This blog post was authored by Jérôme Segura
Viral content shared on social media is highly coveted since it gets a lot of impressions and engagement. Unfortunately, the people who push this kind of content don’t always have the best of intentions.
We recently identified a malvertising campaign on Facebook that uses a cute story that gained attention last year. The fraudsters are luring potential victims into clicking on its link so that they are conditionally redirected to a fake tech support page.
This technique is far from being new but yet still works really well and deserves to be analyzed once again so that affected parties better understand how they are being abused.
Too cute to be true
The scam starts with the sweet story of a man who jumped out of his car at a traffic light to have his puppy meet another dog. This moment was shared on a number of platforms last year and could melt any animal lover’s heart.
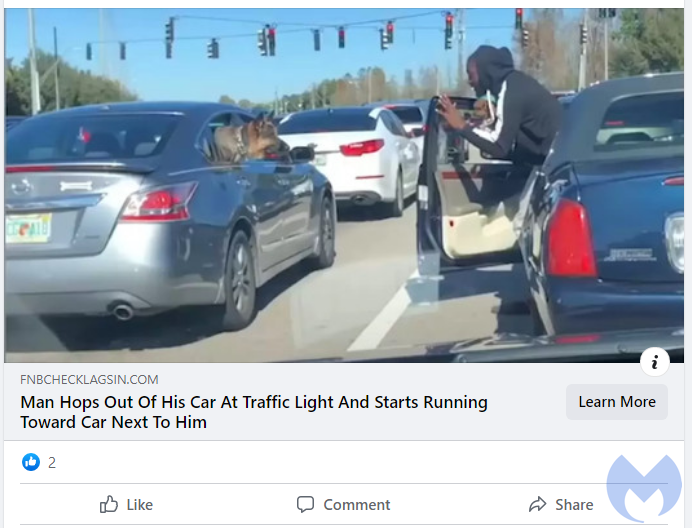
We saw this post on Facebook and it has been viewed and shared since at least mid July. Yet, in this case, the link is a trap set to redirect potential victims to a malicious page known as a browser locker. While it does not actually ‘lock’ anything, the page displays fake messages about computer viruses and entices users to call for assistance. What follows after are the well-known tech support scams.
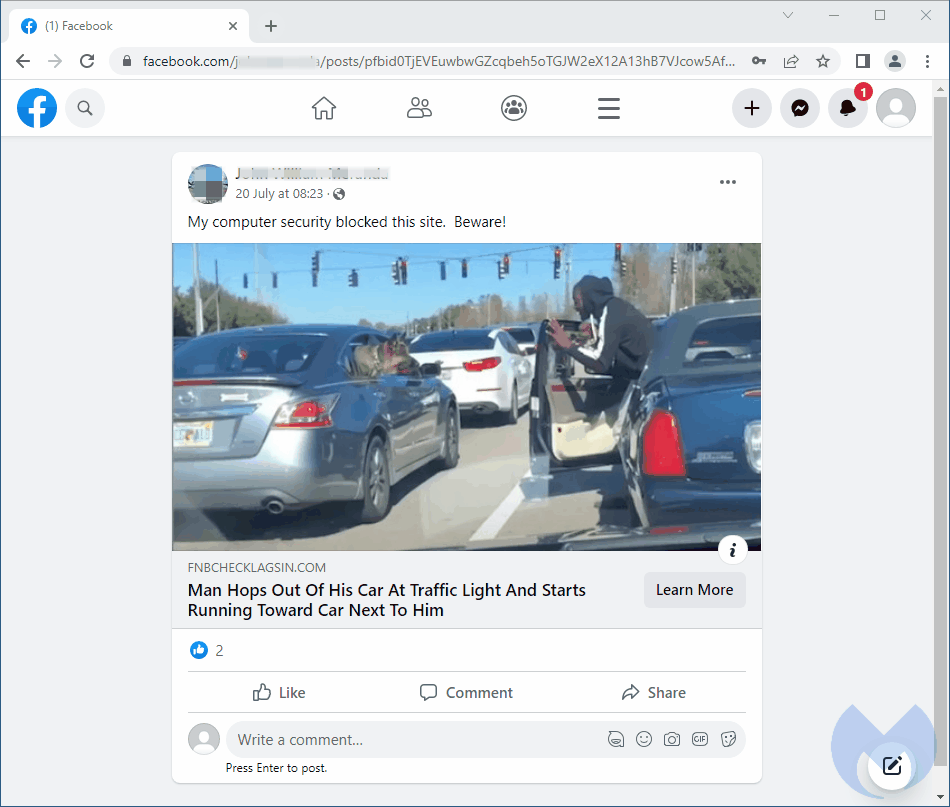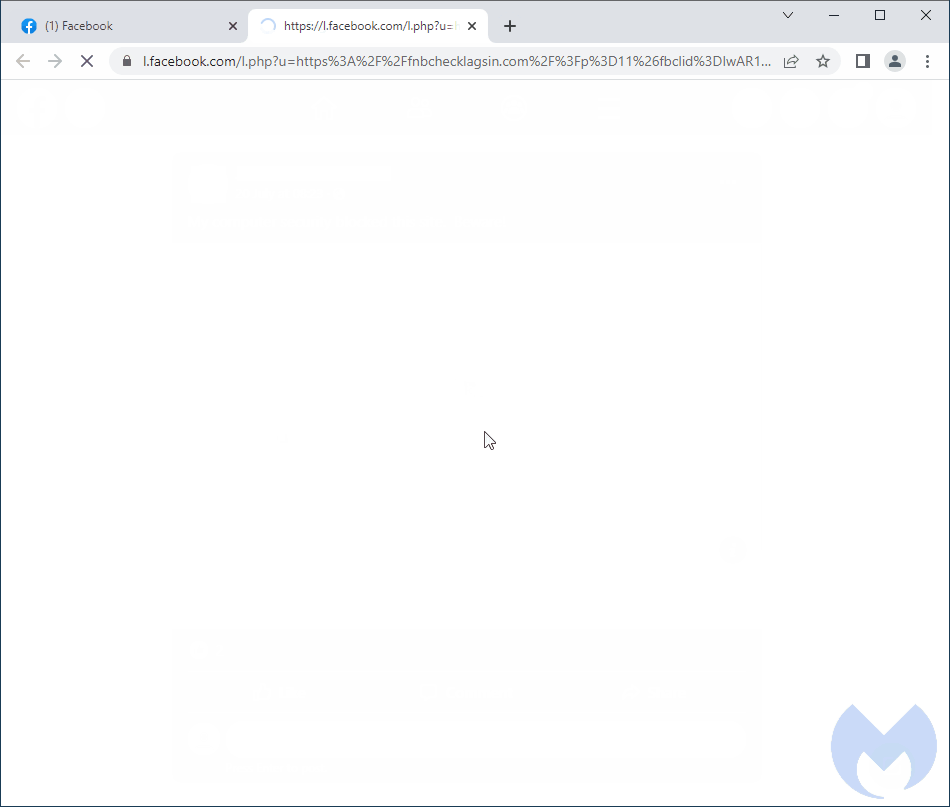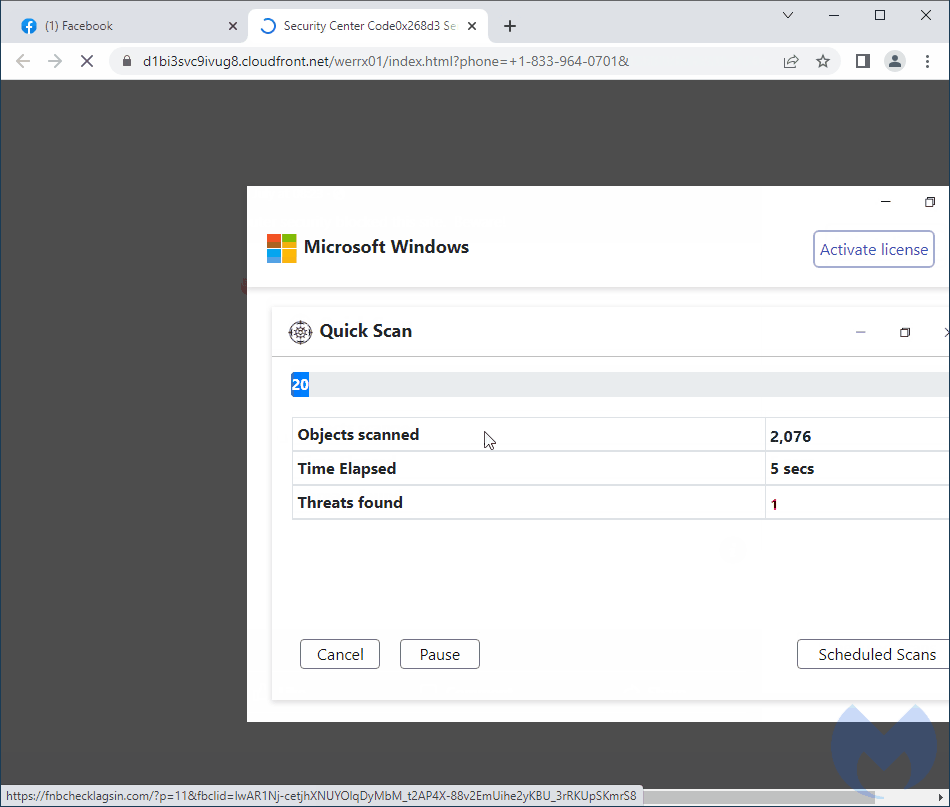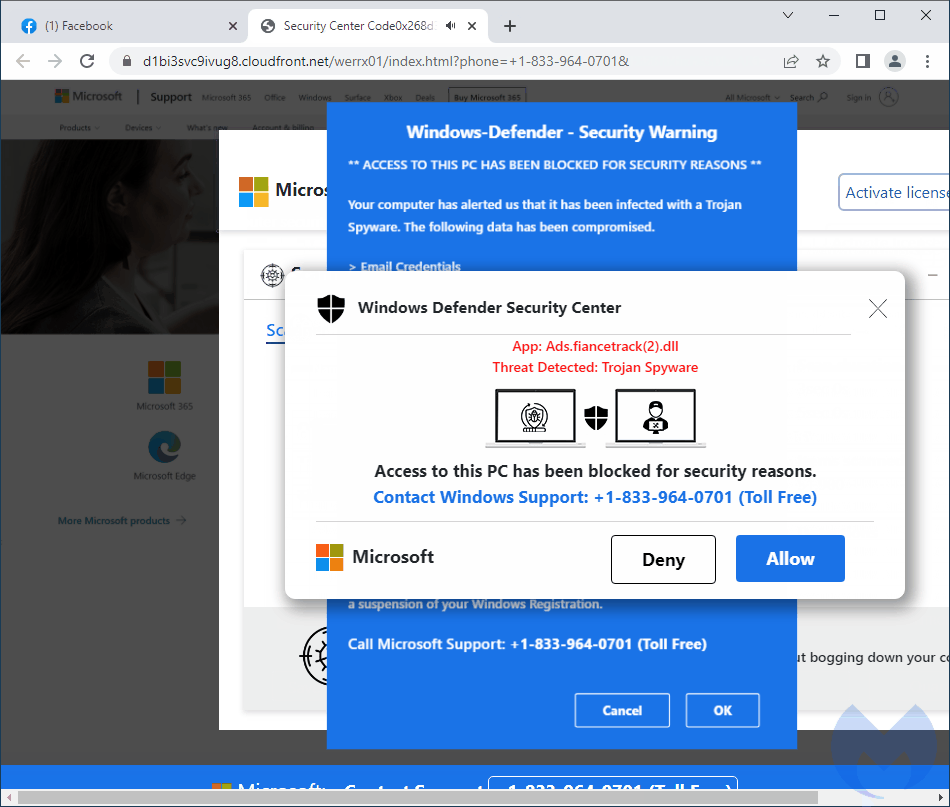
Cloaking games
In order to evade detection and remain active for as long as possible, these fraudulent schemes use a simple technique known as cloaking. The idea is to only display the malicious page in specific scenarios while showing legitimate content the rest of the time.
Here are some examples of filters that threat actors may use to their advantage:
- IP address
- Geolocation (country and city)
- Internet Service Provider (ISP)
- Browser user-agent
- Operating system (Windows, Mac, Mobile)
- Browser name and version
- Referer (the site visited just before)
- Cookies
- Time zone
In other words, for a given campaign a target may be: people living on the US’s west coast using Windows 10 and Google Chrome with a valid Facebook referer clicking on the link for the first time after 6 PM on weekdays. For the rest of the time and other visitors, a decoy page will be shown instead:
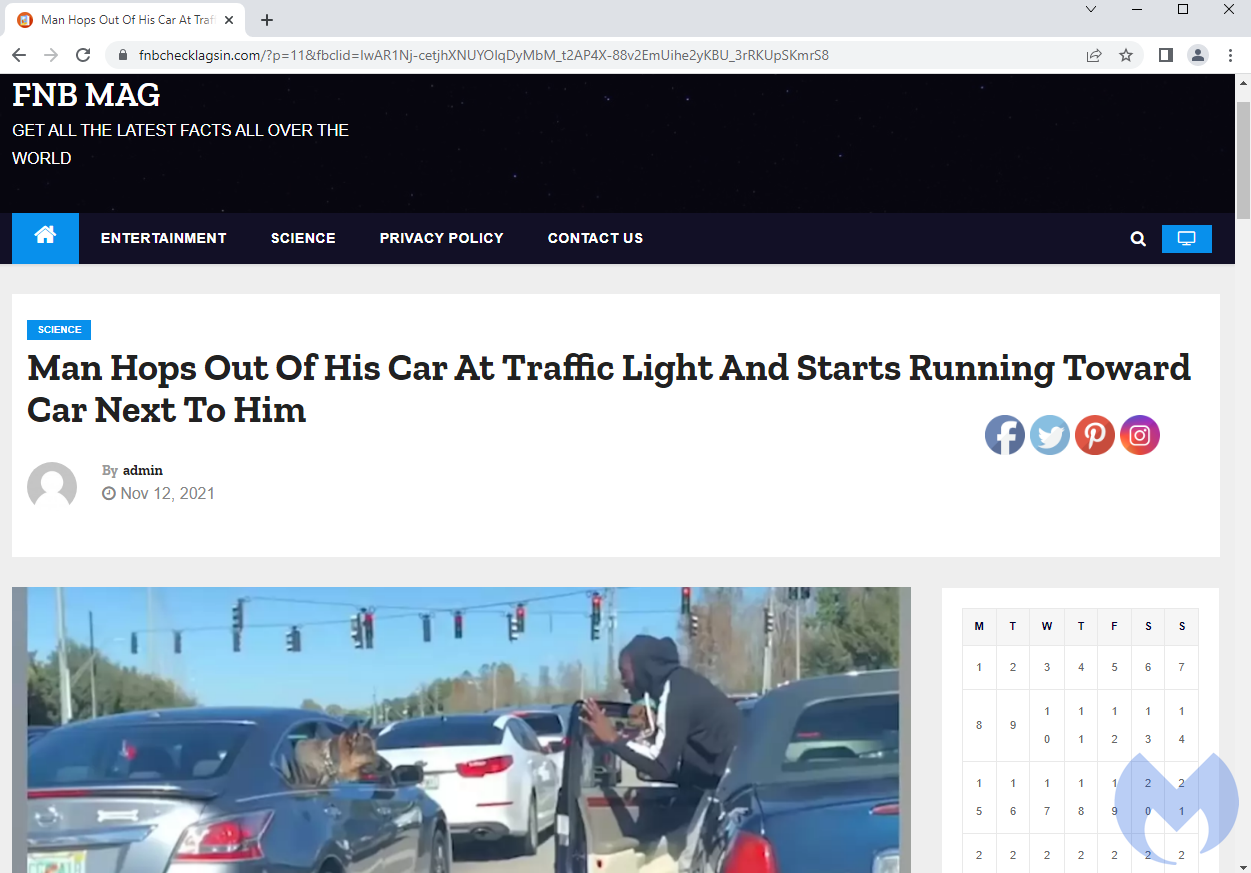
The proverbial ‘smoking gun’
When it comes to reporting such abuses, most registrars, hosting companies and platforms will require some hard evidence unless you have worked with them in the past and they already trust the information you pass along.
While a video capture is a pretty damning piece of evidence, it may not necessarily be enough to convince a provider especially if they aren’t able to reproduce the issue on their side. Because of cloaking, finding that smoking gun can literally take hours of frustrated attempts until finding the right combination of parameters. In fact, in some cases you may have to wait for when the scammers manually activate a redirect for a specific time window.
Running a web proxy is often invaluable to capture the event as it is happening as well as hard evidence of the suspected behavior. For example, what we see below are the request and response headers for the domain performing cloaking.
- The request headers show the host (fnbchecklagsin[.]com) the referer (Facebook) and the full URI we requested (GET)
- The response headers show that the server responded with the HTTP 302 code which indicates a redirect to a new location (browser locker)
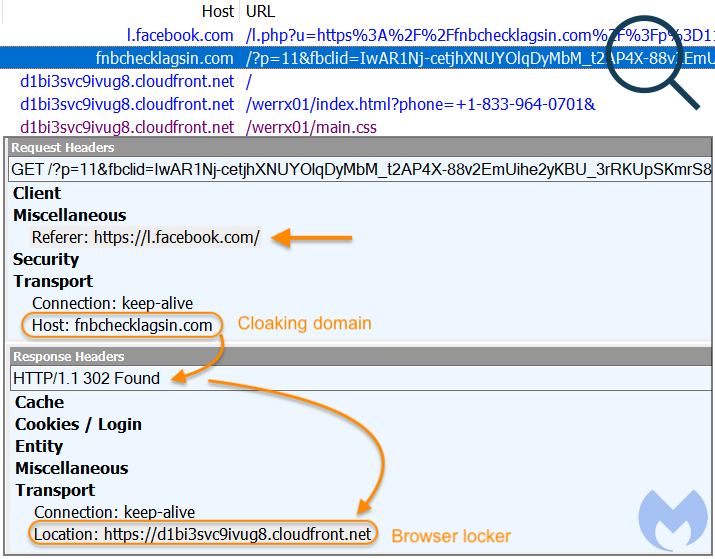
Essentially, the malicious remote server did not even serve the decoy content but immediately redirected our browser to the tech support scam page.
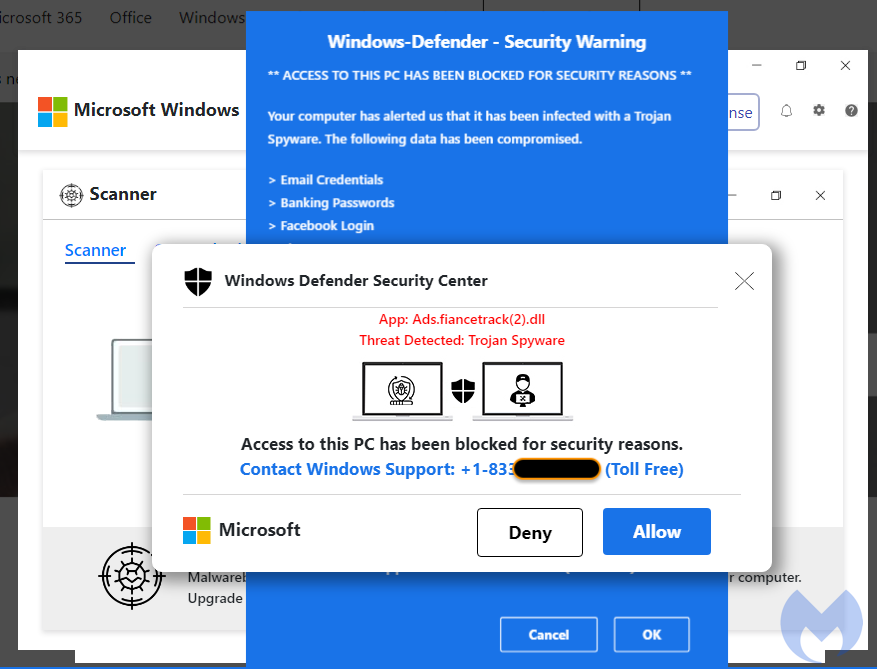
We have reported this incident to the registrar (NameCheap), the hosting provider (DigitalOcean) and the platform (Facebook) abused to spread this scam. Malwarebytes users were already protected thanks to our Browser Guard extension.










