In a recent tweet, the FBI office in Denver warned consumers against using free public charging stations, stating that criminals have managed to hijack public chargers with the objective of infecting devices with malware or other software that can give hackers access to your phone, tablet or computer.
“Avoid using free charging stations in airports, hotels or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.”
When asked, the FBI’s Denver field office said the message was meant as an advisory, and that there was no specific case that prompted it. The method the FBI is referring to is often referred to as “juice jacking.”
Imagine that the battery of your phone is dying and you’re nowhere near a power outlet, would you connect your phone to any old USB port? A juice jacking attack uses a charging port or infected cable to exfiltrate data from the connected device or upload malware onto it. The term was first used by Brian Krebs in 2011 after a proof of concept was conducted at DEF CON by Wall of Sheep. When users plugged their phones into a free charging station, a message appeared on the kiosk screen saying:
“You should not trust public kiosks with your smart phone. Information can be retrieved or downloaded without your consent. Luckily for you, this station has taken the ethical route and your data is safe. Enjoy the free charge!”
In a follow-up warning the FCC hinted at the possibility of malicious cables. Both warnings were greeted with scepticism by a great many people active in the security community, since attacks of this kind are very unlikely to take place, and even more unlikely to succeed. But, while there are no known, recent cases of juice jacking, it doesn’t harm to be aware of potential cyberattacks.
How would juice jacking work?
As you may have noticed, when you charge your phone through the USB port of your computer or laptop, you are also able to move files back and forth between the two systems. That’s because a USB port is not simply a power socket. A regular USB connector has five pins, where only one is needed to charge the receiving end. Two of the others are used by default for data transfers.
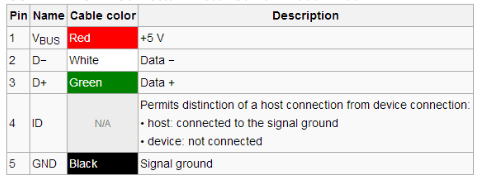
USB connection table courtesy of Sunrom
Unless you have made changes in your settings, the data transfer mode is disabled by default, except on devices running older Android versions. The connection is only visible on the end that provides the power, which in the case of juice jacking is typically not the device owner. That means, any time a user connects to a USB port for a charge, they could also be opening up a pathway to move data between devices, with the following consequences:
- Data theft: during the charge, data is stolen from the connected device.
- Malware installation: as soon as the connection is established, malware is dropped on the connected device. The malware remains on the device until it is detected and removed by the user.
Data theft
In the first type of juice-jacking attack, cybercriminals could steal any and all data from mobile devices connected to charging stations through their USB ports. But there’s no hoodie-wearing hacker sitting behind the controls of the kiosk, so how would they get all your data from your phone to the charging station to their own servers? And if you charge for only a couple minutes, does that save you from losing everything?
Make no mistake, data theft can be fully automated. A cybercriminal could breach an unsecured kiosk using malware, then steal the information from connected devices. There are crawlers that can search your phone for personally identifiable information (PII), account credentials, banking-related or credit card data in seconds. There are also many malicious apps that can clone all of one phone’s data to another phone, using a Windows or Mac computer as a middleman. So, if that’s what hiding on the other end of the USB port, an attacker could get all they need to impersonate you.
Cybercriminals are not necessarily targeting specific, high-profile users for data theft, either—though a threat actor would be extremely happy (and lucky) to fool a potential executive or government target into using a rigged charging station. However, the chances of that happening are rather slim. Instead, hackers know that our mobile devices store a lot of PII, which can be sold on the dark web for profit or re-used in social engineering campaigns.
Malware installation
The second type of juice-jacking attack would involve installing malware onto a user’s device through the same USB connection. This time, data theft isn’t always the end goal, though it often takes place in the service of other criminal activities. If threat actors were to steal data through malware installed on a mobile device, it wouldn’t happen upon USB connection but instead take place over time. This way, hackers could gather more and varied data, such as GPS locations, purchases made, social media interactions, photos, call logs, and other ongoing processes.
There are many categories of malware that cybercriminals could install through juice jacking, including adware, cryptominers, ransomware, spyware, or Trojans. In fact, Android malware nowadays is as versatile as malware aimed at Windows systems. While cryptominers mine a mobile phone’s CPU/GPU for cryptocurrency and drain its battery, ransomware freezes devices or encrypts files for ransom. Spyware allows for long-term monitoring and tracking of a target, and Trojans can hide in the background and serve up any number of other infections at will.
Many of today’s malware families are designed to hide from sight, so it’s possible users could be infected for a long time and not know it. Symptoms of a mobile phone infection include a quickly-draining battery life, random icons appearing on your screen of apps you didn’t download, advertisements popping up in browsers or notification centers, or an unusually large cell phone bill. But sometimes infections leave no trace at all, which means prevention is all the more important.
How to avoid juice jacking
The first and most obvious way to avoid juice jacking is to stay away from public charging stations or portable wall chargers. Don’t let the panic of an almost drained battery get the best of you. I’m probably showing my age here, but I can keep going without my phone for hours. I’d rather not see the latest kitty meme if it means compromising the data on my phone.
If you feel going through a part of your life without a phone is crazy talk and a battery charge is necessary to get you through the next leg of your travels, using a good old-fashioned AC socket (plug and outlet) will do the trick. No data transfer can take place while you charge—though it may be hard to find an empty outlet. While traveling, make sure you have the correct adapter for the various power outlet systems along your route. Note there are 15 major types of electrical outlet plugs in use today around the globe.
Other non-USB options include external batteries, wireless charging stations, and power banks, which are devices that can be charged to hold enough power for several recharges of your phone. Depending on the type and brand of power bank, they can hold between two and eight full charges. Power banks with a high capacity are known to cost more than US$100, but offer the option to charge multiple devices without having to look for a suitable power outlet.
If you still want the option to connect via USB, USB condoms are adaptors that allow the power transfer but don’t connect the data transfer pins. You can attach them to your charging cable as an “always on” protection. Using such a USB data blocker or “juice-jack defender” as they are sometimes called will always prevent accidental data exchange when your device is plugged into another device with a USB cable. This makes it a welcome travel companion, and will only set you back US$10–$20.
Checking your phones’ USB preference settings may help, but it’s not a foolproof solution. There have been cases where data transfers took place despite the “no data transfer” setting.
Finally, avoid using any charging cables and power banks that seem to be left behind. You can compare this trick to the “lost USB stick” in the parking lot. You know you shouldn’t connect those to your computer, right? Consider any random technology left behind as suspect. Your phone will thank you for it.
Malwarebytes removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.











