On March 20th, reports were circulating that a cyberattack had been conducted against broadcast networks and banks in South Korea. In typical reaction, it was suspected that North Korea may have been to blame, although no evidence has surfaced supporting this idea. However, it’s recently been reported that at least one of the bank attacks traces back to a Chinese IP address.
BBC news provided more details that same day, stating “two South Korean banks, Shinhan Bank and Nonghyup, and three TV stations KBS, MBS and YTN, all reported that their networks had suddenly shut down on Wednesday afternoon.”
The malware used in these attacks is a type of disk wiper that renders your computer’s operating system useless. It achieves this by overwriting the Master Boot Record of the primary disk with the string “PRINCIPES” and “HASTATI”, two Latin words for Roman heavy infantry and light infantry, respectively.
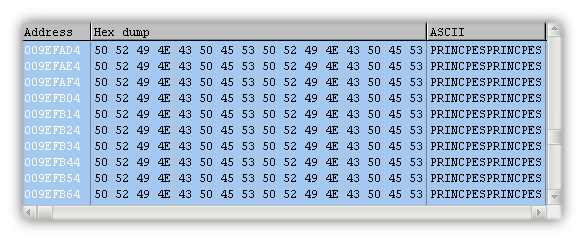
It then cycles through every drive on the host and performs the same operation, ensuring that everything gets hosed in the process. It cycles through every disk drive using letters starting with B: and also accesses them directly starting at \.PhysicalDrive0.
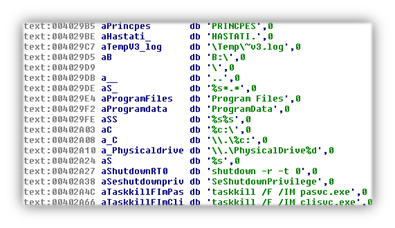
The dropper that creates the “wiper malware” also has some additional components that target remote Linux machines, and also looks for mRemote, a remote connection manager that’s no longer supported. Extra baggage makes the dropper ~400k, whereas the wiper is only 24k in size.
To prevent any disruption from security products, the sample kills a couple of Korean AV processes if they’re running on the host: pasvc.exe (AhnLab) and clisvc.exe (Hauri), but no big US contenders like McAfee or Symantec are on this list. You can also see that shutdown commands are issued after the drives are wiped, thus rendering the host inoperable.
On another front, one Korean network provider LG U+ had their website defaced at about the same time the networks went down. The provider’s original homepage was replaced by one containing skulls and a short message from the “Whois” team, an unknown group with “an Interest in Hacking”. The page has sounds of laughter with lightning effects—to get the full, creepy effect check out the youtube video here.

After the attacks occurred, speculation arose that this could be an example of state-sponsored malware. In my own humble opinion, I don’t think so. While use of Latin military terms and destructive capabilities may echo conventional CNA methods, this “wiper malware” doesn’t seem refined enough to fit the category.
If we recall the state-sponsored Flame malware that was discovered in May 2012, its main module was about 6mb in size, and estimated to be a whopping 20mb when all modules are attached. From another angle, Stuxnet had both a user-mode and kernel-mode component with two digitally-signed certificates from JMicron and Realtek. This just seems juvenile when compared to these cyber weapons.
However, the fact this kills two processes associated with only Korean AV companies indicates a highly-targeted attack. A lot of the malware found in the wild goes after a wide array of AV processes (our article featuring skype.dat ransomware targets 28 processes from AV vendors) from abroad.
Still, many security researchers conclude the wiper malware is very simple indeed: it’s not modularized, not obfuscated, and doesn’t offer anything unique that we haven’t seen before. After performing some of my own analysis, I’d agree; it’s easy to determine the malware’s intent within minutes, something that wouldn’t happen with state-sponsored mega-malware.
As for the hacker group, nobody’s really heard of them, which makes sense since their message states this as the “beginning of our movement”. Will we see anything else from the ‘Whois’ team? I’m not sure, but I am confident this malware isn’t funded by a nation state. In the past, we’ve seen plenty of samples that kill the MBR, it’s not anything new. Although a flashy image with skulls and lightning puts on a good show, to me it resembles someone trying to get attention from that neat trick they just performed, and not the subtlety of a real professional.
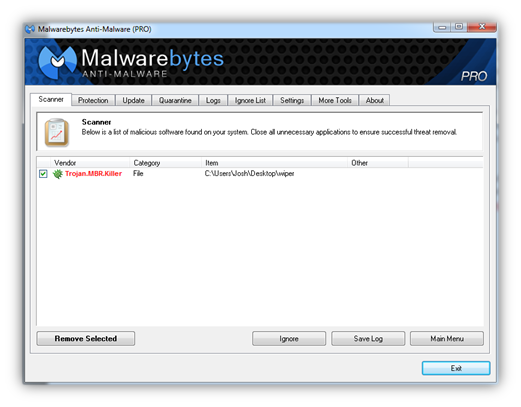
Finally, if you’re reading this wondering if you’re in danger, probably not—the wiper was used in a targeted attack and you’re not likely to encounter it. Regardless, you’ll be happy to know you’re protected from this kind of malware with Malwarebytes Anti-Malware, which it detects as Trojan.MBR.Killer.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell










