Enterprise defenders have a tough job. In contrast to small businesses, large enterprise can have thousands of endpoints, legacy hardware from mergers and acquisitions, and legacy apps that are business critical and prevent timely patching. Add to that a deluge of indicators and metadata from the perimeter that may represent the early stages of a devastating attack—or may be nothing at all.
So how do network defenders get out from behind the 8-ball? How do leaders bring an effective strategy to bear in mobilizing incident response (IR) resources? To deal with knotty problems like this, security researchers have developed a number of IR models to help bring a maximally sane, efficient strategy to network defense efforts.
The cyber kill chain
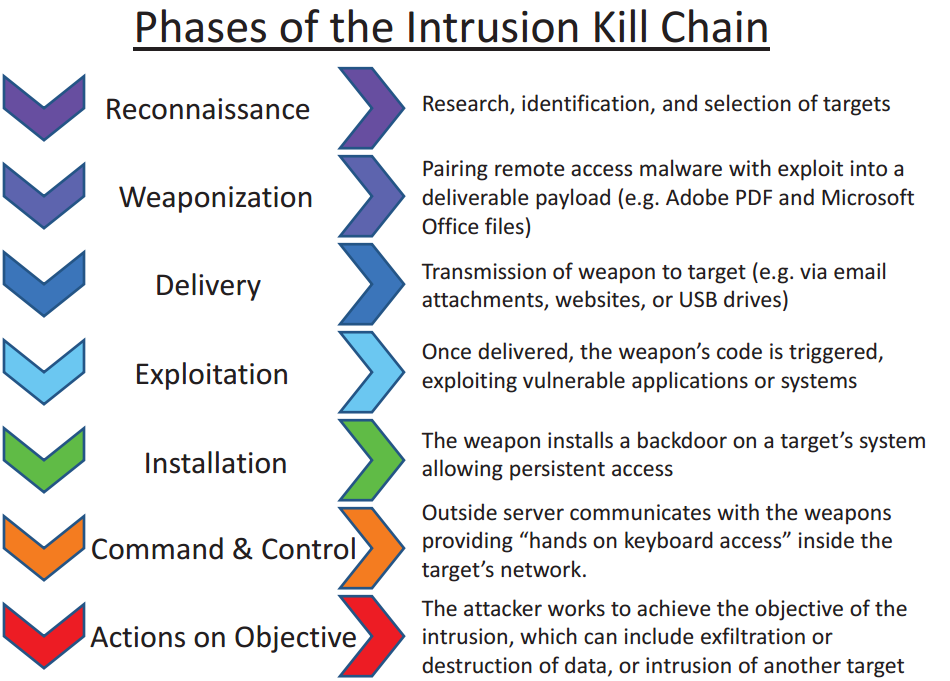
In 2011, Lockheed Martin developed the cyber kill chain. Borrowed from the US military, the kill chain essentially breaks most cyberattacks down to their constituent elements, and theorizes that forcing a hard stop to any of the seven phases will prevent the entire attack. So if an attack is caught at the installation phase and remediated, the attacker can no longer proceed to act on objectives. But if endpoint protection can stop an attack at the delivery phase, so much the better.
The general idea that makes the kill chain such an appealing way of looking at an attack is that you can’t block everything. Malspam will get through perimeter defenses. Reconnaissance will sometimes happen whether you like it or not. Exploitation will definitely happen with that one employee who is committed to clicking on everything.
So rather than throwing up a Maginot line of ever-increasing defenses at ever-escalating costs, the kill chain suggests that defenders have seven opportunities to shut down an attack, and can fight on a battlefield of their choosing. While it would be best to identify an attack at the Reconnaissance phase, killing it at the Delivery phase can keep the network just as safe, without burning out your SOC by expecting them to catch everything. Check out some more details on how the kill chain is implemented here.
The ATT&CK model
A somewhat more granular model, ATT&CK is a matrix that maps a lengthy list of attacker capabilities to a 12-step attack chain. Often seen as a complement to the kill chain, the ATT&CK can be a useful exercise to match TTPs already observed to attack chain phases to determine defense priorities. When looking at use cases for the model, threat data sharing is one of the most useful. Mapping out a full matrix of observed TTPs can be a method to quickly share a snapshot of the threat landscape across multiple defensive groups or different organizations.
Critiques of IR models
Most critiques of the kill chain and its more recent variants boil down to “what about X?” This is a little bit misguided, as attacker capabilities change over time, and a comprehensive matrix of TTPs would be exhausting to look at, and probably inaccurate in some way. What these models are really meant to assist with is bringing threat intelligence and strategy into the SOC to eliminate blind reactivity. Using any strategic model at all can bring better results than blind monitoring.
Intelligence: the bigger point
The takeaway for the SOC leader or CISO looking to implement an IR model is not picking the one, singularly correct model. Rather, implementing strategic defense in any form can boost the SOC’s responsiveness, efficiency, and accuracy. Having a well-mapped matrix tying observed indicators to specific attack phases can be an aid in prioritizing responses, as well as judging severity for a successful attack caught midstream.
Most importantly, having an incident response model forces SOC staff to respond to an incident in a strategic manner, addressing threats furthest along an attack chain first, and using threat staging to derive intelligence on potential ongoing attacks. As with conventional warfare, beating back attacks and winning the war depends on having a plan.
Stay vigilant, and stay safe.










