According to analyses of several cybersecurity firms and CERT (Computer Emergency Response Team) Ukraine (CERT-UA), the state-sponsored threat actor group Tonto Team, which has been linked to China-backed cyber operations, is ramping up its spying campaign against Russian government agencies.
The campaign, which involves an email, a Word document file in RTF (Rich Text File) format, and a backdoor payload, starts off with socially engineering recipients to convince them to open a malformed attachment, triggering the execution of an MS Office exploit, particularly in the Equation Editor.
According to SentinelOne, the RTF file masquerades as a government advisory or security warning to agencies and infrastructure providers of potential attacks.
The fake advisory is written in Russian. Below is the Google-translated text in English:
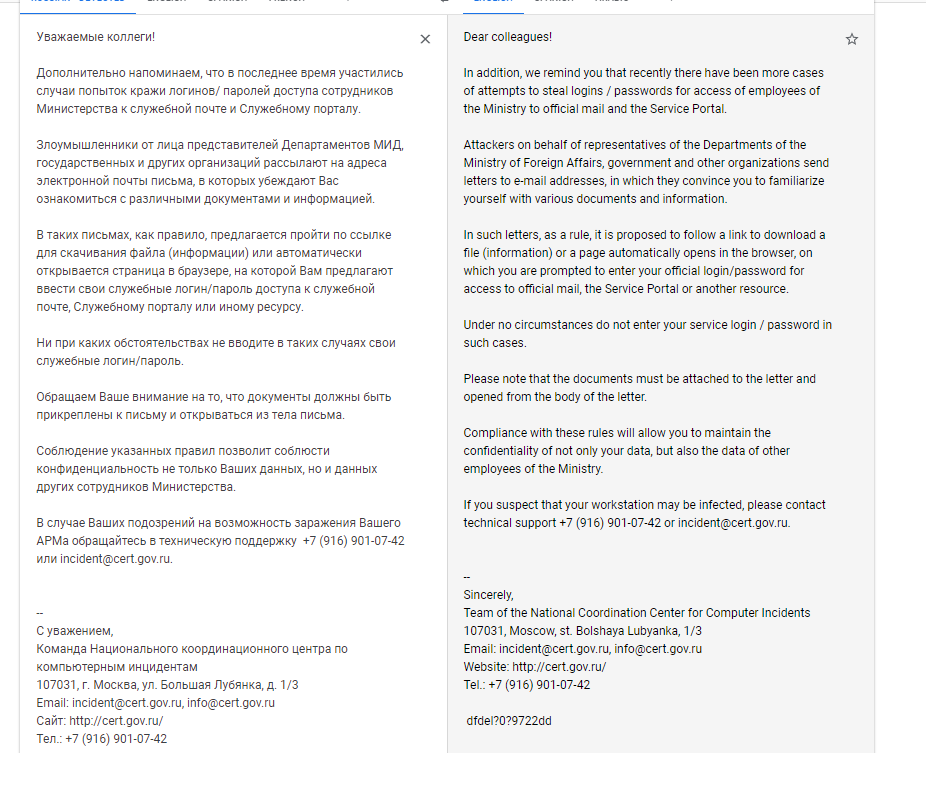
Dear colleagues! In addition, we remind you that recently there have been more cases of attempts to steal logins / passwords for access of employees of the Minsitry to official mail and the Service Portal. Attackers on behalf of representatives of the Department of the Ministry of Foreign Affairs, government and other organizations send letters to e-mail addresses, in which they convince you to familiarize yourself with various documents and information. Under no circumstances do not enter your service login / password in such cases. Please note that the documents must be attached to the letter and opened from the body of the letter. Compliance with these rules will allow you to maintain the confidentiality of not only your data, but also the data of other employees of the Ministry.The Tonto Team used Royal Road (sometimes called “8.t”) to create the malicious RTF file. First analyzed by nao_sec, Royal Road is a document builder that gives threat actors the ability to embed malicious code within RTF files, aiding actors in compromising target systems.
The exploit is triggered upon opening the file, and the malware payload, Bisonal, is dropped. Bisonal, a tool many Chinese threat actors use, is a RAT (remote access Trojan). Apart from Chinese APTs (Advanced Persistent Threats), no other threat actor has used Bisonal.
The Tonto Team, an APT group that has been around almost as long as Bisonal, has many aliases: Karma Panda, Bronze Huntley, CactusPete, and Earth Akhlut. The group is known for targeting Asian nations (South Korea, Taiwan, and Japan) and Russia. So, this isn’t the first time China has been in the case of the former Soviet state. Rather, this is about a notable increase in targeting activity against Russia.
“What we’re seeing here is a potential Chinese government increase in intelligence collection requirements from inside Russia,” SentinelOne Senior Threat Researcher Tom Hegel told Dark Reading in an interview. “Perhaps an increased prioritization or expansion of resources assigned to such tasking.”
China is prioritizing its espionage campaign against Russia due to the ongoing Russian invasion of Ukraine. And while Chinese officials see themselves with Russia as “comprehensive strategic partners of coordination”, their diplomatic relations have strengthened through the years, mainly to suppress the expansion of Western alliances.
What China is doing is “simply China looking out for itself in uncertain times,” Hegel is also quoted saying. “Like any well-resourced nation, they seek to support their own agenda through cyber, and the state of affairs in Russia may be adjusting just what they prioritize.”
Chinese hacking groups have been using Royal Road and Bisonal for years, which says a lot. Its longevity points to the shared use of resources among these groups, making attribution very difficult. The repeated use of these tools through the years also suggests that campaigns against targeted nations have been successful, which gives us an idea of the state of security of these countries.
“The fact that these toolkits evolve and continue to operate really speaks to how well they’re resourced, and the state of the defense side,” Hegel told CyberScoop in a separate interview. “Nothing can really stop them from continuing to use this. It’s still successful in many cases, as we see here. You look at the exploits they’re using in these documents, they’re years old exploits. They’re popping people that are out of date by quite a few years.”










