At Malwarebytes, we frequently examine apps for detection as Potentially Unwanted Programs (PUPs). These are programs that exhibit a wide variety of bad behaviors, but aren’t actually outright malware. Unfortunately, there are many supposed antivirus programs that fit this category.
Following user reports, we began researching a piece of software named CyberByte Antivirus to determine whether it was a PUP. In our initial research, we found that CyberByte met several aspects of our PUP detection criteria, and we made the decision to begin detecting it as such.
One of these violations was that CyberByte acts as a wrapper for the open-source ClamAV engine (which doesn’t have comprehensive Mac signatures in its database), because asking for payment for a free antivirus engine is a potential red flag. However, it appeared likely that they were using another engine in addition to ClamAV.
After further examination, we noticed that there was something awfully familiar about CyberByte’s scans—specifically, the names of the threats it was looking for as part of its “quick scan.”
Among antivirus companies, names of various threats tend to vary, sometimes quite widely. For example, something we call Adware.Crossrider might be called Trojan.Crossrider, OSX/adAgent, or Other:Malware-gen by other antivirus programs. In the case of CyberByte, the names we saw scrolling by during a scan were our own Malwarebytes detection names.
Anyone who has used Malwarebytes for Mac recently will probably have noticed that Trojan.SteamStealer.CSGO is the very first threat that it scans for. It seemed like an extremely unlikely coincidence that CyberByte’s “quick scan” started with exactly the same threat.
Trojan.SteamStealer.CSGO is not a name that is unique to Malwarebytes. However, as the scan progressed, it was easy to see a number of threat names that are not used by any other vendors besides Malwarebytes.
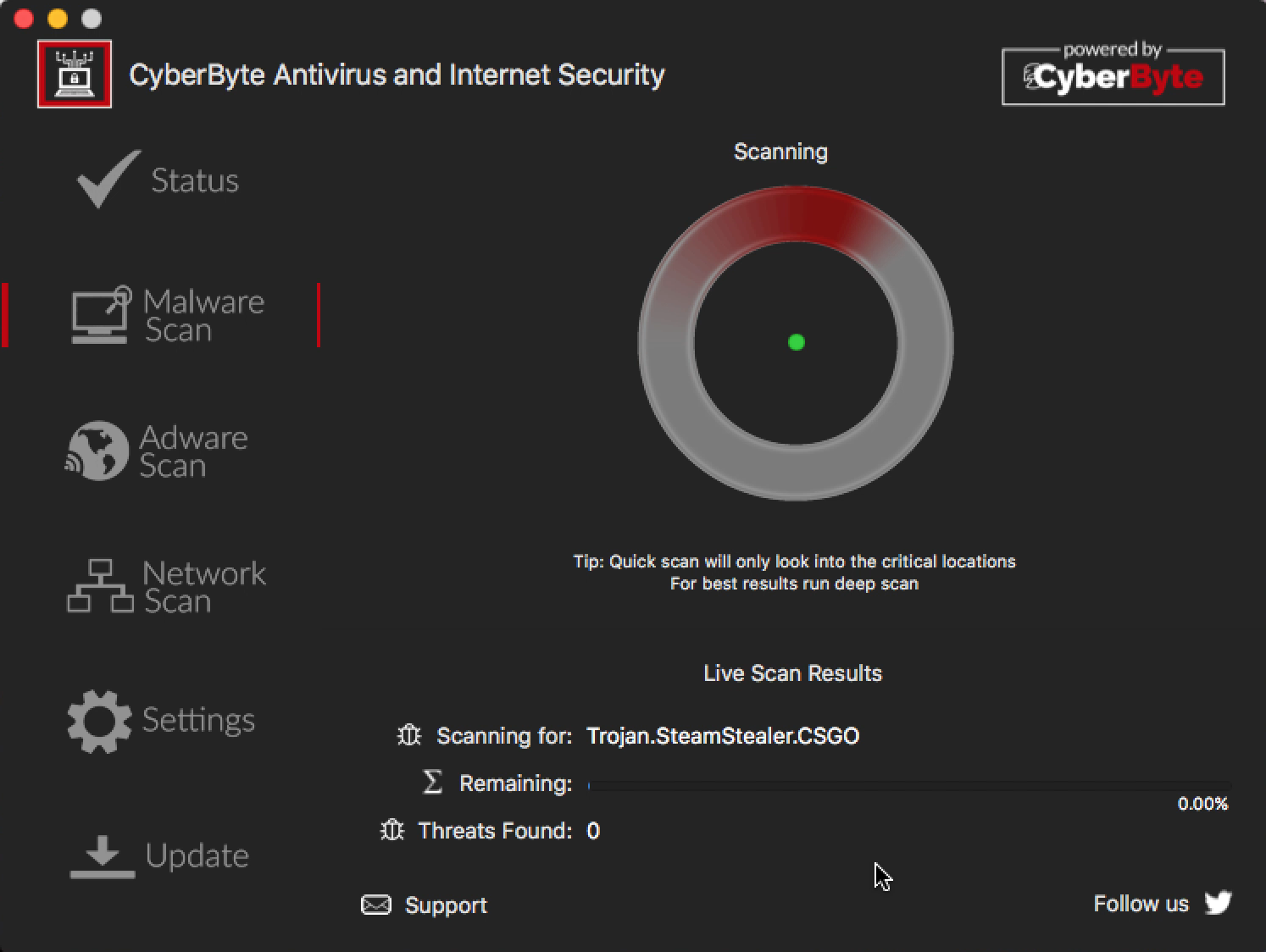
We immediately suspected that CyberByte had stolen our intellectual property to augment the ClamAV engine. However, it did not seem that they were able to entirely duplicate our scan engine, as the “quick scan” only detected a small fraction of the files that Malwarebytes did.
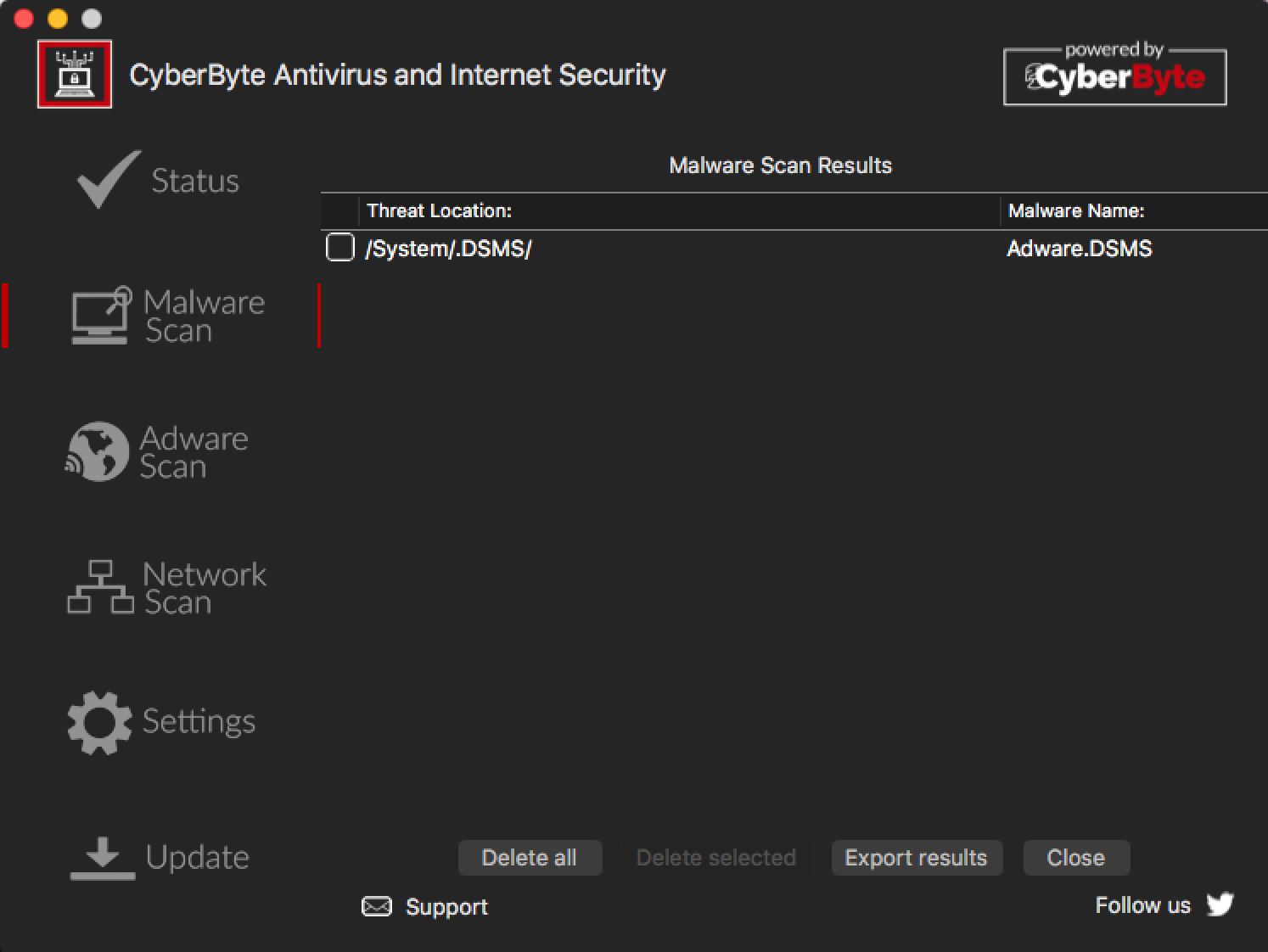
Further proof was needed, so we added a dummy rule to our detections last week. We added a rule that would detect a particular folder—one that should never exist, and that you’d have to jump through hoops to create on a modern Mac system—as “Adware.DSMS” (meaning, “Don’t Steal My Software”).
Monday morning, on a test system, we created the dummy folder, then installed and updated CyberByte on that system. After running a “quick scan” using CyberByte, we caught it detecting the dummy folder as Adware.DSMS, proving that this was not simply a one-time theft. CyberByte has clearly set up a system for the ongoing theft of our intellectual property.
This is not the first time scammers have stolen our intellectual property. Back in 2009, IOBit was caught similarly stealing our intellectual property. A program called Yet Another Cleaner did the same.
For this reason, we have changed our detection of CyberByte from PUP.CyberByte to OSX.FakeAV. We are taking actions to stop this infringement and protect our intellectual property.










