We have identified a new drive-by download campaign that distributes the Princess ransomware (AKA PrincessLocker), leveraging compromised websites and the RIG exploit kit. This is somewhat of a change for those tracking malvertising campaigns and their payloads.
We had analyzed the PrincessLocker ransomware last November and pointed out that despite similarities with Cerber’s onion page, the actual code was much different. A new payment page seemed to have been seen in underground forums and is now being used with attacks in the wild.
From hacked site to RIG EK
We are not so accustomed to witnessing compromised websites pushing exploit kits these days. Indeed, some campaigns have been replaced with tech support scams instead and overall most drive-by activity comes from legitimate publishers and malvertising.
Yet, here we observed an iframe injection which redirected from the hacked site to a temporary gate distinct from the well-known “Seamless gate” which has been dropping copious amounts of the Ramnit Trojan.
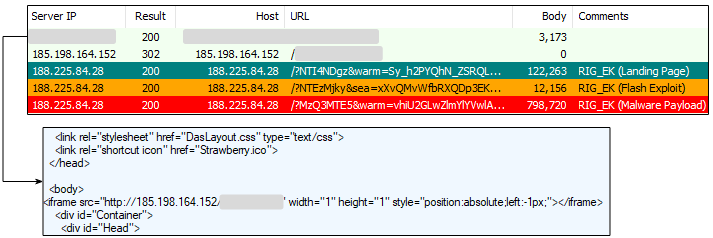
The ultimate call to the RIG exploit kit landing page is done via a standard 302 redirect leading to one of several Internet Explorer (CVE-2013-2551, CVE-2014-6332, CVE-2015-2419, CVE-2016-0189) or Flash Player (CVE-2015-8651) vulnerabilities.
Princess ransomware
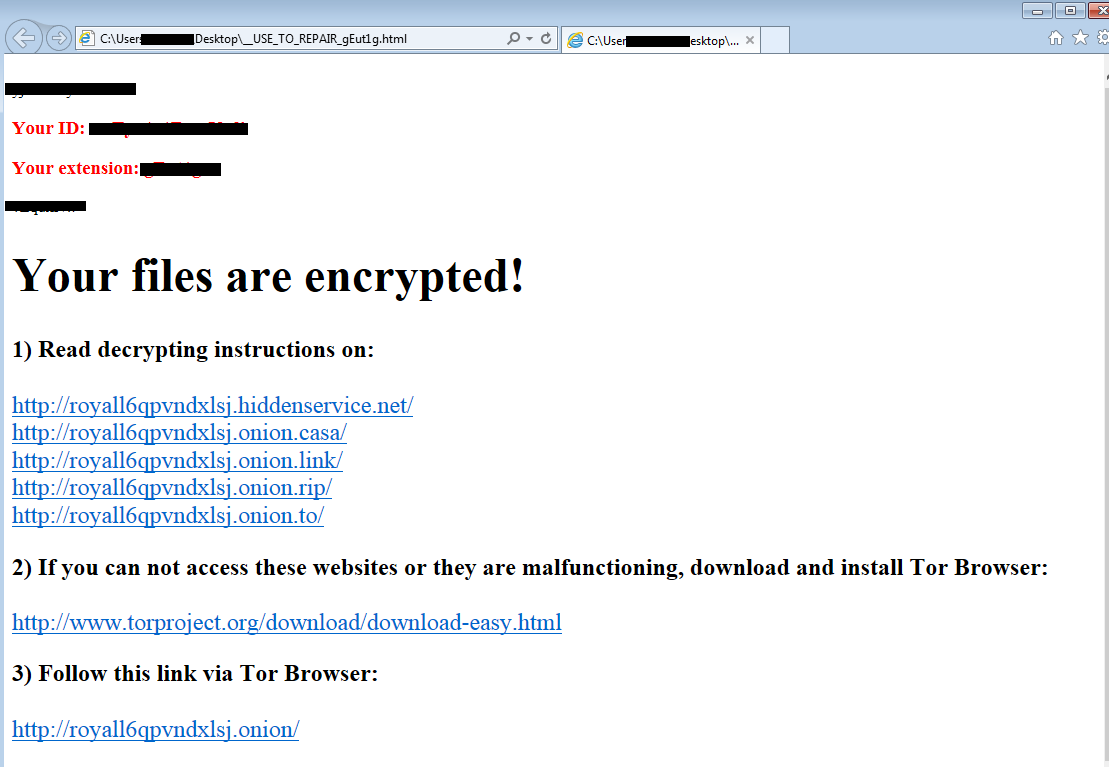
Once the exploitation phase is successful, RIG downloads and runs the Princess Ransomware. The infected user will notice that their files are encrypted and display a new extension. The ransom note is called _USE_TO_REPAIR_[a-zA-Z0-9].html where [a-zA-Z0-9] is a random identifier.
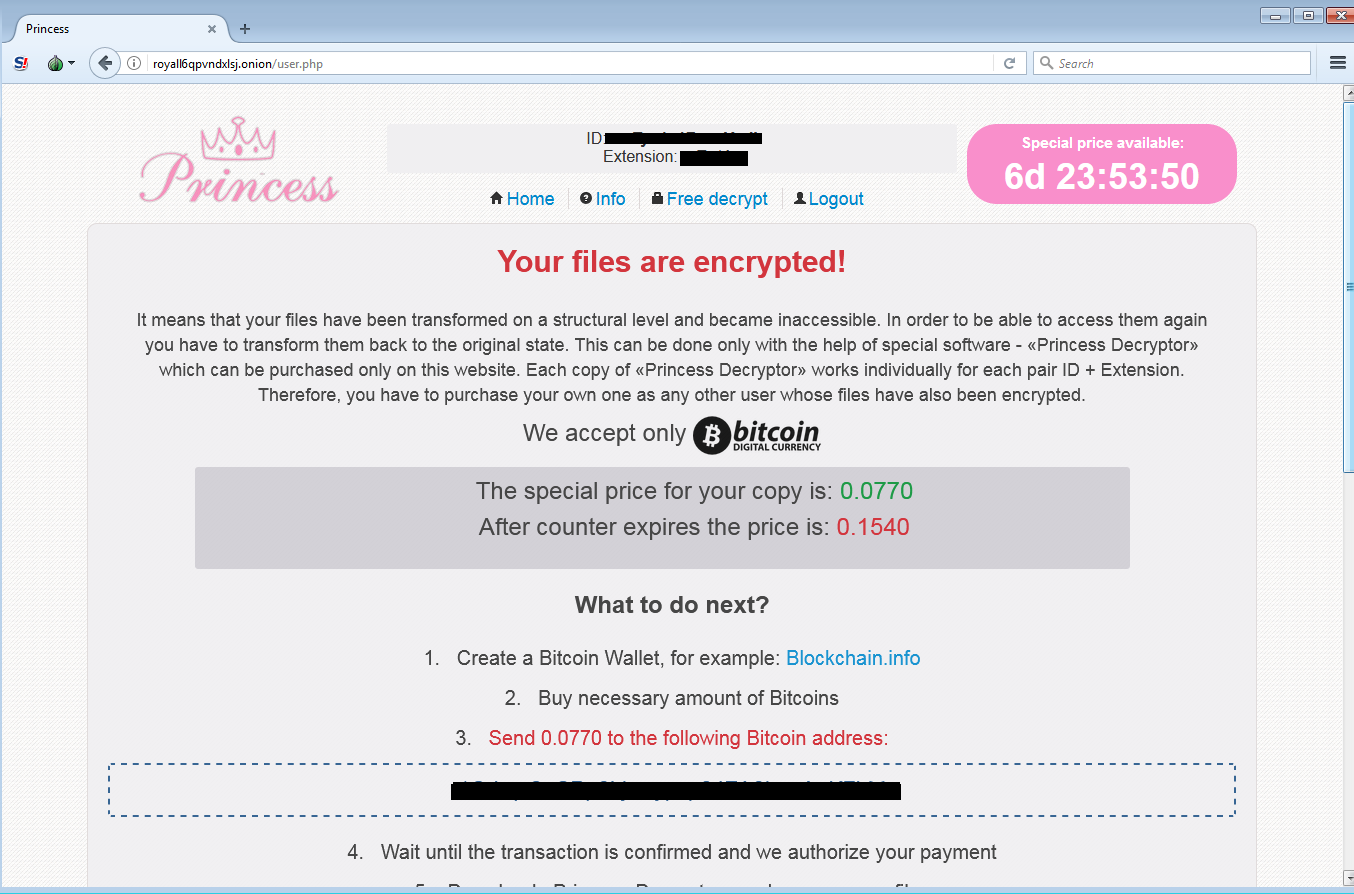
The payment page can be accessed via several provided links including a ‘.onion‘ one. Attackers are asking for 0.0770 BTC, which is about $367 at the time of writing.
Down but still kicking
The exploit kit landscape is not what it was a year ago, but we may be remiss to disregard drive-by download attacks completely. Malvertising is still thriving and we are noticing increased activity and changes with existing threat actors and newcomers.
We will update this post with additional information about Princess Locker if there is anything noteworthy to add.
Indicators of compromise
RIG EK gate:
185.198.164.152
RIG EK IP address:
188.225.84.28
PrincessLocker binary:
c61f4c072bb1e3c6281a9799c1a3902f35dba652756fe96a97e60d0097a3f9b7
PrincessLocker payment page:
royall6qpvndxlsj[.]onion