[Update: Kaspersky has updated their ShadeDecryptor tool to include decryption for the keys released by “shade team”. You can download the tool and find instructions here.]
A GitHub user claiming to represent the authors of the Troldesh Ransomware calling themselves the “Shade team” published this statement last Sunday:
“We are the team which created a trojan-encryptor mostly known as Shade, Troldesh or Encoder.858. In fact, we stopped its distribution in the end of 2019. Now we made a decision to put the last point in this story and to publish all the decryption keys we have (over 750 thousands at all). We are also publishing our decryption soft; we also hope that, having the keys, antivirus companies will issue their own more user-friendly decryption tools. All other data related to our activity (including the source codes of the trojan) was irrevocably destroyed. We apologize to all the victims of the trojan and hope that the keys we published will help them to recover their data.”
Are these the real Troldesh decryption keys?
Yes. Since the statement and the keys were published the keys have been verified as our friends at Kaspersky have confirmed the validity of the keys and are working on a decryption tool. That tool will be added to the No More Ransom project. The “No More Ransom” website is an initiative by the National High Tech Crime Unit of the Dutch police, Europol’s European Cybercrime Centre, Kaspersky and McAfee with the goal to help victims of ransomware retrieve their encrypted data without having to pay the criminals.
In the past, a few decryption tools for some of the Troldesh variants have already been published on the “No More Ransom” website. We will update this post when the Kaspersky decryptor is released and would like to warn against following the instructions on GitHub unless you are a very skilled user. The few extra days of waiting shouldn’t hurt that much and a failed attempt may render the files completely useless.
When is it useful to use the Troldesh decryption tool?
Before you go off and run this expected tool on your victimized computer as soon as it comes out, check if your encrypted files have one of these extensions:
- xtbl
- ytbl
- breaking_bad
- heisenberg
- better_call_saul
- los_pollos
- da_vinci_code
- magic_software_syndicate
- windows10
- windows8
- no_more_ransom
- tyson
- crypted000007
- crypted000078
- rsa3072
- decrypt_it
- dexter
- miami_california
If the file extensions from your affected system(s) do not match one on the list above, then your files are outside of the scope of this decryption tool. If you do find a match you should wait for the decryption tool to be published.
Why would this gang publish the Troldesh decryption keys?
The reason for all this is unknown and subject to speculation. We can imagine a few different reasons. From not very likely to credible.
- Maybe their conscience caught up with them. After all they do apologize to the victims. But these are only the victims that didn’t pay or were unable to recover their files despite paying the ransom.
- The Shade team may suspect that someone has breached their key vault and they were forced or decided on their own accord to publish the keys for that reason. But we have seen no claims to support that possibility.
- The profitability of the ransomware had reached its limit. Ransom.Troldesh has been around since 2014 and we saw a steep detection spike once the threat actors ventured outside of Russian targets in February of 2019. But after that initial spike the number of detections gradually faded out. It was still active and generating money though.
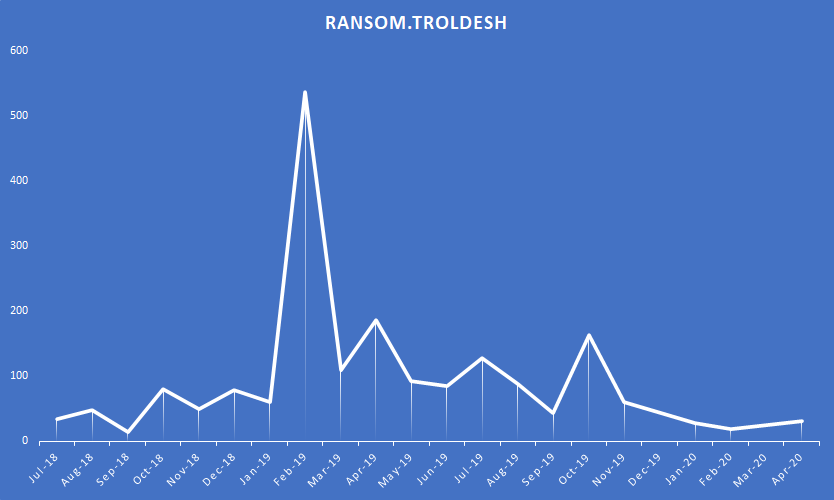
- The development of this ransomware has reached its technical limit and the team will focus on a new software project. The team stated to have stopped distribution in the end of 2019, but failed to let on what they are currently working on.
What we know
All we know for sure is that the keys have been verified and a decryption tool is in the works. All the rest are speculations based on a statement made on GitHub by an account by the name of “shade-team” that joined GitHub on April 25th, just prior to the statement.
Victims can keep their eyes peeled for the release of the decryption tool. We’ll keep you posted.
Stay safe!











