It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.
Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
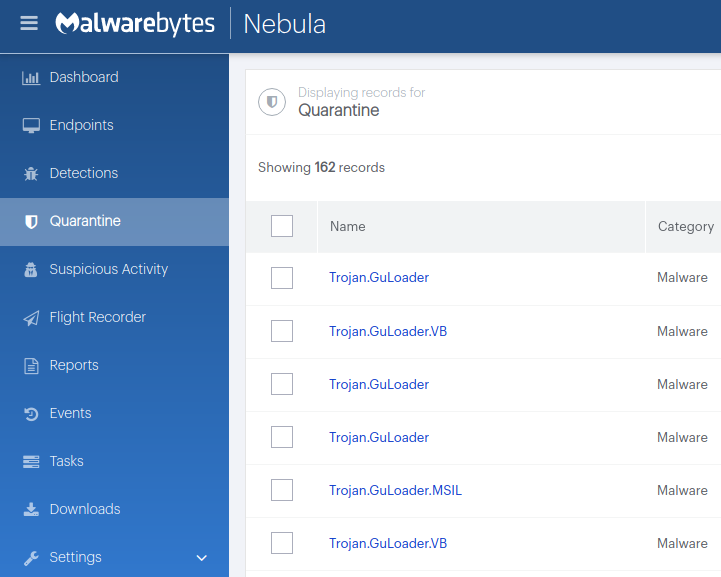
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5
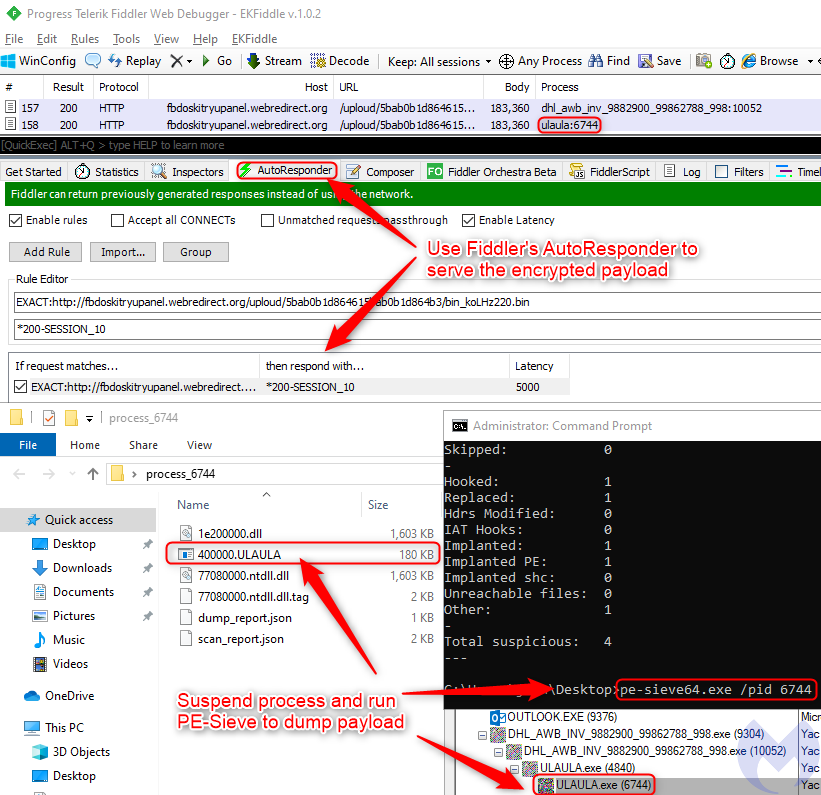
We used PE-Sieve to reconstruct the encrypted payload as a standalone PE file. This allows us to dump the shellcode from memory into a file on disk.

It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.

Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5
GuLoader and stealers
The attachment is an ISO file type which Windows 10 can open by mounting it as a drive. Inside, it contains the GuLoader executable written in Visual Basic. Usiung a decompiler, you can reveal one of its forms, which is very typical of GuLoader:
When you execute it, it will attempt to connect to a remote server to download its payload. By the time we checked this sample, that website no longer responded. However, a PCAP file was available on VirusTotal and allowed us to ‘trick’ the malware so it would proceed to load it as normal.

We used PE-Sieve to reconstruct the encrypted payload as a standalone PE file. This allows us to dump the shellcode from memory into a file on disk.

It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.

Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5
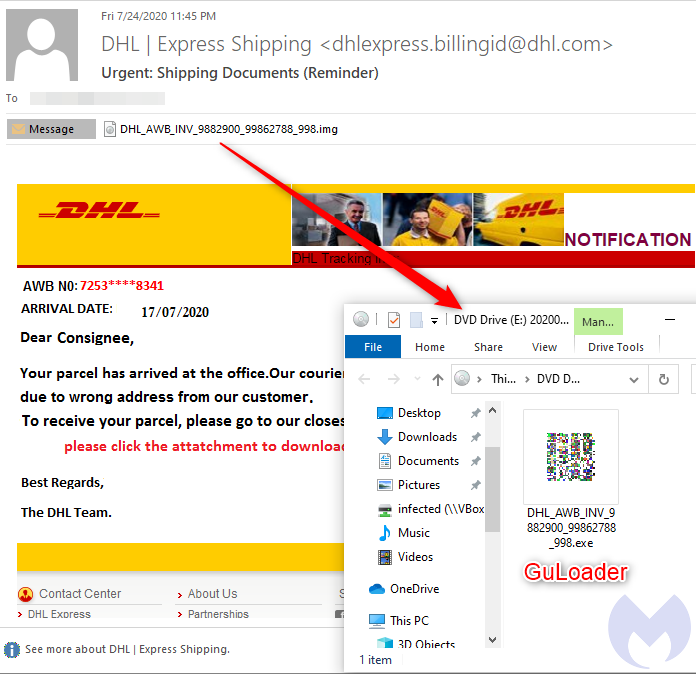
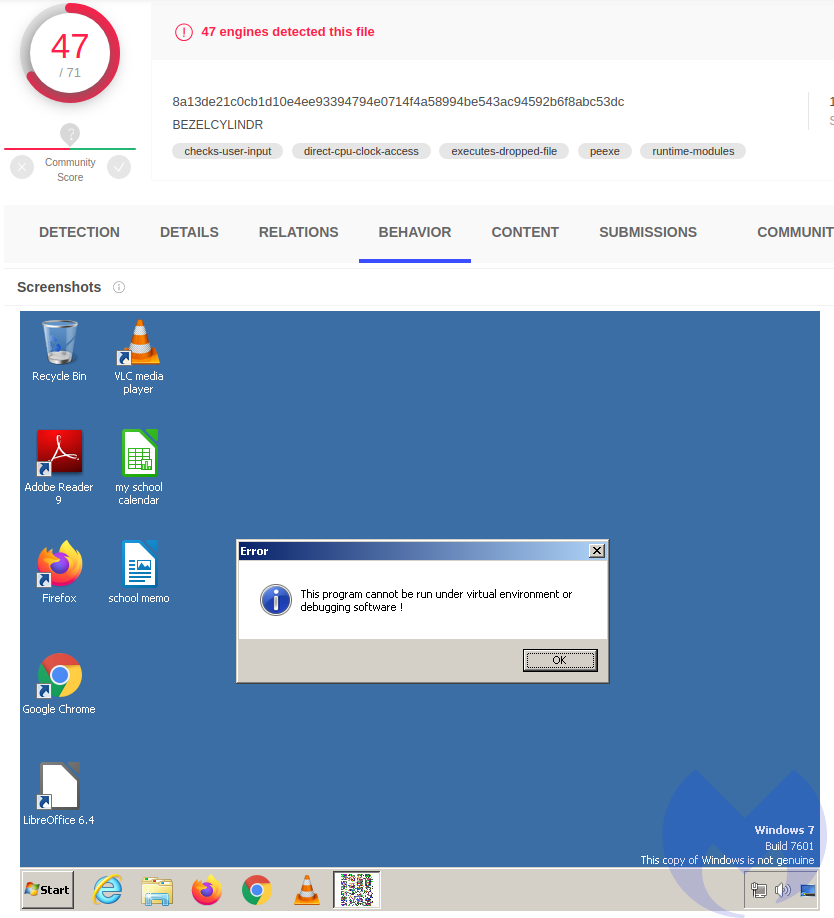
What prompted us to visit the company’s website and see this announcement was seeing GuLoader in the wild back again. We noted malspam activity using the classic DHL delivery lure pushing GuLoader again:

GuLoader and stealers
The attachment is an ISO file type which Windows 10 can open by mounting it as a drive. Inside, it contains the GuLoader executable written in Visual Basic. Usiung a decompiler, you can reveal one of its forms, which is very typical of GuLoader:
When you execute it, it will attempt to connect to a remote server to download its payload. By the time we checked this sample, that website no longer responded. However, a PCAP file was available on VirusTotal and allowed us to ‘trick’ the malware so it would proceed to load it as normal.

We used PE-Sieve to reconstruct the encrypted payload as a standalone PE file. This allows us to dump the shellcode from memory into a file on disk.

It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.

Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5
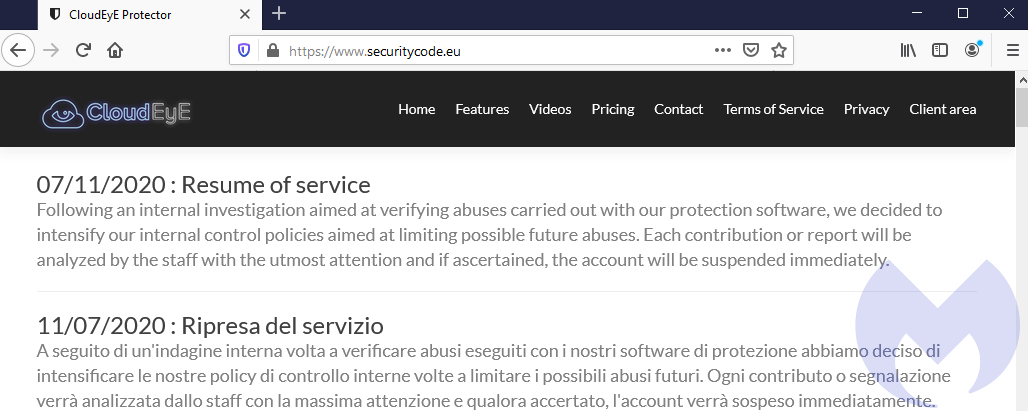
Back in business
On July 11, CloudEye announced it was resuming its business after about a month of interruption during which time sales stopped and accounts used by malicious actors were banned.

What prompted us to visit the company’s website and see this announcement was seeing GuLoader in the wild back again. We noted malspam activity using the classic DHL delivery lure pushing GuLoader again:

GuLoader and stealers
The attachment is an ISO file type which Windows 10 can open by mounting it as a drive. Inside, it contains the GuLoader executable written in Visual Basic. Usiung a decompiler, you can reveal one of its forms, which is very typical of GuLoader:
When you execute it, it will attempt to connect to a remote server to download its payload. By the time we checked this sample, that website no longer responded. However, a PCAP file was available on VirusTotal and allowed us to ‘trick’ the malware so it would proceed to load it as normal.

We used PE-Sieve to reconstruct the encrypted payload as a standalone PE file. This allows us to dump the shellcode from memory into a file on disk.

It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.

Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5
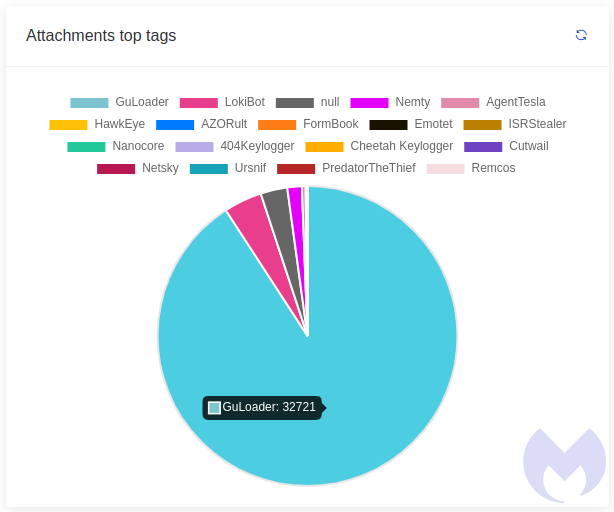
This is exactly the kind of feature criminals may want to distribute their malware. Unsurprisingly, this is exactly what happened and at one point GuLoader became the most popular malicious attachment in our spam honeypot.

Back in business
On July 11, CloudEye announced it was resuming its business after about a month of interruption during which time sales stopped and accounts used by malicious actors were banned.

What prompted us to visit the company’s website and see this announcement was seeing GuLoader in the wild back again. We noted malspam activity using the classic DHL delivery lure pushing GuLoader again:

GuLoader and stealers
The attachment is an ISO file type which Windows 10 can open by mounting it as a drive. Inside, it contains the GuLoader executable written in Visual Basic. Usiung a decompiler, you can reveal one of its forms, which is very typical of GuLoader:
When you execute it, it will attempt to connect to a remote server to download its payload. By the time we checked this sample, that website no longer responded. However, a PCAP file was available on VirusTotal and allowed us to ‘trick’ the malware so it would proceed to load it as normal.

We used PE-Sieve to reconstruct the encrypted payload as a standalone PE file. This allows us to dump the shellcode from memory into a file on disk.

It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.

Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5
They say any publicity is good publicity. But perhaps this isn’t true for CloudEye, an Italian firm that claims to provide “the next generation of Windows executables’ protection”.
First described by Proofpoint security researchers in March 2020, GuLoader is a downloader used by threat actors to distribute malware on a large scale. In June, CloudEye was exposed by CheckPoint as the entity behind GuLoader.
Following the spotlight from several security firms and news outlets, GuLoader activity dropped in late June. But around the second week of July, we started seeing the downloader in malspam campaigns again.
Protection and evasion attract criminal element
While the concept of downloaders is certainly not new, GuLoader itself found its origins in DarkEye Protector, a crypter sold in various forums circa 2011, which later evolved into CloudEye.
Designed as a product to prevent reverse engineering and protect against other forms of code theft, CloudEye is a Visual Basic 6 downloader that leverages cloud services to store and retrieve the final piece of software (in the form of heavily obfuscated shellcode) a customer wants to install.
GuLoader/CloudEye has proved to be very effective at bypassing sandboxes and security products including network-based detection.

This is exactly the kind of feature criminals may want to distribute their malware. Unsurprisingly, this is exactly what happened and at one point GuLoader became the most popular malicious attachment in our spam honeypot.

Back in business
On July 11, CloudEye announced it was resuming its business after about a month of interruption during which time sales stopped and accounts used by malicious actors were banned.

What prompted us to visit the company’s website and see this announcement was seeing GuLoader in the wild back again. We noted malspam activity using the classic DHL delivery lure pushing GuLoader again:

GuLoader and stealers
The attachment is an ISO file type which Windows 10 can open by mounting it as a drive. Inside, it contains the GuLoader executable written in Visual Basic. Usiung a decompiler, you can reveal one of its forms, which is very typical of GuLoader:
When you execute it, it will attempt to connect to a remote server to download its payload. By the time we checked this sample, that website no longer responded. However, a PCAP file was available on VirusTotal and allowed us to ‘trick’ the malware so it would proceed to load it as normal.

We used PE-Sieve to reconstruct the encrypted payload as a standalone PE file. This allows us to dump the shellcode from memory into a file on disk.

It turned out to be the FormBook stealer, which is consistent with the type of payloads we see associated with GuLoader.
Popular tool already cracked?
We believe one particular threat group is engaged in malspam campaigns with and without GuLoader, and instead using RAR attachments to spread other stealers.
Once a tool has proved to be popular and effective for criminal purposes (whether it was built for legitimate reasons or not), it will continue to fuel malware campaigns.
It’s quite possible that of the many builders of GuLoader in circulation some have been cracked and are now being used by threat actors on their own accord.
We track the GuLoader malspam campaigns and continue to protect our customers against this threat.

Thanks to S!Ri for the heads up on the return of GuLoader.
Indicators of Compromise
GuLoader
DHL_AWB_INV_9882900_99862788_998.exe
8a13de21c0cb1d10e4ee93394794e0714f4a58994be543ac94592b6f8abc53dc
Shellcode loaded by GuLoader
fbdoskitryupanel.webredirect[.]org/uploud/5bab0b1d864615bab0b1d864b3/bin_koLHz220.bin
45.76.45[.]167
Decoded shellcode into binary
7b4d3b6eb50a072d36f6233aeb56352735c59dd54ba54d6e6fbca6b23a1739d5