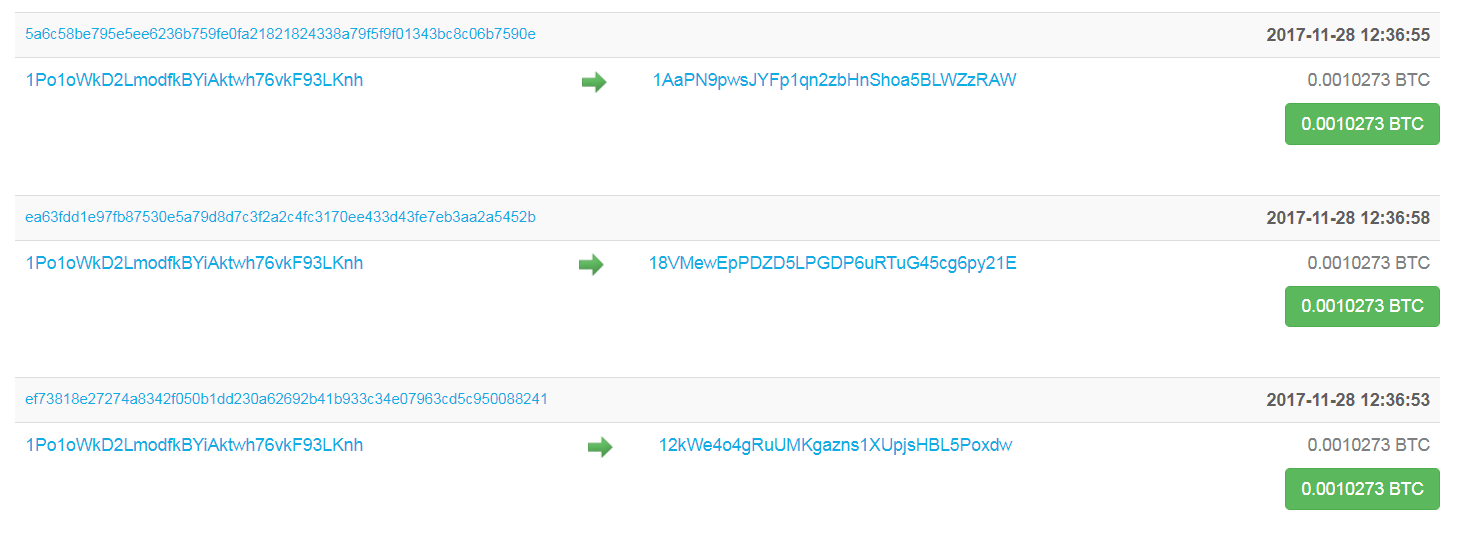
The most notable difference between Bitcoin and Monero mining is anonymity. Where you will hear people say that Bitcoins are anonymous, you should realize that this is not by design. If you look at a site likeTherefore we call Bitcoin “pseudononymous.” This means you may or may not know the name of that person, but you can track every payment to and from his address if you want. There are ways to obfuscate your traffic, but they are difficult, costly, and time-consuming.
Monero however, has always-on privacy features applied to its transactions. When someone sends you Monero, you can’t tell who sent it to you. And when you send Monero to someone else, the recipient won’t know it was you unless you tell them. And because you don’t know their wallet address and you can’t backtrack their transactions, you can’t find out how “rich” they are.
Transactions inside a Bitcoin block are an open book.
Mining
Monero mining does not depend on heavily specialized, application-specific integrated circuits (ASICs), but can be done with any CPU or GPU. Without ASICs, it is almost pointless for an ordinary computer to participate in the mining process for Bitcoin. The Monero mining algorithm does not favor ASICs, because it was designed to attract more “little” nodes rather than rely on a few farms and mining pools.
There are more differences that lend themselves to Monero’s popularity among behind-the-scenes miners, like the adaptable block size, which means your transactions do not have to wait until they fit into a later block. The Bitcoin main-stream blockchain has a 1 MB block cap, where Monero blocks do not have a size limit. So Bitcoin transactions will sometimes have to wait longer, especially when the transaction fees are low.
The advantages of Monero over Bitcoin for threat actors or website owners are mainly that:
- It’s untraceable.
- It can make faster transactions (especially when they are small).
- It can use “normal” computers effectively for mining
Links
For those of you looking for more information on the technical aspects of this subject, we recommend: