Over the weekend, I received this unsolicited message from an acquaintance on Steam:
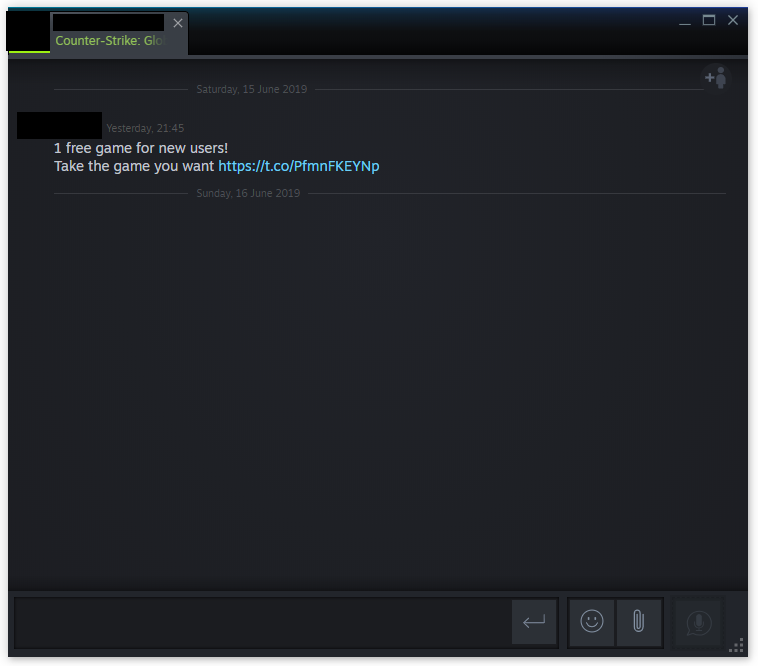
1 free game for new users!
Take the game you want https://t.co/{redacted}
Fortunately, other friends on Steam were quick to publicly warn others about potentially hacked accounts spamming dubious messages to anyone (if not all) in their network. I was reading these warnings hours before receiving a sample of the spam message to my own account.
A shallow online search reveals that this campaign has been going on since mid-March of this year. Because it’s quite low-profile, not a lot were able to dig deeper into it. We’ll attempt to do that here.
Latest Steam phishing campaign: a walk-through
Steam users were right to point out that this shortened URL indeed redirects to a phishing domain—but not at once.
Clicking the t.co link, which is a Twitter shortened URL, in the chat takes users to the site behind it: steamredirect[dot]fun. This is the re-director domain that takes users to the “proper” phishing page, which pretends to be a site where one can win free games.
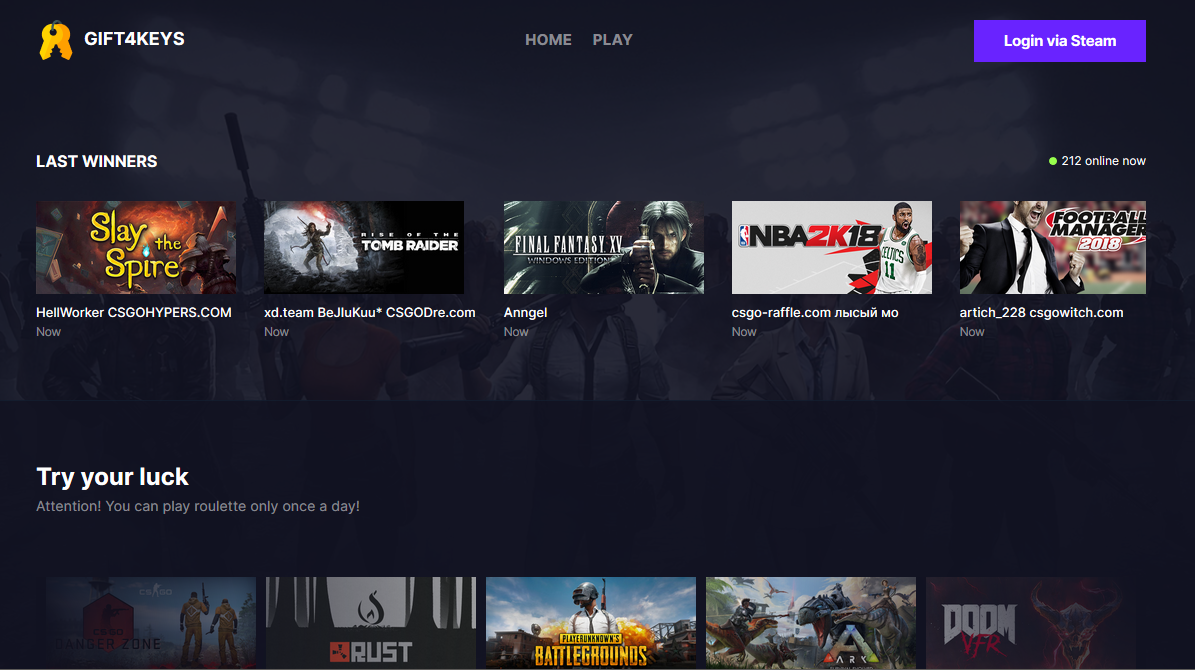
In the middle of the site is the “Try your luck” section, a roulette game where users can get their (supposed) free game. All they have to do is press the blue Play button.
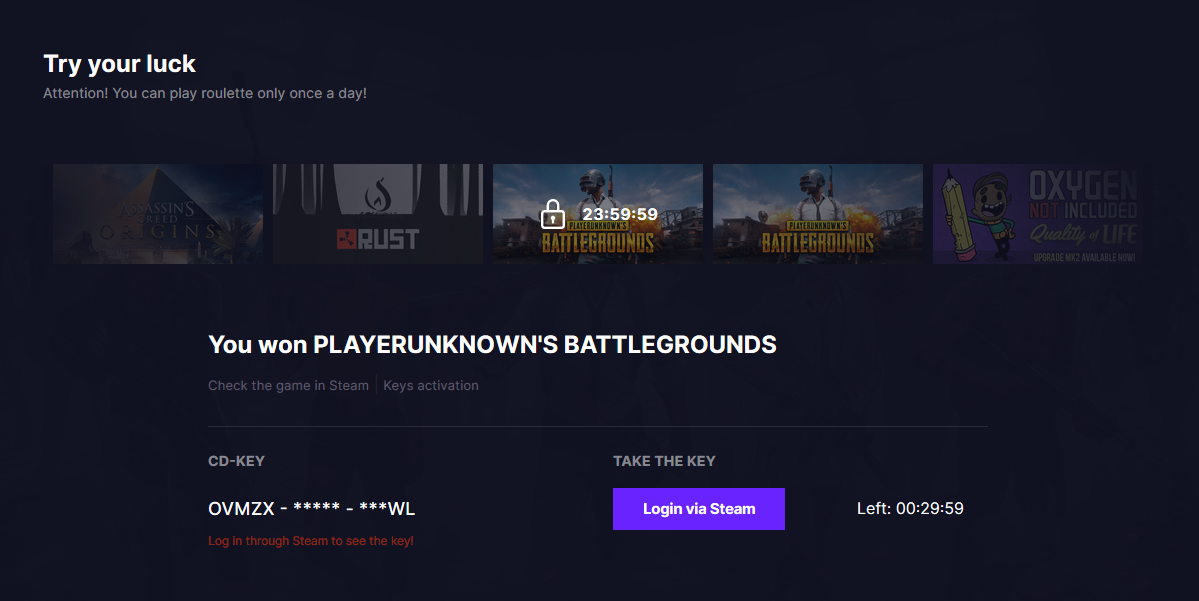
The page then shows to the user that they have less than 30 minutes to claim the complete key by logging into their Steam account via the website. At the same time, the page also shows that the user would need to wait for 24 hours before they can roll the roulette again and get another free game.
Clicking the Login via Steam button here—or at the upper right-hand corner of the site—opens a page that looks like the bog-standard unaffiliated third-party Steam login page. This is either as a pop-up window or a new tab. The site did both during several tests.
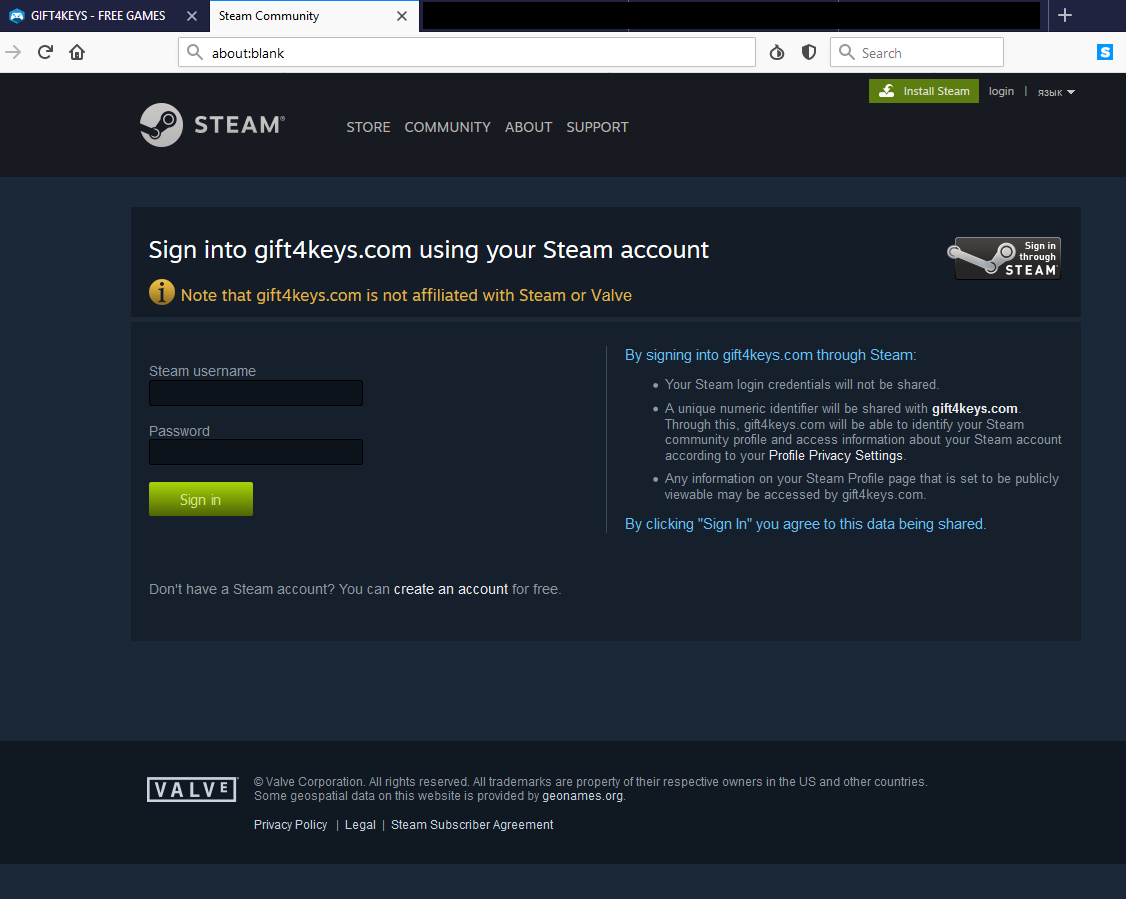
Here are a few reasons why, at this point, Steam users should start considering bailing from this site all together and not hand over their credentials:
- The links on the page, such as “Profile Privacy Setting” and “create an account” don’t work.
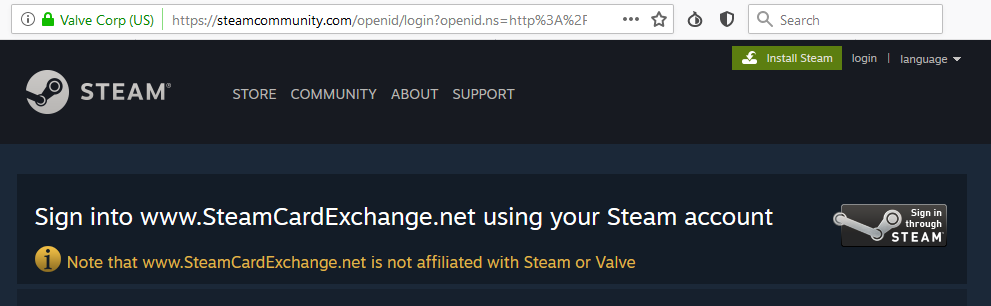
- The URL address bar is blank. Legitimate unaffiliated third-party sites display an EV certificate for Valve Corp, and the URL in the address bar says that the signing in takes place in steamcommunity.com.
- The Language drop-down box at the upper right-hand corner doesn’t work. It also appears to be in Russian even when visitors are outside of Russia.
Supplying credentials to this phish page, as we know, will result in accounts getting hijacked to further proliferate the phishing links.
Links in identical campaigns in the past were not hidden behind a URL shortener. It’s also no surprise that these links kept changing. In this case, the shortened URLs have redirected to the following domains, which are less than four months old, at some point:
- easyk3y[dot]com
- ezzkeys[dot]com
- g4meroll[dot]com
- g4me5[dot]com
- gift4keys[dot]com
- gifts-key[dot]com
- ong4me[dot]com
- tf2details[dot]com
- yes-key[dot]com
Be forewarned that a number of these sites are still online, and if you visit them, they all look like this:

As of this writing, the only way to access the actual “free games roulette” page we have been showing above is by appending certain strings at the end of the URLs. That’s probably a good thing.
Keep calm and be vigilant
Steam has always been the platform of choice of fraudsters for a long time because of its millions of active users. This isn’t the first time that users have met and reacted to such a phishing campaign. In fact, this latest one has all the telltale signs of previous campaigns: Steam friend sends a message with link out of nowhere, link leads to a fake Steam login page, collected Steam credentials are used to hijack accounts and spam their friends.
Yes, there are still Steam users falling for old tricks. Yet, it’s also good to see Steam users realizing the danger early on, giving their friends a heads-up about it, and, should they suspect that they are affected, try to contain their zombified accounts to prevent other users from getting compromised.
So be calm, keep on the lookout, stay informed, and continue to look after each other.
Stay safe!
Other related blog(s):










