Ethical hacker and security researcher Kody Kinzie shared with BleepingComputer a list of over 50 domains of which many are spelling variations of the brand name Sniffies.
Sniffies identifies itself as a “modern, map-based, meetup app for gay, bi, and curious guys.”
Kody used an open source tool called DNSTwist to generate a list of lookalike domains for Sniffies.com. Out of the 3531 possibilities generated by the tool, 51 represented valid domains.
“I saw a good amount of domains registered with the same MX server set up, even though the domains were hosted on random platforms.”
A mail exchanger record (MX record) specifies the mail server responsible for accepting email messages on behalf of a domain name. So that would imply that the domains were set up by the same threat-actor.
Typosquatting
Typosquatting is a term you may have seen when reading about Internet scams. In essence it relies on users making typing errors (typos) when entering a site or domain name. Sometimes it is also referred to as URL hijacking or domain mimicry, but IMHO the word typosquatting more accurately describes the matter. As you will understand, the success of a typosquat scammer depends on the number of victims that are likely to misspell the intended domain and land on the scammers’ pages.
One factor is the popularity of the domain. With an estimated number of 79,600 visitors per day, Sniffies certainly qualifies in that department.
Advertising
BleepingComputer’s test results were described as:
“Once accessed, the illicit ‘Sniffies’ copycat domains do one of the following things:
- Push the user to install dubious Chrome extensions
- Launch the ‘Music’ App on Apple devices right from the web browser
- Lead the users to bogus technical ‘support’ scam sites
- Lead the users to fake job posting sites”
Obviously, we did some testing of our own. We found some domains that had either been abandoned or parked for the future, but some did what they were set up for—redirect visitors based on some basic system properties and the location (based on IP address).
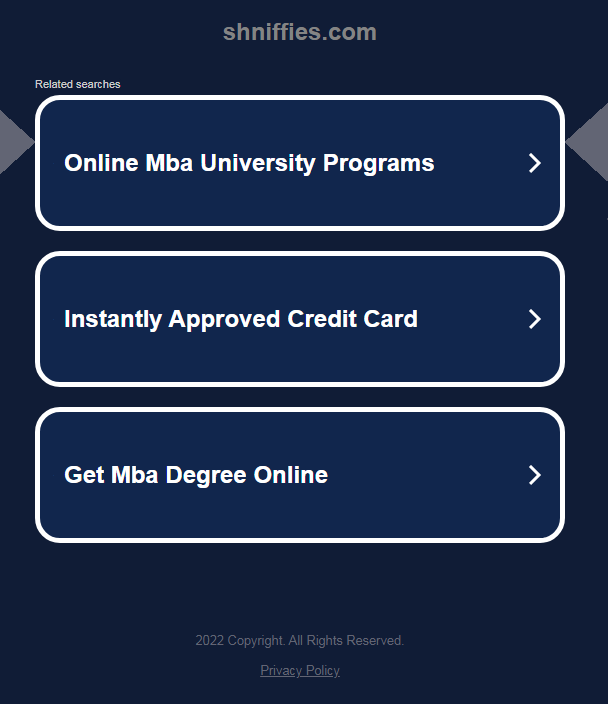
Most of the redirects we found at Malwarebytes went to advertising sites that were more or less legitimate. But certainly not what the user would be looking for. Many shared this look, offering the visitor a few choices.
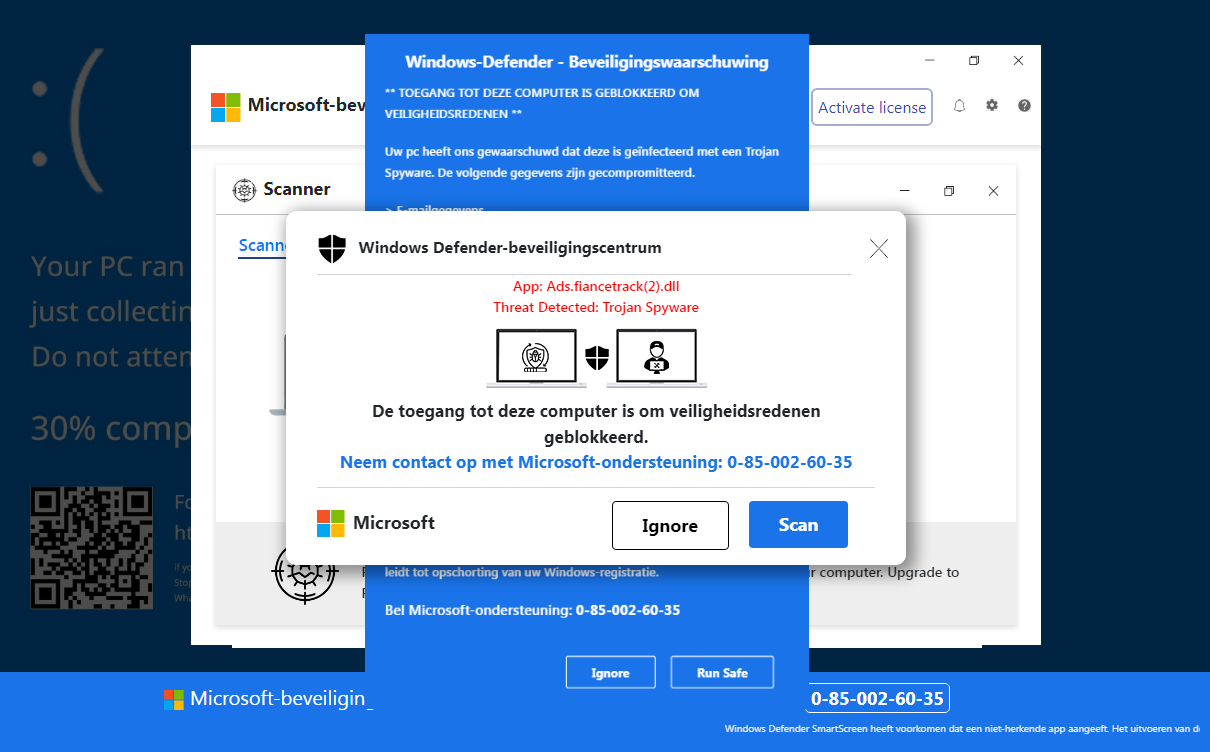
In one instance (Dutch IP, Windows system) we were redirected to a fake Microsoft Defender warning site (including soundtrack and locked screen), parked in the domain ondigitalocean.app which has been on Malwarebytes’ radar for some time.
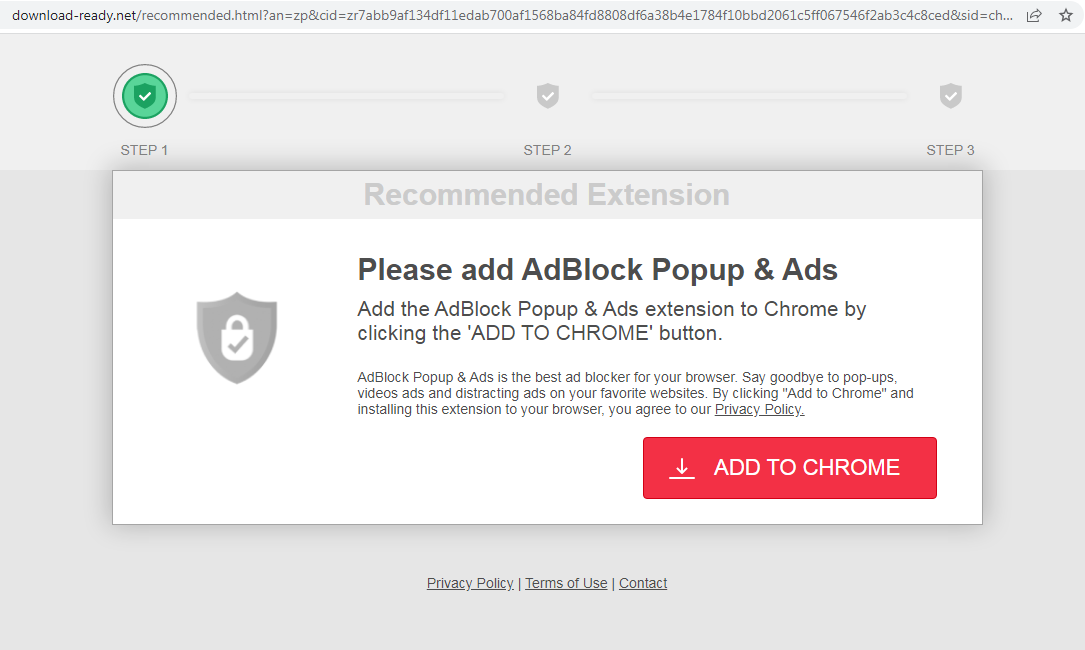
We also found one of the Chrome extensions that BleepingComputer described as dubious. Malwarebytes detects these extensions as PUP.Optional.AdMax.
Mitigation
While it’s certainly nice to read how these campaigns work and how the research was done, Sniffies is just an example of what is out there.
To avoid falling victim to typosquatters, there are a few basic measures you can take, which are in essence aimed at not typing the url.
- Bookmark your favorites
- Use search results rather than typing the url in the address bar
- Leave some or all of the sites that you visit every day open in your browser tabs (most popular browsers offer the option to continue where you left off or to specify a set of sites to start with)
- Never click links in unexpected emails or on unknown sites
- Use an antivirus or anti-malware solution that offers web protection and preferably even an anti-exploit solution.
Stay safe, everyone!











