Ransom.Avaddon
Short bio
Ransom.Avaddon is Malwarebytes’ detection name for a family of ransomware-as-a-service that is likely of Russian origin.
Symptoms
Victims will find the ransome note named: [random number]-readme.html
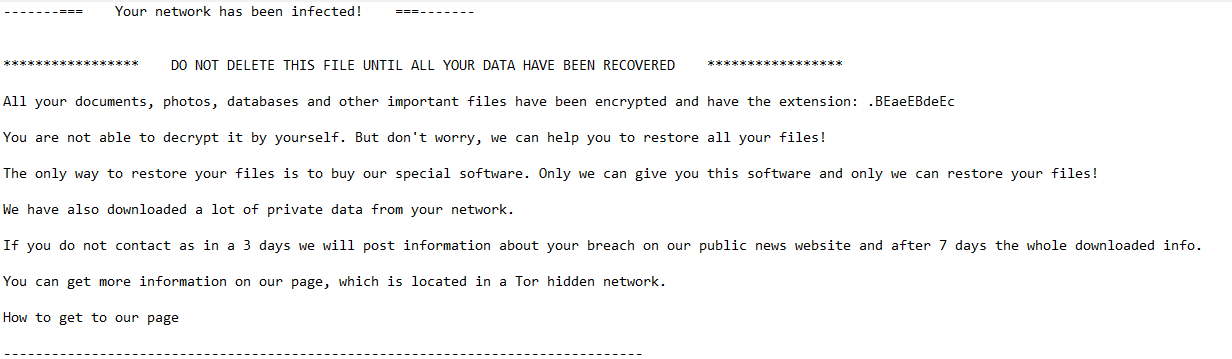
and this notification:
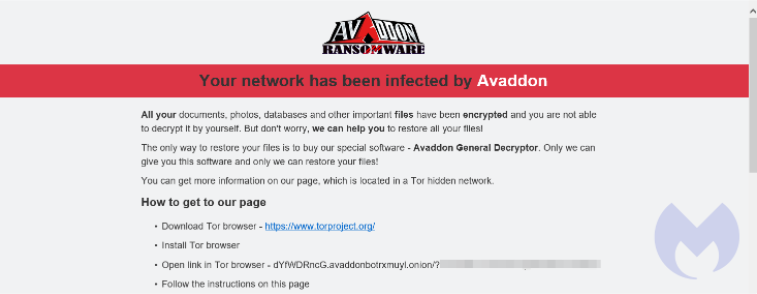
Type and source of infection
Ransom.Avaddon is sold to criminal affiliates as a Ransomware-as-a-Service (RaaS) strain. It has been around since 2019 and in June of 2020 it got some real traction due to a malspam campaign. Later it started promoting higher rates for its affiliates using adverts on networks and RDP. Avaddon ransomware performs an encryption in offline mode using AES-256 + RSA-2048 to encrypt files. Typically, with RaaS you will see affiliates run different distribution vectors and look over each other’s shoulder to see what is working best. Probably because of this model we have seen Ransom.Avaddon spread by a botnet, in malspam campaigns, by exploit kits (RIG-EK), and recently by brute forcing RDP and VPN credentials.
Aftermath
Like many other ransomware operators Avaddon has also increased pressure on its victims by threatening to publicize exfiltrated data on the dark web, and by performing DDoS attacks. The extortion/data leak process typically follows these steps:
- Leak warning: After initially gaining access to a victim network, Avaddon actors leave a ransom note on the victim’s network and post a “leak warning” to the Avaddon dark web leak website. The warning consists of screenshots from files and proof of access to the victim’s network.
- 5 percent leak: If the victim does not quickly pay the ransom within 3 to 5 days, Avaddon actors increase the pressure on victims by leaking a portion of the stolen files. The Avaddon actors leak this data by uploading a small .zip file to Avaddon’s dark web leak website.
- Full leak: If the ransom is not paid after the 5 percent leak, Avaddon actors post all their exfiltrated data in large .zip files in the “Full dumps” section of the Avaddon dark web leak website.
Protection
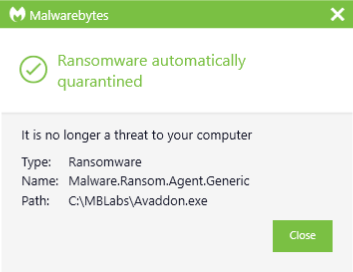
Malwarebytes blocks Ransom.Avaddon
Home remediation
Malwarebytes can detect and remove Ransom.Sekhmet without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Business remediation
How to remove Ransom.Avaddon with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
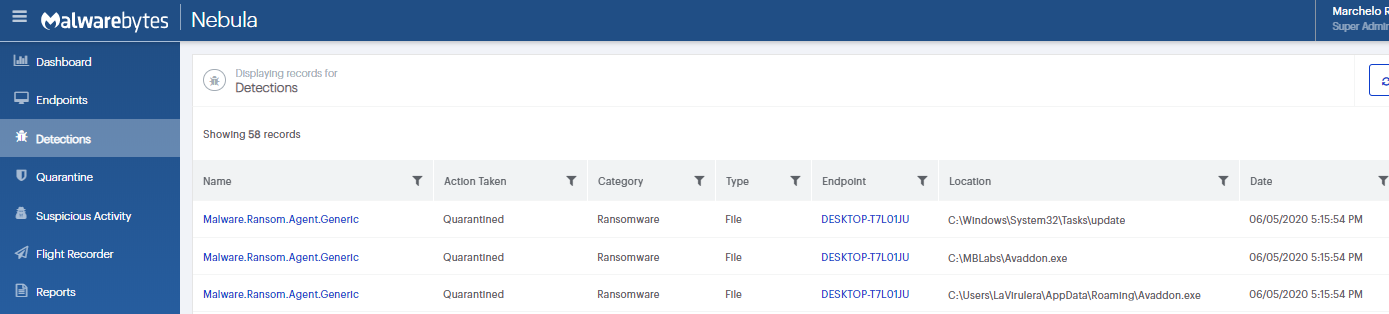
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
All component/technology detections are passed to the remediation engine for complete removal from infected systems. This industry leading technology uses patented techniques in identifying all cohorts or associated files for a single threat and removes them all together to prevent malware from resuscitating itself. If you are using Malwarebytes Ransomware Rollback technology, it allows you to wind back the clock to negate the impact of ransomware by leveraging just-in-time backups.
Traces/IOCs
C&C server: 217.8.117.63
SHA256 hashes:
fcf076de61f050573def84a471da943d940a8c9fd8120021eca893fea9bcaed3
05af0cf40590aef24b28fa04c6b4998b7ab3b7f26e60c507adb84f3d837778f2





