CES, the annual consumer electronics extravaganza in Las Vegas, isn’t just a showcase for virtual reality and poorly-timed power outages. It’s also an opportunity to get a peek at the future of network security.
That’s why on the first day of CES, the Wi-Fi Alliance announced the newest security protocol for Wi-Fi devices: WPA3. The new protocol is the most significant upgrade to Wi-Fi security since WPA2 was ratified in 2004.
Details are thin, but the announcement outlined four new security capabilities that will protect wireless connections in the years to come.
1. Protection against brute force “dictionary” attacks
Despite a generation of irritated admins requesting that users choose stronger passwords, the most popular passwords are still common words like “password” or “football.” That makes networks vulnerable to simple brute force attacks that systematically submit every word in the dictionary as a password. Online tutorials of this Wi-Fi hack are trivially easy to find.
WPA3 should make that issue a thing of the past by “delivering robust protections even when users choose passwords that fall short of typical complexity recommendations.” Some security experts have speculated that this refers to a type of key exchange called Dragonfly. According to the Internet Engineering Task Force (IETF), Dragonfly “employs discrete logarithm cryptography to perform an efficient exchange in a way that performs mutual authentication using a password that is probably resistant to an offline dictionary attack.”
2. Easier Internet of Things (IoT) security
WPA3 promises to “simplify the process of configuring security for devices that have limited or no display interface.” That’s a nod to the growing number of devices that are enhanced by network connections, such as smart door locks, home personal assistants, and (apparently) toothbrushes. Since IoT devices rarely have a graphical interface, it’s difficult to configure them for optimal security. You can’t type a password directly on a toothbrush, after all. This can naturally lead to less secure connections and vulnerable devices. Hackers could, for example, access your smart speakers and play whatever audio they want in your living room.
The Wi-Fi Alliance hasn’t yet offered details on how WPA3 overcomes this challenge. But researchers have successfully enhanced security on IoT devices by configuring them with a smartphone.
3. Stronger encryption
WPA2 requires a 64-bit or 128-bit encryption key. But WPA3 uses a stronger standard: 192-bit encryption and alignment with the Commercial National Security Algorithm (CNSA) Suite. This promises consumers the kind of beefier security that’s currently used to protect governments and corporations.
4. Secure public Wi-Fi
Public Wi-Fi connections, like the kind you might use in a coffee shop or library, are always less secure than private ones. That’s partly due to the inherent security limitations of open wireless networks, and party due to the fact that librarians and coffee shop owners aren’t typically network security masters. The new standards promise to “strengthen user privacy in open networks through individualized data encryption.” Though the announcement doesn’t offer specifics on how that will be achieved.
Curiously, during its CES announcement, the Wi-Fi Alliance made no mention of KRACK, the vulnerability in WPA2 that impacted all Wi-Fi devices. However, Mathy Vanhoef, the researcher who discovered the vulnerability, wrote several enthusiastic tweets about WPA3.
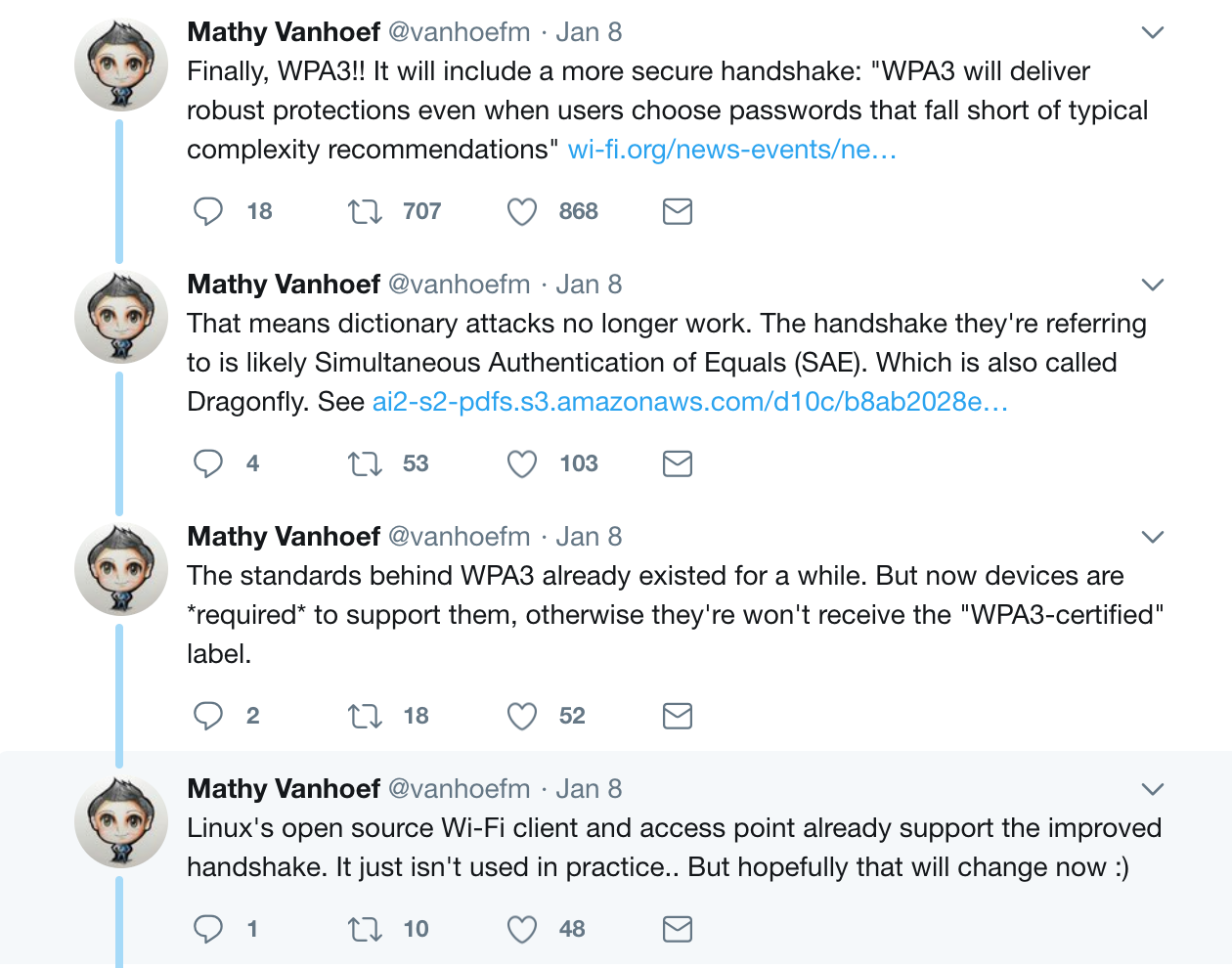
In one, he speculates that WPA3 will include Opportunistic Wireless Encryption. This enables connection on an open network without a shared and public Pre-Shared Key (PSK). That’s important because a PSK can give hackers easy access to the Traffic Encryption Keys (TEKs), thus allowing them access to a data stream. In other words, the new protocol should help prevent hackers from snooping on your web browsing while you’re at Starbucks.
Before we start to see the benefits of WPA3, the Wi-Fi Alliance has to certify hardware that uses the security protocol. So there’s no telling when people can start enjoying the enhanced security protections. But you shouldn’t be surprised if you start seeing devices that use the new protocol later this year.
Guest post by Logan Strain, author for Crimewire Father, writer, and reformed Usenet troll. Lives in San Diego. Doesn’t surf, but should learn. Follow Logan on Twitter @LM_Strain










