Globant, an IT and software development firm with offices all around the globe, admitted in a press statementWednesday that it has suffered a breach in its network. Affected data includes (but may not be limited to) some source code and certain project documentation of clients.
“We have recently detected that a limited section of our company’s code repository has been subject to unauthorized access. We have activated our security protocols and are conducting an exhaustive investigation,” company officials wrote. “To date, we have not found any evidence that other areas of our infrastructure systems or those of our clients were affected. We are taking strict measures to prevent further incidents.”
The breach allegedly represents the latest work from the increasingly popular threat actor group LAPSUS$, which claimed responsibility for the attack this week. In a message sent on Telegram to 45,000 followers, individuals who claim to be behind LAPSUS$ first announced that they were “officially back from vacation.”
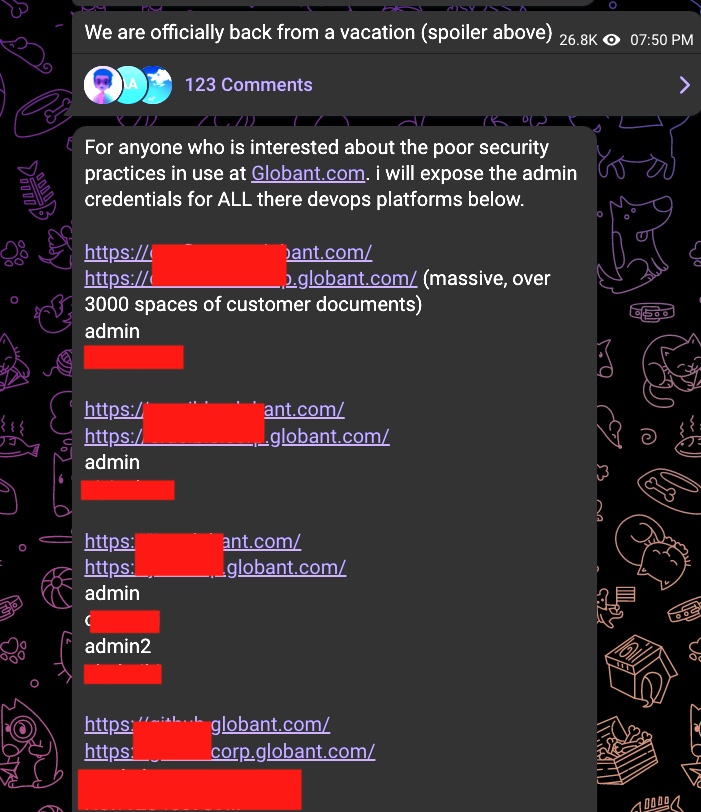
A follow-up message sent shortly after reads:
For anyone who is interersted about the poor security practices in use at Globant.com. I will expose the admin credentials for ALL their devops platforms below.
As of this writing, Globant hasn’t confirmed when it was breached, nor did it mention if a group approached it for ransom.
More about LAPSUS$
Globant is the latest company in a lengthening list of huge names compromised by LAPSUS$, a relatively new group in the online extortion gig. This list already includes Microsoft, Nvidia, Samsung, LG, and Okta.
If you’re wondering if LAPSUS$ has always targeted such large companies, the answer is yes. When LAPSUS$ first grabbed the attention of the cybersecurity community, it had already compromised companies like Impresa, the largest media conglomerate in Brazil; Claro, one of Brazil’s telecommunications operators; and Brazil’s Ministry of Health.
These early attacks led people to believe that LAPSUS$ hailed from South America. Notably, its use of Spanish and Portuguese was akin to native speakers. Microsoft tracks the group as “DEV-0537”.
As a criminal group, its primary focus is to hack companies, steal their data, and demand a ransom. In some cases, it has used ransomware and phishing (among other social engineering tactics) as a precursor to get inside target systems. LAPSUS$ is known for not only stealing data but also for stealing code from companies it targets. It is said that it uses stolen code to better hide malware. To date, it has reportedly pilfered a total of $14 million (£10.6 million)
Before revealing it had breached Globant and stole the company’s data, LAPSUS$ claimed that some of its members were taking “a vacation”. In cybersecurity, we have learned that this could either mean that threat actors are moving away from the spotlight to lay low—because of the pressure to evade law enforcement—or the actors have somehow already been captured. It appears that the latter applies in LAPSUS$’s case.
In late March, cybersecurity researchers investigating these big-named hacks were able to trace the attacks to a 16-year old teenager in Oxford, England. The teen, who remains unnamed due to his age, goes by the online monikers “White” and “Breachbase” and is believed to be the group’s mastermind. It is said that the Oxford teen hacker’s personal information, including those of his parents, was leaked by rival hackers. On top of that, forensic investigators used evidence from the hacks and public information to tie the teen to the hacking group.
Another suspected LAPSUS$ member is also a teenager but based in Brazil. According to Bloomberg, this teen is “so skilled at hacking—and so fast—that researchers initially thought the activity they were observing was automated.”
Investigators looking into the hacks have found a total of seven unique accounts associated with the extortion group. This indicates that there are likely more members of LAPSUS$ that are involved.
On March 21, the FBI launched a public appealfor information about the group. Four days later, news of the UK police arresting seven teenagersbetween the ages of 16 and 21 broke. It was part of an international police investigation into the LAPSUS$ gang. Today, according to the BBC, two of the teens (aged 16 and 17) have been formally charged with “three counts of unauthorised access to a computer with intent to impair the reliability of data, one count of fraud by false representation, and one count of unauthorised access to a computer with intent to hinder access to data.”
The 16-year-old, whom we believe could be the teen from Oxford, is also charged with “one count of causing a computer to perform a function to secure unauthorised access to a program.”










