The city of Antwerp’s digital systems have come to a grinding halt. The Flemish government under which Antwerp resides has confirmed that this is the result of a ransomware attack.
The consequences for the city’s inhabitants are drastic, as hundreds of city employees revert to working on paper instead of on their computers. This is creating complications for everything from the obvious to the not-so-obvious.
For example: There are problems with payments to people that depend on city benefits (which are not expected to be resolved before the end of the year); libraries and recycling centers are closed; there is no way to obtain new IDs; and students with special needs are unable to use their laptops.
The Play ransomware group is claiming credit on its dark web leak site.
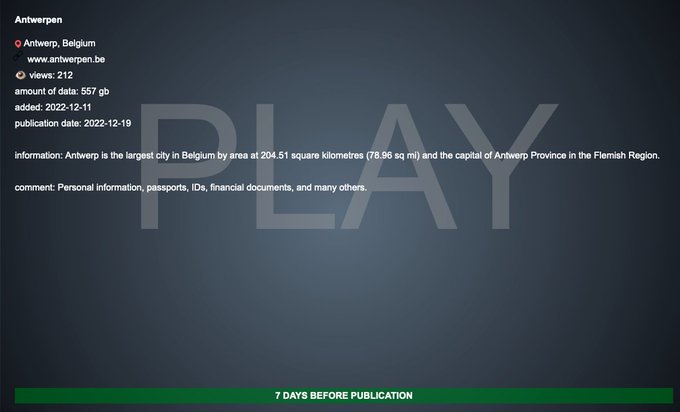
Play is a relatively new ransomware group and first attracted media attention a few months ago, when it attacked Argentina’s Judiciary of Córdoba. Play can be recognized by the .play extension it adds to encrypted files and a very simple
ReadMe.txtC: drive, that simply contains the word ‘PLAY’ and a contact email address. According to the leak site, 557 GB of information was stolen, including personal information, passports, other IDs, and financial documents.
ITdaily claims the attackers gained initial access through Digitalis, the digital partner of the city of Antwerp. From there they were able to encrypt essential files which rendered databases and applications unreachable.
The large amount of stolen data suggests that the threat actor must have had access over a longer period of time.
The city has been given until December 19, 2022 to pay the ransom or the threat actor will start publishing the stolen data.
Government warning
In a newsletter to Belgian government employees, staff were cautioned to be alert and careful. This was prompted by recent attacks on the systems of the Zwijndrecht police by Ragnar Locker, and an attack on the municipality of Diest which has not been claimed by a specific ransomware group yet.
The Belgian government’s warning is specifically about actionable items for the staff:
- Be alert about phishing attempts.
- Use secure and unique passwords.
- Identity verification during contact. Make sure the person you are communicating with is who they claim to be.
- Use updated devices, only permitted software, and limit administrator privileges to where they are strictly necessary.
We concur. For organizations we would like to add:
- Always use active anti-virus/anti-malware protection.
- Limit Internet access to critical devices and systems where possible.
- Ask the same prudence of your service providers.
- Maintain offsite, offline backups and test that you can restore from them
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











