A few weeks back, we told everyone we were going to BSides to do things like meet awesome people and give some talks. Well we are back now and ready to tell you all about it.
BSides San Francisco was a great experience for everyone; we saw some fantastic talks, met up with some awesome people and were able to share our own knowledge with the rest of the conference and soon, all of you. While there, two of our researchers, Jerome Segura and I, gave some talks about issues that we thought were most important.
“I want my PC Back” An In-depth Look at Ransomware:
Our Ransomware talk went great, it was about an hour long and we spent every single moment informing the audience about the very real threat of Ransomware malware. It started with a look back at the evolution of this kind of malware from a variant we saw just the other day to all the way back to 1989. After that we discussed the methodology behind Ransomware, why it worked so well and why was it being used so often. We really enjoyed this portion of the talk and we think the audience did as well because it was not super technical; we were able to talk about something that everyone has experienced at some point in their lives, guilt.
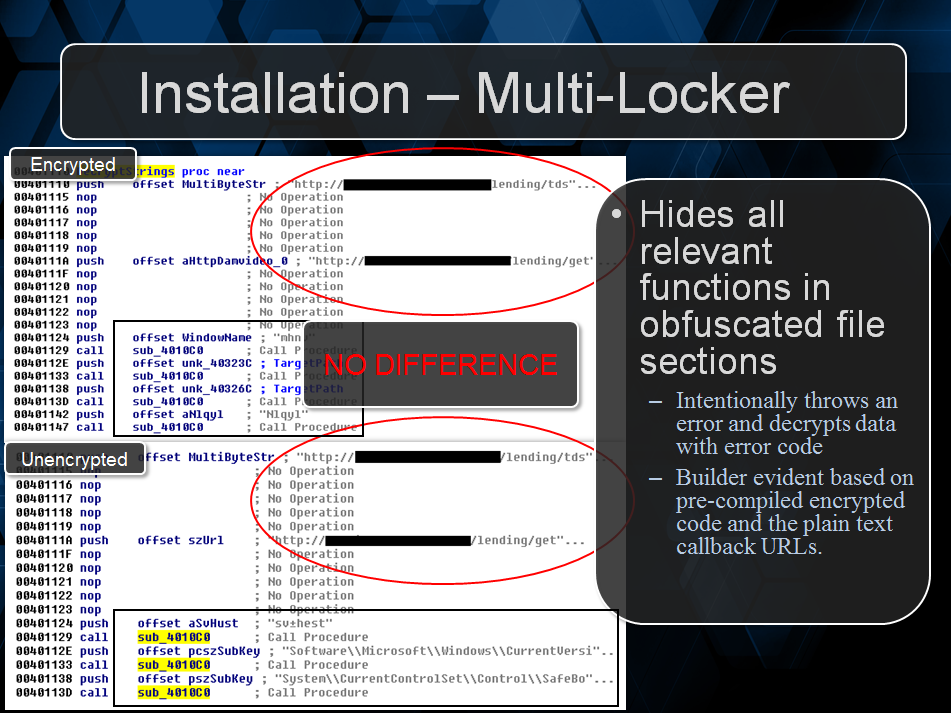
After that, Jerome did a great introduction into drive-by exploits, how they work and how they are involved in Ransomware operations, I think everyone watching might have become a little more afraid of malware knowing that attacks like 0-Day drive-by attacks can happen to anyone. Following that we looked into how two variants, Multi Locker and Reveton install on the user system and their very different methods for achieving the same goal.
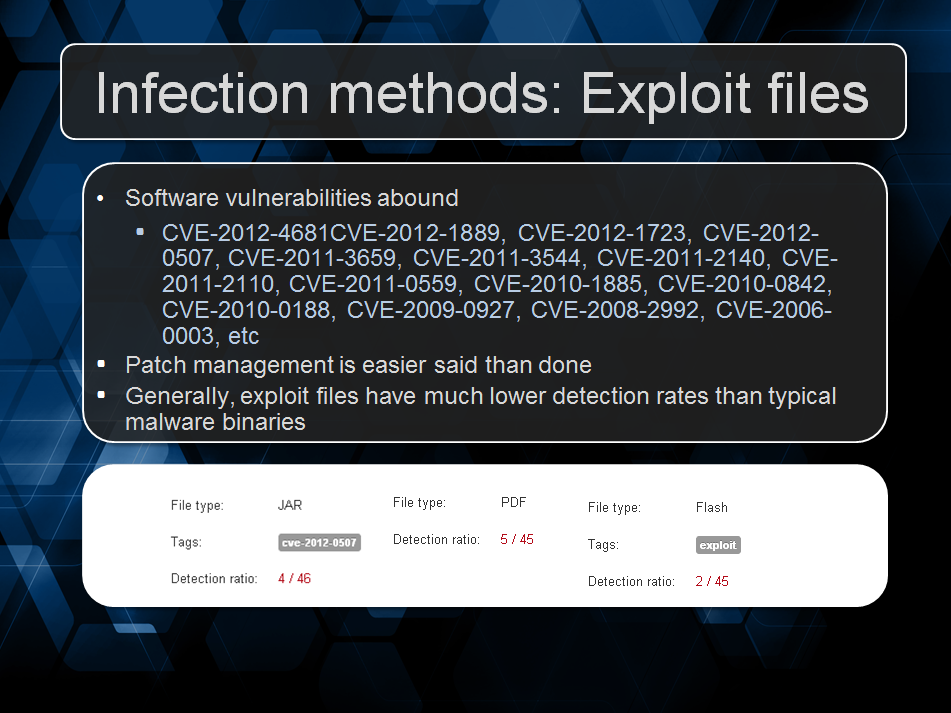
Jerome took on the job of describing what goes on under the hood when it came to traffic between the command and control server and the actual Ransomware, describing the technology used and even some sample traffic of an unlocking operation. We decided to make a demo of the actual infection and showed the audience a video we recorded that gave the watcher the perspective of not only the victim but also the attacker and used a Multi-Locker C2 and implant to visualize the entire ransom process, from installation to unlocking.
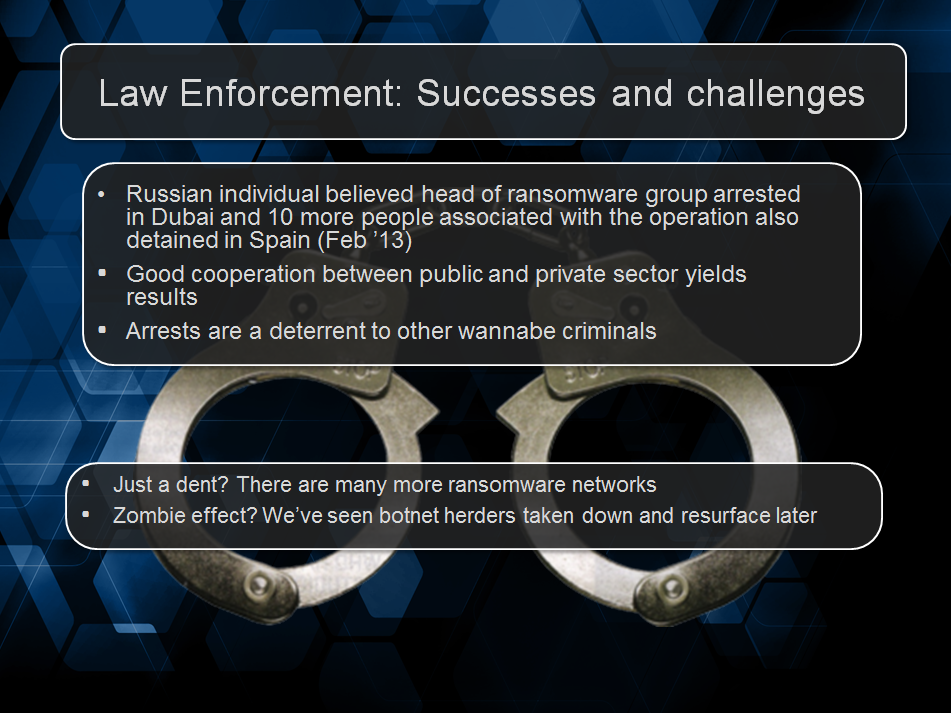
We continued by showing the audience the operations involved when the Ransomware actually unlocked itself and finished that section by showing different methods for manual removal. Finally, we gave a nod toward recent arrests of a Ransomware gang and talked about our own predictions for the future of Ransomware. All in all it was a pretty fantastic experience and are looking forward to an opportunity to do it again.
For more info, check out a PDF version of the Ransomware Presentation.
Videos:
- You can find the Multi-locker demo video HERE.
- In addition, the Speaking Ransomware video can be found HERE.
Press Start: The basics of Malware Analysis
This talk I did on my own and it was a total beginners look at malware analysis. It began with the description of the various levels of analysis and what was involved with each level. The talk itself would only go up to very basic dynamic analysis but it was important to let the audience know that there was much more involved if they chose this career path.

Next was how to collect malware for analysis and how to setup an analysis environment, the very basics of malware analysis revolve around these concepts as without the actual malware and without a place to analyze it, how can you possible do your job?

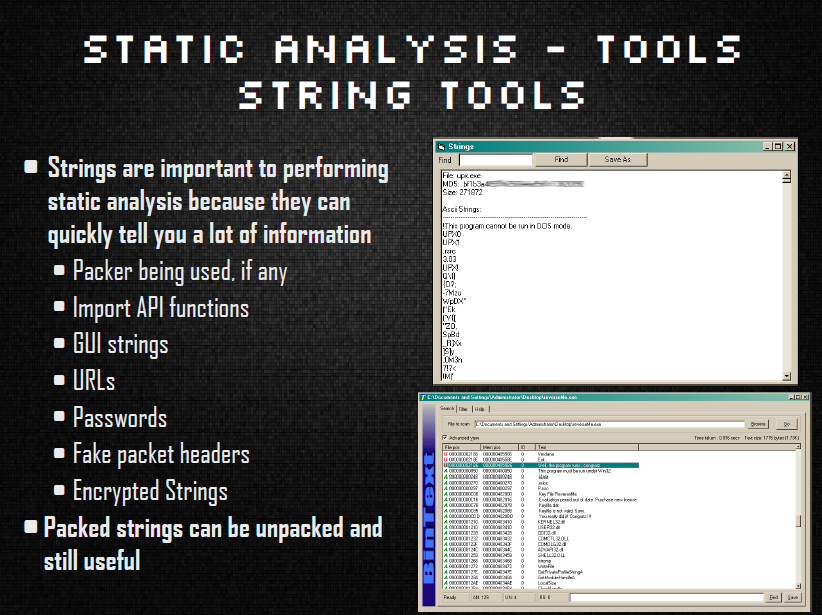
Static analysis was next and an explanation of what kinds of data can be derived from a file without ever actually executing it then what kind of information is important enough to derive from that data. I listed numerous tools used to gather this data, finishing up the section with how to take that data and run it against numerous online sources that might shorten the actual analysis time significantly.
The next section was all about dynamic analysis and what tools/operations are involved in watching the malware execute. This section listed tools and methods for collecting data on system modifications such as registry and file changes, actual logs of what calls the malware was making and network traffic information. The talk finished up by describing what the next step would be on the path of malware research and a listing of some of my favorite educational sources.
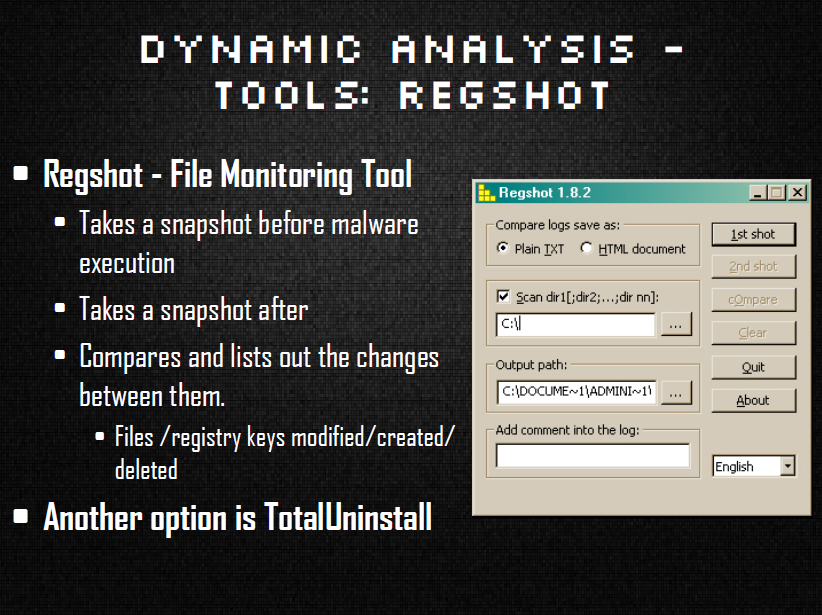
I received a lot of good feedback on the talk and was answering questions about it until the day the convention ended! I would love to revamp it and make it a bit longer to give at a future conference. To check out a PDF version of Press Start: The Basics of Malware Analysis.
Conclusion
We had a blast at BSides SF and hope next year to give more talks or at least watch some great ones. In the meantime, if you did not make it out to BSides this time, you can still check out our presentations by either PDF (above) or watching a recording of the talk done by the staff at BSides. The video is not up yet but as soon as it gets posted we will post the link here for you. Thanks for reading and Stay Safe!
—————————————————————————————————————————–
Adam Kujawa is a computer scientist with over eight years’ experience in reverse engineering and malware analysis. He has worked at a number of United States federal and defense agencies, helping these organizations reverse engineer malware and develop defense and mitigation techniques. Adam has also previously taught malware analysis and reverse engineering to personnel in both the government and private sectors. He is currently the Malware Intelligence Lead for the Malwarebytes Corporation. Follow him on Twitter @Kujman5000











