Cleafy, a cybersecurity firm specializing in online fraud, has published new detailsabout banking Trojan BRATA (Brazilian Remote Access Tool, Android), a known malware strain that first became widespread in 2019.
BRATA is now being used to perform factory resets on victims’ machines. It’s rare for malware to damage or wipe victims’ machines (there is rarely anything in it for the attackers) so what’s going on here?
According to Cleafy, the victim’s Android device is factory reset after the attackers siphon money from the victim’s bank account. This distracts users from the crime, while removing traces or footprints that might be of interest to forensic analysts.
Out with the old
BRATA used to target Brazilian banks exclusively, but Cleafy reports that the target list has now been expanded to include banks in Italy, the UK, US, Poland, Spain, and Latin America. It has also revealeda number of new capabilities, alongside the factory reset functonality:
- A GPS tracking capability
- Multiple methods of maintaining contact with command and control (C2) servers
- The ability to use a VNC (Virtual Network Computing) and keylogging to continuously monitor a victim’s bank account
But how does such dangerous malware end up on victims’ devices?
How BRATA is spread
A BRATA campaign starts off when a potential target receives an SMS claiming to be from their bank. The SMS contains a link to a website that encourages the target to download the BRATA malware. They also receive a call from an attacker, who pretends to work for the bank.
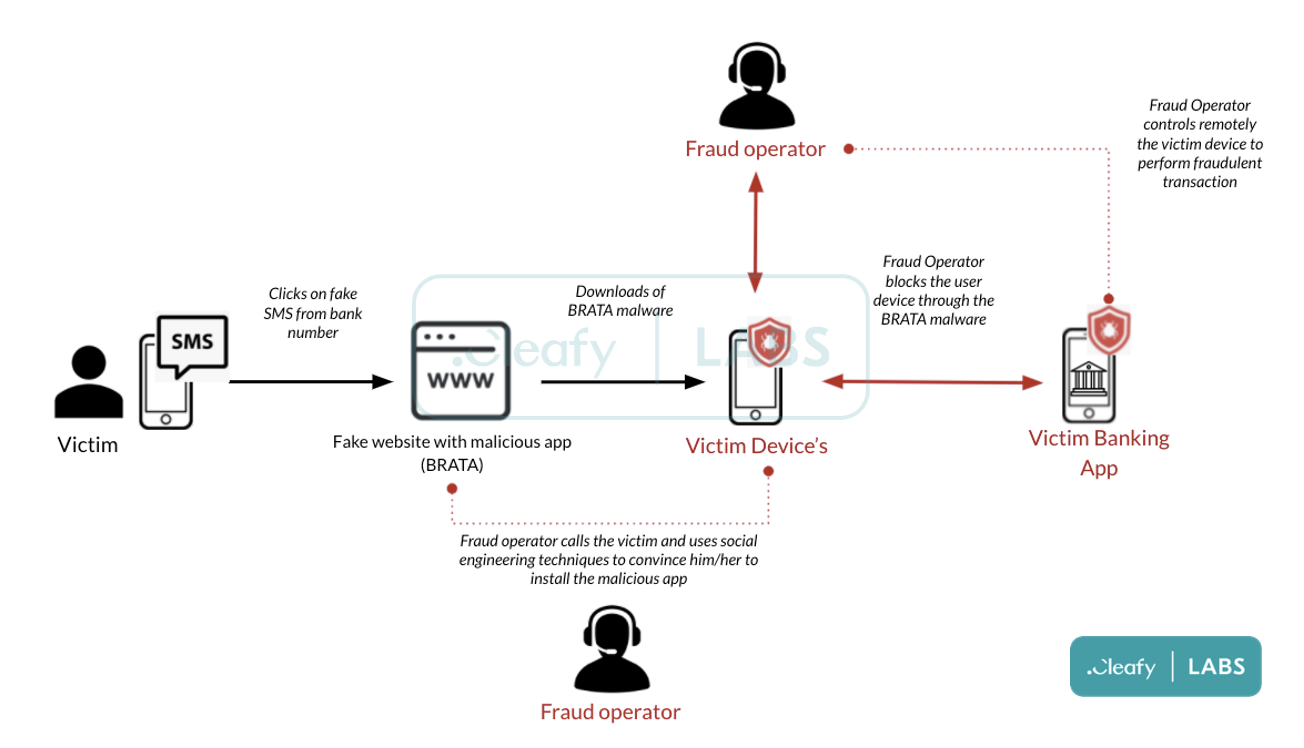
The app asks for multiple permissions that, to the trained eye, would raise some red flags, and might make users reluctant to install it. According to Cleafy, the caller’s first job is therefore to use social engineering tactics to convince victims to install it.
Once the app is installed, the fraudsters can remotely hijack the device whenever they want to, and can perform banking transactions without the target knowing. Not only that, the app can be used to initiate admin-level actions, such as locking the screen, changing the screen lock, and setting password rules. For the most recent BRATA strain, being an admin app also allows it to initiate a factory reset on the affected mobile device.
A two-factor authentication (2FA) code from the bank does not protect accounts here. Through BRATA, the 2FA codes from banks are intercepted and sent to the fraudster’s command and control sever.
Clearfy believes that current operators of the BRATA mobile malware are based in at least one country in Europe as mule accounts linked to this campaign were found in Italy, Lithuania, and the Netherlands.
Protect yourself from BRATA
The existence of this malware is a reminder to all Android users to avoid installing apps that don’t come from Google Play, and to pay attention to the permissions that apps ask for. For example, BRATA requests access to the “Erase all data” permission, and most of us don’t want apps that can do that running on our mobile devices.
Although this version of BRATA was not found on Google Play, in the past it has been found, called out, and removed from Google’s online store. So, even when you’re using Google Play, stay vigilant and make sure to keep your mobile antivirusrunning in real time and up to date.
IOCs:
- E00240F62EC68488EF9DFDE705258B025C613A41760138B5D9BDB2FB59DB4D5E – Malwarebytes detects it as Android/Trojan.Agent.PWSCR
- E769EF0D011CBF3322C9E85D4CDF70AF413F021D033AED884C1431F2B7861D0D – Malwarebytes detects it as Android/Trojan.Spy.Agent.GPPSSATB
- 2846C9DDA06A052049D89B1586CFF21F44D1D28F153A2FF4726051AC27CA3BA7 – Malwarebytes detects it as Android/Trojan.Spy.Brat.dsa
- F9DC40A7DD2A875344721834E7D80BF7DBFA1BF08F29B7209DEB0DECAD77E992 – Malwarebytes detects it as Android/Trojan.Spy.Brat.gvmb
- 4CDBD105AB8117620731630F8F89EB2E6110DBF6341DF43712A0EC9837C5A9BE – Malwarebytes detects it as Android/Trojan.Spy.Brat.oupa
- D9BC87AB45B0C786AA09F964A8101F6DF7EA76895E2E8438C13935A356D9116B – Malwarebytes detects it as Android/Trojan.Spy.Brat.prta
- 648A5A705BBE88E52569B3774A689A82F53962E8827B143189639D48727BD159 – Malwarebytes detects it as Android/Trojan.Spy.SpyNote.dcnp










