Two-factor authentication (2FA) has been around for a while now and for the majority of tech users in the US and UK, it has became a security staple. Indeed, wake up calls brought about by data breaches have stirred others out of their comfort zones into finally adopting 2FA and making it part of their online lives.
But online criminals—quick as they are with anything at this rate—are already one (if not several) step ahead.
As early as 2017, cybercriminals have been incorporating capabilities to defeat 2FA into their kits. With 2FA becoming much more commonplace, such kits are increasing in popularity and are in high demand in the underground market.
Academics from Stony Brook University and Palo Alto Networks—namely Brian Kondracki, Babak Amin Azad, Nick Nikiforakis, and Oleksii Starov—have found at least 1,200 phishing kits online capable of capturing or intercepting 2FA security codes. This, of course, would enable them to bypass any any 2FA procedures their target victims have already set up.
According to their report entitled “Catching Transparent Phish: Analyzing and Detecting MITM Phishing Toolkits” cybercriminals are using Man-in-The-Middle (MiTM) phishing kits which mirror live content to users while at the same time extract credentials and session cookies in transit.
These kits make it easy for the cybercriminals, because the harvesting of 2FA authentication session tokens are automatic. And because victims can browse within the phishing page as if it’s the real thing after they authenticate, users are less likely to notice they’ve been phished.
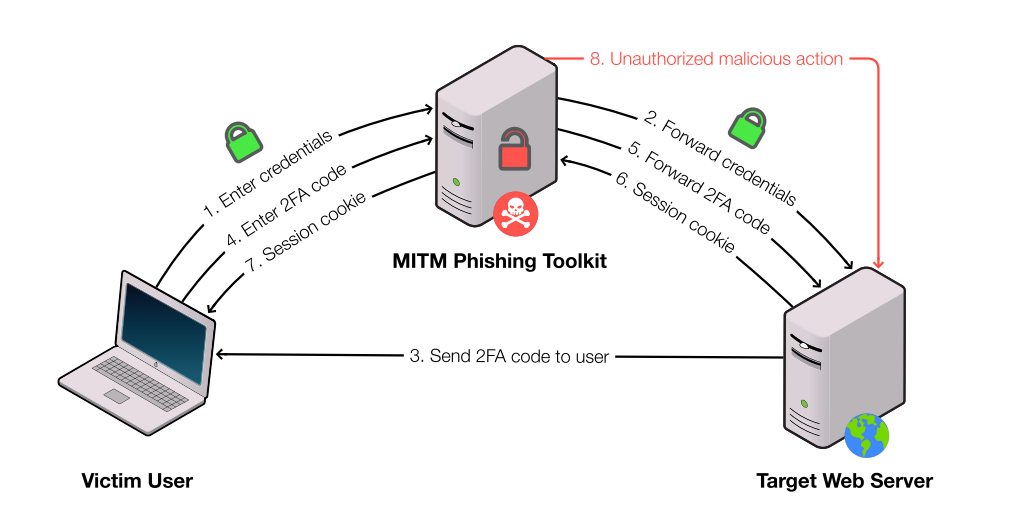
MiTM phishing attacks are perfect for scenarios where cybercriminals don’t want to use malware to steal credentials, and the attack itself doesn’t need human involvement in the process. Perhaps this is why email accounts, social media accounts, and some gaming accounts (as opposed to banking sites) are likely targets of MiTM phishers. These services have a more relaxed approach on how they log in users and keep them logged in until they manually log out.
Some of these services also create authentication sessions that can remain valid for years. Such sessions tokens can be used to abuse the account on a long term basis without the user knowing.
There are currently three widely known MiTM toolkits in popular hacking forums and code repositories: Evilginx, Muraena, and Modlishka. Among these, Modlishka (the Polish word for “mantis”) is the most familiar, and we covered it back in 2019.
Using machine learning, the academics created a fingerprinting tool they called PHOCA (Latin word for “seal”, the sea mammal). Per the report, PHOCA “can detect previously-hidden MITM phishing toolkits using features inherent to their nature, as opposed to visual cues.” All one needs to do is feed the tool with a URL or domain name, and then the tool determines if its web server is a MiTM phishing toolkit by using its trained classifier.
Criminals using a 2FA bypass is inevitable. PHOCA seems to be the only tool that can successfully pinpoint and help users thwart MiTM phishing websites. Aside from PHOCA, the academics propose client-side fingerprinting and TLS fingerprinting as form of detection method to greatly help thwart this type of attack.
Seemingly invisible threats like MiTM phishing are real. And we hope that we can protect from it sooner rather than later.