As if you haven’t heard it enough from us, the threat landscape is changing. It’s always changing, and usually not for the better.
The new malware we see being developed and deployed in the wild have features and techniques that allow them to go beyond what they were originally able to do, either for the purpose of additional infection or evasion of detection.
To that end, we decided to take a look at a few of these threats and pick apart what about them makes them difficult to detect, remaining just out of sight and able to silently spread across an organization.
Download: Under the Radar: The Future of Undetected Malware
We then examine what technologies are unprepared for these threats, which modern tech is actually effective against these new threats, and finally, where the evolution of these threats might eventually lead.
The threats we discuss:
While discussing these threats, we also look at where they are most commonly found in the US, APAC, and EMEA regions.
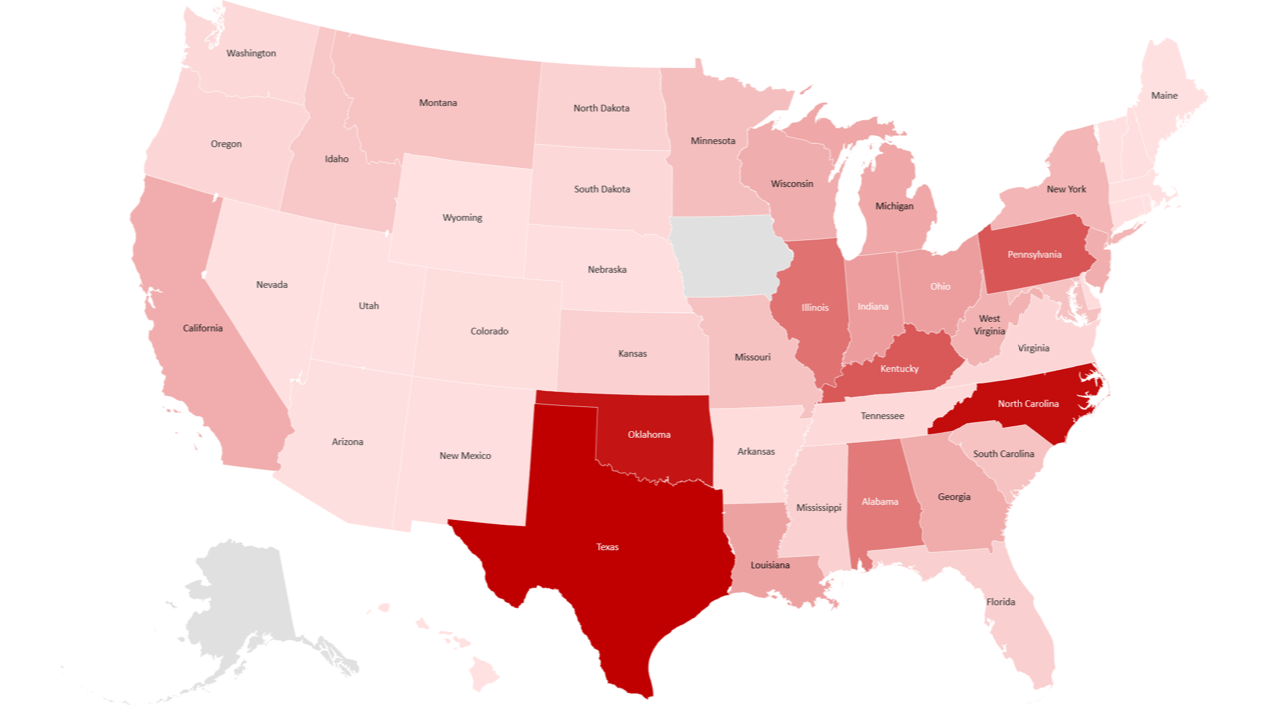
Emotet 2018 detections in the United States
In doing so, we discovered interesting trends that create new questions, some of which are clear and others that need more digging. Regardless, it is evident that these threats are not old hat, but rather making bigger and bigger splashes as the year goes on, in interesting and sometimes unexpected ways.
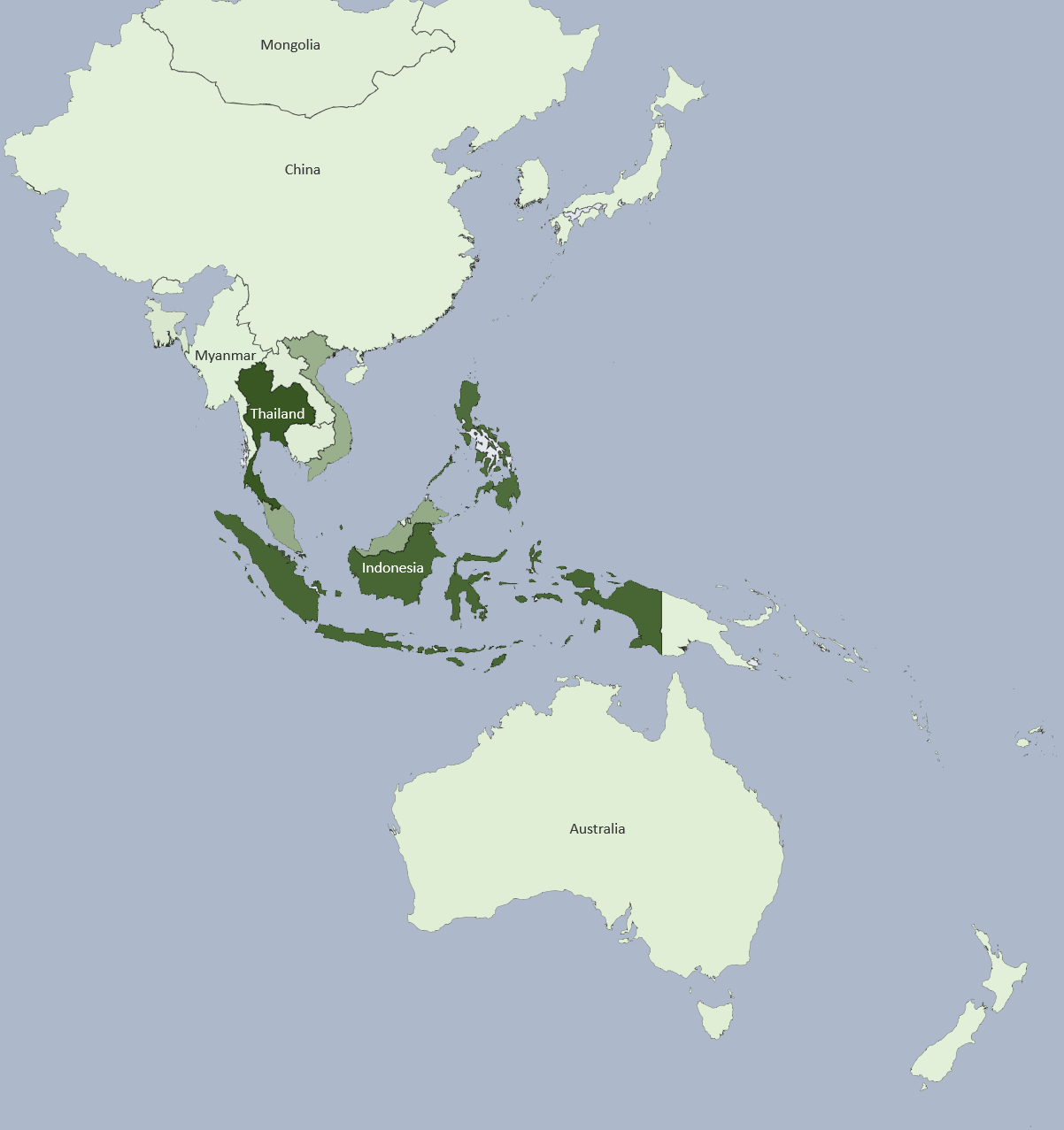
Though the spread and capabilities of future threats are unknown, we have to prepare people to protect their data and experiences online. Unfortunately, many older security solutions will not be able to combat future threats, let alone what is out there now.
Not all is bad news in security, though, as we do have a lot going for us as in technological developments and innovations in modern features. For example:
- Behavioral detection
- Blocking at delivery
- Self-defense modes
These features are effective at combating today’s threats and will soon be needed to build the basis for future developments, such as:
- Artificial Intelligence being used to develop, distribute, or control malware
- The continued development of fileless and “invisible” malware
- Businesses becoming worm food for future malware










