Various download sites have been plastering ads all over their pages for years, some of which are just for other types of software and some of them are for services. However, a new trend among these ads has emerged, adding an extra download button where there should not be one. Many users have been falling for this simple trick of putting in a big and shiny download button in ads as a method of tricking people into clicking it when they try to download the file they want. This trickery is not only annoying and confusing but also opens an avenue for redirects to malicious sites that can exploit your browser and infect you with malware.
The Trick
The trick is actually very simple and obviously effective as the ads continue to obtain attention and therefore the use of this method continues. In some cases, they are obviously fake, but in others it requires actually looking at the link and seeing where it points in order to determine whether or not link is legit or not. I will be showing numerous examples of this method in use that I obtained from real download sites and discussing each one.

Are you confused yet?
In this example, we see multiple “Download” buttons, however none of them actually download what we want. In order to get the file we need, we have to click one of the green arrows. This is a good example of how ads like these can get confusing.

That download button is so enticing!
Here is another example of multiple download links but the only real way to download the file we want is by clicking the link that the page advises us to click. It’s pretty small and therefore easy to ignore.
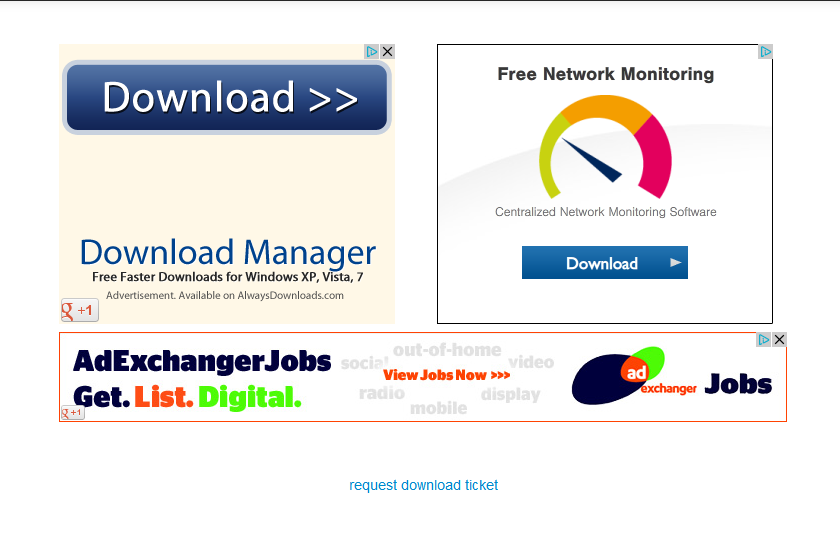
I don’t need to submit a ticket, the download button is right there!
This is an even more confusing example of this method in action. Unbelievably, the only real way to download our file is to click the “request download ticket” link at the bottom. The wording used actually makes it seem like the link is not relevant to us; since we are looking for a “Download
Will paying get me only one download link?
Sendspace is a popular site to store files, in fact it is so popular is that it is often employed by cyber-criminals to store and download malware. In this example, we see three download links and only the bottom “Click here to start download from Sendspace” link is the correct link. Notice how there is an upgrade option which lets you pay for “Fast & Ad-Free” file transfers, this is a common tactic used by download sites to make money.
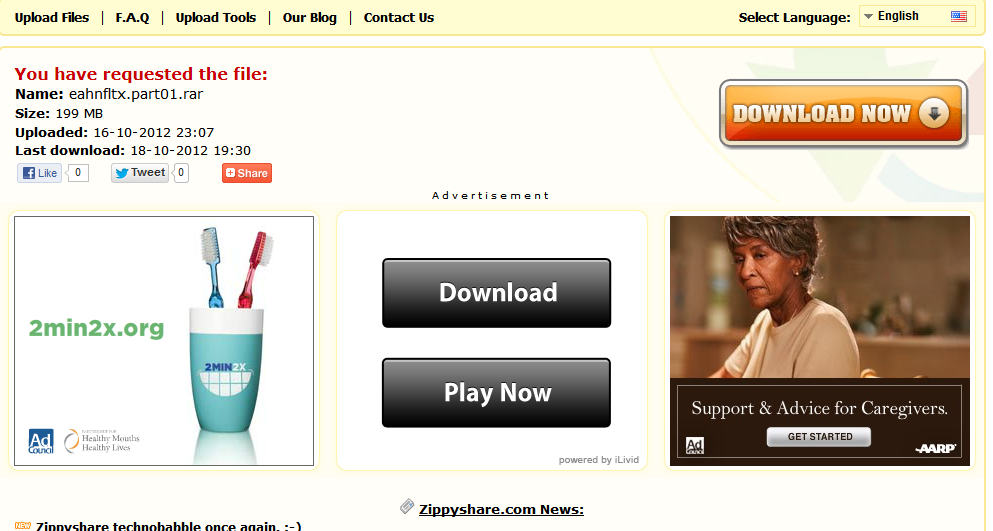
Thank you for clarifying the “Advertisement”
This example has a nice “Advertisement” box to help users determine the difference between the real download link and a fake one. The actual link is that big button to the right, but after looking at the previous examples, it looks somewhat suspicious. In this case, I would scroll over the button/link and look in the lower left hand corner of your browser to find out where the link takes you. If the URL includes the filename you are attempting to download, it is probably legit. If it does not or includes a long URL full of random characters and probably the word “ad” somewhere, it is most likely fake.
This giant and easy to see download interface seems legit enough.
This ad cracks me up since it is so massive and takes up the entire screen, anyone who is not paying attention would instantly assume that the “Click to download” button was legitimate. Truth be told, that little link on the lower right of the screen which says “Download File” is the actual link. The ad does not even tell you what it is for, who knows what you might be downloading.
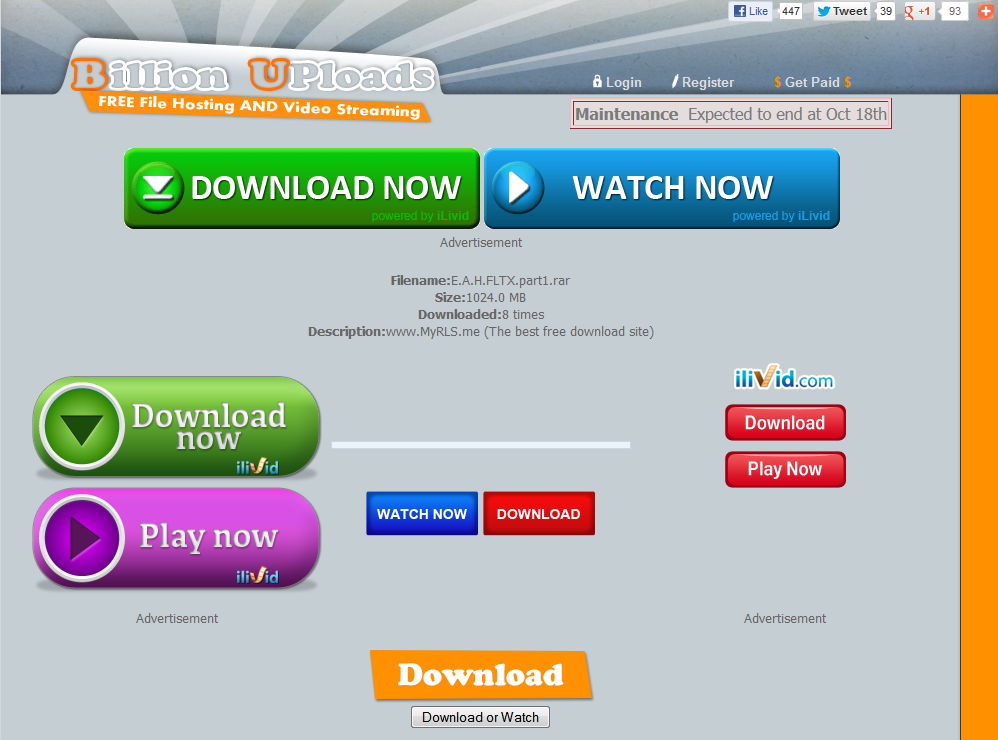
This one is tricky
Okay, this is just ridiculous. Once again, the only way to determine the actual link is to scroll over each button. Since three of the download buttons have “Advertisement” notices near them, it might help in determining the correct link, however the buttons in the center and the one at the bottom of the screen could be anyone’s guess.
Ads for Malware
Now that we have shown plenty of examples of the fake download trick in action on real websites, let us talk about the worst-case scenario, an ad leading to malware. The following screenshot shows a download site that includes a fake download ad, however unlike other ads this one leads to a site handing out malware.

Must..Press..Download Button
After the user clicks on the fake “Download” button, they are sent to a web page that includes what appears to be a video requiring flash. Where it then asks the user to download software in order to view the video. It then provides the user with an executable that turns out to be malicious software once installed. The reality is that by paying close attention you could avoid this issue by reading the actual text on the video and realizing that its not an update, just useless software. In addition, you weren’t here to even watch a video but to download your file so scams like this may or may not work depending on the knowledge, experience and vigilance of the user.
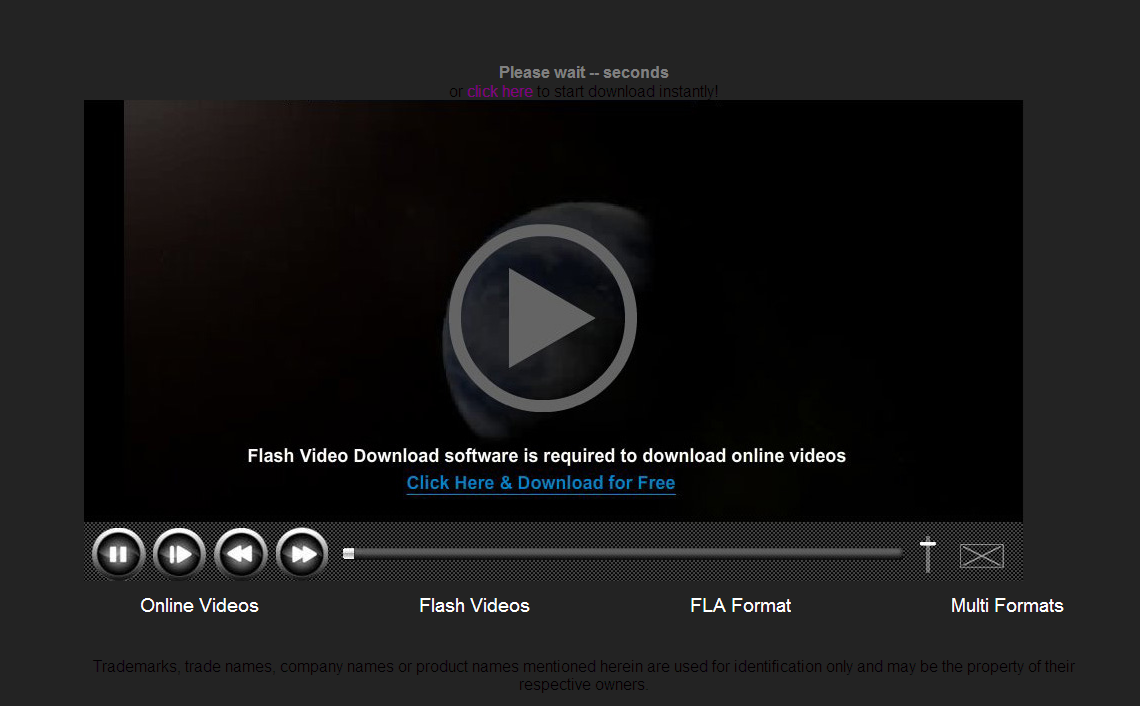
Ooh! An update!
This same type of attack had been used in the attacks against Syrian rebels earlier this year, wherein a web site was passed around advertising an Anti-Syrian government video that required a flash update in order to watch. Once the rebels downloaded and installed the provided binary, they became infected with variants of the Blackshades and DarkComet RAT. You can read more about this attack in my blog: Blackshades in Syria
ARO & CNET
Since we are on the topic of misleading download buttons, I thought it would be a good time to bring up an issue that has caused inconvenience for many of our users. Check out the screenshot below:
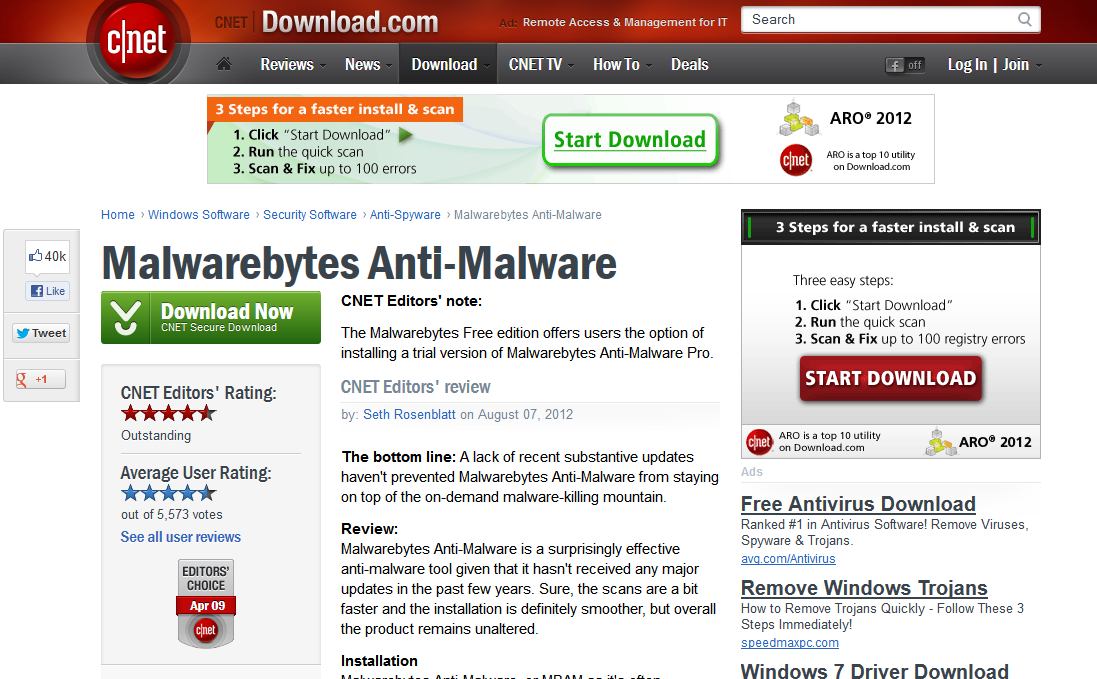
Always go green
The above screenshot shows the CNET download.com page for our product, Malwarebytes Anti-Malware. However, this is not the page that we direct our users to from our website but the page that comes up when doing a search for our product via download.com. Notice the numerous download buttons located in ads for the Support.com tool, ARO 2012.
We have had numerous instances where our users have mistakenly downloaded and installed ARO 2012 and have been required to pay for this tool when all they wanted was our tool. Please be advised that you always need to click on the green Download Now button when downloading from download.com, do not click any of the other ads.
How to avoid becoming a victim
As mentioned before, the best way to determine a fake download link and a real one is just to mouse over it. Here is an example of this method in action:
Example 1: BAD

Notice how when I mouse over the “Download Now” link at the top of the screen, my browser informs me at the bottom of the screen where I will be going, in this case the URL does not appear to include be the file I want to download; this download button is probably a fake.
Example 2: GOOD

This arrow buttons URL leads to something that contains the filename of what I want to download. Therefore, the link is probably legit and I should click it. This may appear to be a very simple practice, but by simply scrolling your mouse pointer over links before you click them, you can save yourself a lot of headache.
Conclusion
These days it is almost impossible not to come across some kind of ad every time you open your browser. While companies and ad servers make their profits by putting up these ads, cyber-criminals have also taken a hint and take every chance they can to infect your system with new and malicious malware. In the meantime, the best thing you can do is always be vigilant when surfing in unknown territory or clicking on links from sites, organizations or people you do not trust. Doing so is one of the best ways to keep you and your family safe from malware and the tactics of cyber-criminals.
UPDATE:
Looks like we aren’t the only ones tired of this kind of scam, fellow cyber-security researcher and one of the founding fathers of the Internet as we know it today, Bill Pytlovany wrote on his blog pretty much about the same thing on Sunday. Check it out if you get a chance =D. The Dangers of Downloading Free Software
Adam Kujawa is a computer scientist with over eight years’ experience in reverse engineering and malware analysis. He has worked at a number of United States federal and defense agencies, helping these organizations reverse engineer malware and develop defense and mitigation techniques. Adam has also previously taught malware analysis and reverse engineering to personnel in both the government and private sectors. He is currently the Malware Intelligence Lead for the Malwarebytes Corporation. Follow him on Twitter @Kujman5000











