Since its discovery less than a month ago, a new Trojan malware for Android we detect as Android/Trojan.FakeAdsBlock has already been seen on over 500 devices, and it’s on the rise. This nasty piece of mobile malware cleverly hides itself on Android devices while serving up a host of advertisements: full-page ads, ads delivered when opening the default browser, ads in the notifications, and even ads via home screen widget. All while, ironically, posing as an ad blocker vaguely named Ads Blocker.
Upon installation: trouble
Diving right into this mobile threat, let’s look at its ease of infection. Immediately upon installation, it asks for Allow display over other apps rights.
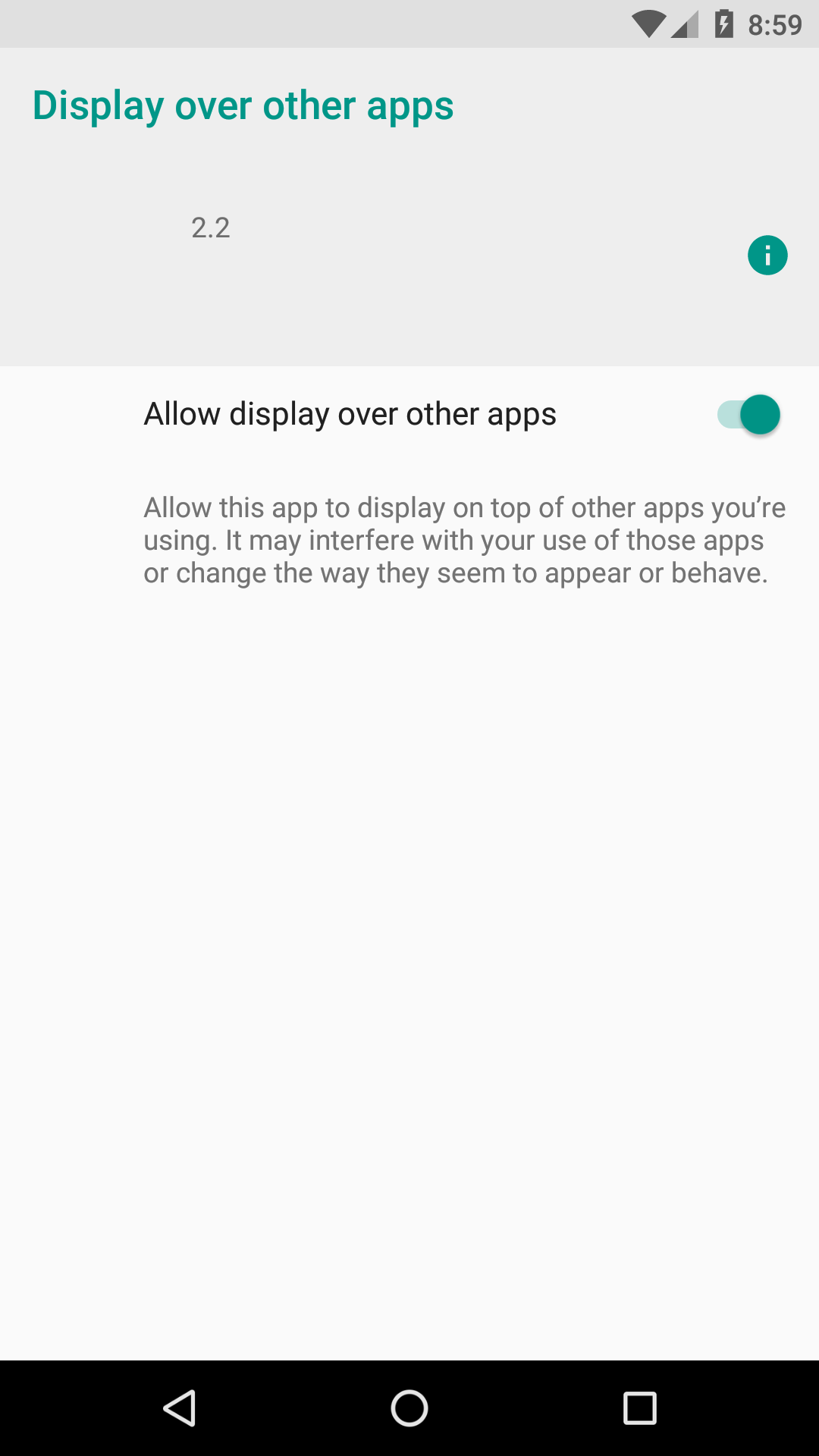
This is, of course, so it can display all the ads it serves.
After that, the app opens and asks for a Connection request to “set up a VPN connection that allows it to monitor network traffic.” Establishing a VPN connection is not unusual for an ad blocker, so why wouldn’t you click OK?
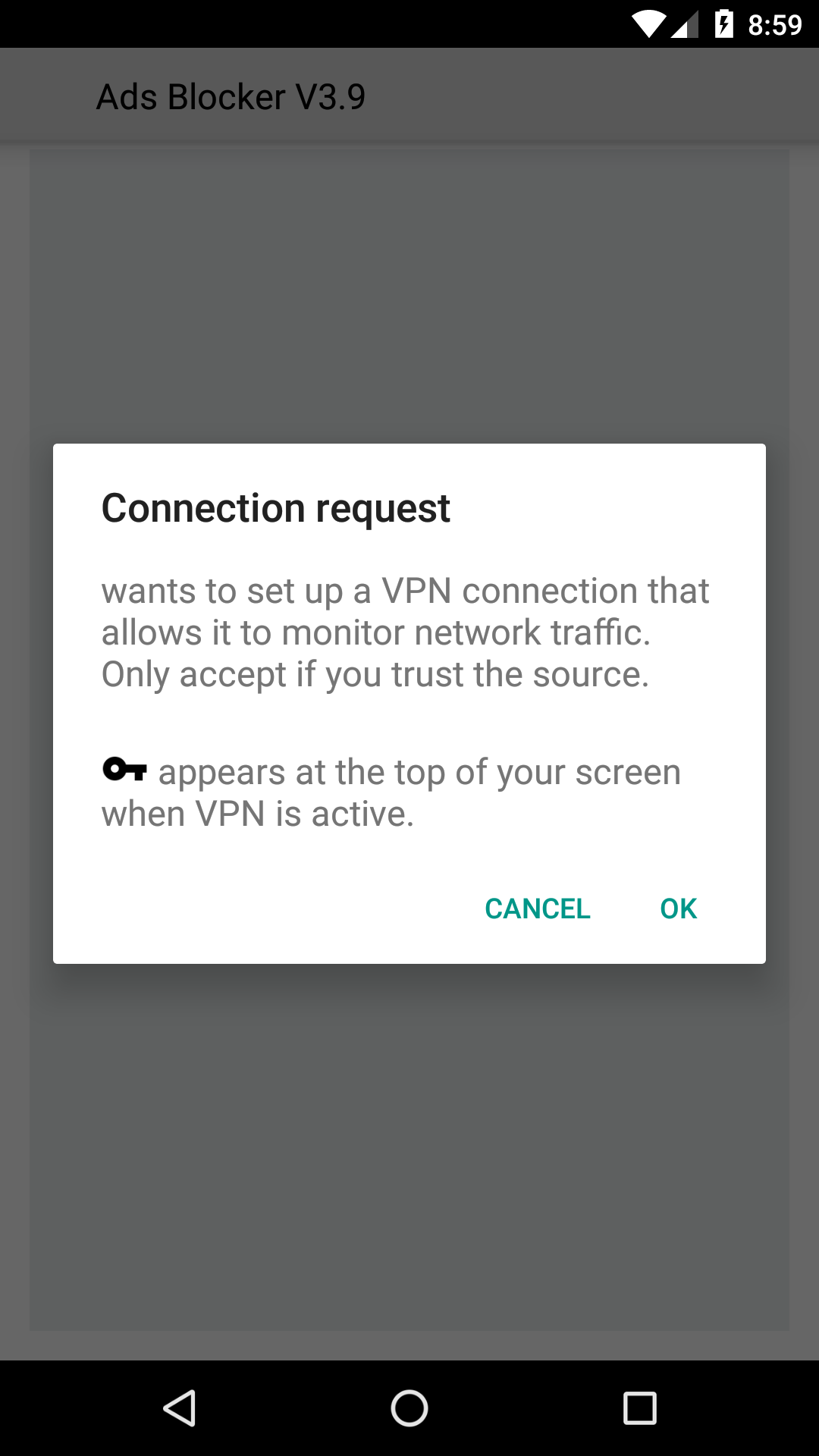
To clarify, the app doesn’t actually connect to any VPN. Instead, by clicking OK, users actually allow the malware run in the background at all times.
Next up is a request to add a home screen widget.
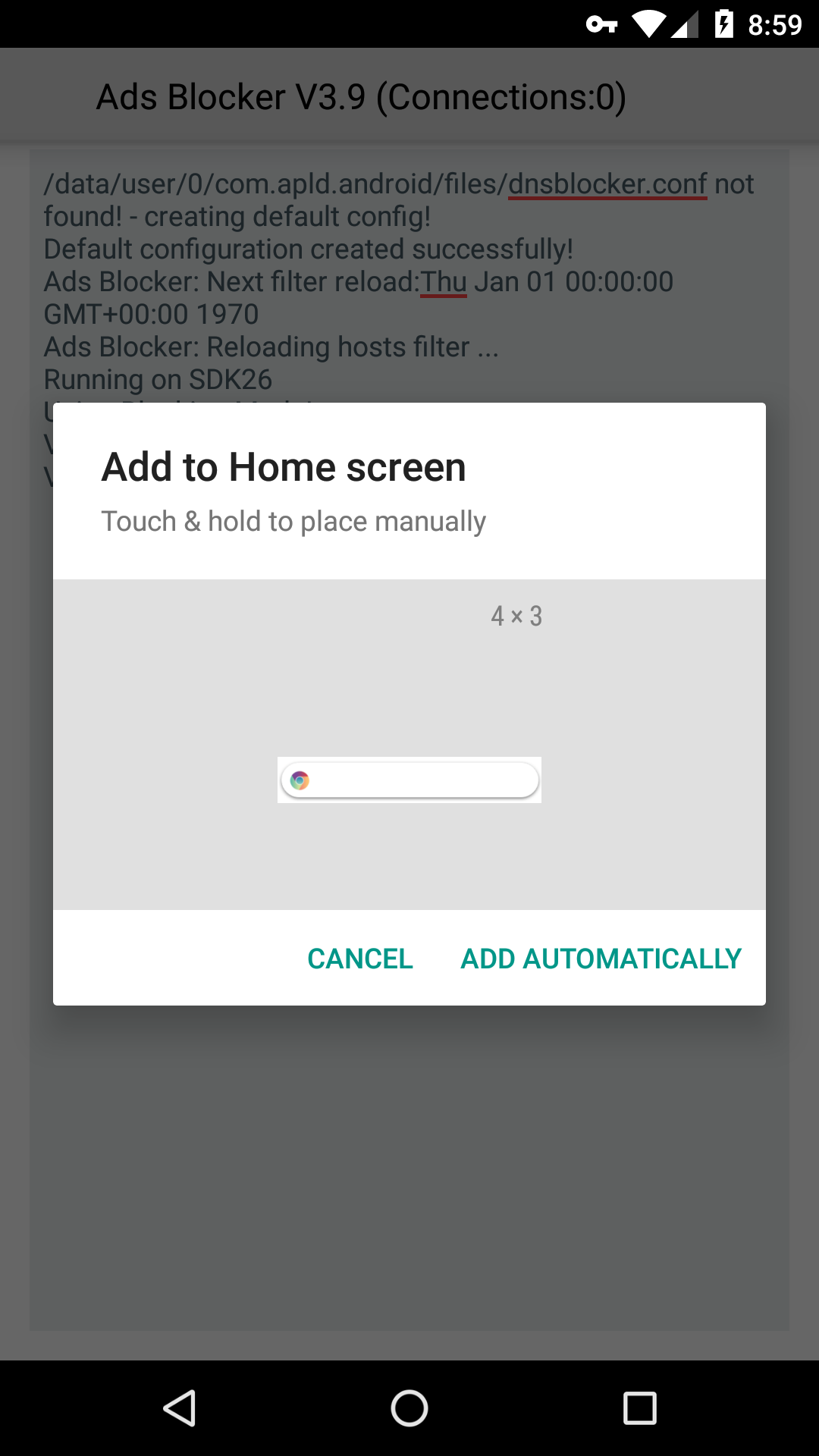
This is where things get suspicious. The added widget is nowhere to be found. On my test device, it added the widget to a new home screen page. Good luck finding and/or clicking it though.
The fake ad blocker then outputs some jargon to make it look legit.
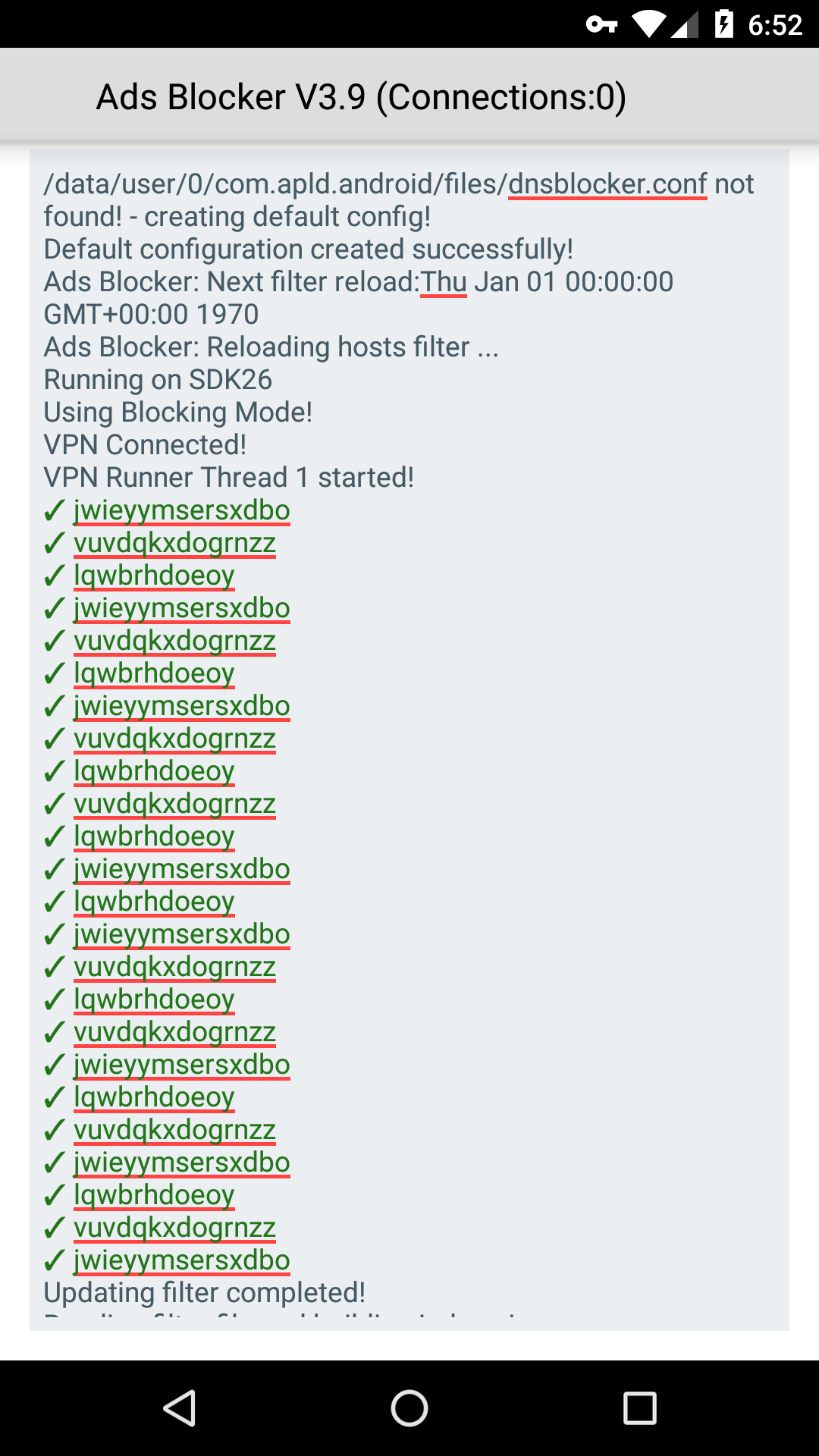
Take a good look, because this will most likely be the last time you’ll see this supposed ad blocker if you are one of the many unfortunate victims of its infection.
Extreme stealth
Ads Blocker is inordinately hard to find on the mobile device once installed. To start, there is no icon for Ads Blocker. However, there are some hints of its existence, for example, a small key icon status bar.

This key icon was created after accepting the fake VPN connection message, as shown above. As a result, this small key is proof that the malware is running the background.
Although hard to spot, another clue is a blank white notification box hidden in plain sight.
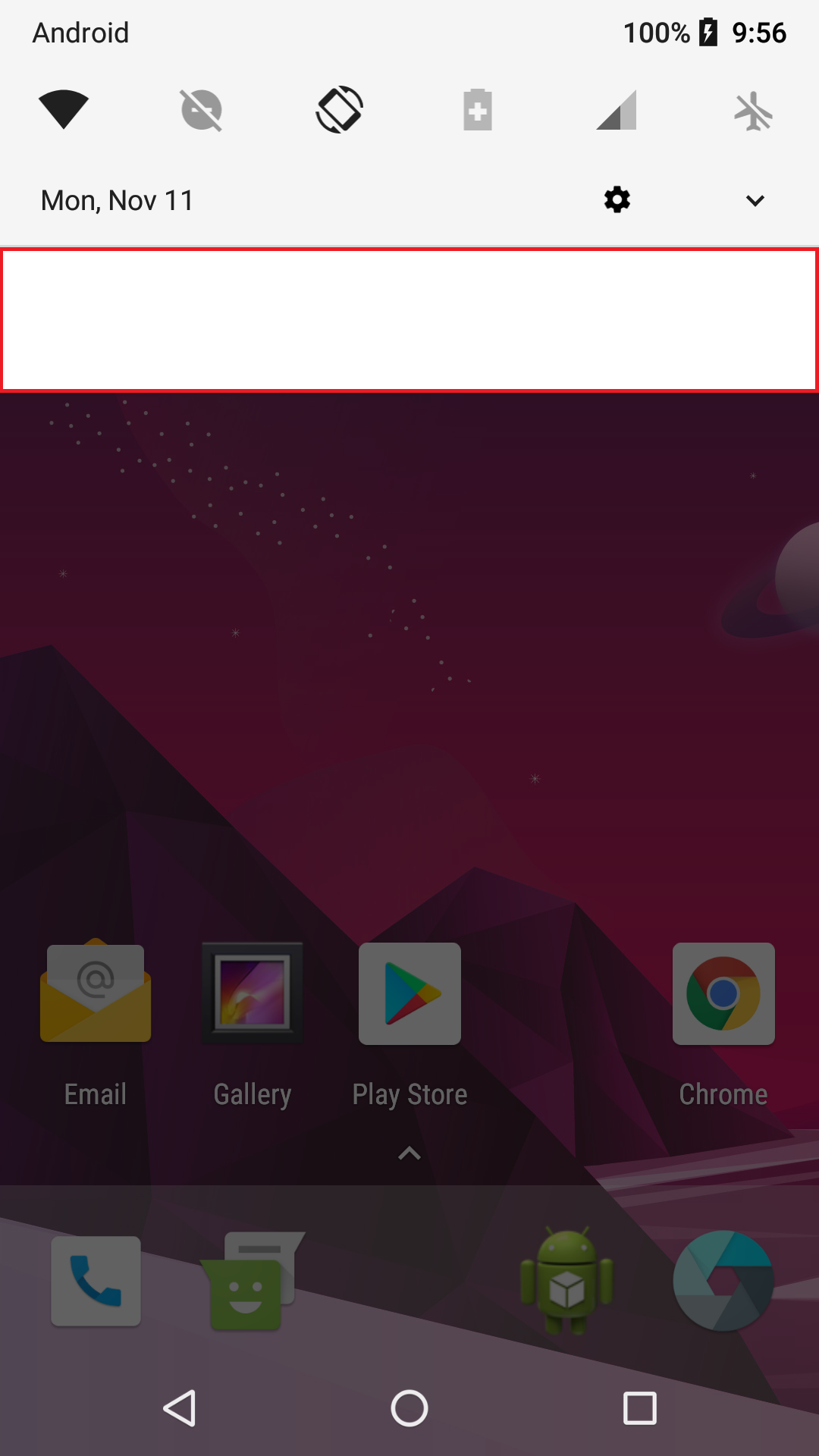
Warning: If you happen to press this blank notification, it will ask permission to Install unknown apps with a toggle button to Allow from this source. In this case, the source is the malware, and clicking on it could allow for the capability to install even more malware.
If you try to find Ads Blocker on the App info page on your mobile device to remove manually, it once again hides itself with a blank white box.
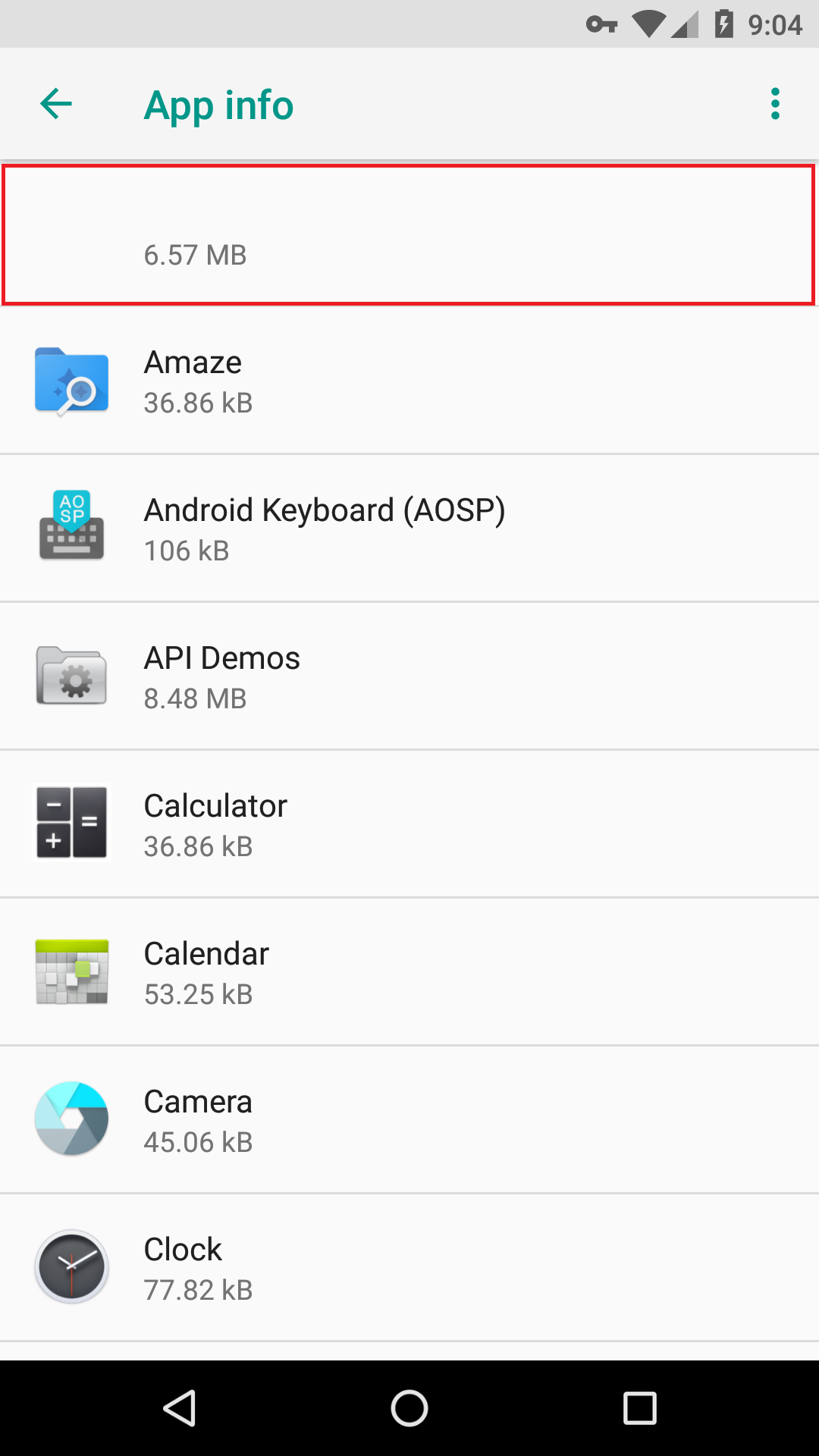
Luckily, it can’t hide the app storage used, so the floating 6.57 MB figure show above can assist in finding it. Unless you spot this app storage number and figure out which app it belongs to (by process of elimination), you won’t be able to remove Ads Blocker from your device.
Android malware digs in its fangs
This Android malware is absolutely relentless in its ad-serving capabilities and frequency. As a matter of fact, while writing this blog, it served up numerous ads on my test device at a frequency of about once every couple minutes. In addition, the ads were displayed using a variety of different methods.
For instance, it starts with the basic full-page ad:
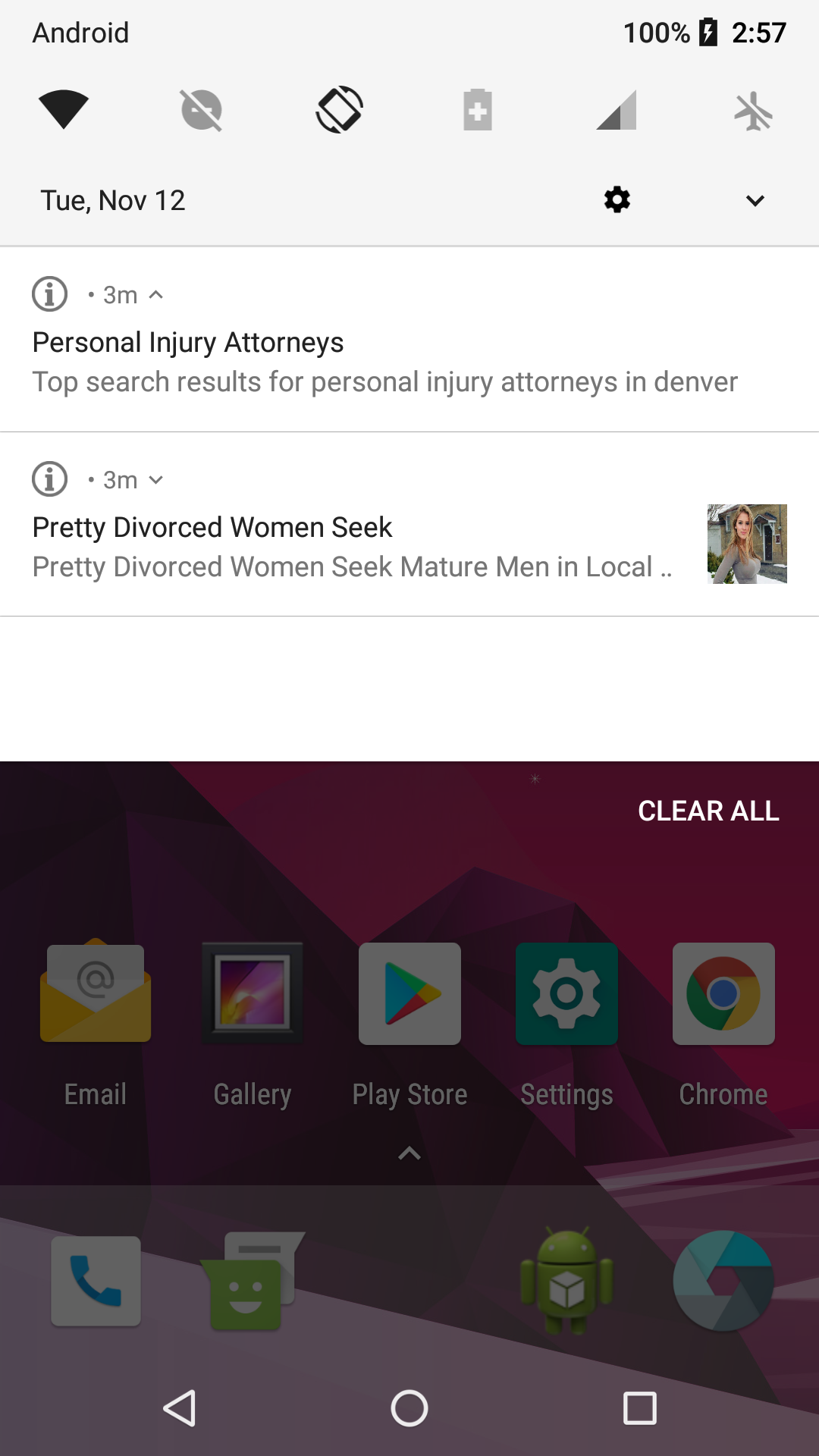
In addition, it offers ads in the notifications:
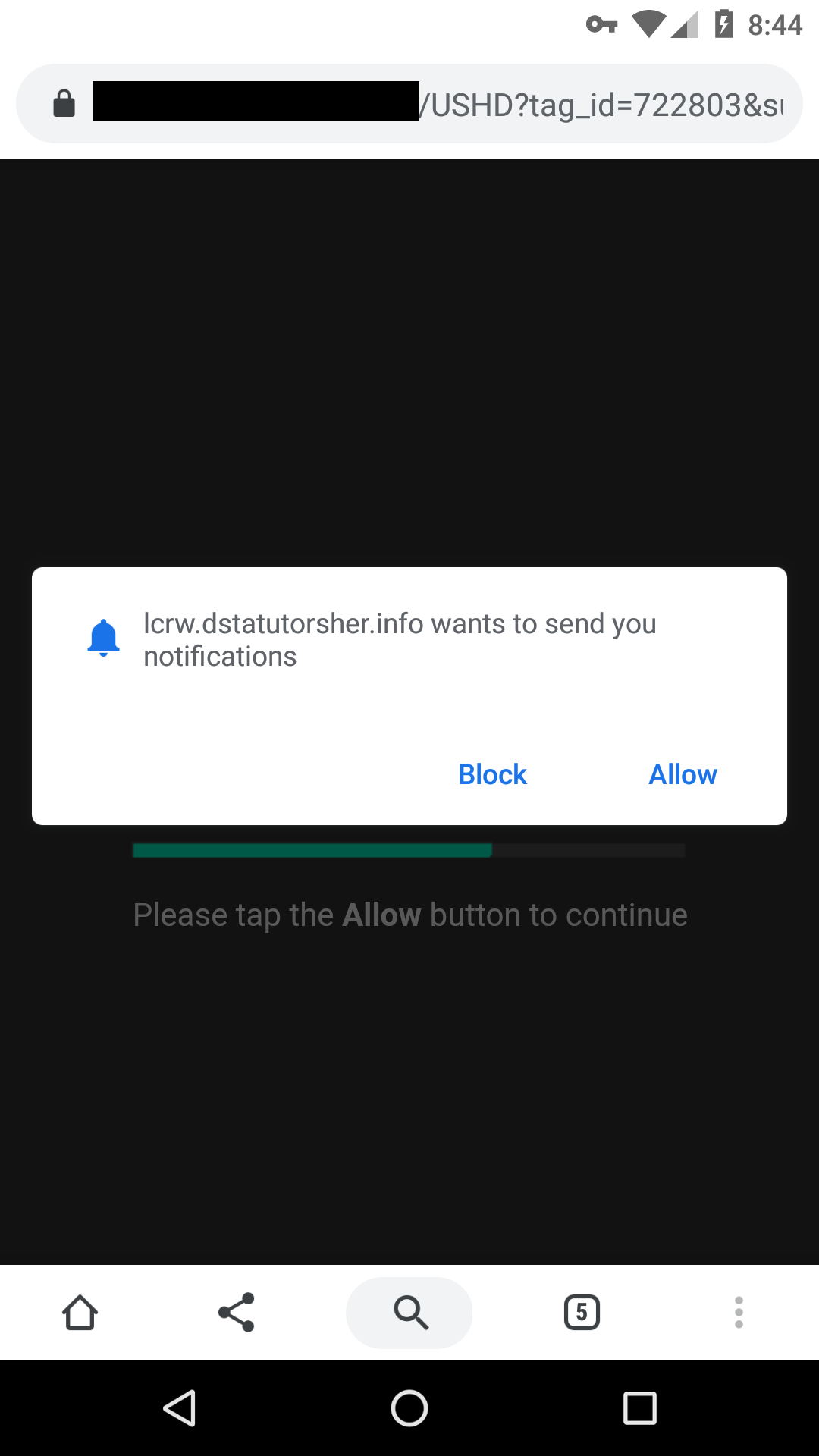
Oh look, it wants to send ads through the default web browser:
Last, remember the request to add a widget to the home screen that seemed to be invisible? Invisible widget presents: even more ads.

The ads themselves cover a wide variety of content, and some are quite unsavory—certainly not what you want to see on your mobile device.
Infections on the rise
Needless to say, this stealthy Android malware that plasters users with vulgar ads is not what folks are looking for when they download an ad blocker. Unfortunately, we have already counted over 500 detections of Android/Trojan.FakeAdsBlock. Moreover, we collected over 1,800 samples in our Mobile Intelligence System of FakeAdsBlock, leading us to believe that infection rates are quite high. On the positive side, Malwarebytes for Android removed more than 500 infections that are otherwise exceedingly difficult to remove manually.
Source of infection
It is unclear exactly where this Android malware is coming from. The most compelling evidence we have is based on VirusTotal submission data, which suggests the infection is spreading in the United States. Most likely, users are downloading the app from third-party app store(s) looking for a legitimate ad blocker, but are unknowingly installing this malware instead.
Moreover, from the filenames of several submissions, such as Hulk (2003).apk, Guardians of the Galaxy.apk, and Joker (2019).apk., there’s also a connection with a bogus movie app store as another possible source of infection.
Additional evidence demonstrates the Android malware might also be spreading in European countries such as France and Germany. A forum post was created on the French version of CCM.net regarding Ads Blocker, and a German filename was submitted to VirusTotal.
A new breed of mobile malware
A new breed of stealthy mobile malware is clearly on the uptick. Back in August, we wrote about the hidden mobile malware xHelper, which we detect asAndroid/Trojan.Dropper.xHelper. At that time, xHelper had already been removed from 33,000 mobile devices—and the numbers continue to grow. Ads Blocker is even more stealthy and could easily reach the same rate of infection.
You can call it shameless plugging if you like, but this trend of stealthy Android malware highlights the necessity of a good mobile anti-malware scanner, like Malwarebytes. With more and more users turning to their mobile phones for banking, shopping, storing health data, emailing, and other sensitive, yet important functions, protecting against mobile malware has become paramount. Beware of third-party app stores, yes, but have backup in case apps like Ads Blocker have you fooled.
Stay safe out there!