Staff in the hospitality industry are trained to accommodate their guests, and when they have a few years of experience under their belt you can be sure they’ll have received some extraordinary requests.
Which is something that clever cybercriminals are taking advantage of. Researchers at Perception Point recently documented a sophisticated phishing campaign targeting hotels and travel agencies.
The campaign raised alarm because of the clever scheme deployed to trick staff into installing an information stealer. This part of the campaign is made up out of highly targeted attacks.
The first stage of the attack typically sees the attackers send a query about a booking or make a reservation. The bookings will always have low or no cancellation costs so the attackers can minimize their investment.
Once the attackers receive a response, they’ll come up with a persuasive reason for the hotel staff to print or study something ahead of their arrival. Examples include medical records for a child or an important map they would like to print out for their elderly parents.
To add a touch of legitimacy and to evade detection, they even provide the hotel representative with a password to unlock these so-called “important files.”
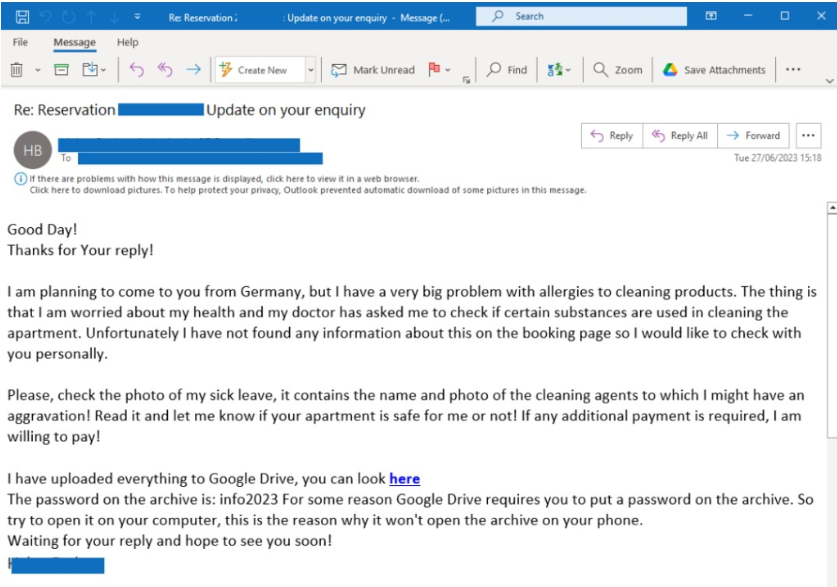
Image courtesy of Perception Point
In reality, the document contains malware hosted on a file sharing platform, such as Google Drive. The file is encrypted but is decrypted when the victim enters the password. The main executable file often has a misleading icon, such as one that makes it look like a pdf. Once the victim double-clicks on the file, the information stealer (or InfoStealer) is then unleashed.
The second step in this attack targets the customers, and was discovered by Akamai researchers.
After the InfoStealer is executed on the original target’s (hotel/travel agent’s) systems, the attacker then begins messaging legitimate customers. The message used in this campaign contains a link to what it says is an additional card verification step. In reality, the link triggers an executable on the victim’s machine which gathers information about the browser and presents the recipient with several security validation questions.
Once the victim passes the tests, they are forwarded to a credit card phishing site masquerading as a Booking.com payment page.
Tips for hospitality organizations
Besides having adequate up-to-date real-time protection on your systems, there are some general tips that can keep you out of trouble.
- Always confirm the identity of anyone requesting sensitive information or access to internal systems.
- Educate your team so they know how to recognize phishing attempts and where to report potential threats.
- Invest in an email security solution which makes it harder for phishing emails and unknown malware to reach the intended target.
- Never click on unsolicited links.
- Be cautious of messages that create a sense of urgency or threaten negative consequences if you don’t take immediate action.
Tips for consumers
These phishing schemes are exceptionally well thought out and tailored so victims are more likely to click. Still, there are some red flags that can help you prevent falling victim.
- Double check unexpected communications which ask for additional payments or payment details. There is no harm in asking for clarification or confirmation.
- Inspect links before you click on them to see whether they lead to where you expect.
- Do not send information that the booked accommodation should already have or shouldn’t need at all.
- Be suspicious of urgent or threatening messages asking for immediate action.
Identity theft victims
If you suspect you are a victim of credit card identity theft, the FTC recommends you contact your bank or credit card company to cancel your card and request a new one. If you get a new card, don’t forget to update any automatic payments with your new card number.
To find out if you are a victim:
- Review your transactions regularly to make sure no one has misused your card, and consider credit monitoring.
- If you find fraudulent charges, call your bank’s fraud department to alert them.
- Check your own credit report at annualcreditreport.com.
- Consider freezing your credit report. This stops new creditors and potential thieves from accessing your credit report.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











