On January 12, 2023, the Liquor Control Board of Ontario (LCBO) published a news release about a cybersecurity incident, affecting online sales through LCBO.com. It is one of the largest retailers and wholesalers of beverage alcohol in the world.
Web skimmer
The cybersecurity incident was a web skimmer, which is designed to retrieve customer payment information. Or, in the words of the LCBO:
“an unauthorized party embedded malicious code into our website that was designed to obtain customer information during the checkout process.”
LCBO has reset all LCBO.com account passwords.
Magecart
The web skimmer was identified by experts as a Magecart web skimmer. The malicious code injected was inside a Google Tag Manager (GTM) snippet encoded as Base64. The abuse of this legitimate Google service has been ongoing because it provides attackers free infrastructure upon which they can host their scripts, while also granting enhanced capability to avoid detection.
Malwarebytes’ Director of Threat Intelligence Jérôme Segura commented:
The attack on LCBO’s online portal follows a trend we’ve seen before of injecting malicious code disguised as legitimate snippets such as Google Tag Manager. In this case, the threat actor added an extra level of stealth by loading the skimmer code via a websocket, instead of a more typical HTTP request. LCBO took quick action to take its site offline and publicly acknowledge and disclose the issue which should be commended.”
The code only loads the skimmer if the current URL contains the string ‘checkou’ (note the missing ‘t’). It then opens a websocket for communication which is more covert than a typical HTTP request. The Magecart domain is: magento-cdn[.]net, which was registered less than a month ago.
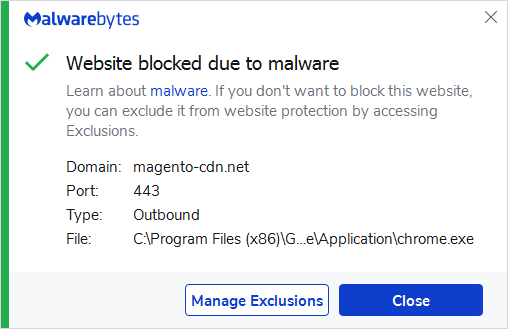
Stolen information
According to the press release, customers who provided personal information on check-out pages and proceeded to the payment page on LCBO.com between January 5, 2023, and January 10, 2023, may have had their information compromised.
The stolen information could include names, email and mailing addresses, Aeroplan numbers, LCBO.com account password, and credit card information.
LCBO is looking to contact those affected directly, but in the meantime all customers who initiated or completed payment for orders on LCBO.com during that time period should monitor their credit card statements and report any suspicious transactions to their credit card providers.
The vast majority of payment card records that are stolen by Magecart groups using the GTM container method were later offered for sale on Dark Web marketplaces.
Preventing web skimmers on your site
Operating an e-commerce website comes with certain responsibilities, especially if payment information is handled through it. It is usually a safer (and easier) practice to outsource the handling of financial transactions to larger, trusted parties. PCI compliance and risks associated with collecting data can be overwhelming, especially for site owners that would rather focus on the business side of things.
Third-party resource integrity checking is one security aspect that has been overlooked but can provide great benefits when loading external content. The reality is that a website usually cannot host all the content itself, and it makes more sense to rely on CDNs and other providers for speed and cost reasons.
This relationship does not necessarily mean having to weather the issues experienced by a third party. There are a number of threats that can be disseminated via third-party libraries. For this reason, implementing safeguards such as Content Security Policy (CSP) and Subresource Integrity (SRI) can help to mitigate many issues.
Not falling victim
One thing to keep in mind as consumers is that we are largely placing our trust in the online stores where we are shopping. For this reason, it may be wise to avoid smaller sites that perhaps do not have the same level of security as larger ones.
Using browser plugins such as NoScript can prevent JavaScript loading from untrusted sites and therefore reduces the surface of attack. However, it has the same shortcomings when malicious code is embedded in already trusted resources.
Magecart and other web skimmers can be mitigated at the exfiltration layer, by blocking connections to known domains and IPs used by the attackers. It is not foolproof, though, considering how trivial it is to register new properties. But infrastructure reuse is something we still see quite often.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











