If you are in the United States, then you likely already know that we are on our 24th day of a government shutdown. While it is considered a “partial” shutdown, there are still plenty of government workers who are furloughed, which impacts the services they run—both online and off.
Last week, TechCrunch posted a concerning story about the shutdown, which covered the findings of NetCraft, a UK Internet service company, who discovered that numerous US government websites are now inaccessible due to expired security certificates.
This is a quick post to explain what happened, and more importantly, how cybercriminals will use this situation to their advantage.
Security certificates
We aren’t going to dig deep into how security certificates work for websites, but the gist is that every vendor or organization that uses a website requires a security certificate for users to access their site with trust. Today, a few browsers, like Chrome, require these certificates before they even let users access the websites. You can recognize when a website uses a valid security certificate, usually indicated by a green lock on the URL bar.
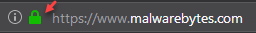
The certificate confirms that the identity of the website that you are communicating with is legitimate. In addition, these certificates make it possible for users to establish a secure connection with the web server hosting the site, which is incredibly important when sending financial or personal information over the Internet.
Since some of the most popular browsers won’t even let users visit a website if it doesn’t have a valid certificate, we now have a lot of users who can’t access government websites because the certificates have expired.
Why did they expire?
If a security certificate lasted forever, what would be the assurance that it hasn’t been stolen by criminals who could then use it on their own malicious websites? Because of this, the organization that owns the website must purchase and deploy a new certificate each year. Think of it as a yearly registration fee, not unlike renewing your car tags.
The reason these certificates were allowed to lapse is because no one’s at work renewing them. Apparently, most US government websites maintain their own certificates. This is why not all US .gov websites are down—just a few of them (at least for now). With the partial shutdown, the people in charge of making sure citizens can access their websites by keeping these certificates up-to-date are unable to do their jobs, which eventually leads to users being unable to access these sites at all.
What’s the problem?
Obviously, not being able to access some government websites is a pain, but is it dangerous? The answer is: yes, because you can bet that cybercriminals are going to take advantage of the situation.
That is why we want to share some vital warnings about how this shutdown may help cybercriminals. Please, share this with everyone you know, at least until the shutdown is over.
Cybercriminals frequently use real-world events to trick users into clicking on a link or opening an attachment. You can look back at a couple of instances where events in Syria directly influenced the actions of cybercriminals, be it state sponsored or otherwise. In another case, the Boston bombing was used to try and scam people. From terrorist attacks to natural disasters, threat actors jump on the chance to exploit episodes of fear and uncertainty.
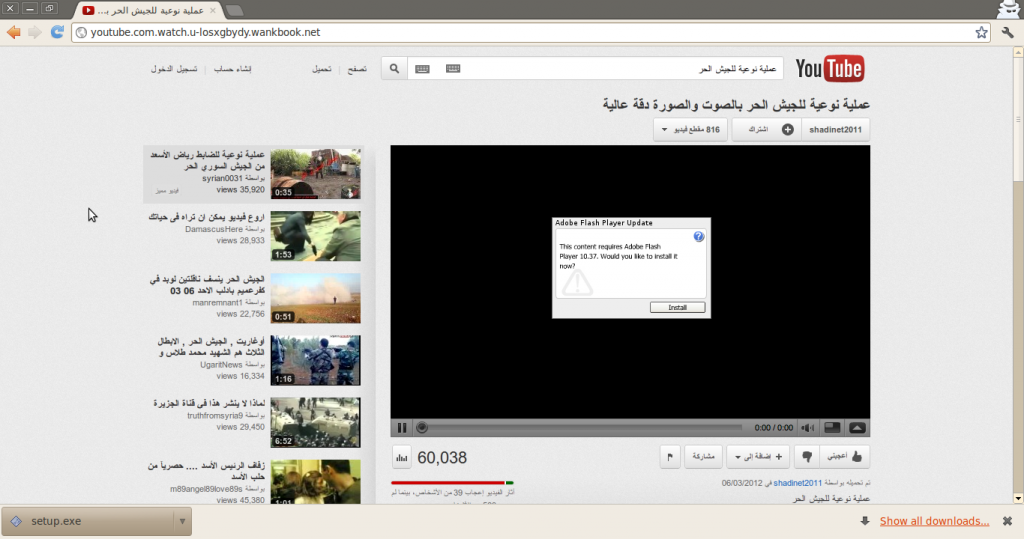
Fake YouTube page set up to infect Syrian rebels
You can expect that users who are looking for government websites, especially if they offer a service or require personal information or a login to access, are going to find copies of these sites presented as an alternative to access the same website.
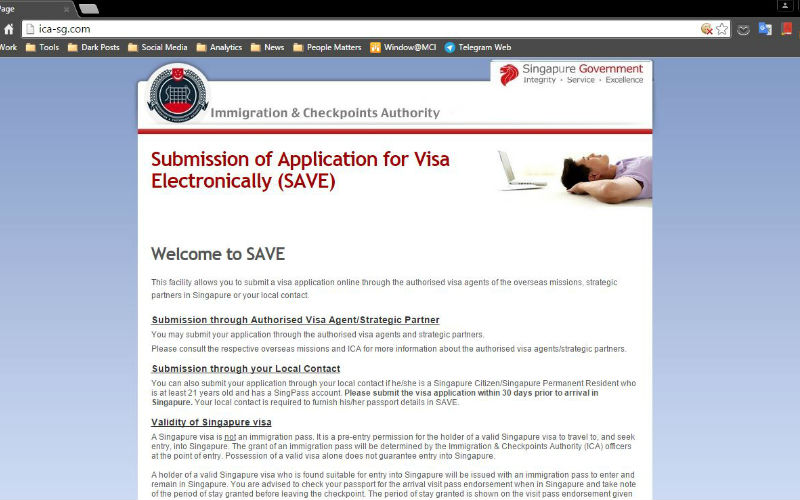
Fake Singapore government website. Photo credit: Gov.SG
Users who rely on social services—typically older folks, veterans, or the disabled—will be looking for a way to access the government sites they frequent. When they search for the site, their first link might take them to a dead end, since the security certificate has expired. However, the second or third link might work and take the user to a page that looks exactly like where they want to go.
Classic phishing attack.
What to do about it
The best thing to do right now is share this information with those closest to you so they don’t make a mistake and give away valuable personal info just because the government has issues keeping itself open. Also, be vigilant moving forward, not just in this case but anytime there is sensational news. Don’t just accept what the Internet tells you. Investigate. Think twice. And please, please, when in doubt, do not submit your personal information online.
The bad guys know human behavior, and they know that people can’t help clicking on links that are either convenient or scandalous and sensational. Prove them wrong.
Stay safe out there!











