The City of Columbus, Ohio is suing a security researcher for sharing stolen data.
All the complaint will accomplish, we imagine, is spotlight the ignorance of certain city officials in handling a common security matter.
What happened is that the City of Columbus was attacked by a ransomware group on July 18, 2024. Due to the timing, it was at first unclear whether the disruption in the public facing services was caused by the CrowdStrike incident or if it was in fact an attack. The attack was later claimed by the Rhysida ransomware group on their leak site, where the group posts information about recent victims that are unwilling to pay.
The City of Columbus said that the city’s Department of Technology quickly identified the threat and took action to significantly limit potential exposure. Due to the swift action no systems had been encrypted, but they were looking into the possibility that sensitive data might have been stolen in the attack.
“The city is in the process of identifying individuals whose personal information was potentially exposed and will provide notice and additional guidance to all who are impacted in the coming weeks.”
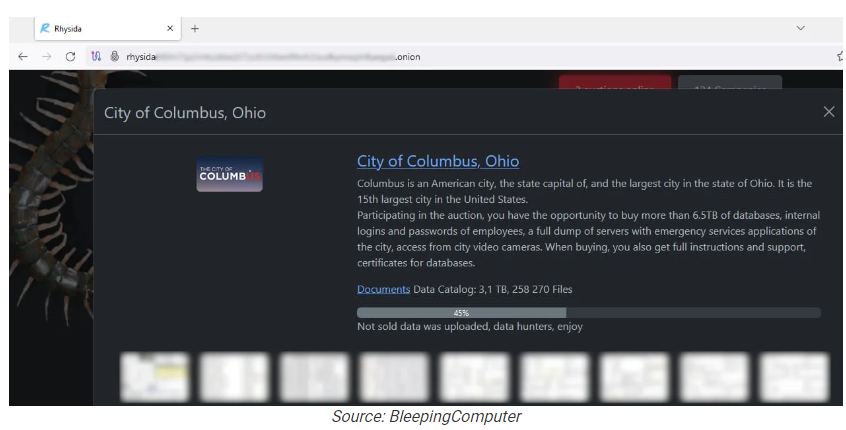
Rhysida started an auction to buy the stolen data with a starting bid of about $1.7 million in bitcoin. When that didn’t render any results, Rhysida published (please note the word “published” here, it’s important) stolen data comprising 260,000 files (3.1 TB) which was almost half of what they claimed to have, on August 8, 2024.
On that same day, the mayor of Columbus stated on local media that the disclosed information was neither valuable nor usable.
“The fact that the threat actor’s attempted data auction failed is a strong indication that the data lacks value to those who would seek to do harm or profit from it.”
This is where an external security researcher comes in. Security researcher David Leroy Ross, aka Connor Goodwolf, shared information with the media about the content of the stolen data. From what Goodwolf shared it became clear that the data contained unencrypted personal information of city employees and residents.
So, the City of Columbus decided to sue Goodwolf for alleged damages for criminal acts, invasion of privacy, negligence, and civil conversion.
The lawsuit claimed that downloading documents from a dark web site run by ransomware attackers amounted to him interacting with the ransomware group and that it required special expertise and tools.
When all he did was use a special browser to visit a website, download a file, and disclose the nature of the data to the local press. These actions, mind you, indistinguishable from the work of many security researchers committed to stopping cyberattacks.
Take, for instance, the means of access for Goodwolf.
If you are willing to consider the Tor Browser to be a special tool, I’ll grant you that one, although grudgingly. If you are a Firefox user, you may see a big resemblance with the Tor Browser, so the browser is not really that special. If visiting a website and downloading a file is a crime, we’re all guilty of said crime. If disclosing that a public official told an untruth (even if it was out of ignorance) is wrong then you probably shouldn’t want to live in a democratic country.
But unfortunately, a Franklin County judge issued the coveted temporary restraining order barring Goodwolf from accessing, downloading, and disseminating the City’s stolen data. The order also requires the defendant to preserve all data that was downloaded to date.
We want to make absolutely clear: Rhysida stole and published the data. And it was spokespeople from The City of Columbus that told everyone not to worry about other criminals using the data for further crimes, instead of warning the people that they should be wary of phishing attempts that could leverage the stolen data against them.
Protecting yourself after a data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened, and follow any specific advice they offer.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the vendor website to see if they are contacting victims, and verify the identity of anyone who contacts you using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Consider not storing your card details. It’s definitely more convenient to get sites to remember your card details for you, but we highly recommend not storing that information on websites.
- Set up identity monitoring. Identity monitoring alerts you if your personal information is found being traded illegally online, and helps you recover after.
Check your digital footprint
If you want to find out what personal data of yours has been exposed online, you can use our free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and we’ll send you a free report.
We don’t just report on threats—we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your, and your family’s, personal information by using identity protection.











