In this connected world, time is of the essence. The bad guys are counting on releasing their malicious programs and infecting machines before security companies have time to analyze those samples and provide detection signatures to block the threat.
Although antivirus companies have evolved their technologies and can now provide proactive heuristic detections (essentially this means being able to detect new malware without having seen it before), cyber criminals thwart these by first testing their creations against each major security vendor to make sure they aren’t detected. If they are, they simply alter their code enough to bypass detection, at least temporarily. So much for all these fancy algorithmic engines…
This is an arms race and the bad guys always have the head start. If they can infect a few thousand computers in a couple of hours before getting detected, they have achieved their goal. And even in the case of the antivirus software later detecting the threat, it is already too late as many pieces of malware disable the security products installed on a machine therefore rending them useless.
Case in point, checking your email is something people do quite regularly. Chances are you will open an email within a few hours of it being received. This is exactly what the bad guys are counting on.
Here is an example of a recent phishing scam for UPS:
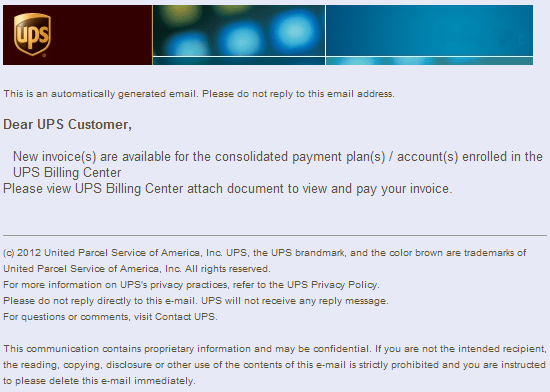
This is a classic case of printing an invoice or checking documents you have scanned. The file attached is compressed as a ZIP file (almost no email program out there ever lets you attach executable files directly anymore). As you can see, this email has made it to my inbox without being blocked at all by regular anti-spam filters.
The second layer of security is an actual scan of the attachment by one of the leading antivirus products on the market, which by the way I am not picking on at all (as you will later see):
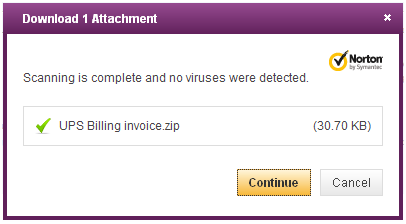
This scan was performed a few hours after the email was received and unfortunately the attachment was not detected as malicious. I wish there were still some sort of notice letting the user know that even though the file appeared to be clean, you should still apply caution before opening it.
As said above, this is not about pointing the finger at one AV product in particular. In fact, right at the same time, most vendors were totally blind to this threat.
One may wonder why security vendors fail so miserably at detecting new threats in a timely fashion. Well, as stated above, despite smart detection engines capable of detecting never-before-seen threats, the bad guys still test their malware and tweak it until it evades detection. This battle has been fought for years and always lost.
So if technology is not the answer, then what is? It is the ability to counter a threat within minutes of its release. Sure the bad guys can bypass your engine detection but they can’t do anything about you being extremely reactive and agile. The idea is simple:
Sample is released in the wild -> Sample is caught, analyzed and blocked within minutes -> end user wakes up to check their email -> sample is blocked.
Although this sounds simple in principle, it actually is hard to implement, especially for larger security companies. For starters, AV companies are flooded with new malware samples every day. How do you know which ones to prioritize? Or are they all equally as important? Secondly, companies have to go through so many processes before they can release an update to their customer base. This includes various testing cycles that at the end of the day delay the time sensitive release of a new malware definition.
Although those Quality Assurance tests are important, they need to be streamlined. Some large AV companies are conservative (and for good reason!) before they release an update. And yet, it has not prevented ‘accidents’ such as major false positives which always make big headlines and ridicule your company. In large parts, such incidents happen because everything is so automated and people learn to trust these automated processes to be flawless (or at least less error prone than humans). While this is true, the human factor should not be taken out of the equation. In almost all cases of a major false positive (such as an AV engine detecting itself) it would have been spotted easily by a human tester.
I’d like to conclude this post by looking at how a company like Malwarebytes tackles the issue. First and foremost, a large part of Malwarebytes’ success is its ability to leverage the community’s input. Since its inception, the company has vowed to battle online threats to offer a malware-free experience for computer users without having to pay a dime for it. The last thing you want to do if your PC is fully infected is purchase a security product using your credit card and get that leaked to the bad guys too. As such, the company has earned respect from many users who are very willing to help out in the fight against malware.
In addition, Malwarebytes employs some of the best security researchers worldwide who have had extensive experience helping out people in online forums, their community etc… And those guys who never sleep (no, really!) are extremely reactive to new threats. If you got that phishing email with the bad attachment in your inbox today, you can bet they already looked at it while you were still sleeping.
While the bad guys can beat complex pieces of technology, they can’t beat a relentless determination to fight them back before they can make money at the end user’s expense.
Note 1: Malwarebytes Anti-Malware did detect the fake UPS invoice right away.
Note 2: if you ever scan/email a document from the UPS store, make sure to ask them to delete it then when you are still in the store. In an experience I had recently, they had kept my papers on their computers for several days. If they got infected, a lot of confidential documents could get leaked.









