Twilio has warned users of the Authy multi-factor authentication (MFA) app about an incident in which cybercriminals may have obtained their phone numbers.
Twilio said the cybercriminals abused an unsecured Application Programming Interface (API) endpoint to verify the phone numbers of millions of Authy multi-factor authentication users.
Authy is an app that you install on your device which then produces a MFA code for you when logging into services.
The cybercriminals were able test the validity of an enormous list of phone numbers against the unsecured API endpoint. If the number was valid, the endpoint would return information about the associated accounts registered with Authy.
Twilio says it has seen no evidence of the attackers gaining access to Twilio’s systems or other sensitive data, but as a precaution it is asking all Authy users to update to the latest Android and iOS apps.
BleepingComputer notes that a threat actor named ShinyHunters leaked a CSV text file containing what they claim are 33 million phone numbers registered with the Authy service.
“In late June, a threat actor named ShinyHunters leaked a CSV text file containing what they claim are 33 million phone numbers registered with the Authy service.”
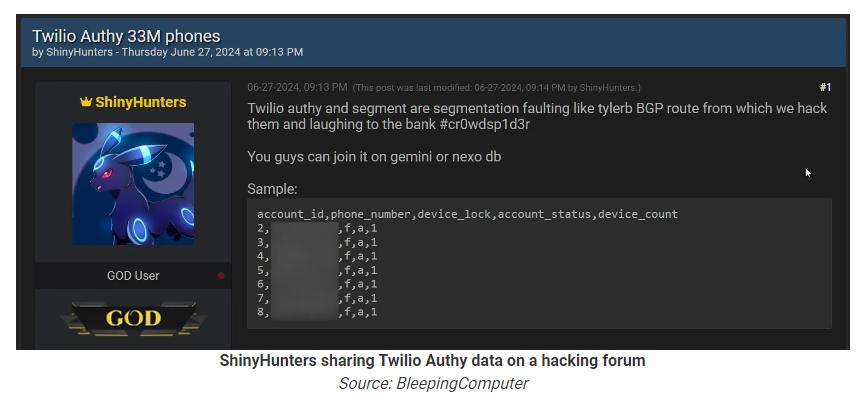
In that post, ShinyHunters suggests that buyers combine the data set with those leaked in the Gemini or Nexo data breaches. Nexo is a crypto platform where users can buy, exchange, and store Bitcoin and other cryptocurrencies. Gemini is another cryptocurrency exchange which has suffered several breaches in the past years.
With matches between the data sets, a cybercriminal could engage in SIM-swapping or phishing attacks to steal the target’s cryptocurrencies.
If you are an Authy user we advise you to update at your earliest convenience and keep an eye out for any potential phishing messages.
How to avoid being phished
Remember that phishing messages will try to rush you into making a decision by setting an ultimatum or otherwise imposing a sense of urgency. Don’t let them rush you into an expensive mistake.
There are a few tell-tale signs for phishing mails:
- It asks you to update/fill in personal information.
- The URL on the email and the URL that displays when you hover over the link are different from one another.
- The “From” address is not the legitimate address, although it may be a close imitation.
- The formatting and design are different from what you usually receive from the impersonated brand.
- The email contains an attachment you weren’t expecting.
However, with the advancement of AI, phishing emails are getting more sophisticated. So if you have even a tiny amount of suspicion that something is phishy, don’t hesitate to confirm the source of the email through another method. The chances of losing your money are much smaller after a quick call asking “Did you send this?”
You can check if your phone number was included in this breach by searching our database for the email address that is associated with your Authy account.
We don’t just report on threats—we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your, and your family’s, personal information by using identity protection.











