Researchers at Positive Security have discovered a drive-by remote code-execution (RCE) bug in Windows 10. The vulnerability can be triggered by an argument injection in the Windows 10 default handler for ms-officecmd: URIs. It is likely that this vulnerability also exists in Windows 11.
What’s worrying is that the research team simply decided to find a code execution vulnerability in a default Windows 10 URI handler, and that they succeeded within two weeks. Given how many URI handlers are included in Windows you can bet that there are others to be found.
What is an URI handler?
A Uniform Resource Identifier (URI) is a unique sequence of characters that identifies a logical or physical resource used by web technologies. The well-known uniform resource locator (URL) and the uniform resource name (URN) are both examples of URIs. A URI handler is the program that gets launched to open a URI of a certain type. For example, the URI handler for ftp links can be different from the URI handler that deals with http links. This depends on your settings and often on which software and apps you have installed.
The problem handler
In this case the code execution is triggered by a malicious website which performs a Javascript redirect to a crafted ms-officecmd: URI (a scheme used by the Microsoft Office Universal Windows Platform (UWP) app to launch other Office desktop applications).
As an alternative to exploitation through malicious websites, crafted ms-officecmd: URIs could also be delivered via desktop applications performing unsafe URL handling. However, this exploit only works if the user has Microsoft Teams installed but it is not running.
ms-officecmd
While looking for viable candidates, the ms-officecmd: scheme immediately grabbed the attention of the research team due to its promising name. MS Office is a very complex suite of applications with many legacy features and a long history of exploitability. On top of that, the scheme ends in the abbreviation for ‘command’, which suggests even more complexity and potential for injection.
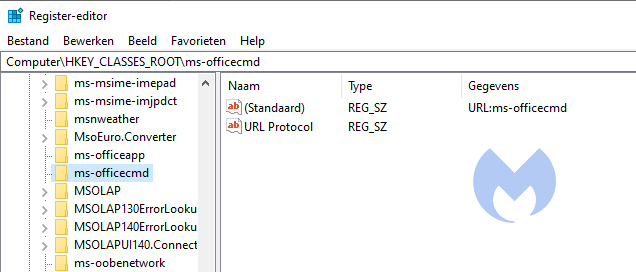
When the team started playing around with it, they noticed an executable called LocalBridge.exe which would briefly run, but would show no apparent external effect.
The research team decided to decompile LocalBridge.exe. which taught them how to create a valid JSON payload. It turned out they had to dig deeper. That meant analyzing AppBridge.dll next, since it contained the LaunchOfficeAppValidated method which the JSON payload is ultimately passed to.
As a different approach to dissecting the application that handles ms-officecmd: URIs, they tried inspecting an application which generates URIs that get handled by ms-officecmd:.They ended up at the Office UWP app. In this context it is good to know that the Office apps for phones using Windows 10 Mobile (Word, Excel, PowerPoint, OneNote) reached end of support on January 12, 2021. That means that since that date, app users no longer receive security updates, non-security hotfixes, free assisted support options or online technical content updates from Microsoft.
After some tinkering, the researchers managed to use the extracted JSON payload to open Office desktop applications via ms-officecmd: URIs. Specifically, the payload extracted from the Office UWP app could be used to open Outlook.
Phishing angle
The researchers found that when an http(s) URL was provided in the filename property, Outlook would render the respective webpage in an IE11 powered embedded web view. No indication of the webpage’s origin or even the fact that the displayed content stemmed from an external webpage was given. This behavior could be abused to mount very believable phishing attacks, especially since mailto: links are, depending on local configuration, expected to open the user’s email program.
Based on this information, the researchers crafted a PoC that does the following once a user can be tricked into clicking a link on a malicious website:
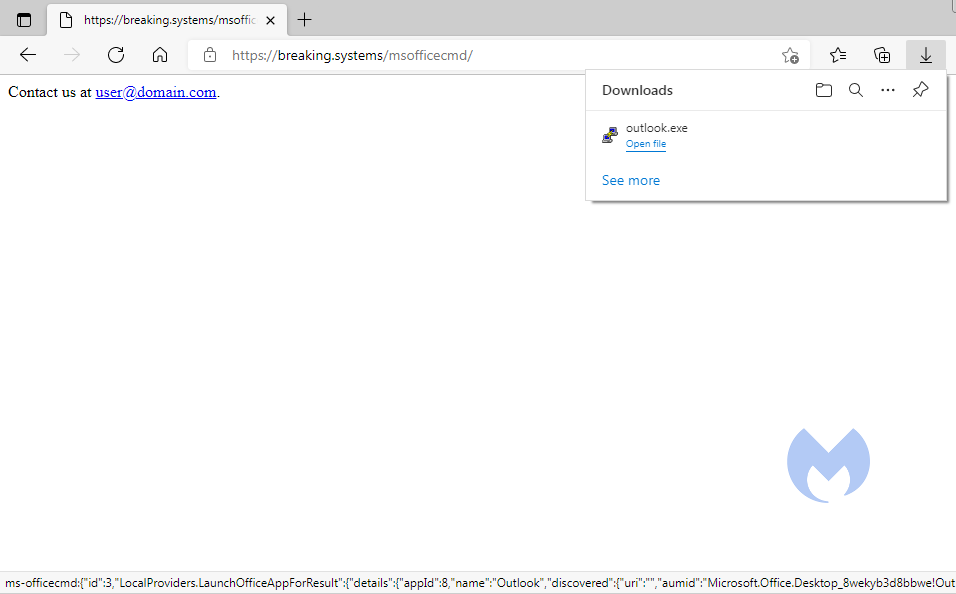
- A malicious executable named outlook.exe is saved to the victim’s download folder by dynamically adding an iframe that points to the exe file.
- The innocent looking mailto: link target is replaced with a malicious ms-officecmd: URI which references the downloaded executable in its filename property.
- The user confirms the ‘Open LocalBridge?’ dialog, which is not an explicit security warning.
- When Outlook is starting up, it displays a warning dialog about opening a potentially unsafe hyperlink. The user confirms opening the local ‘outlook.exe’ file since they are expecting outlook to be opened.
- The downloaded file is executed.
Patched or not?
The researchers have been going back and forth with Microsoft about this for months, having initially disclosed the weakness to Microsoft in March. Microsoft closed Positive Security’s initial report the very next day, based on what Positive Security called Microsoft’s “erroneous” belief that the exploit relies on social engineering, which would not meet the definition of a security vulnerability.
According to the researchers, the patch that was issued after five months seems to only affect Teams and Skype. The argument injection vulnerability described in this post is still present on fully patched Windows 10 and 11 systems. After the researchers brought this to Microsoft’s attention, they were told another patch addressing the argument injection was underway. Microsoft gave the researchers the go-ahead to post their write-up independently of its rollout.
Unfortunately, I was unable to confirm this. None of my Windows 10 machines have Edge Legacy installed and IE crashes on every exploit attempt, which is also annoying but not what I was waiting to see. When I tried it on the latest version of Edge, Malwarebytes Browser Guard blocked the download of the “outlook.exe.”
Anyway. This goes to show it pays to actually read the prompts and hover the links.
Stay safe, everyone!