The media home page of Australia’s largest telecommunications company, Telstra, was pushing some malvertising similar to the attack we just documented on the PlentyOfFish website.
The infection chain goes like this:
- media.telstra.com.au/home.html (Publisher)
- frexw.co.uk/public/id-55048502/300×250.php (Malvertising)
- gp-urti.info/bard-vb4735/vcyz-46820t.js (Malicious redirector)
- goo.gl/s3LrVw (Abuse of Google URL shortener to load an exploit kit)
- augpdoiof.info/document.shtml?AfWlx={redacted} (Nuclear Exploit Kit)
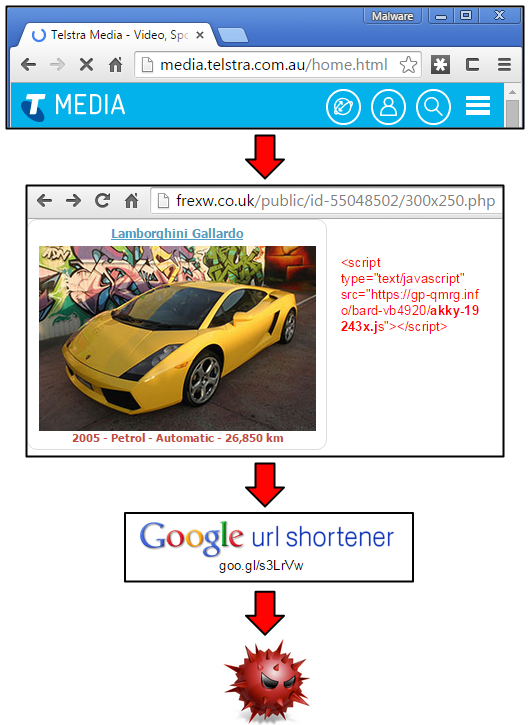
While we did not collect the particular sample dropped in this campaign, it is quite likely to be the Tinba banking Trojan, just as we observed on POF.com.
The Google link has now been disabled:
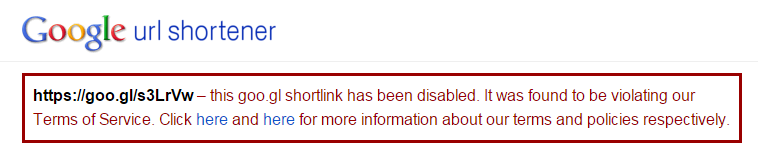
The malvertising attack lasted for a few days and was last seen on the 17th.










