A few days ago, an advertisement for a zero-day vulnerability in Firefox for Android appeared on Inj3ct0r, an exploit database.
The author, “fil9”, was just registered to the site last month, and claims the exploit works on Firefox versions 23/24/26(Nightly) for Android.
The exploit forces the mobile browser to download and execute a (possibly) malicious app. In his video, fil9 shows the exploit in action, downloading and installing what appears to be an update for Firefox. However, when the “update” is executed automatically, viewers can see the potential for malicious code to be inserted.
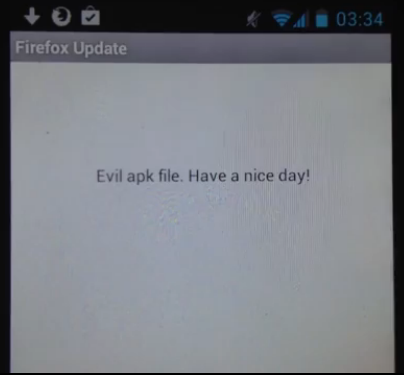
In order for the downloaded app to execute, users must allow installation of Android apps (APKs) from unknown sources, something that’s not recommended from a security standpoint. Also, users have to be using a standard apk installer.
The biggest problem in this situation is that Firefox automatically executes certain known files once they’re downloaded, and doesn’t give users an option to disable this. Without some sort of prompt, users have no idea that an external app has just been executed.
As others have already pointed out, this could cause serious havoc to Firefox users on Android. Websites are compromised frequently, and all a user would have to do is visit an infected website to fall victim to this attack.
Additionally, the exploit could be leveraged by luring Firefox Android users with social engineering tricks, like phishing, getting the user to click a compromised link and thereby exploiting them. Phishing is a very popular method of infiltration, and has been very successful in attacks against high-profile targets, such as banks or government entities.
It’s clear that Mozilla needs to make some changes to their browser to make it more secure. If you’re currently using Firefox for Android, we’d recommend switching to an alternative until Mozilla patches the vulnerability and allows users to disable the automatic execution features.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









