Ransom.Locky
Short bio
Ransom.Locky is Malwarebytes’ detection name for the Locky ransomware,which encrypts files on Windows OSes and holds them hostage for ransom. Locky was first discovered at the beginning of 2016 and immediately became one of the most significant malwarethreats in the wild. As of this writing, Locky is out of commission.
Symptoms
Typically, those infected with Locky ransomware would see a ransom note displayed either as a desktop wallpaper or a text file.

The Locky v1 ransom note, which is displayed to users in two ways: as desktop wallpaper and as a text file. The image file is named _Locky_recover_instructions.bmp,while the text file is named Locky_recover_instructions.txt.
Encrypted files bear the following extension names:
- .aesir
- .asasin
- .diablo6
- .locky
- .loptr
- .odin
- .osiris
- .shit
- .thor
- .ykcol
- .zepto
- .zzzzz
Aside from the presence of the BMP and TXT files mentioned earlier, below are other ransom note files that were found present in Locky-infected systems:
- _HELP_instructions.html
- asasin-{random characters}.htm
- DesktopOSIRIS.htm
- diablo6-{random characters}.htm
- HELP_Recover_Files_.html
- ykcol-{random characters}.htm
Type and source of infection
Ransom.Locky is distributed through the use of both exploit kits(EKs) and malspam. The Neutrino, RIG, and NuclearEKs have all distributed Locky sporadically in the past.The Necurs botnetis the main perpetrator behind the malspam that spreads Locky infections, usually as a result of a specially-crafted Microsoft Office Word or Excel file with malicious macros or a ZIP-compressed attachment containing a malicious script.
Aftermath
Systems affected by ransomware are rendered unusable due to files that are typically used for regular operations being encrypted.Affected users who choose to pay the threat actors behind ransomware campaigns in exchange for access to data may find that they don’t get their files back. There is also no sure way to know that threat actors will honor their end of the deal after paying the ransom.Affected users who chose to pay the threat actors may also find themselves likely targets for future ransomware campaigns.Data held hostage that wasn’t given back to users or deleted after the ransom has been paid can be used by threat actors either to (a) sell on the black market or (b) create a profile of the user they can use for fraud.
Protection
Malwarebytes protects users from Ransom.Locky by blocking the malware in real time.Malwarebytes also blocks the malicious macro contained in the specially-crafted Microsoft Office document file.
Home remediation
Malwarebytes can detect and remove Ransom.Locky without further user interaction.
- Please download Malwarebytesto your desktop.
- Double-click MBSetup.exeand follow the prompts to install the program.
- When your Malwarebytes for Windowsinstallation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantineto remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Business remediation
How to remove Ransom.Locky with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections pageto see which threats were found.
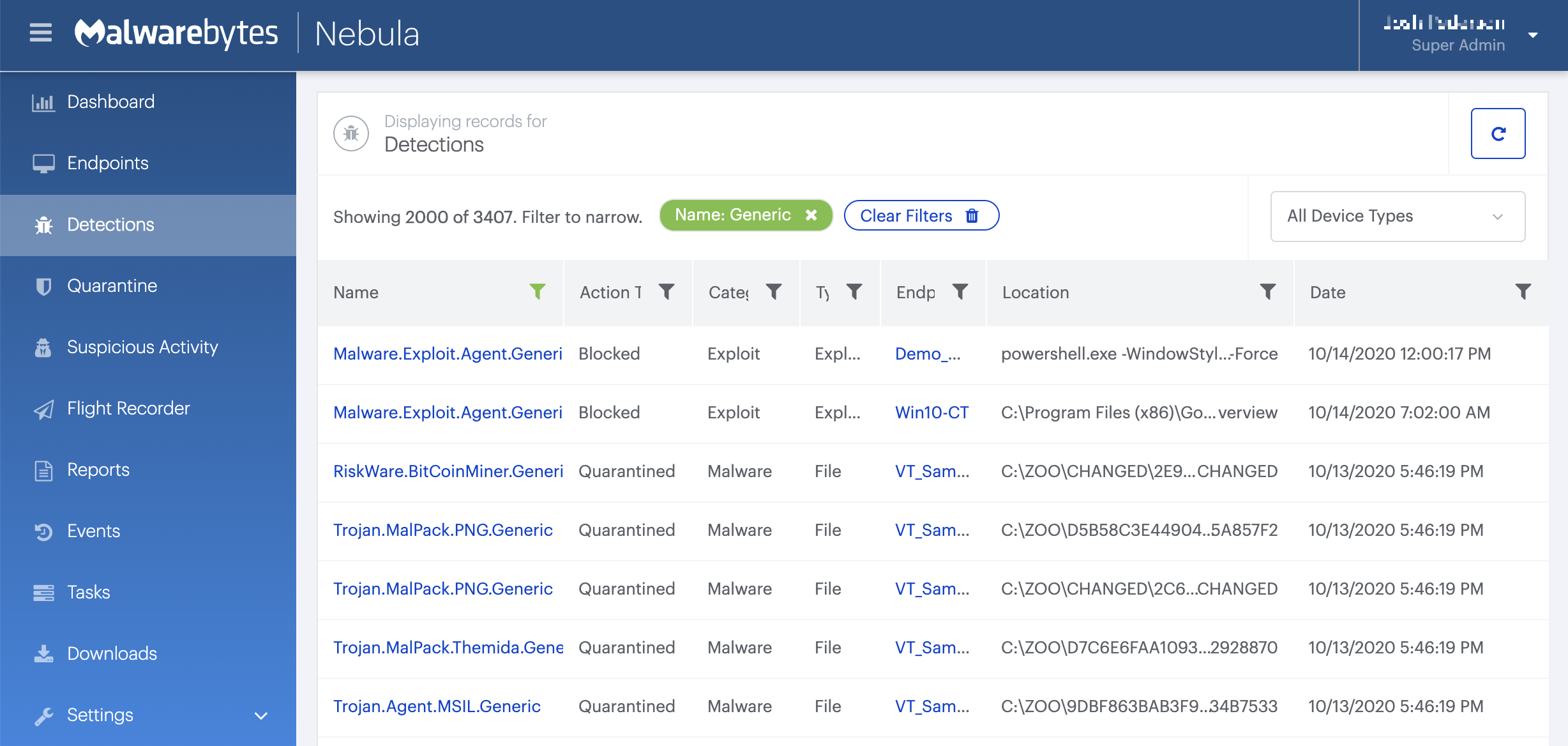
On the Quarantine pageyou can see which threats were quarantined and restore them if necessary.
All component/technology detections are passed to the remediation engine for complete removal from infected systems. This industry leading technology uses patented techniques in identifying all cohorts or associated files for a single threat and removes them all together to prevent malware from resuscitating itself. If you are using Malwarebytes Ransomware Rollback technology, it allows you to wind back the clock to negate the impact of ransomware by leveraging just-in-time backups.
Traces/IOCs
195.123.209.8/information.cgi213.32.66.16/information.cgi95.213.186.93/information.cgi91.201.202.130/information.cgi69.195.129.70/information.cgi94.242.55.81/information.cgi95.46.114.205/information.cgi82.146.32.92/information.cgi91.107.107.165/information.cgi95.46.8.175/information.cgi46.8.29.176/information.cgi89.108.118.180/information.cgi109.248.222.47/information.cgi91.142.90.55/information.cgi31.41.47.48/information.cgi213.32.90.193/information.cgi91.201.42.83/information.cgi185.118.167.144/information.cgi185.146.171.180/information.cgi92.122.214.96/information.cgi91.198.174.192/information.cgi185.115.140.210/information.cgi78.155.205.46/checkupdate91.228.239.216/checkupdate31.202.128.249/checkupdate192.162.103.213/imageload.cgi185.17.120.130/imageload.cgi195.123.218.175/imageload.cgi192.162.103.118/imageload.cgi185.20.185.119/imageload.cgi5.196.99.239/imageload.cgi5.188.63.30/imageload.cgi46.17.44.153/imageload.cgi46.183.165.45/imageload.cgi109.234.35.75/imageload.cgi91.230.211.76/imageload.cgi185.67.2.156/imageload.cgi188.127.239.10/imageload.cgi91.203.5.162/imageload.cgi91.191.184.158/imageload.cgi





