Once again, Skype has proven itself to be a valuable tool for the spread of malware and other malicious doings by cyber criminals. Our researchers have discovered a scam being spread via Skype that is designed to steal the log in credentials for Skype users by dangling free premium upgrades. However unlike other attacks, this one checks the legitimacy of your credentials before infecting your system with malware.
The Scam
The scam starts off with a user receiving the following message from one of his or her friends:
hey go to hxxp://www.SkyPremiumSetup.com/ and activate your account, Skype is giving away free premium for life to a few thousand people. Once you have it, you can do group video calls and a ton of other cool stuff. i got to head out now but I’ll ttyl for sure!
After clicking on the link, the user is sent to the site seen below and required to enter his or her username and password to activate the free premium account. In reality, there is no free premium upgrade and if you had actually fallen for this tactic, the bad guys would now have your Skype log in credentials. In addition, a good tip off that this is in fact a real scam is the incorrect grammar used in the title text. First of all “receive” is spelled incorrectly and Life Long should be one word. Maybe nothing that you would notice immediately but errors in text and formatting are always a great way to determine the legitimacy of something you come across online.
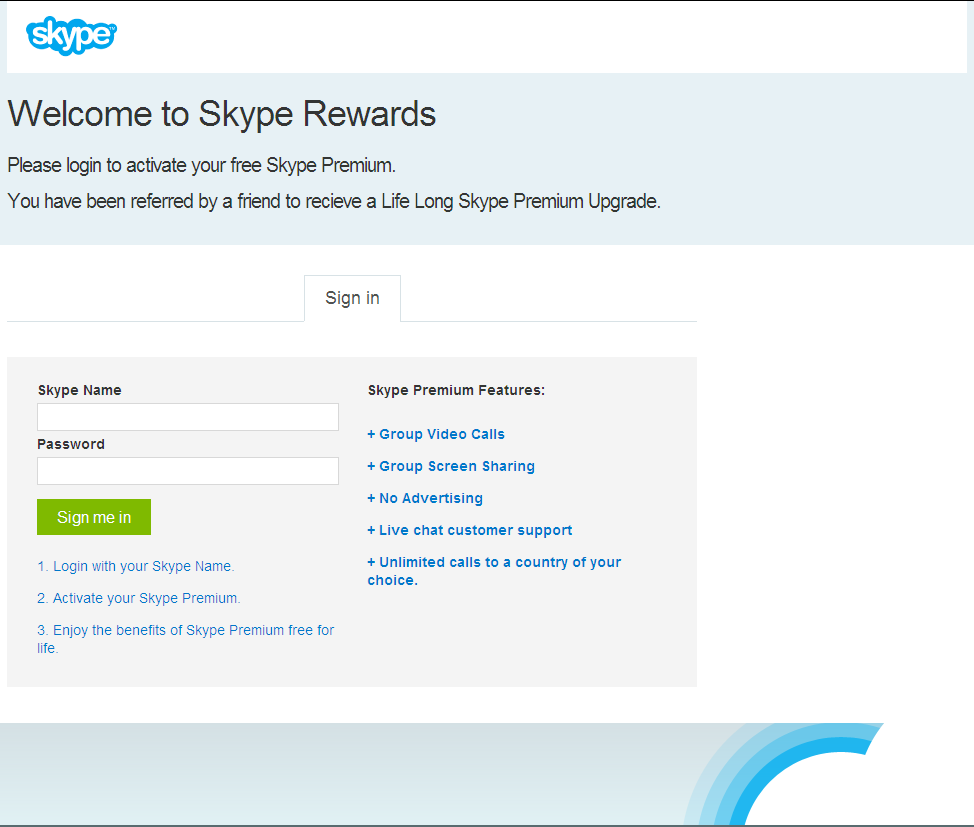
A new tactic for the bad guys is actually ensuring that the credentials you’re providing are legit! When you enter your Skype log in credentials, they are checked for accuracy using a legitimate Skype authentication service and if you give fake or incorrect log in details, the scam will not proceed. I know this based on my traffic capture , which revealed a Secured Shell (SSH) tunnel being created between my system and a valid Skype application domain. From there it was obvious that the log in prompt was legitimate however, what becomes of your credentials once you press “Sign me in” is another story entirely.
So in order to test this scam without giving up my own personal information, I decided to create a new account with the name “Juan Sanchez villa-lobos Ramirez” and the Skype username Villa-LobosRamirez. (Extra points if you get the reference.) Once I had the new account created I plugged in the credentials and was on my way to the next stage of the scam.

Chief Metallurgist to King Charles V and Anti-Scam Warrior (image copyright 20th century fox)
After legitimate credentials have been provided, you are redirected to a download web page that looks a lot like the official Skype download page.
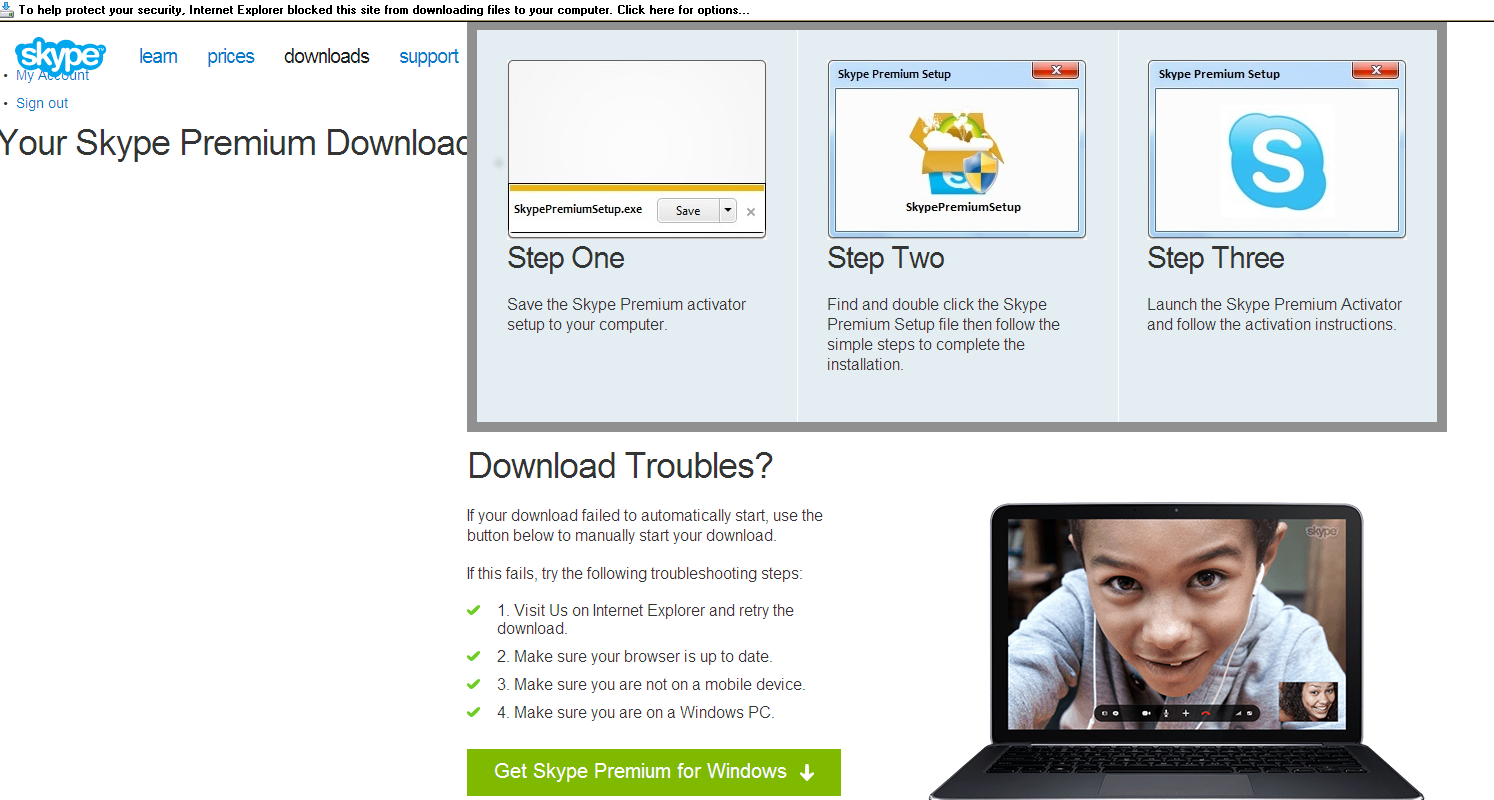
…that is if the Skype download page were on drugs
The page will attempt to download the recommended installer and launch it in order for the premium activation application to upgrade your account. At this point it’s just adding insult to injury—you have already given up your Skype log in credentials but now you are also downloading suspicious software.
The Malware
After you download the software and let it execute, a screen pops up that looks a little suspicious, with the Skype logo image not quite fitting in with the rest of the screen—the screen claims that it is activating your life premium package.

In reality, malware is being downloaded and executed on your system while the application is “activating.” You can see the download happening by checking out this screenshot of my Fiddler capture during the “activation” process.
The file is labeled “kickit.lol,” which, unbelievably, is actually a known Banker Trojan.

Now that your Skype credentials have been stolen and you also have malware running on your system, your contacts can expect to see a similar message to the one you received in the near future.
Here are the file properties for anyone who might want to check out these files further:
| File Name | MD5 Hash | File Size |
Kickit.lol | 46F7320243320CA494B00C056DA7E7C3 | 96256 |
SkypePremiumSetup.exe | ACBCD179C1A72BCC84F2A88C827B5A7A | 773632 |
Fortunately, the domains used in this scam have been taken down however that doesn’t mean that others won’t pop up.
How to Protect Yourself
The term “phishing” has moved beyond the traditionally seen scammer e-mail attack and into the realm of social media and communication tools like Skype. The reality is that while you may do everything in your power to keep your data safe and secure from cyber criminals, your friends and family might not be so prudent. With that in mind, it is important that any communication that you are not certain is coming from someone you know be seen as suspicious.
For example, if you received the message referenced in this post from a friend of yours and he or she immediately logged off or you attempted to talk to the friend and he or she did not respond, that is a flag that the message might be malicious, and you should wait until you communicate with your friend further before clicking it. The same goes for messages received on Twitter, Facebook, Google+, or even traditional e-mail.
By keeping your security software such as anti-malware or spam detection software and applications such as Java, Flash and your operating system up to date, you may very well lessen the damage of this attack if you happen to fall victim to it.
Conclusion
It seems like more and more often we are seeing attacks coming at users from all angles and under the guise of trusted contacts and legitimate services. Despite the uncertainty of trusting your friends and their activities online, the one certainty in all this is that the attacks will continue and with mass customization of phishing attacks based on data derived from your online footprint, they are going to get worse. The key is to always be skeptical and use prudent security approaches with everything you come across. By double-checking the legitimacy of a single link, you could save yourself some serious heartache. Thanks for reading and stay safe!











